VLAN (Virtual Local Area Network) is a method of creating logically isolated virtual network groups that cannot communicate directly with each other, using a single piece of physical hardware (like a switch). This makes networks more secure, faster, and easier to manage.
One of the important features of VLANs is their ability to unite devices or networks from different physical areas under a single logical network.
Ports on a VLAN-enabled switch are configured in two basic modes:
Access Port:
- Usually belongs to a single VLAN.
- Used to connect end-user devices like computers or phones to the network.
- A device connected to this port becomes part of the network to which the port is assigned, and the device is generally unaware of the VLAN.
Trunk Port:
- Can carry traffic from multiple VLANs simultaneously.
- Adds VLAN tags to packets using tagging methods like 802.1Q to differentiate traffic.
- Generally used for connections between two switches or a switch and a router. This allows traffic from different VLANs to be transported between devices.
VLAN-Capable NICs
This is the ability of a computer's (usually a server's) network interface card (NIC) to perform VLAN tagging. This means the computer's operating system can directly add a tag to the packets it sends, such as "This packet belongs to VLAN 10" or "This packet belongs to VLAN 20."
- Now, not just the switch, but the computer itself can add a tag to the data it sends, saying "I belong to VLAN 20."
- This feature allows a server to connect to multiple VLANs simultaneously with a single physical network cable. This is particularly useful for servers running virtual machines.
Assigning a VLAN to a Device (Linux)
A virtual VLAN interface (e.g., eth0.55) is created on top of a physical interface (e.g., eth0).
- Many tools like
ipandvconfigcan be used to assign a VLAN. - Now, we need to find the name of the physical Ethernet interface on which we will create the VLAN interface:
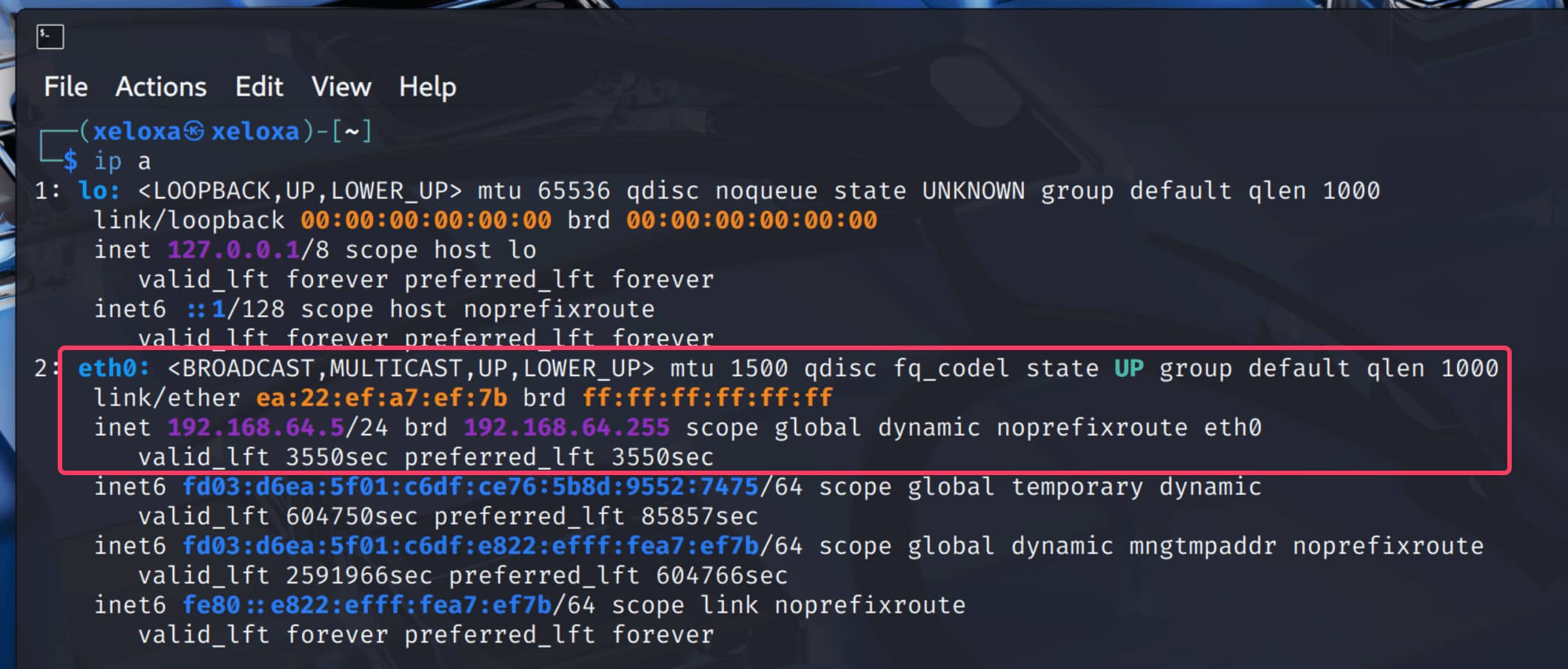
- Next, we will use
vconfigto create a new interface on eth0 that is a member of the desired VLAN, for example, 55: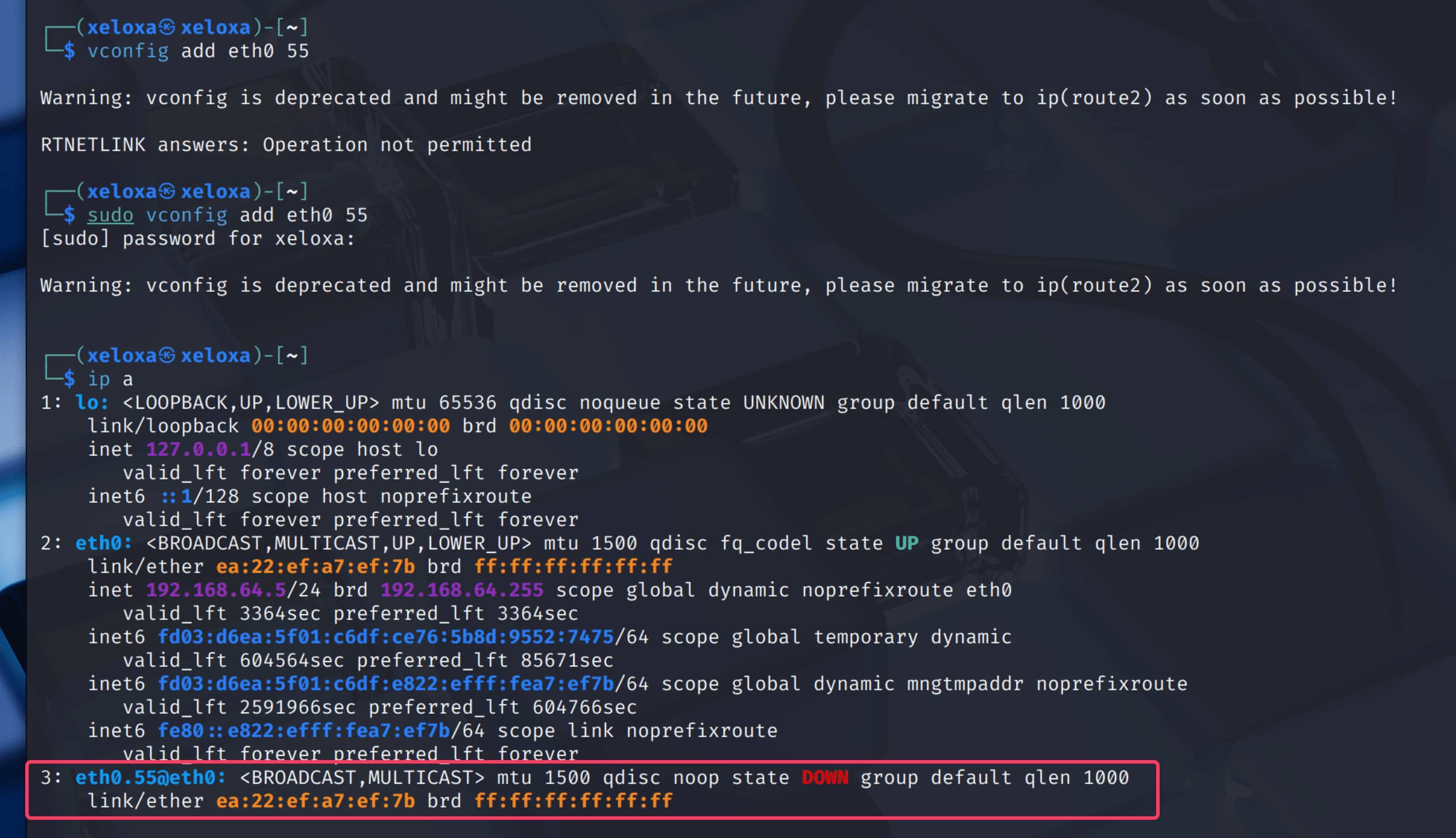
- Then, we need to assign an IP address to the interface according to the subnet assigned to addresses with VLAN 55 in the local network and bring it up:
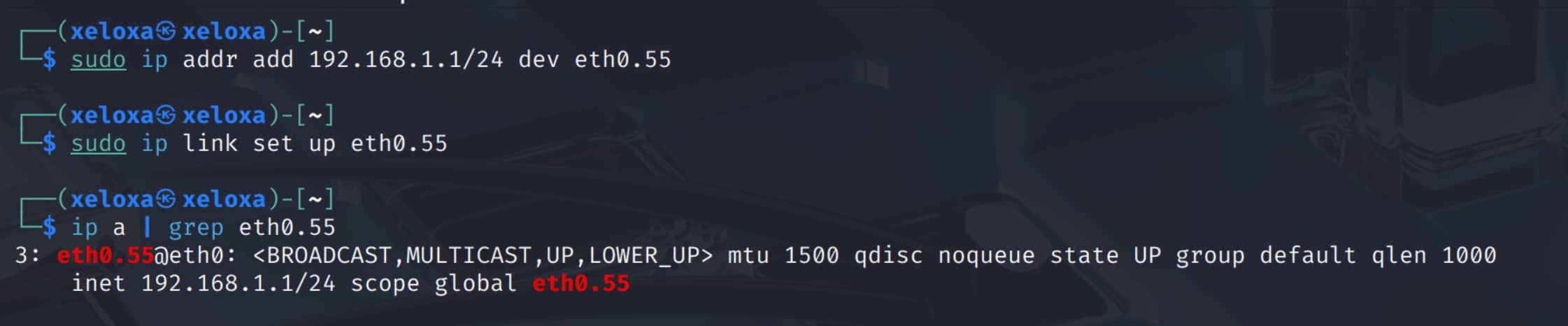
When you create virtual interfaces like eth0.10 or eth0.55 in Linux, you are essentially telling the operating system, "Tag the packets going out of this virtual interface as VLAN 10." The hardware that performs this operation is the VLAN-capable network card.
VLAN Attacks
Although VLANs increase security by logically separating networks, they also have their own vulnerabilities and can be subject to various attacks if not configured correctly.
VLAN Hopping
This is a type of attack that allows an attacker to send or receive traffic belonging to a VLAN they do not normally have access to. There are two main techniques:
a. Switch Spoofing
This attack exploits the vulnerability of switch ports being left in "dynamic" mode by default.
How it Works:
- On Cisco switches, the Dynamic Trunking Protocol (DTP) is active by default. This protocol allows two switches to automatically establish a trunk link between them when they are connected.
- The attacker physically connects to a port on the network. They configure their computer to act like a switch and continuously send DTP messages to the switch, saying "I want to be a trunk."
- If the switch port is in
dynamic autoordynamic desirablemode, it accepts this request and turns the port connected to the attacker into a Trunk Port. - Since the attacker now has a Trunk Port, they can listen to traffic from all VLANs and send tagged packets to any VLAN they want.
b. Double Tagging
This attack exploits a vulnerability in how switches handle Native VLAN traffic.
Native VLAN
Native VLAN is the default VLAN to which untagged traffic sent over a Trunk port is assumed to belong. When a switch receives an untagged packet on this port, it automatically considers it to belong to the Native VLAN.
How it Works:
Prerequisite: The attacker must be in the same VLAN as the Trunk port's Native VLAN. (The Native VLAN is also a specific VLAN. For example, you would say, "Set VLAN 10 as the Native VLAN.")
- The attacker creates a special packet. The packet has two tags: an outer tag (the Native VLAN ID) and an inner tag (the Target VLAN ID).
- The packet reaches the first switch the attacker is connected to. The switch only looks at the outer tag of a packet coming from a Access Port. Since it belongs to the Native VLAN, it strips the outer tag and forwards the packet to other Trunk Ports.
- The packet, now with a single tag (the target VLAN's tag), reaches the second switch.
- The second switch looks at the tag on the packet (the inner tag), assumes the packet belongs to the target VLAN, and forwards it to the devices in that VLAN. Thus, the attacker has successfully sent a packet to the target VLAN.
Comments
Loading comments...